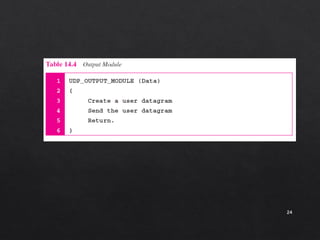
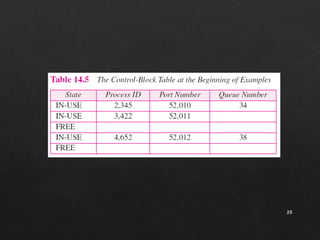
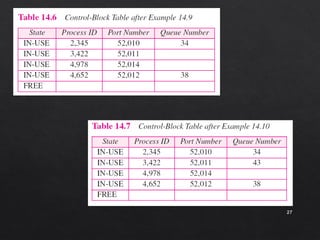
The document discusses the User Datagram Protocol (UDP). It provides the following key points:
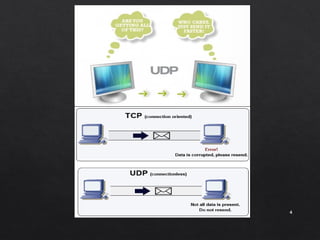
- UDP is an alternative to TCP that offers a limited connectionless datagram service for delivery of messages between devices on an IP network. It does not guarantee delivery, order of packets, or duplicate protection like TCP.
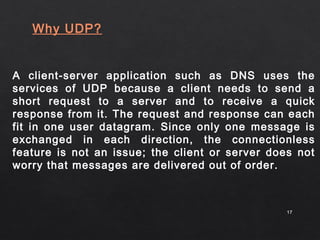
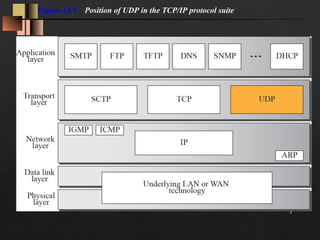
- UDP is commonly used for applications that require low latency and minimal processing time like DNS, SNMP, and streaming media. These applications can tolerate some data loss since reliability is not critical.
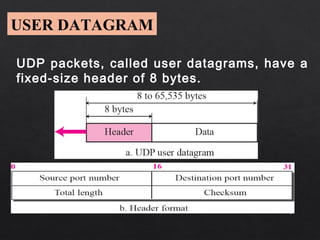
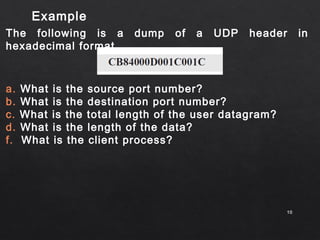
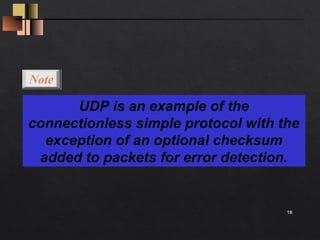
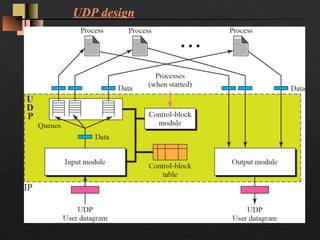
- The UDP header is only 8 bytes, containing source/destination port numbers and length fields. It provides an optional checksum for error detection but no other reliability mechanisms.




![Applications
Numerous key Internet applications use UDP, including: the
Domain Name System (DNS), where queries must be fast and
only consist of a single request followed by a single reply
packet, the Simple Network Management Protocol (SNMP),
the Routing Information Protocol (RIP)[2] and the Dynamic Host
Configuration Protocol (DHCP).
Voice and video traffic is generally transmitted using UDP
many businesses are finding that a recent increase in UDP
traffic from these real-time applications is hindering the
performance of applications using TCP, such as point of sale,
accounting, and database systems. When TCP detects packet
loss,
88](https://image.slidesharecdn.com/udpseminar-141126033559-conversion-gate01/85/User-Datagram-protocol-For-Msc-CS-8-320.jpg)