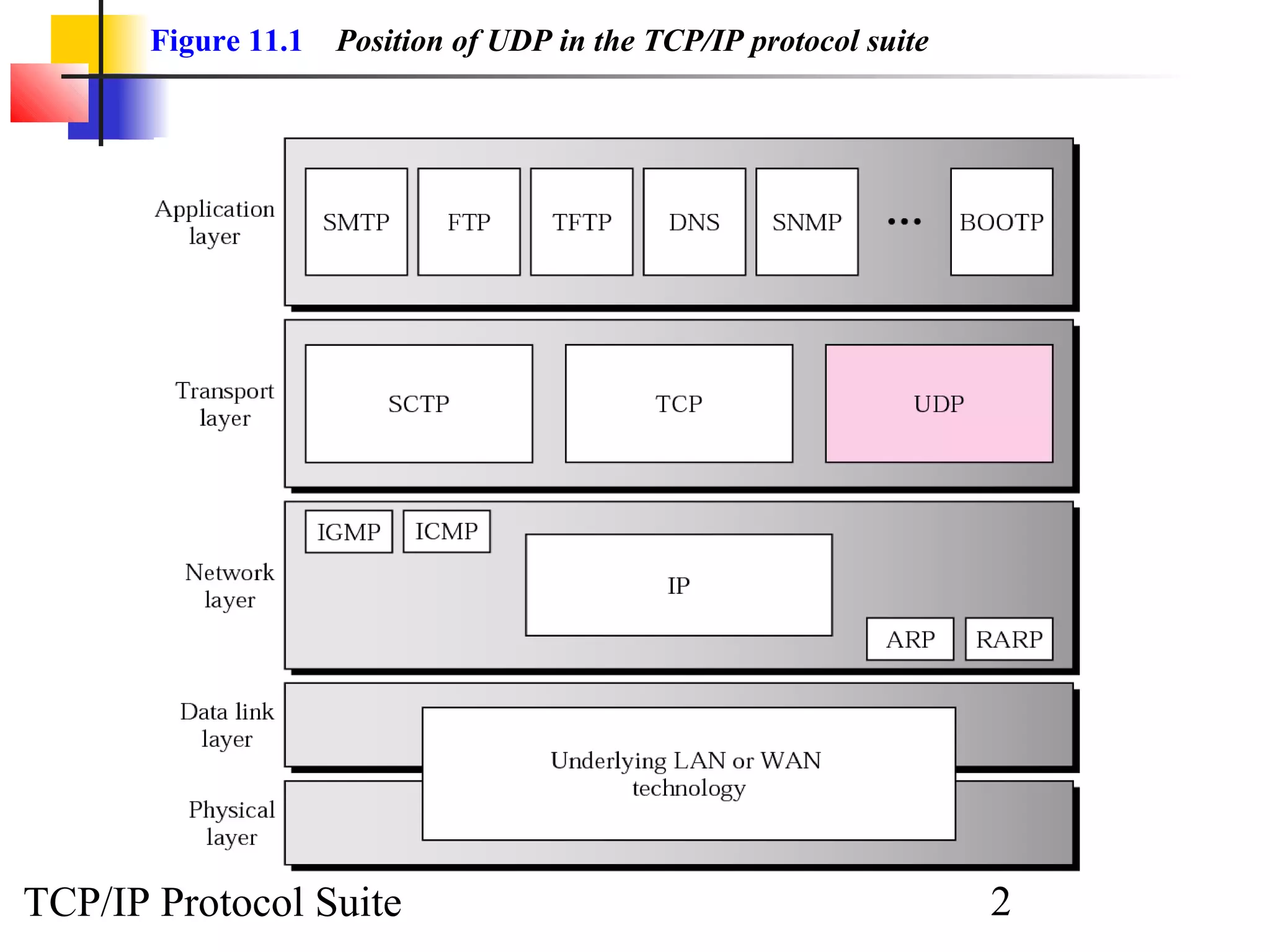
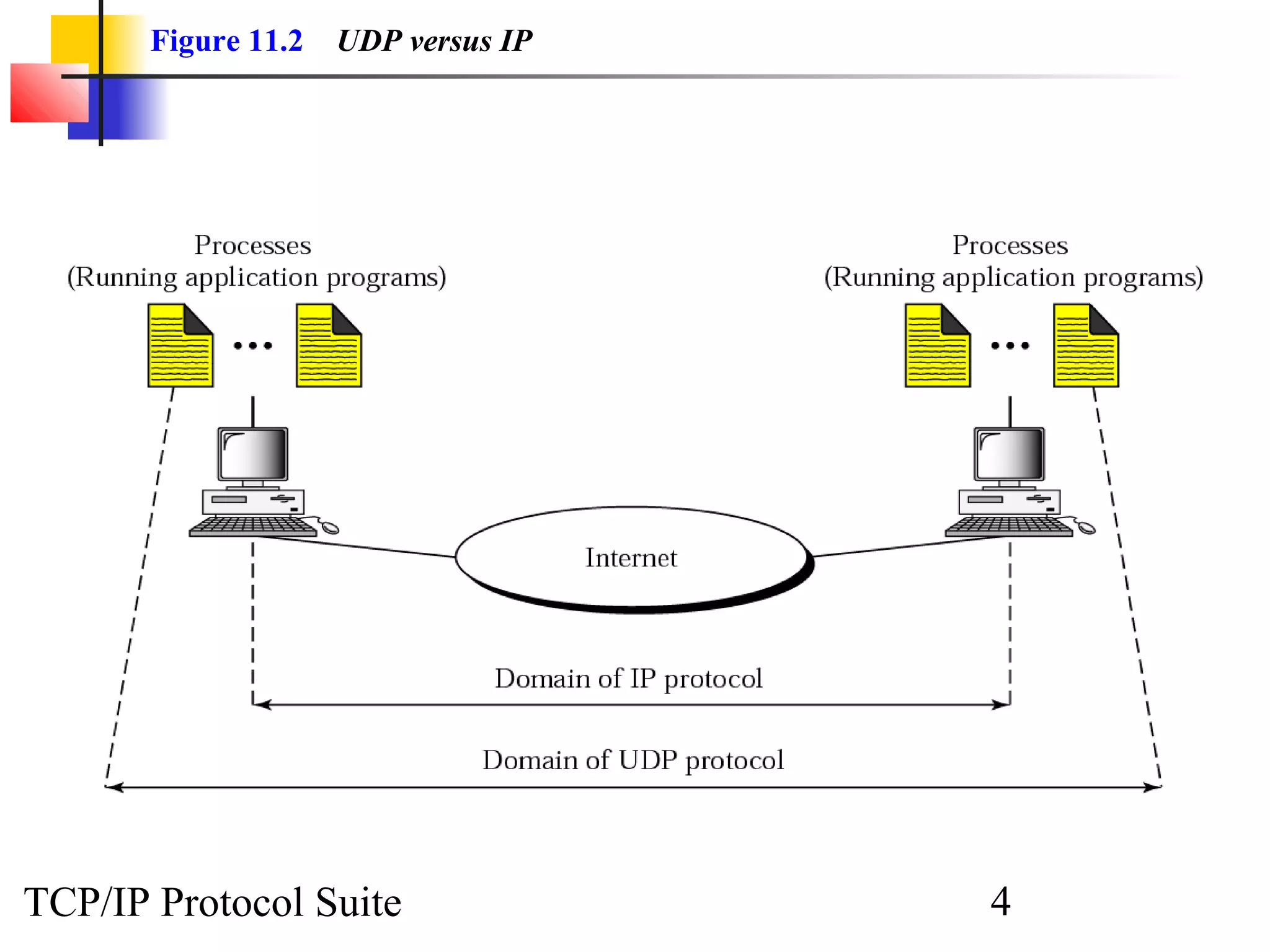
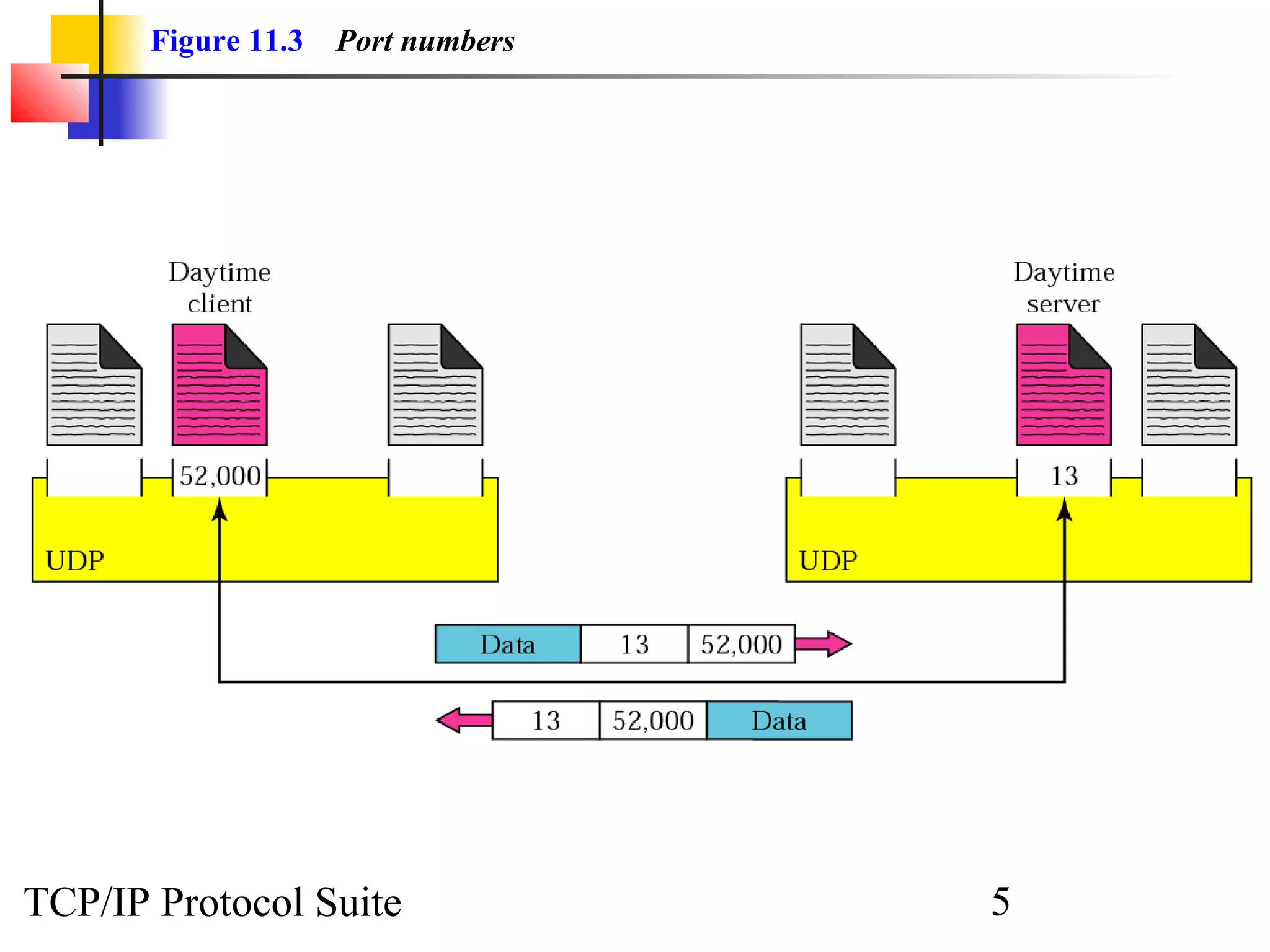
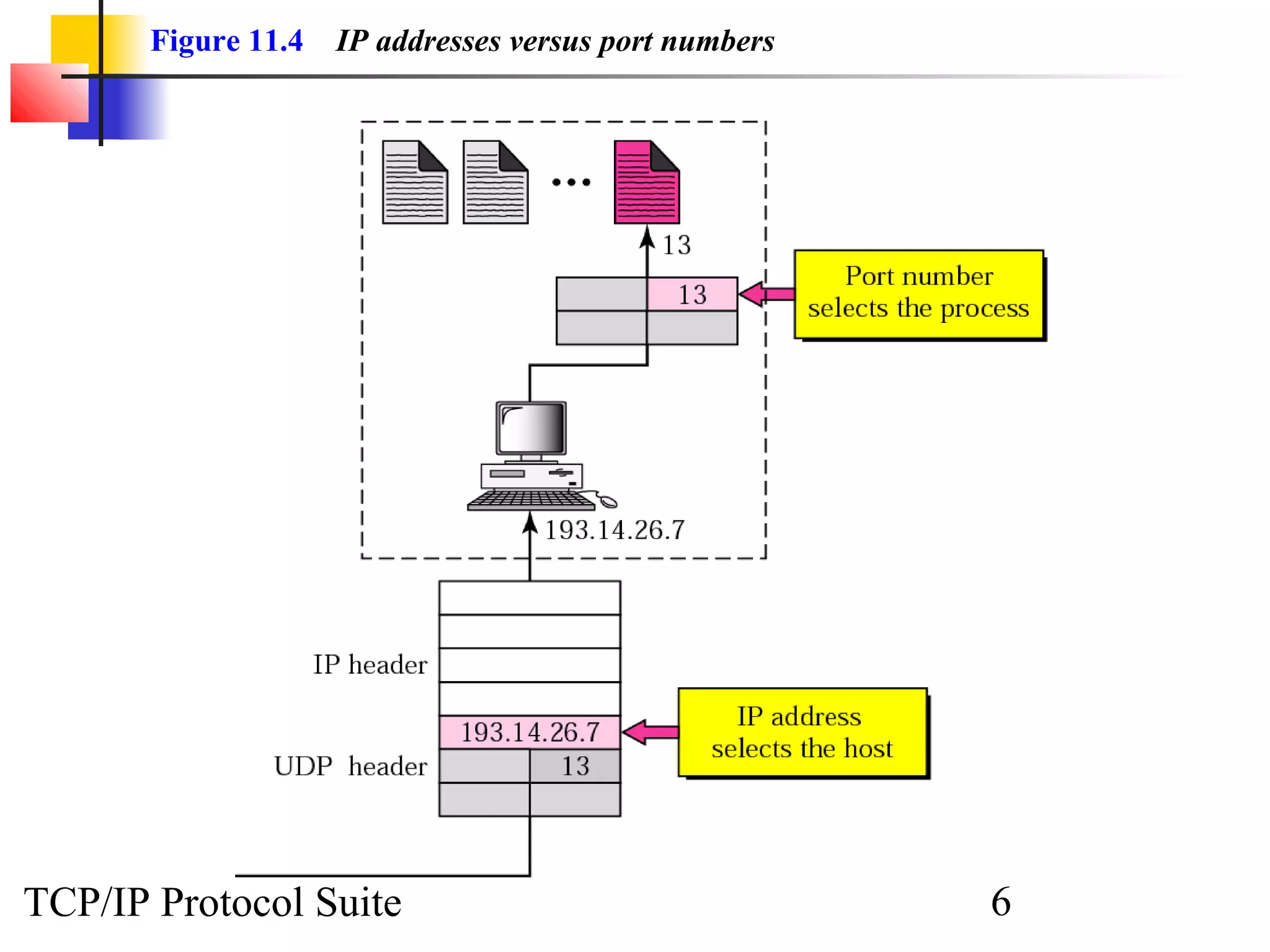
