The document provides an overview of secure web messaging in HTML5. It discusses how traditional methods of communication like JavaScript, AJAX, and frames had limitations due to the same-origin policy. The HTML5 postMessage API allows for secure cross-origin communication between frames by abstracting multiple principals. While more secure than previous techniques, the postMessage API still requires careful configuration of target origins, validation of received data, and mitigation of framing attacks to prevent security issues like cross-site scripting.


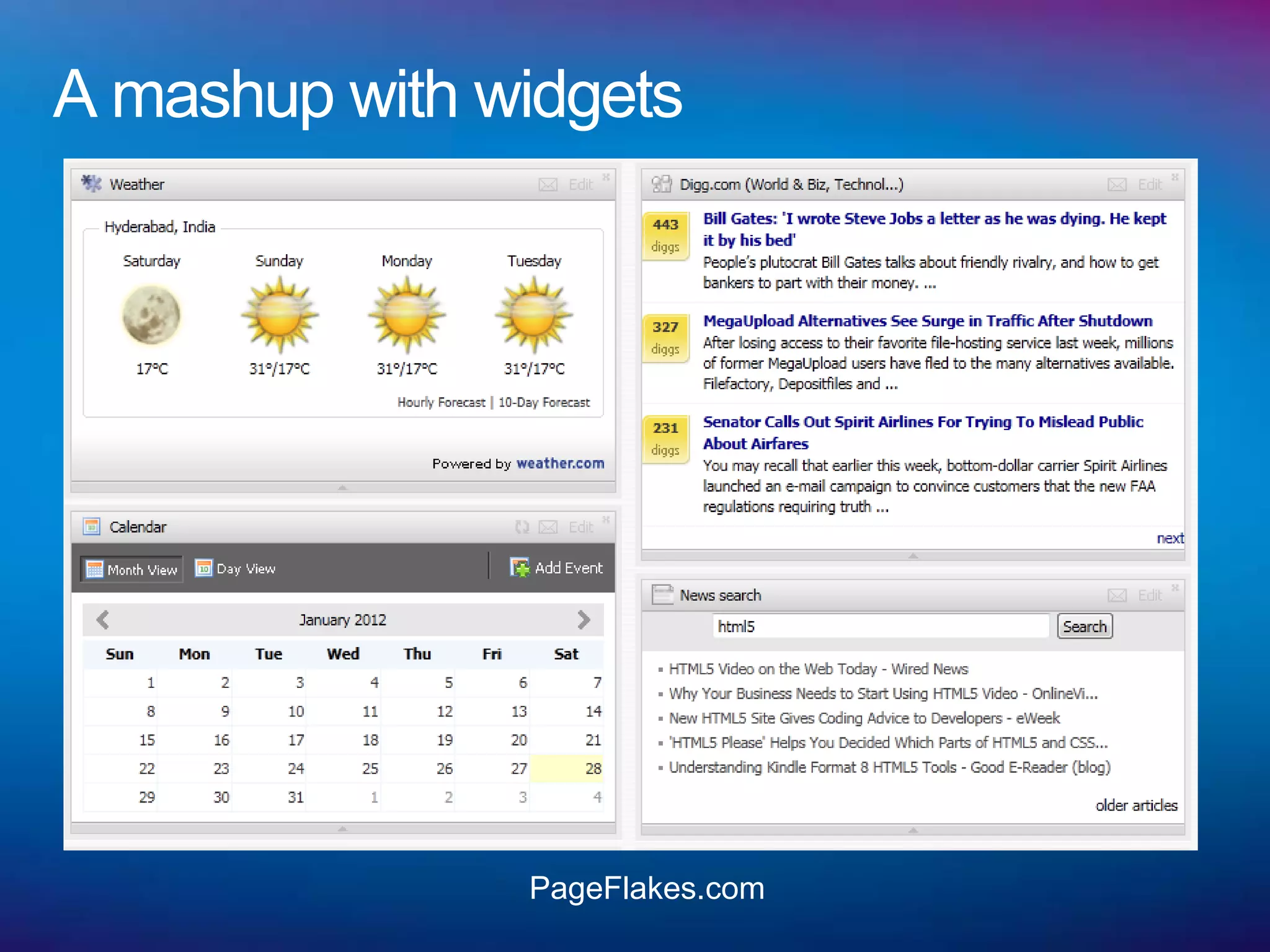
![Isolation with Frames
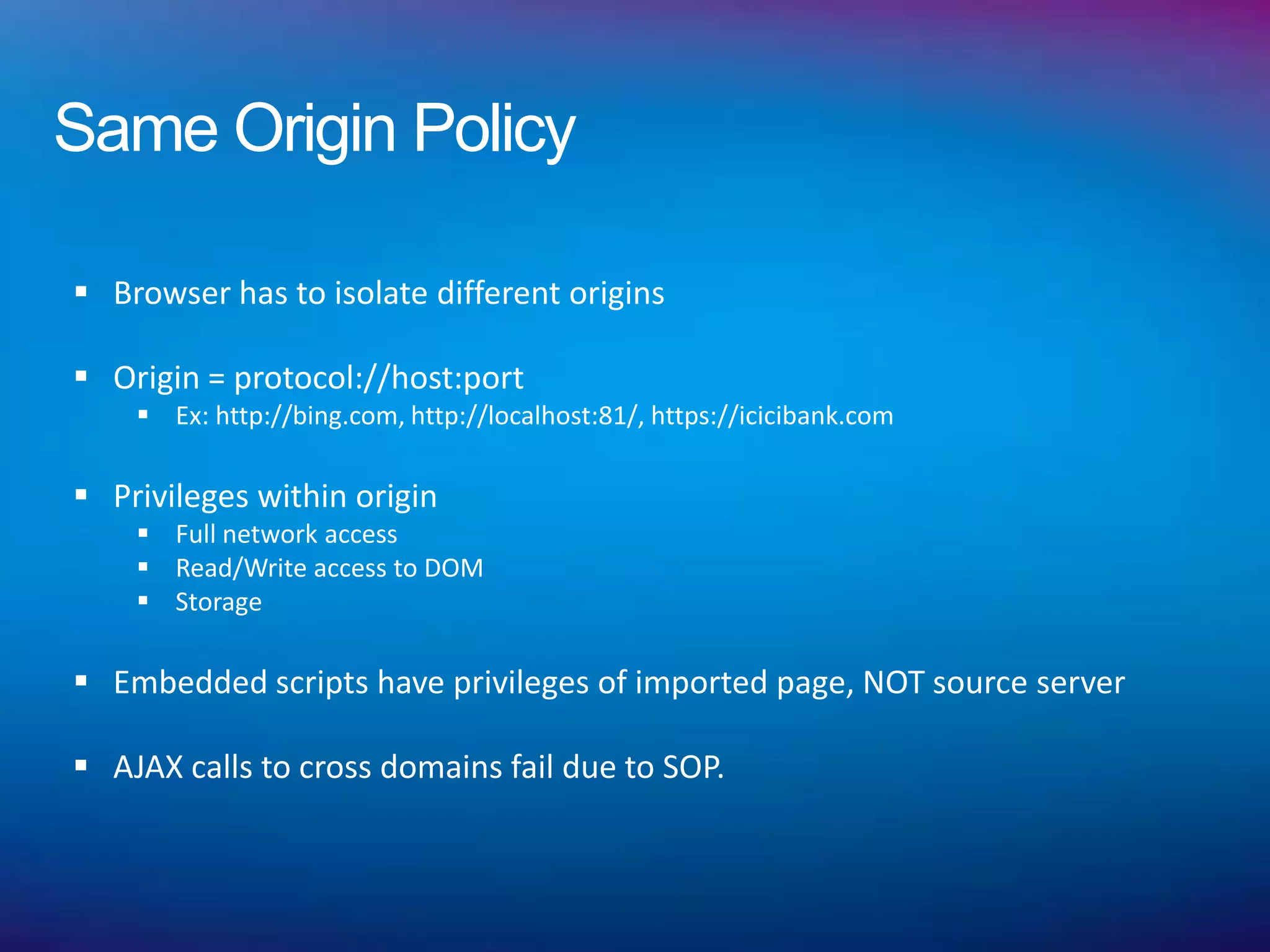
Different security contexts for different origins
Brings modularity but less interactive than embedding JS
No standard communication mechanism
Comply with SOP - Run remote code safely
<!-- This is allowed -->
<iframe src="sameDomainPage.html"> </iframe>
alert(frames[0].contentDocument.body); //works fine
<!-- This is **NOT** allowed -->
