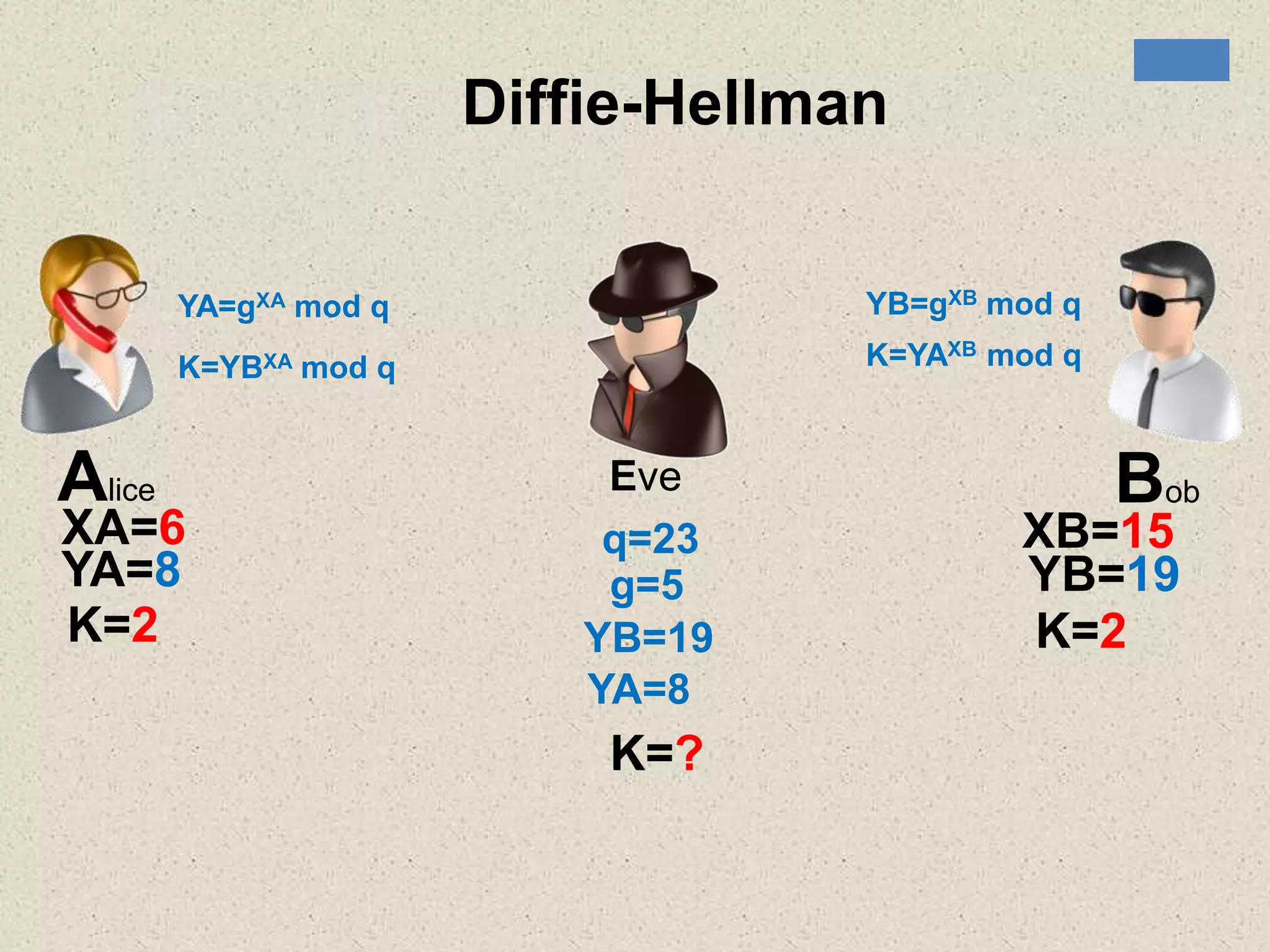
