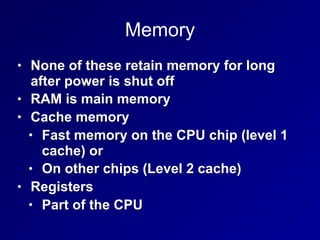
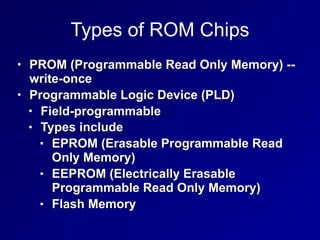
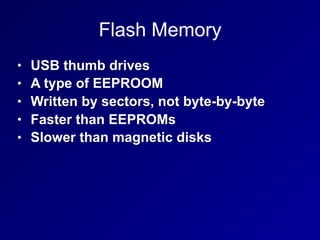
The document covers key topics related to asset security in information security, including data classification, ownership, data destruction, and security controls. It outlines the roles of various stakeholders such as data owners, custodians, and system owners in protecting sensitive information. The document also details methods for secure data handling, memory retention, and encryption practices.