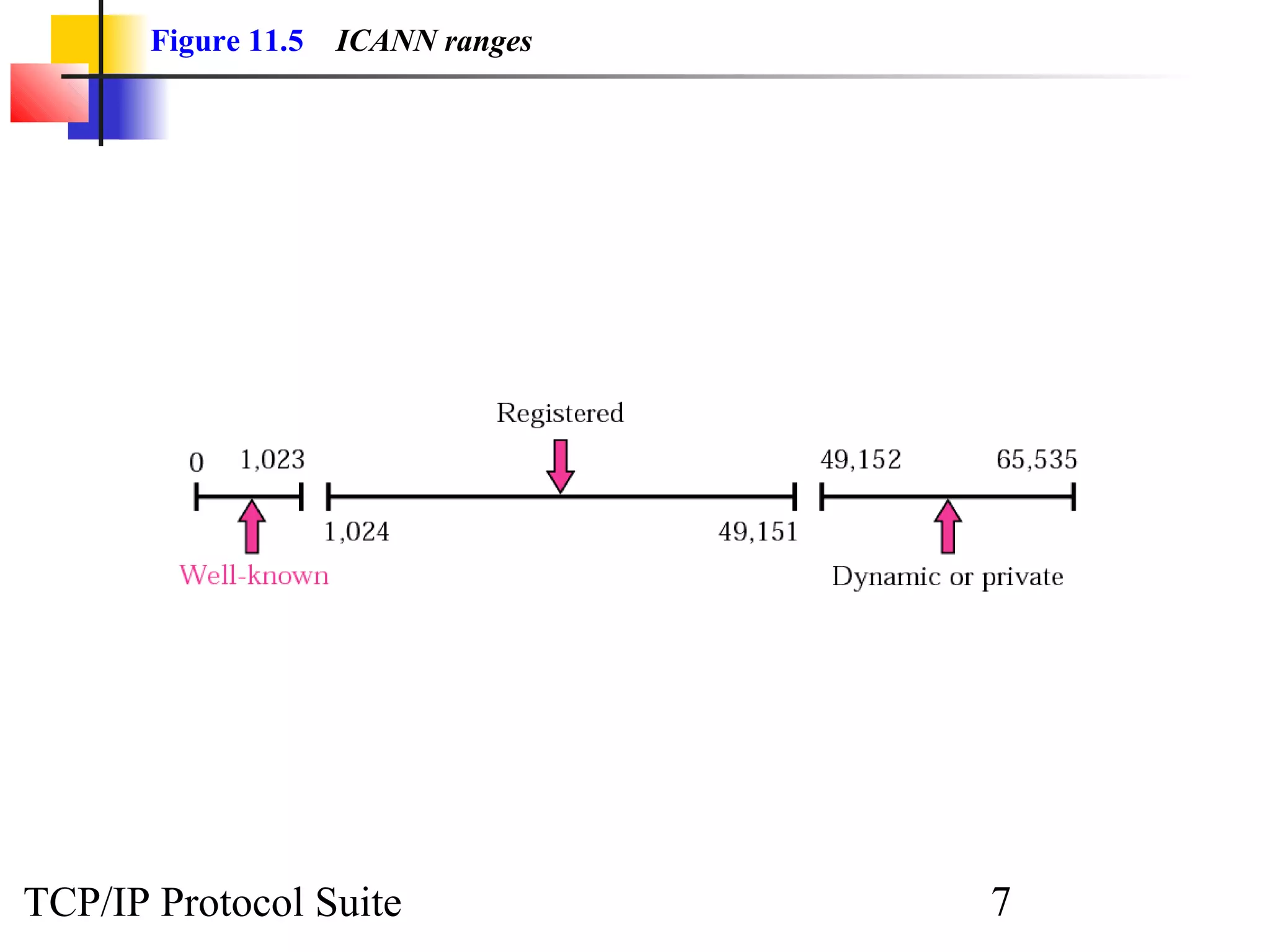
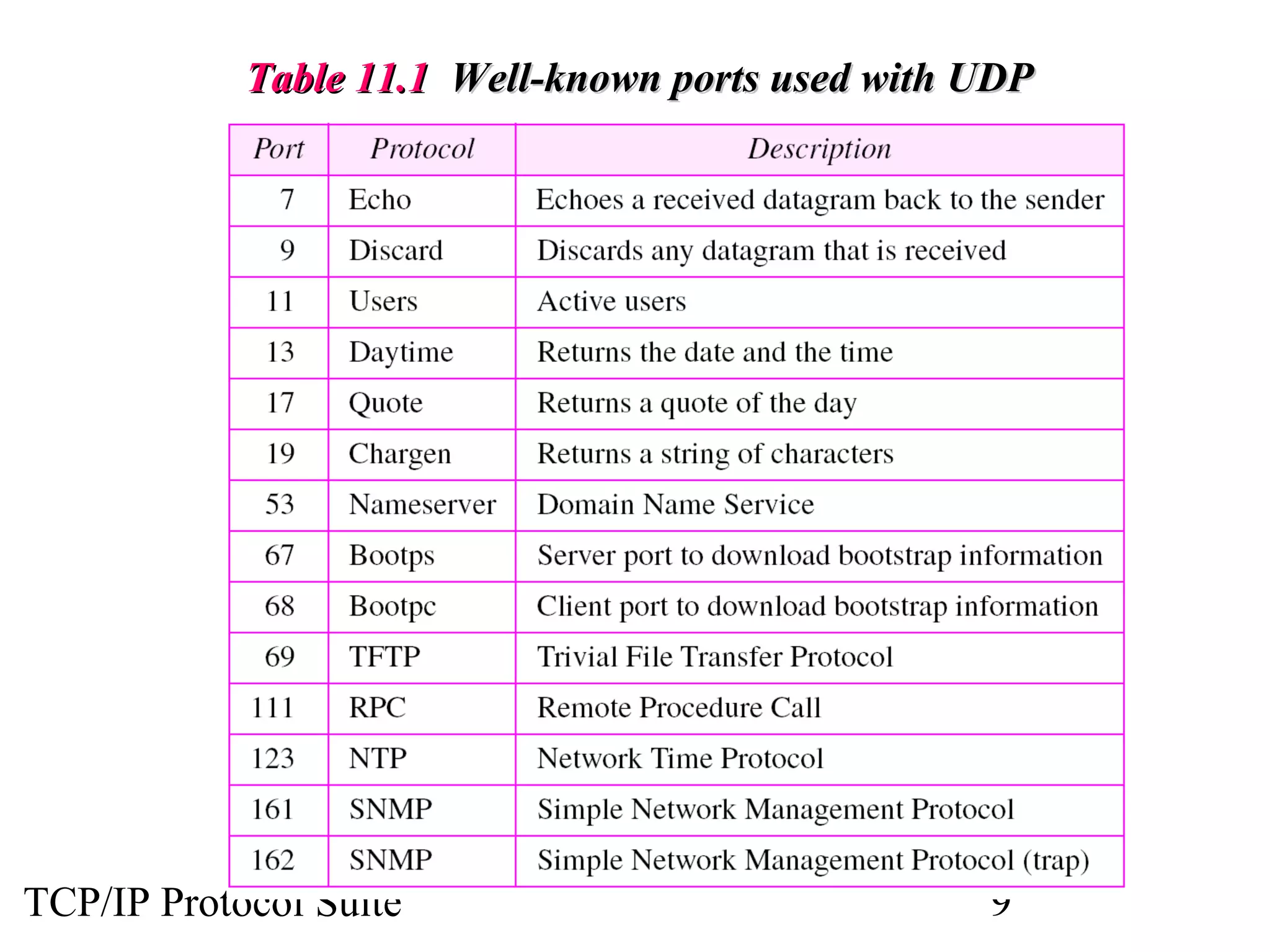
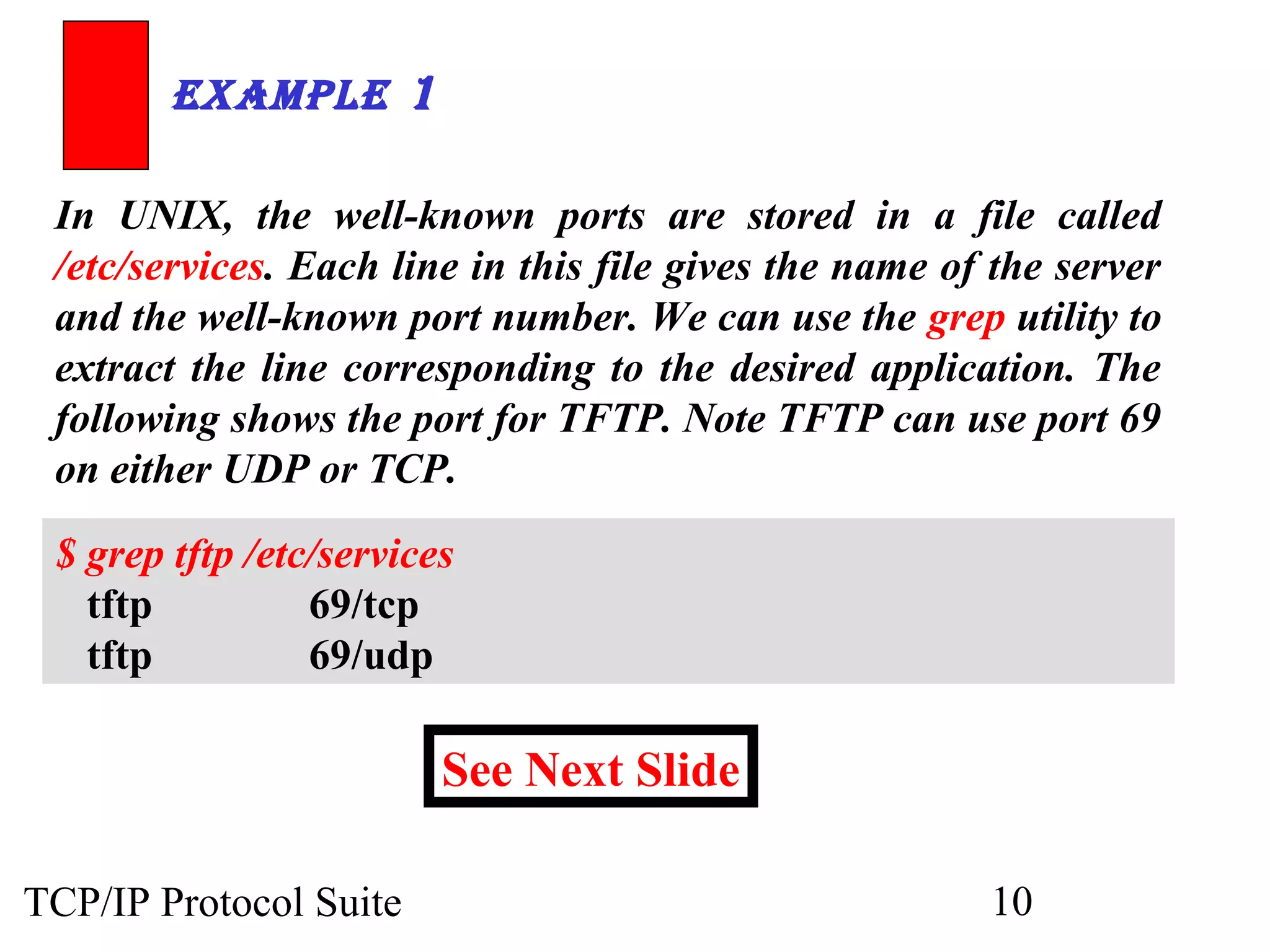