<iframe src="http://crossDomain.com"> </iframe>
alert(frames[0].contentDocument.body); //throws error](https://image.slidesharecdn.com/securewebmessaginginhtml5-120128232659-phpapp01/75/Secure-web-messaging-in-HTML5-8-2048.jpg)
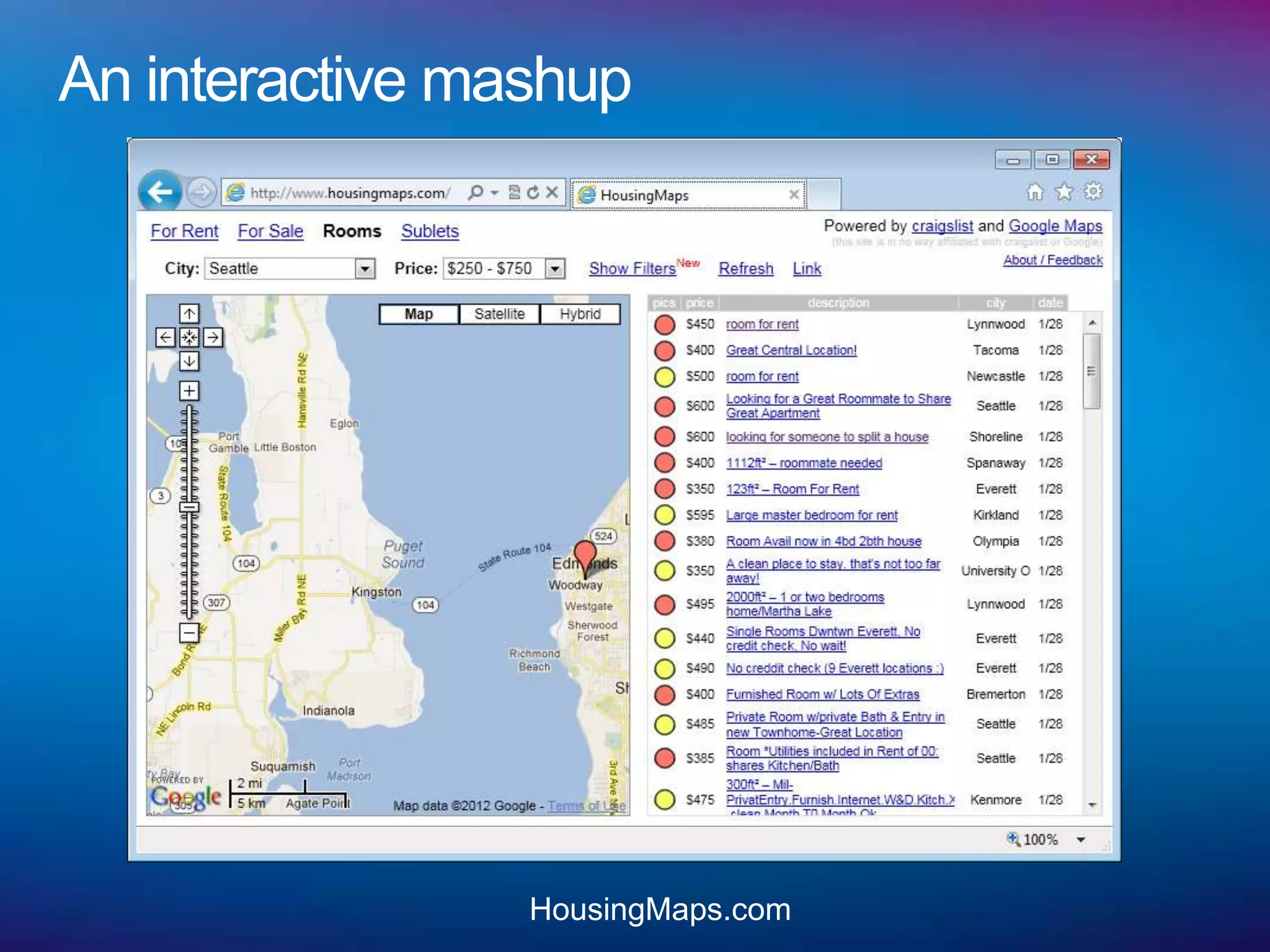
![Frame Navigation
Beware! Frames can be navigated to different origins!
Frame-Frame relationships
Can script in Frame A modify DOM of Frame B?
Can Script in Frame A “navigate” or change the origin of Frame B?
Frame navigation is NOT the same as SOP - often mistaken!