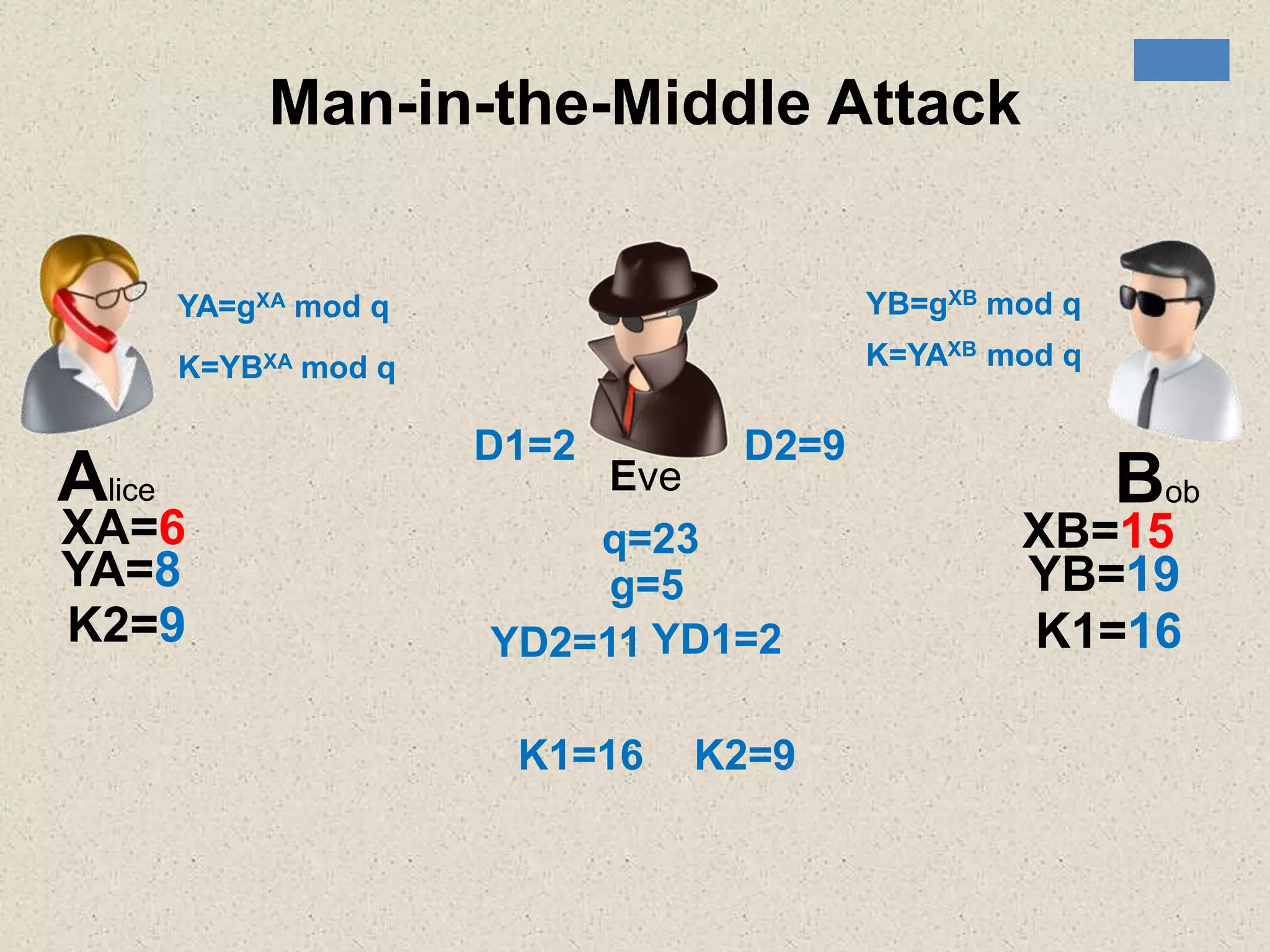