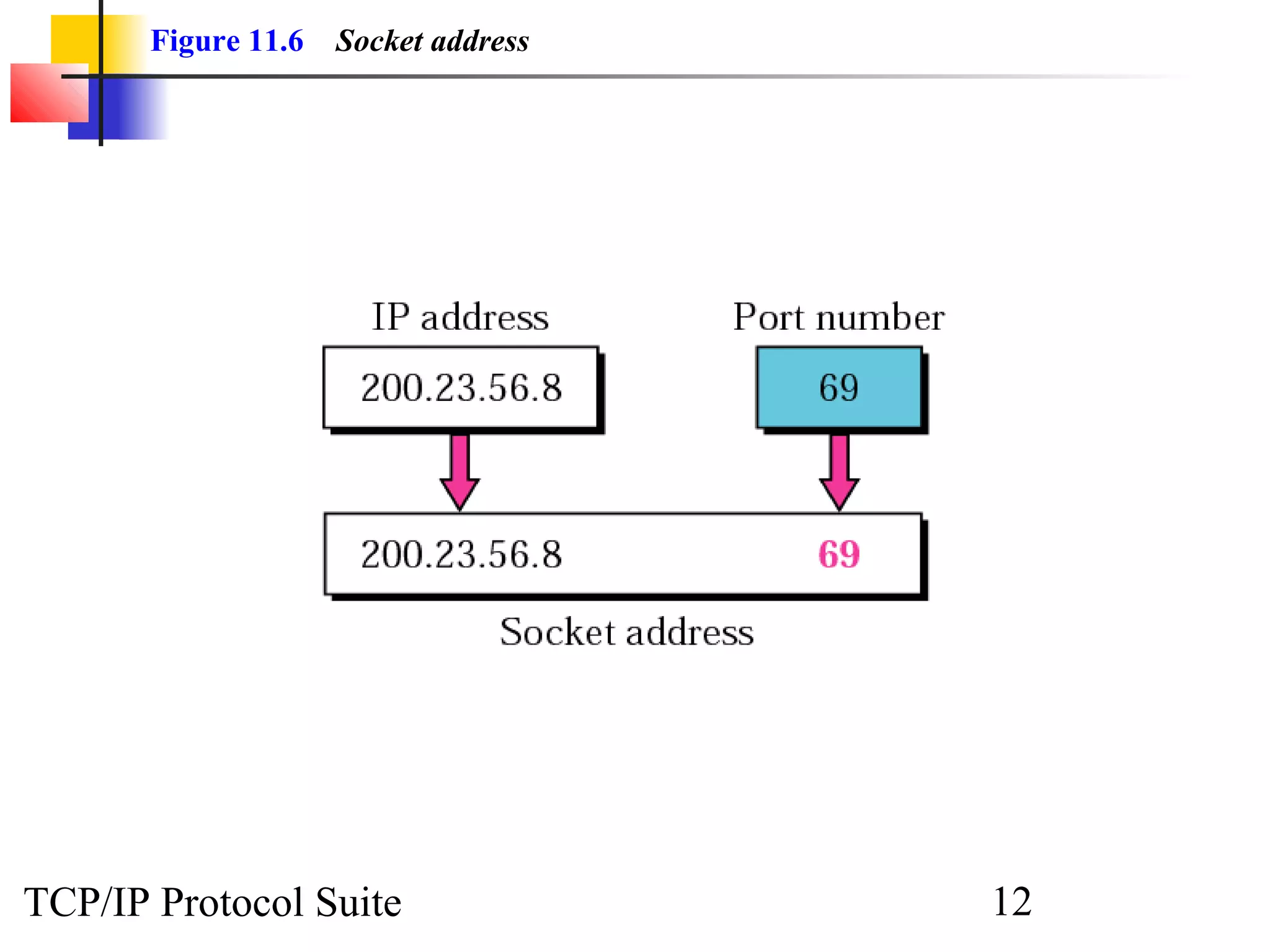
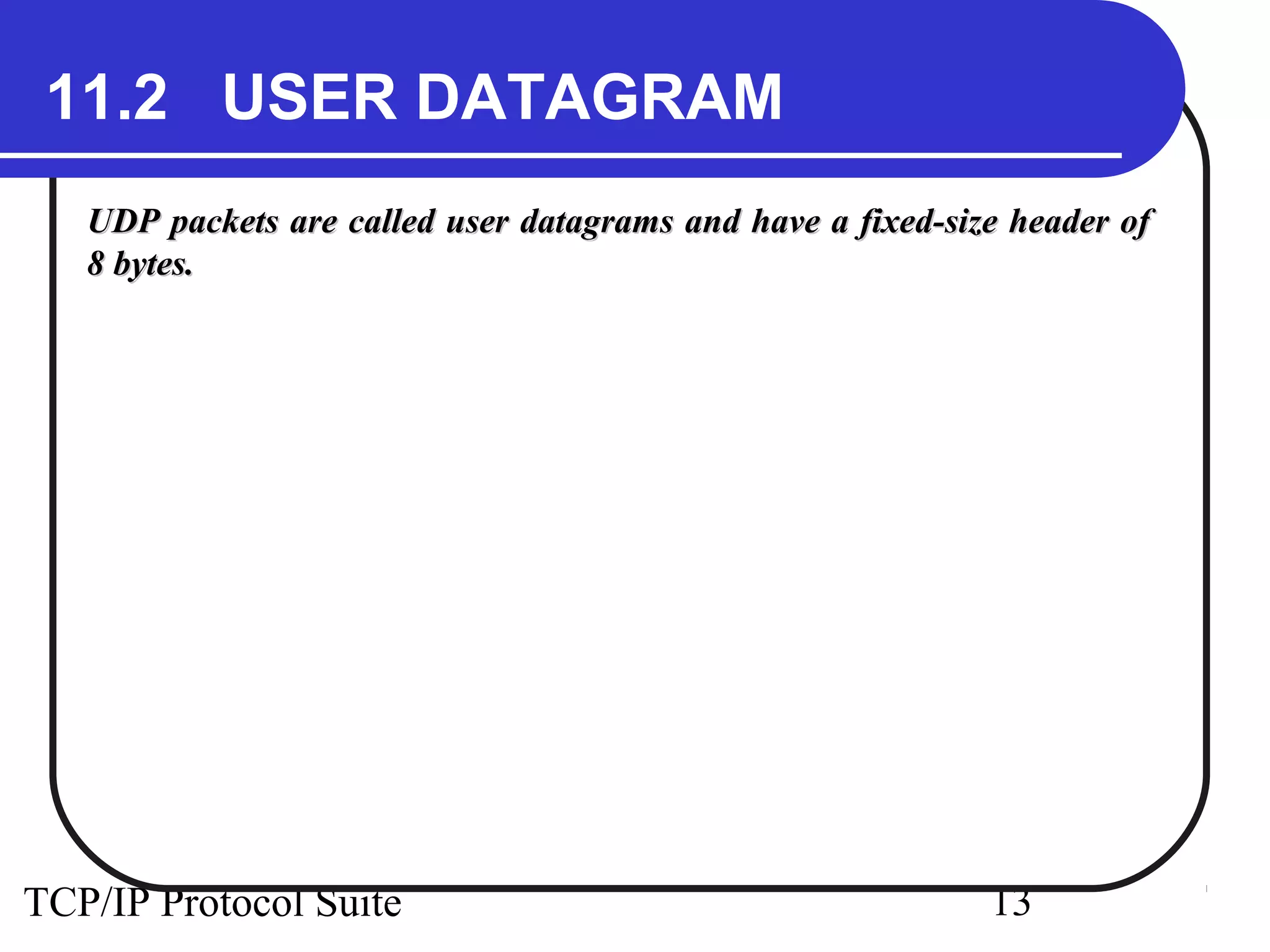
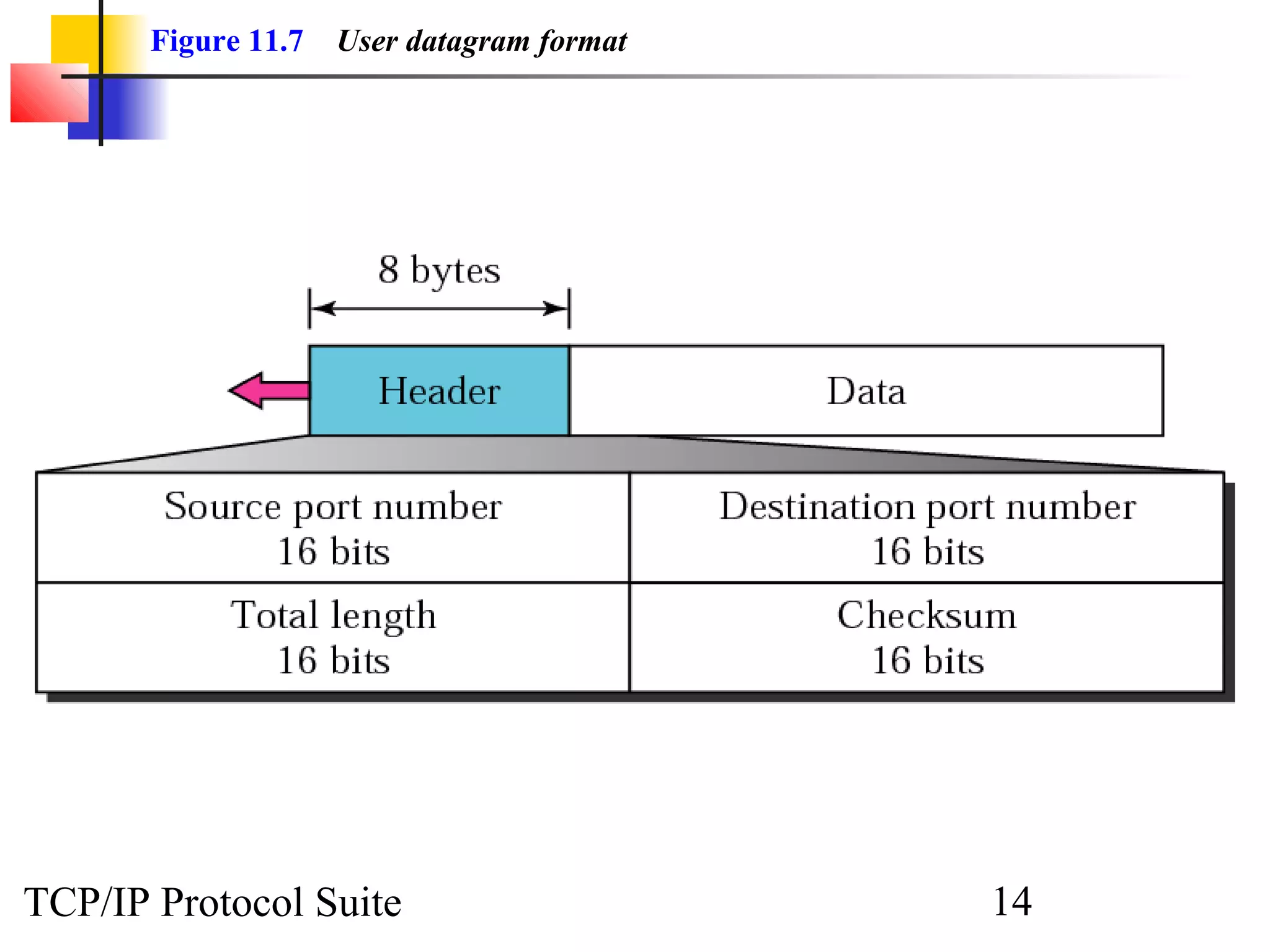
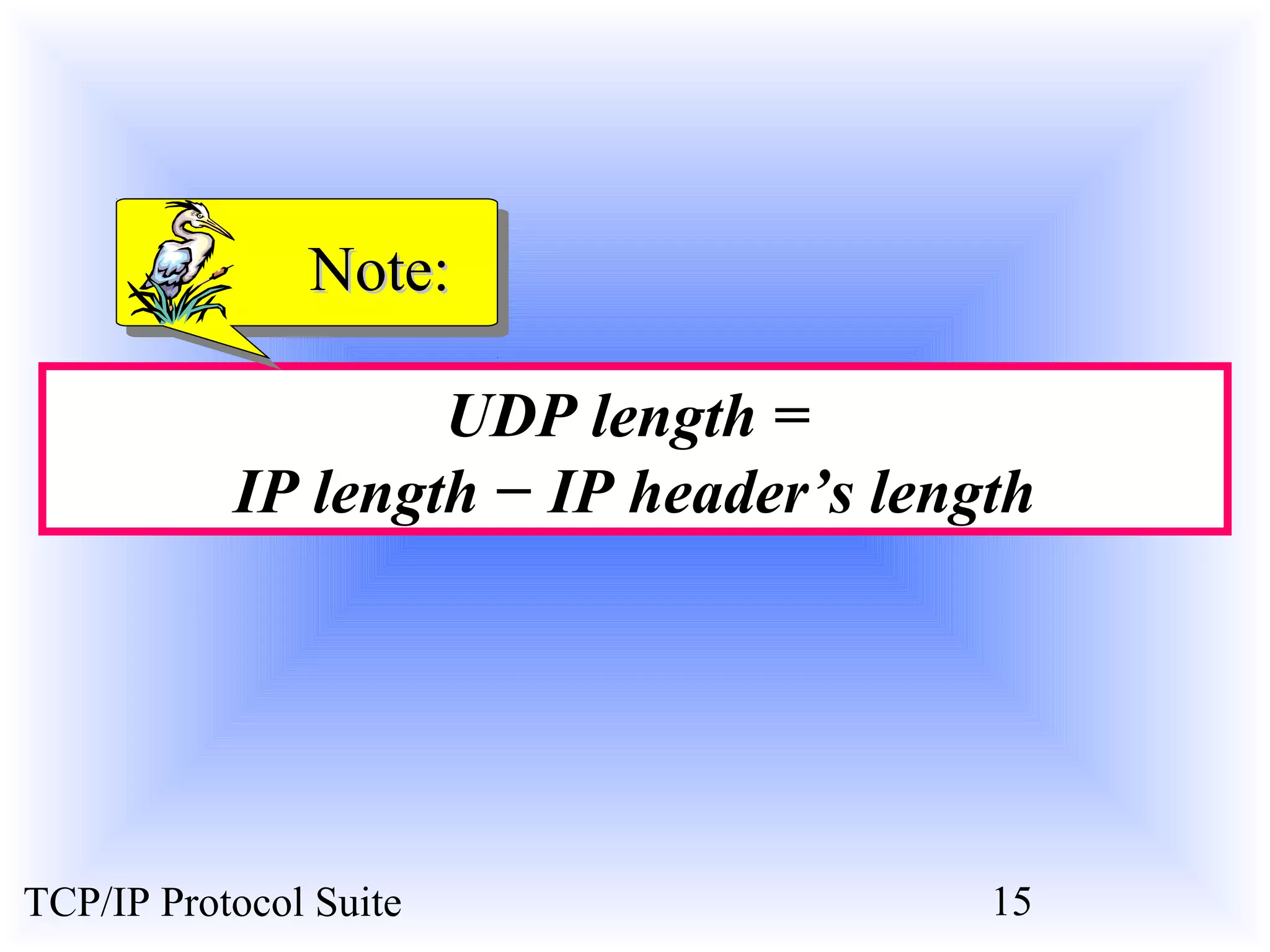