<iframe src=“http://crossDomain.com"> </iframe>
<!-- This is **NOT** allowed -->
alert(frames[0].src); //throws error – SOP restriction
<!-- This is allowed -->
alert(frames[0].src=“http://bing.com”); //works fine - frame navigation](https://image.slidesharecdn.com/securewebmessaginginhtml5-120128232659-phpapp01/75/Secure-web-messaging-in-HTML5-9-2048.jpg)
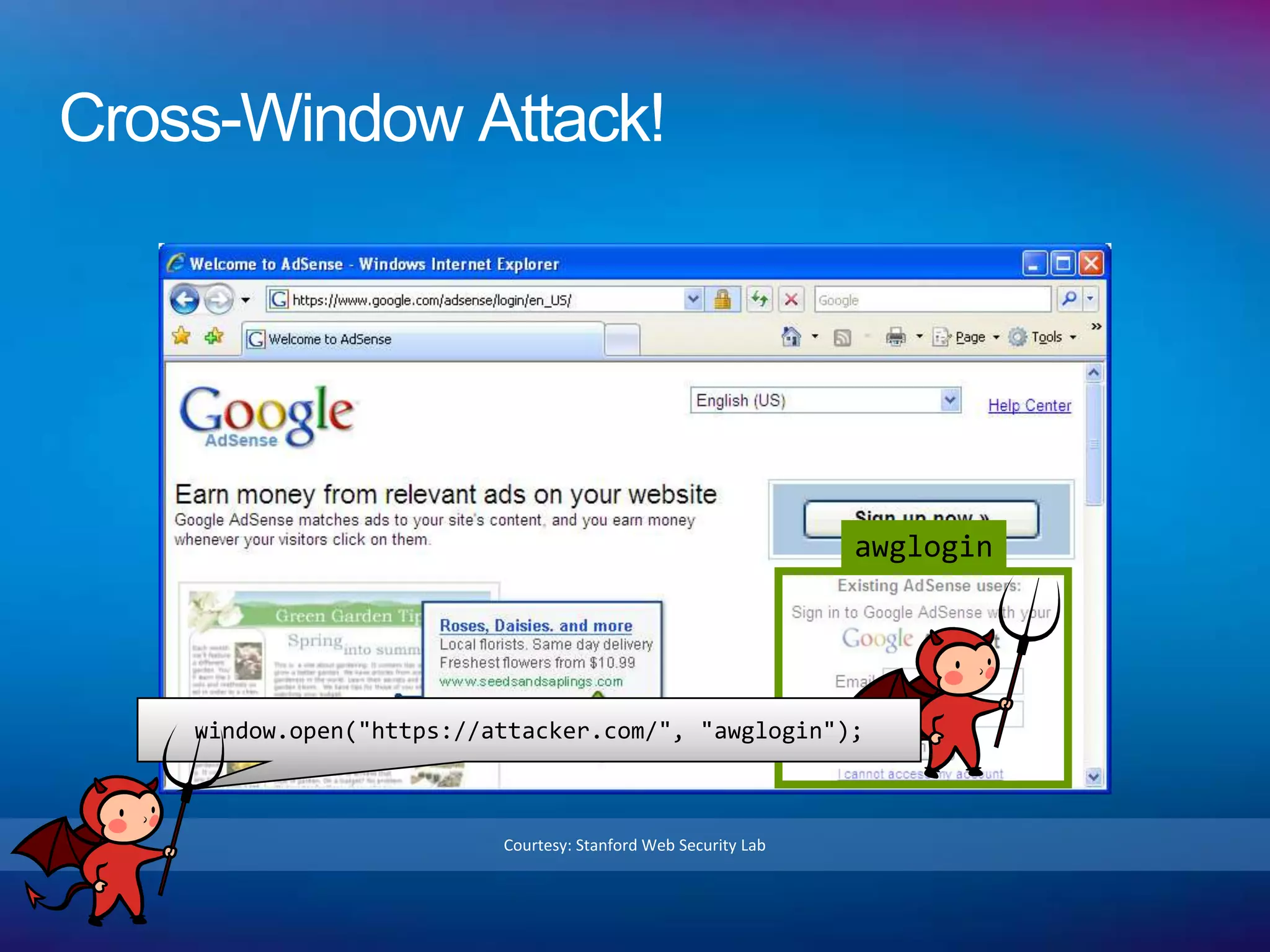
![Same-Window attack!
top.frames[1].location = "http://www.attacker.com/...";
top.frames[2].location = "http://www.attacker.com/...";
...
