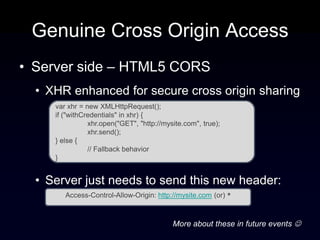
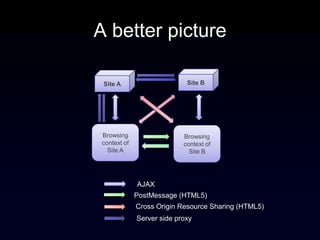
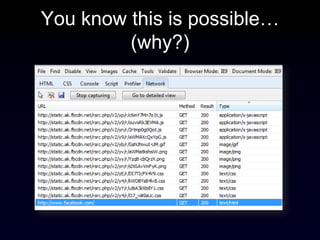
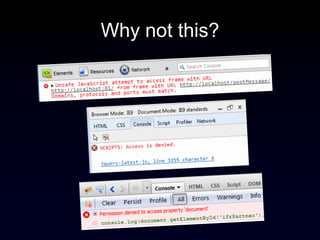
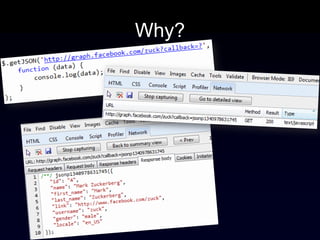
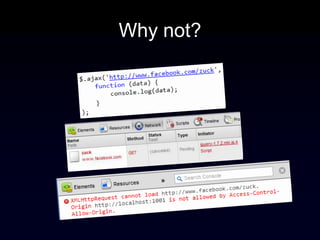
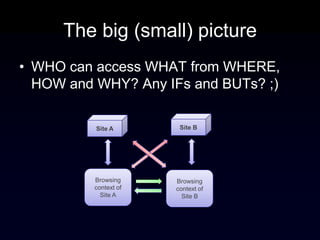
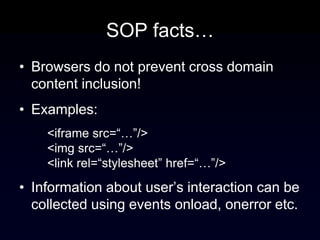
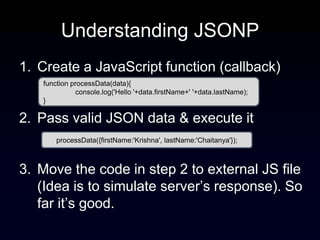
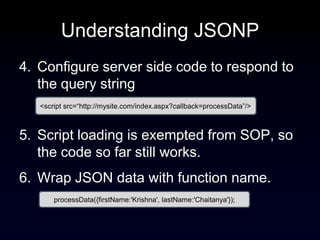
The document discusses the Same Origin Policy (SOP), which governs how different web origins can interact with each other and what resources can be accessed across origins. It elaborates on various methods and hacks to bypass SOP restrictions for cross-origin communication, including JSONP and HTML5's postMessage API. Additionally, it introduces CORS (Cross-Origin Resource Sharing) as a newer standard for secure cross-origin access.









![Genuine Cross Origin Access
• Client side - HTML5 PostMessage API
• Secure communication between frames
otherwindow.postMessage(message, targetOrigin);
//Posting message to a cross domain partner.
frames[0].postMessage(“Hello Partner!”,
"http://localhost:81/");
//Retrieving message from the sender
window.onmessage = function (e) {
if (e.origin == 'http://localhost') {
//sanitize and accept data
}
};](https://image.slidesharecdn.com/browserinternals-sameoriginpolicy-120701004438-phpapp01/85/Browser-Internals-Same-Origin-Policy-19-320.jpg)