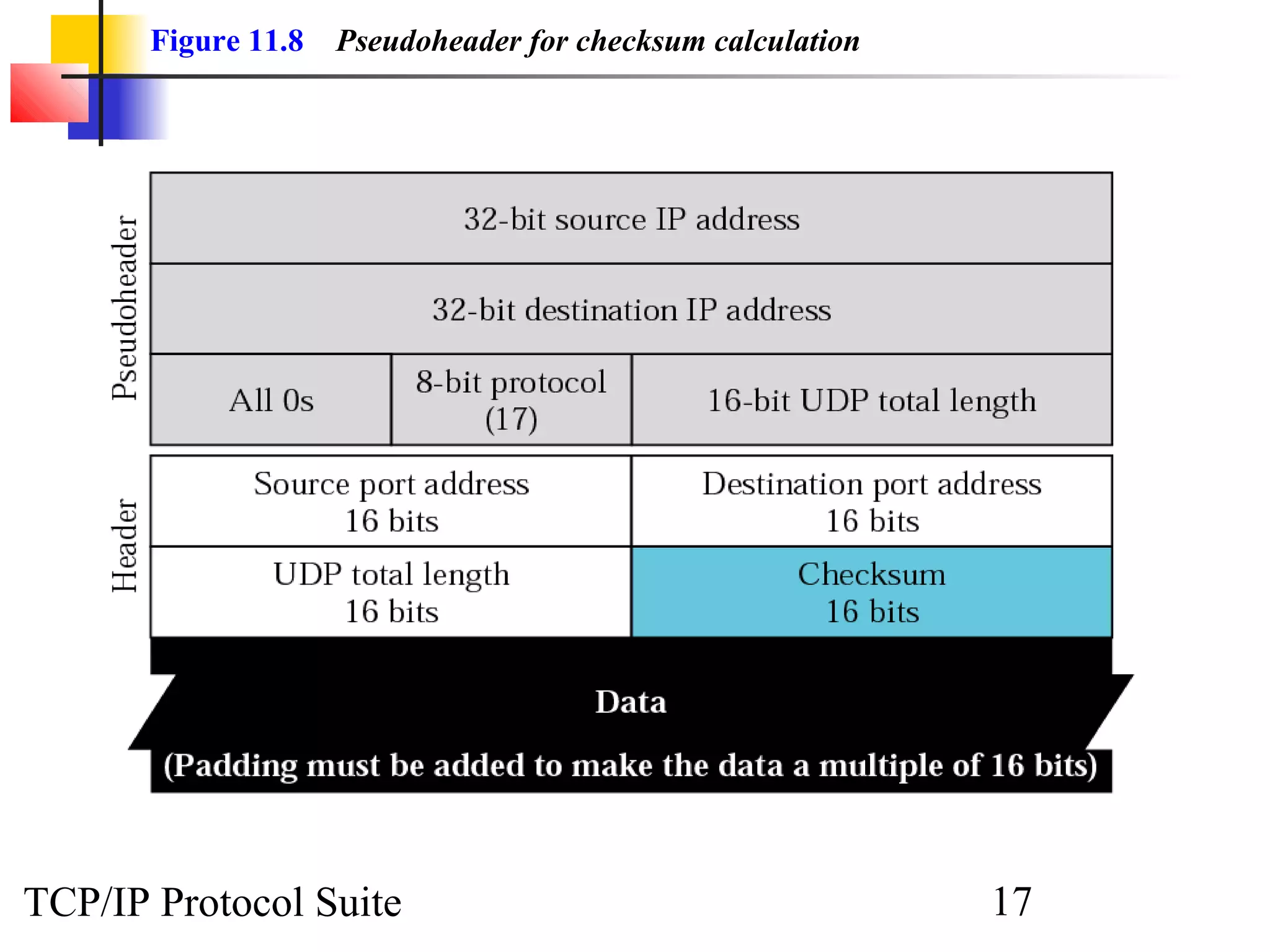
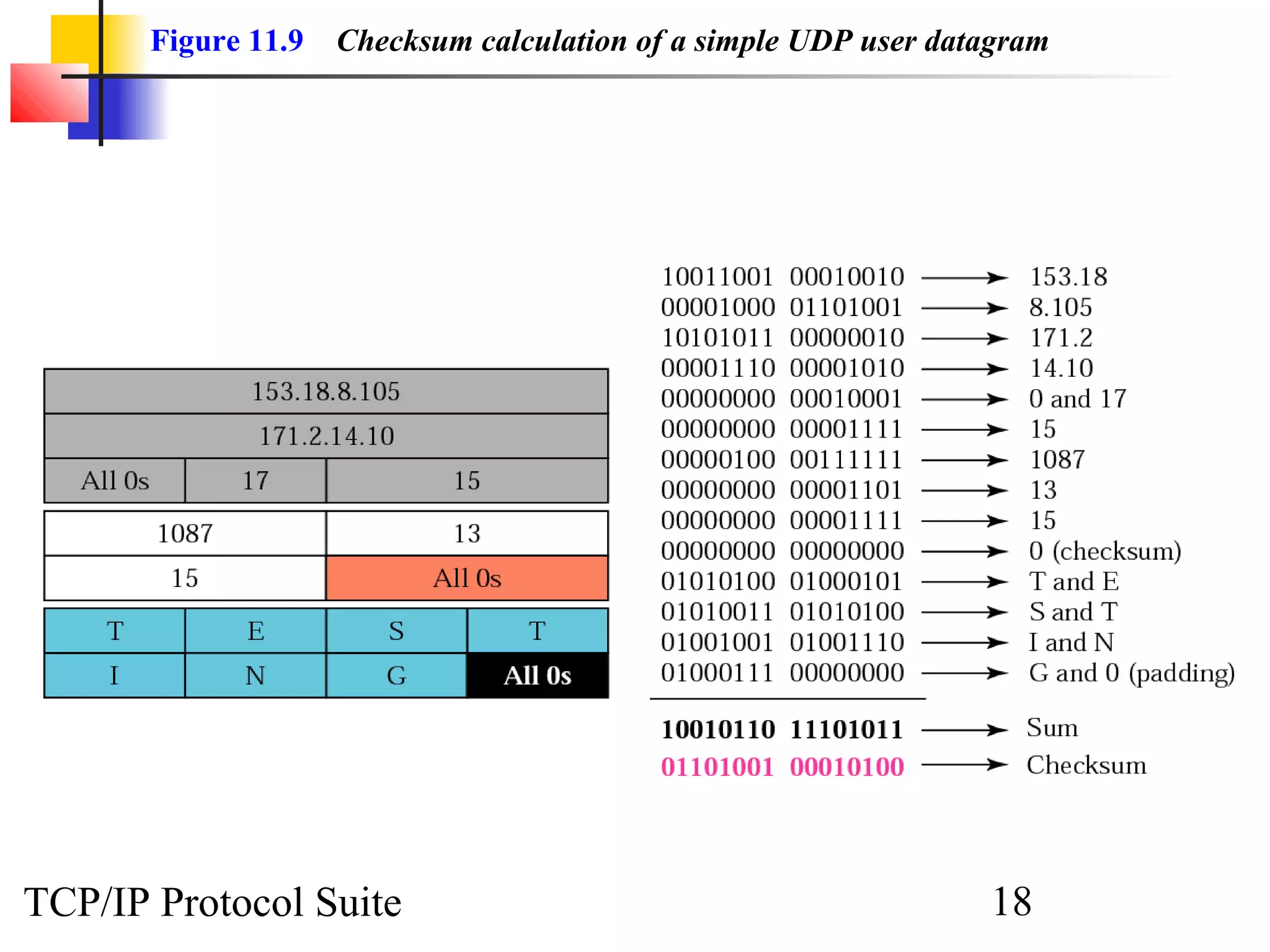
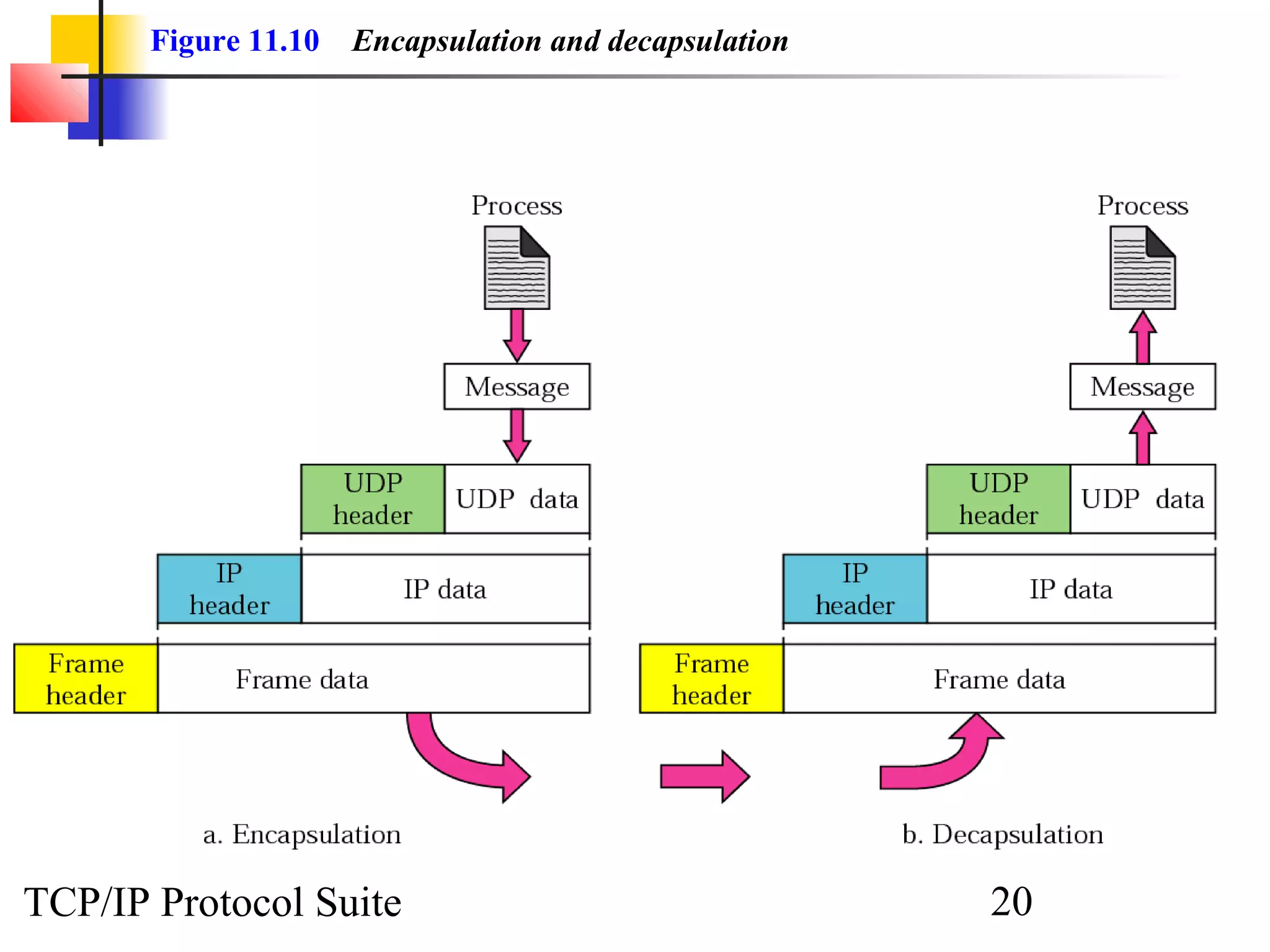