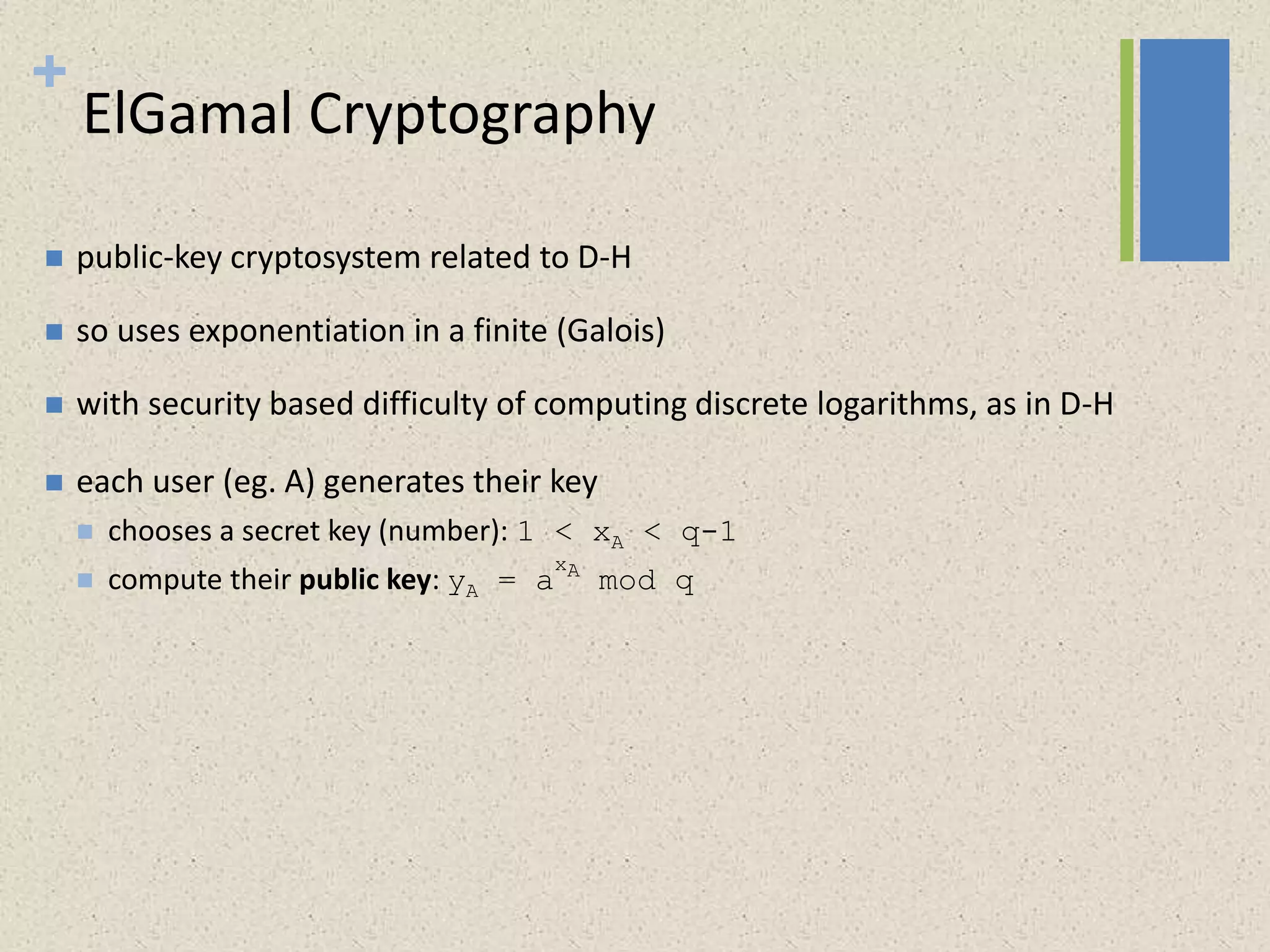