Courtesy: Stanford Web Security Lab](https://image.slidesharecdn.com/securewebmessaginginhtml5-120128232659-phpapp01/75/Secure-web-messaging-in-HTML5-11-2048.jpg)


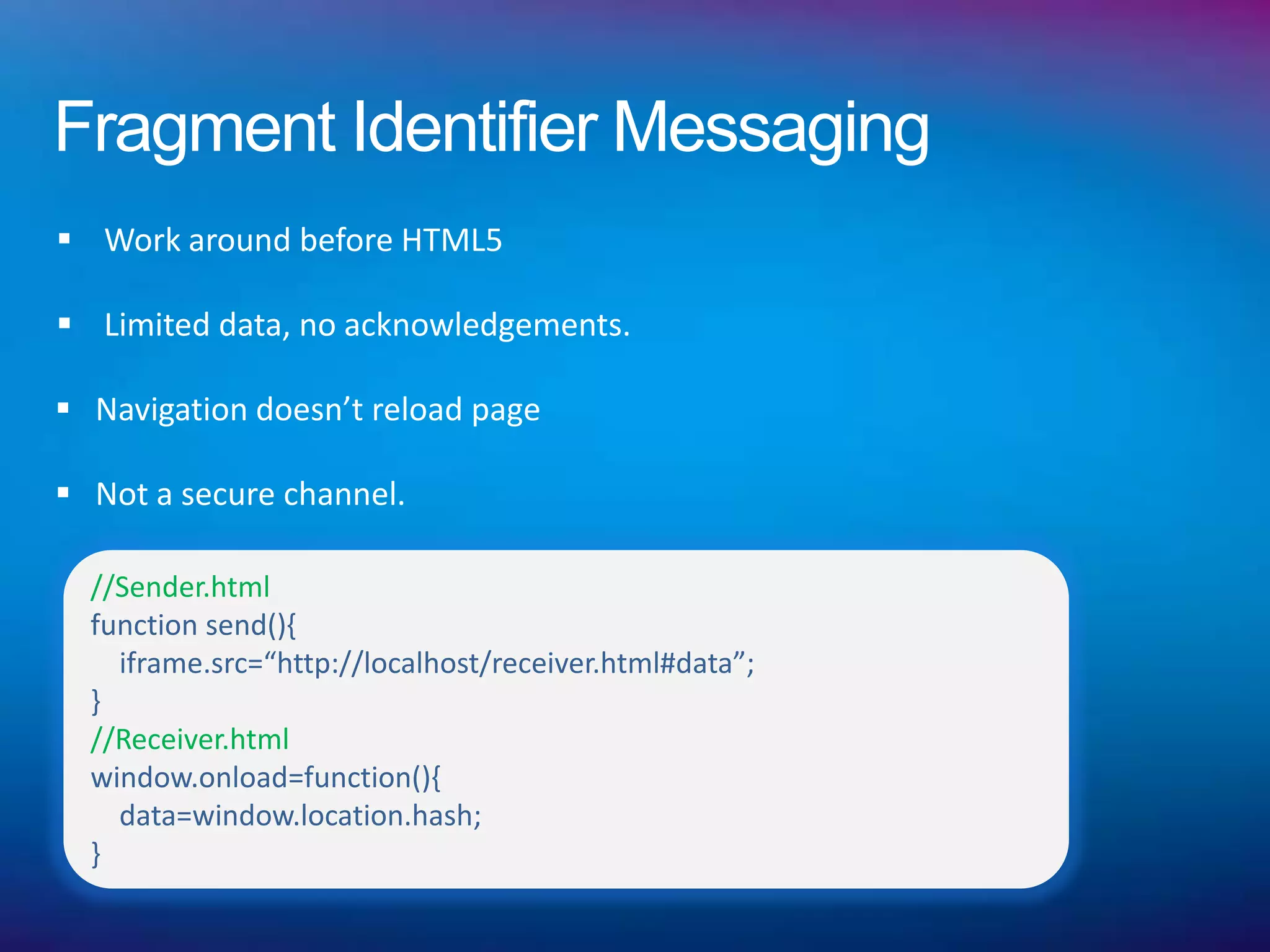
![HTML5 Post Message API
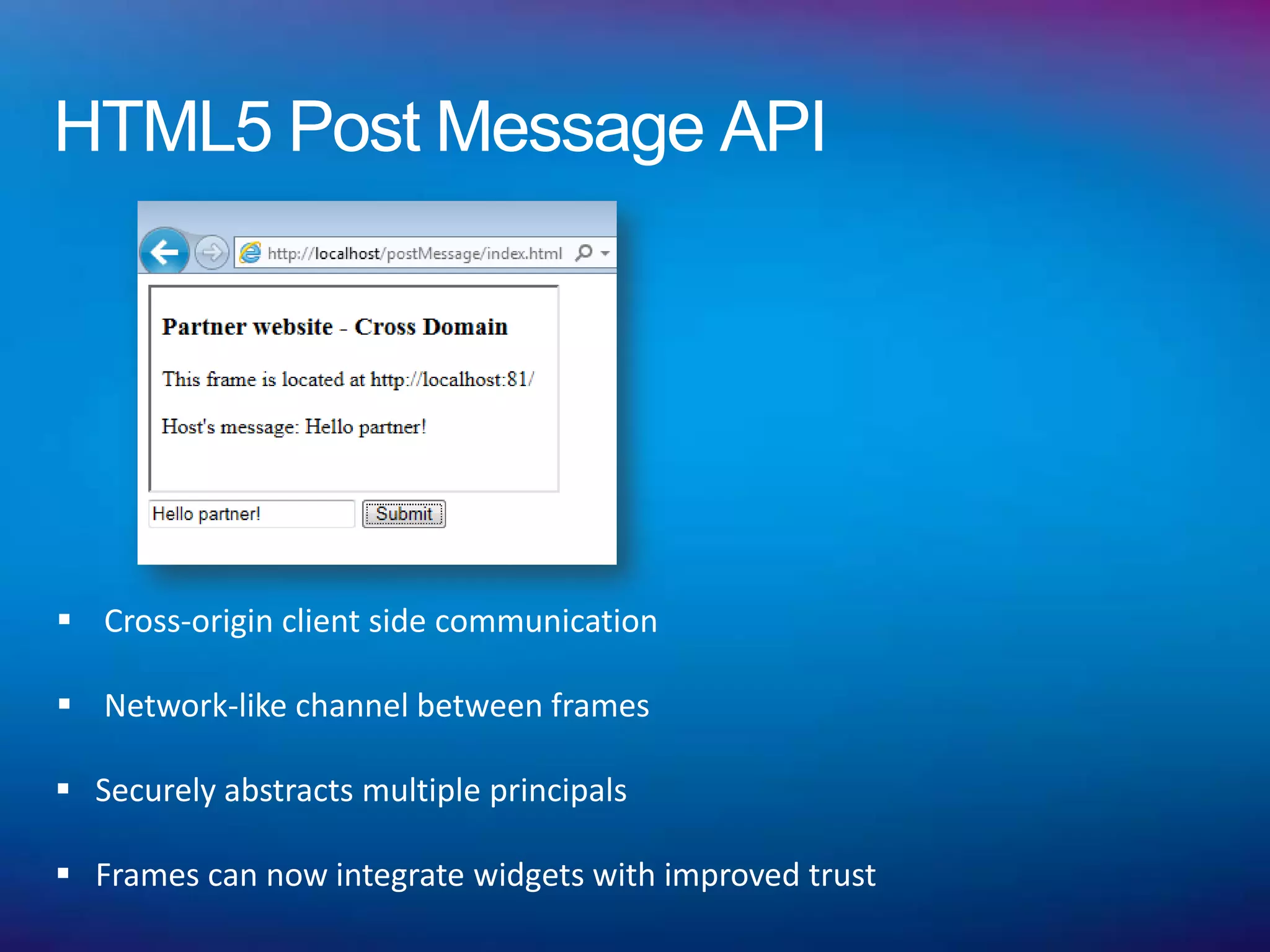
Syntax: otherwindow.postMessage(message, targetOrigin);
targetOrigin can be a trusted source or wild card *“*”+
//Posting message to a cross domain partner.
frames[0].postMessage(“Hello Partner!”, "http://localhost:81/");
//Retrieving message from the sender
window.onmessage = function (e) {
if (e.origin == 'http://localhost') {
//sanitize and accept data
}
};](https://image.slidesharecdn.com/securewebmessaginginhtml5-120128232659-phpapp01/75/Secure-web-messaging-in-HTML5-16-2048.jpg)