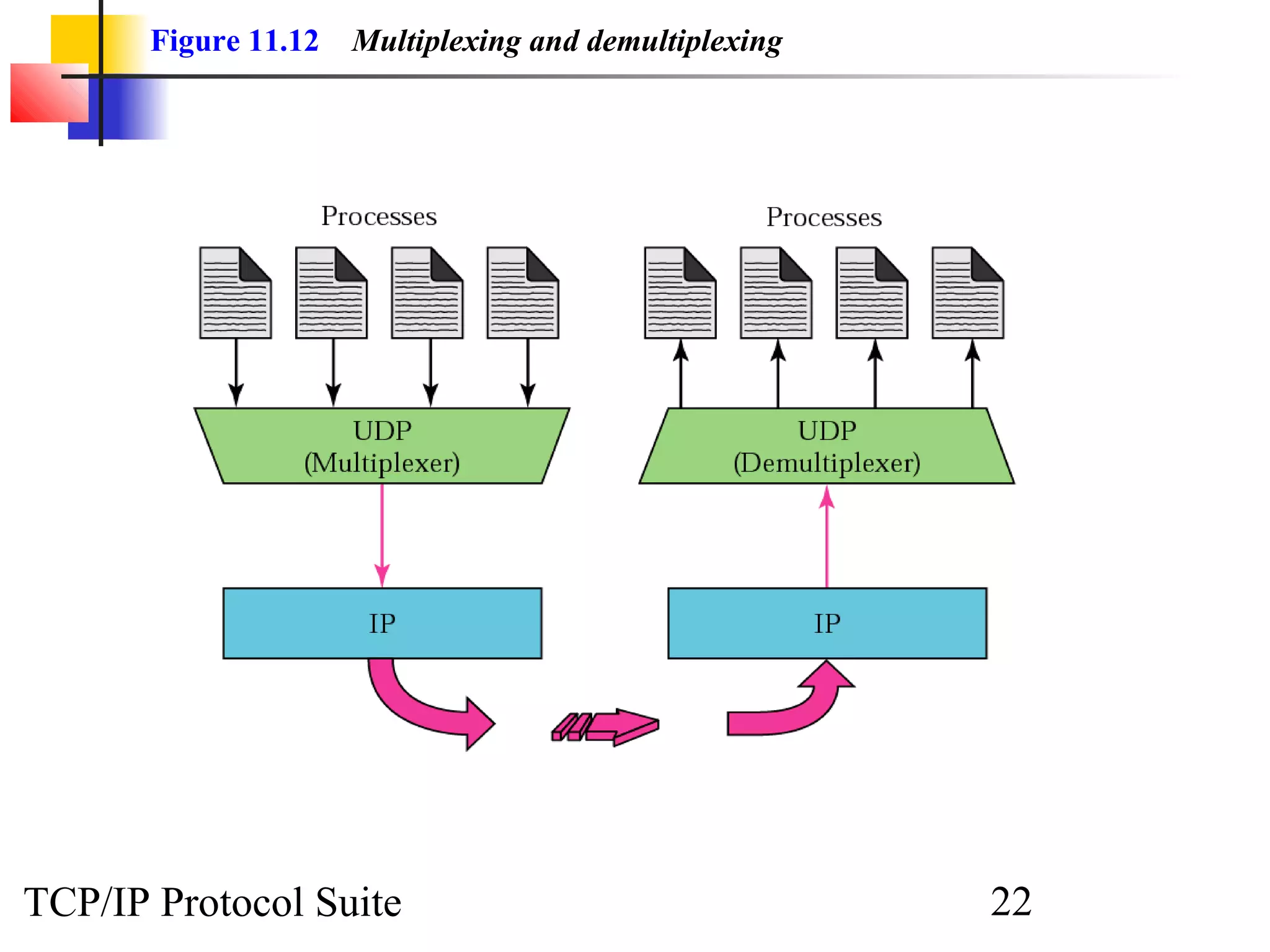
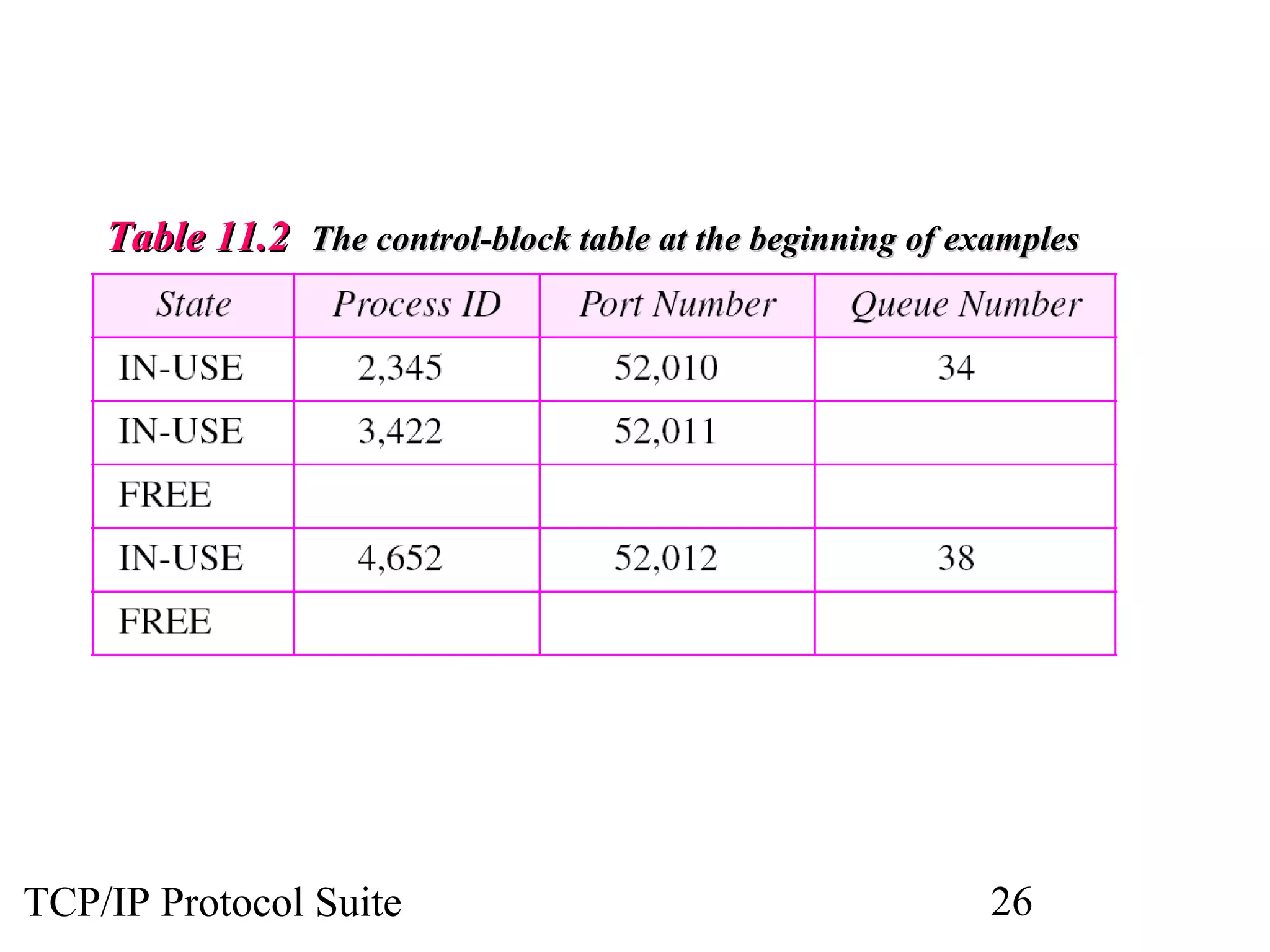
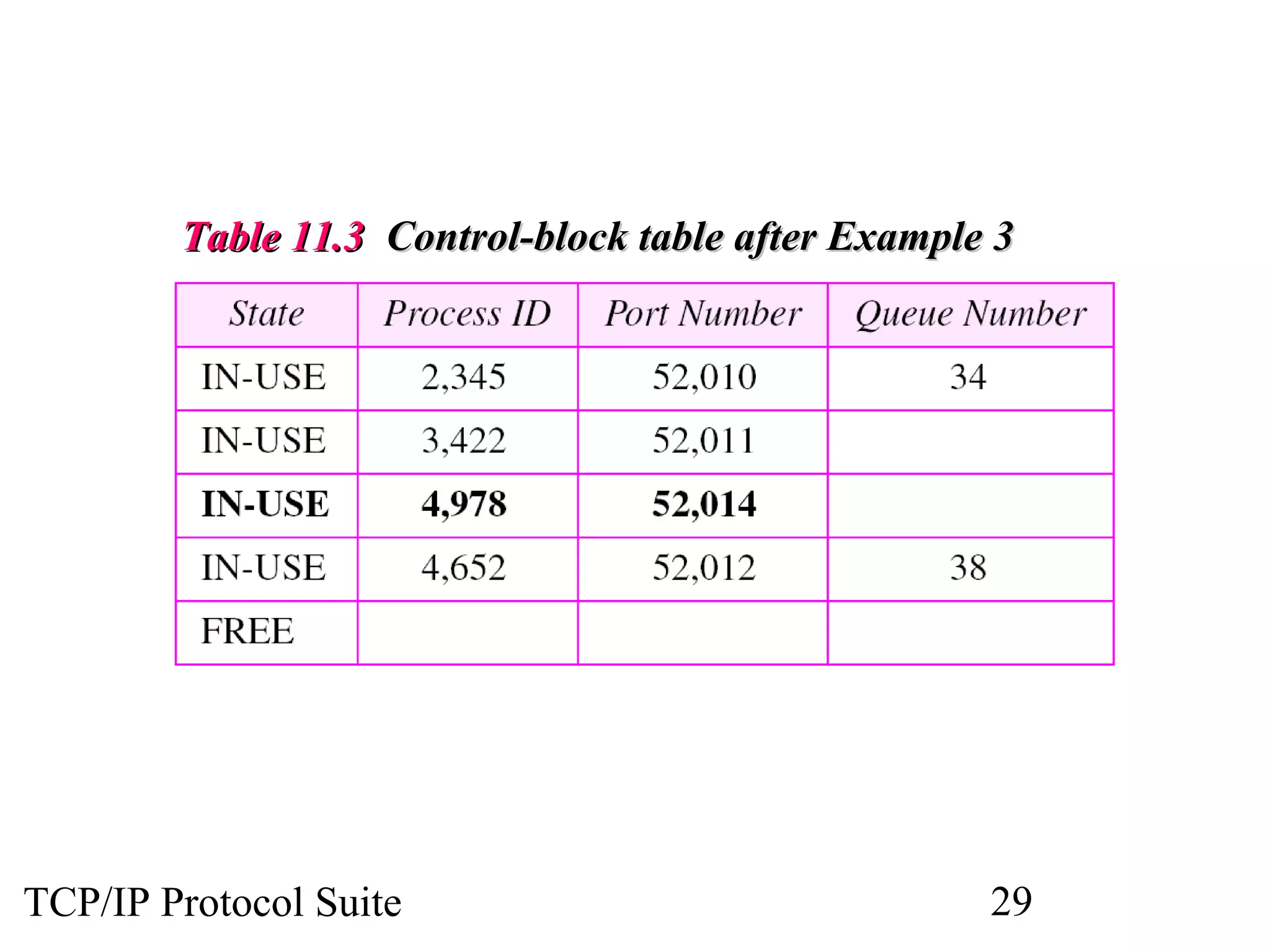
This document discusses the User Datagram Protocol (UDP) which provides connectionless and unreliable data transmission between applications. It covers UDP packet formats, checksum calculation, operation including encapsulation and multiplexing, appropriate uses of UDP, and the modules involved in a UDP implementation including control blocks, input/output queues, and tables. Examples are provided to illustrate how UDP handles packet reception and association with processes.