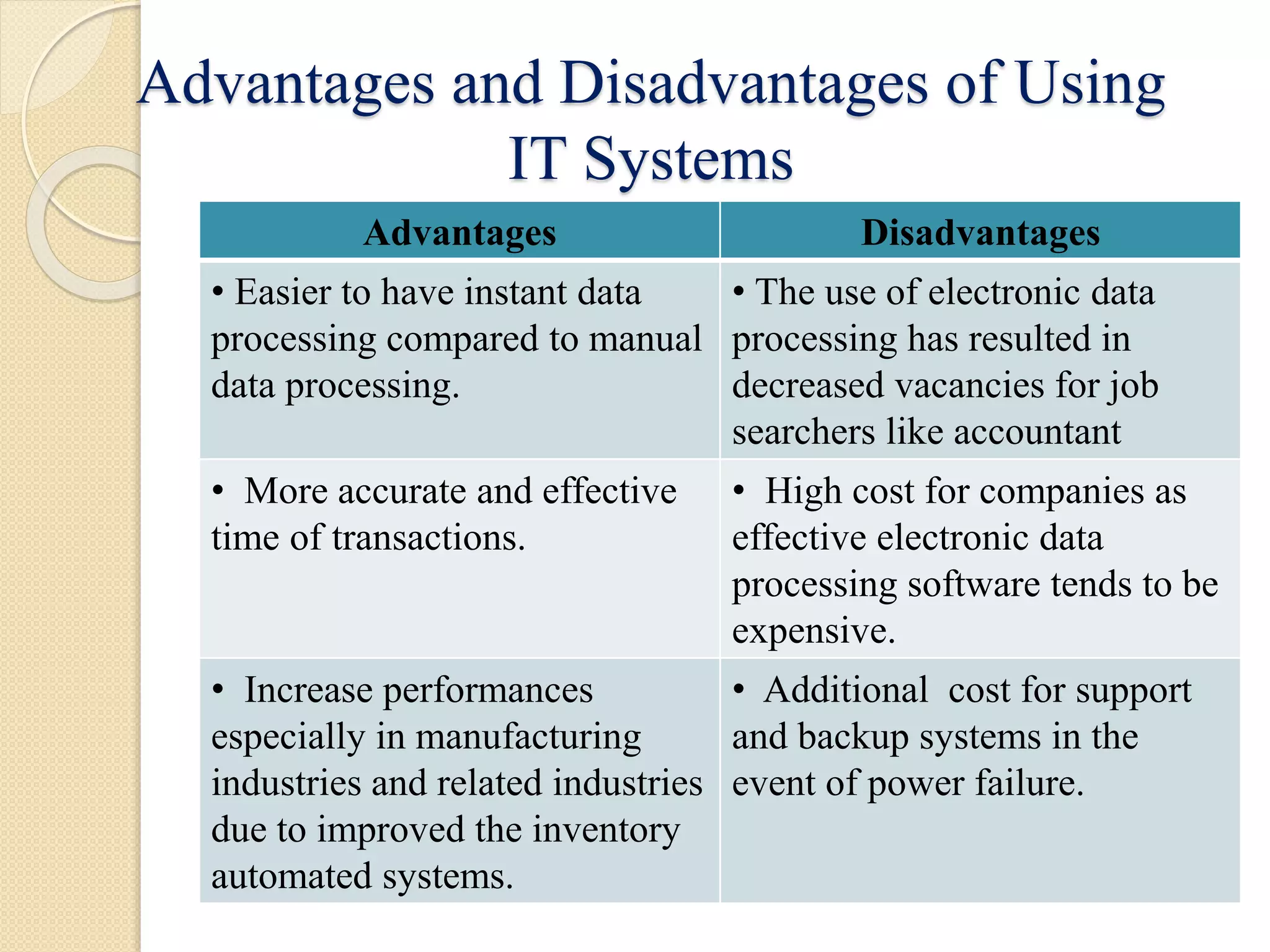
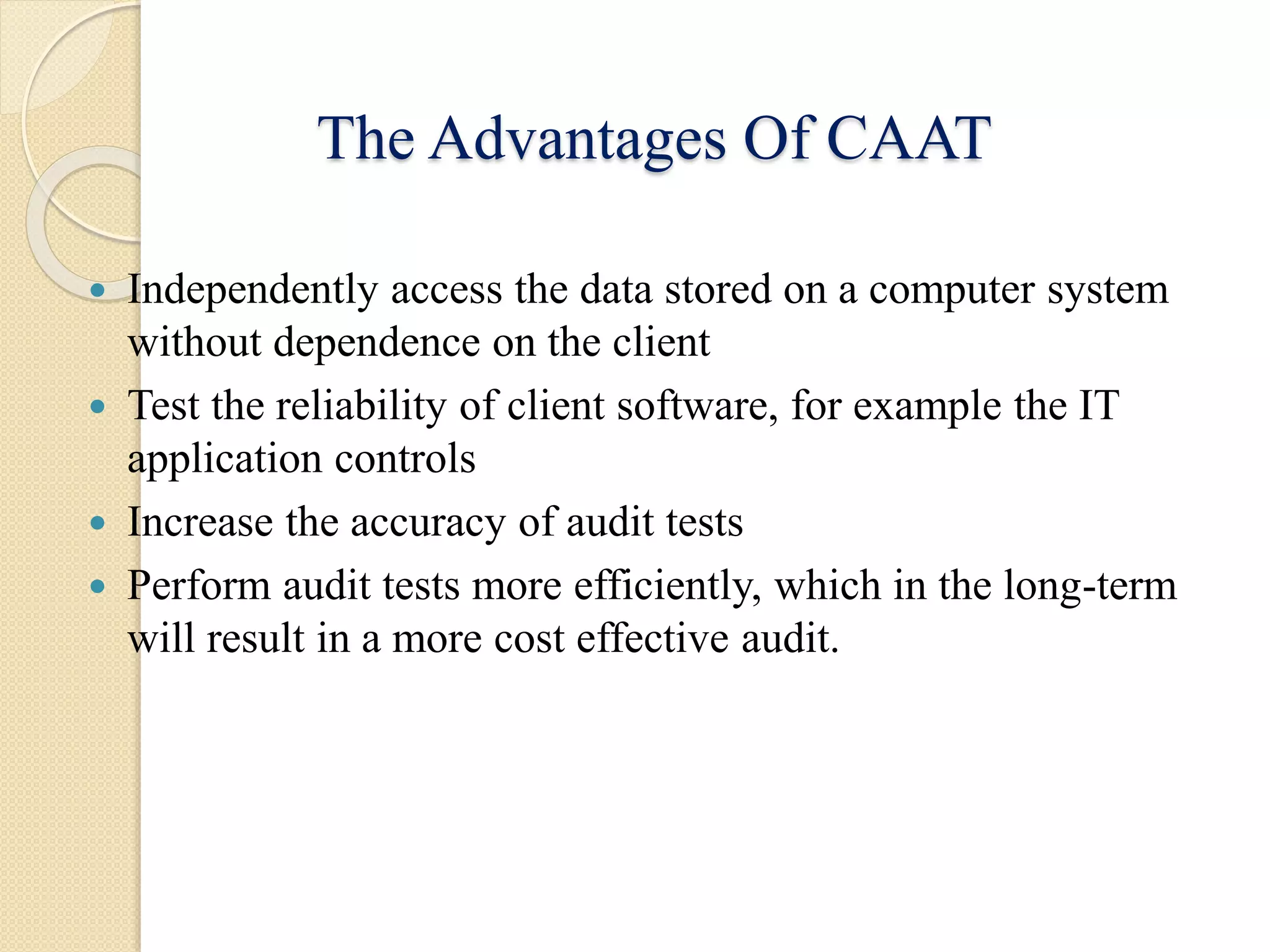
This document discusses auditing in a computerized information system environment. It begins by describing how information technology has changed accounting and auditing processes. Most companies now use IT to improve internal controls and processes like planning, recording, managing and reporting business transactions electronically. The document then discusses the implications of this transition from manual to electronic environments for auditors. It also describes different levels of complexity in computerized information systems, types of general and application controls, and methods for auditing computerized systems like auditing around or through the computer.