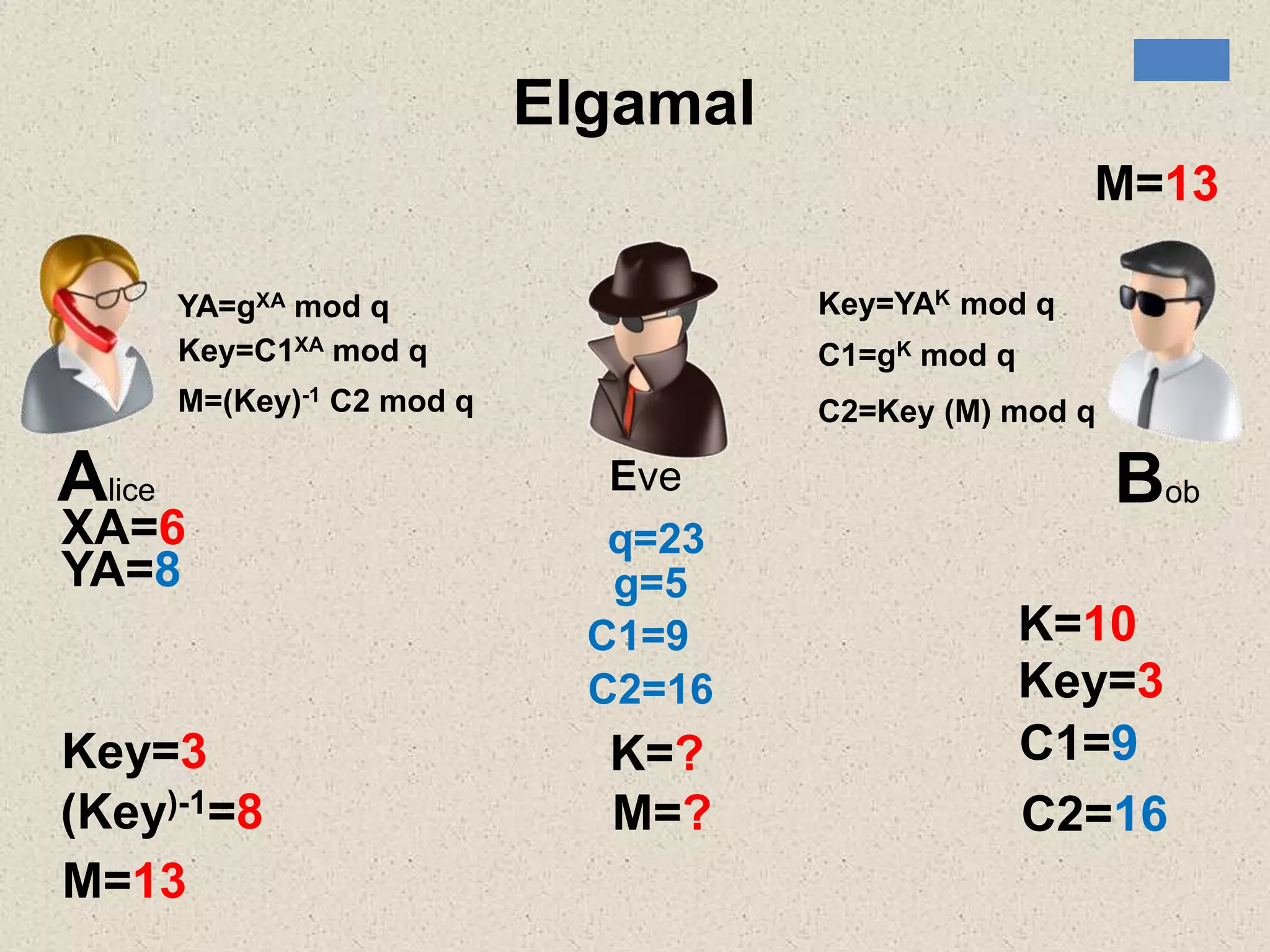
