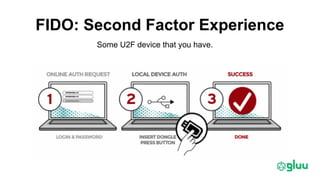
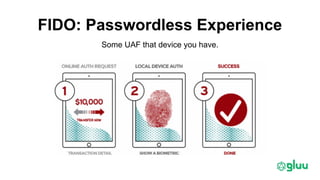
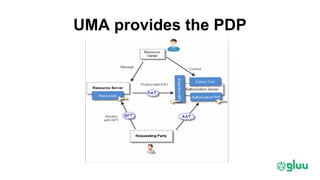
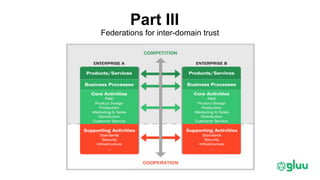
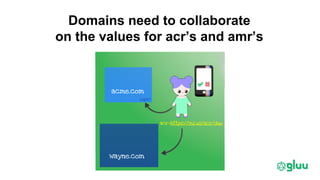
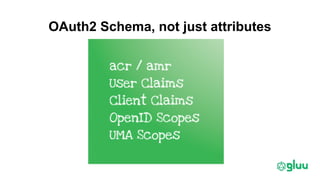
Trust elevation allows increasing authentication strength to enable higher-risk transactions. It involves tradeoffs between security and usability. OAuth2 and OpenID Connect provide standard authentication frameworks for apps and APIs, supporting a range of authentication methods from passwords to biometrics. User managed access (UMA) further extends OAuth2 to implement policy-based access control. To enable cross-domain trust elevation, organizations can participate in federated identity systems like SAML and OAuth2 federations, which standardize technical and legal integration between identity providers. Emerging areas involve authentication for IoT devices and fine-grained access control over distributed data.