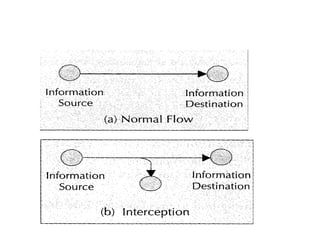
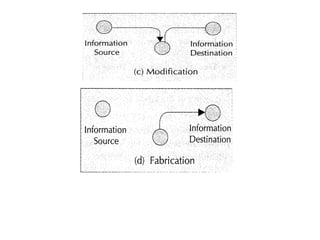
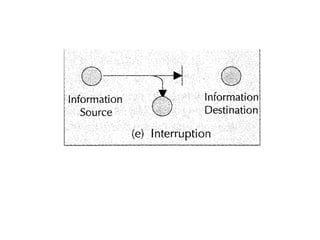
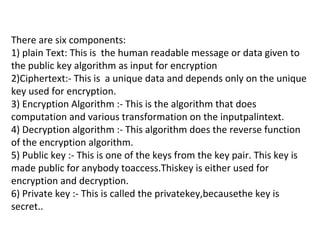
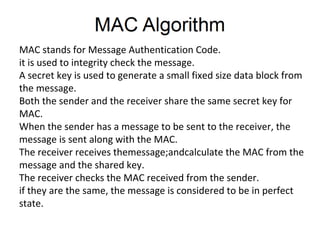
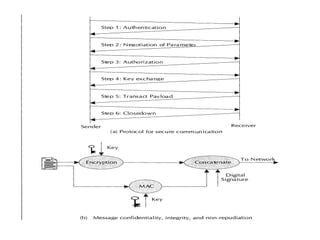
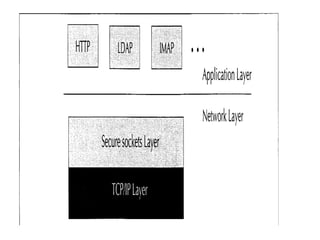
This document discusses security issues related to mobile technology. It begins by explaining the importance of understanding threats when building a security system. It then discusses different types of attacks like interception, modification, and interruption that can target both static and dynamic assets. The document also covers security concepts like confidentiality, integrity, authorization, and availability. It explains symmetric and asymmetric encryption techniques as well as protocols like SSL, TLS, and WTLS that use these techniques to securely transmit data over networks.
![Security Issues in Mobile
Technology
•presented By: -
Parmar Pallavi[112343].
Solanki Urmi[112324].](https://image.slidesharecdn.com/112324112343securityissu-150511124411-lva1-app6891/75/security-issue-1-2048.jpg)