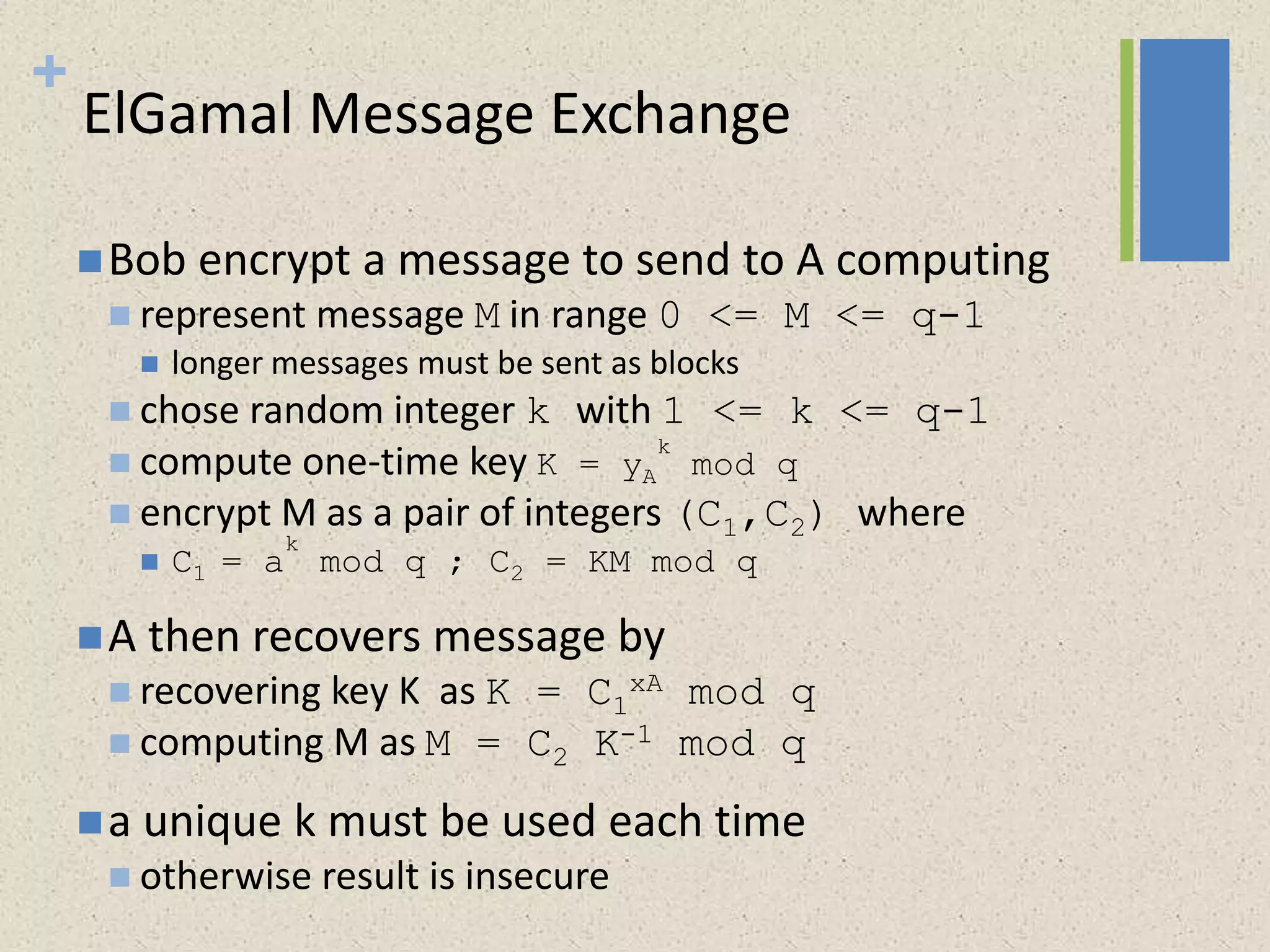
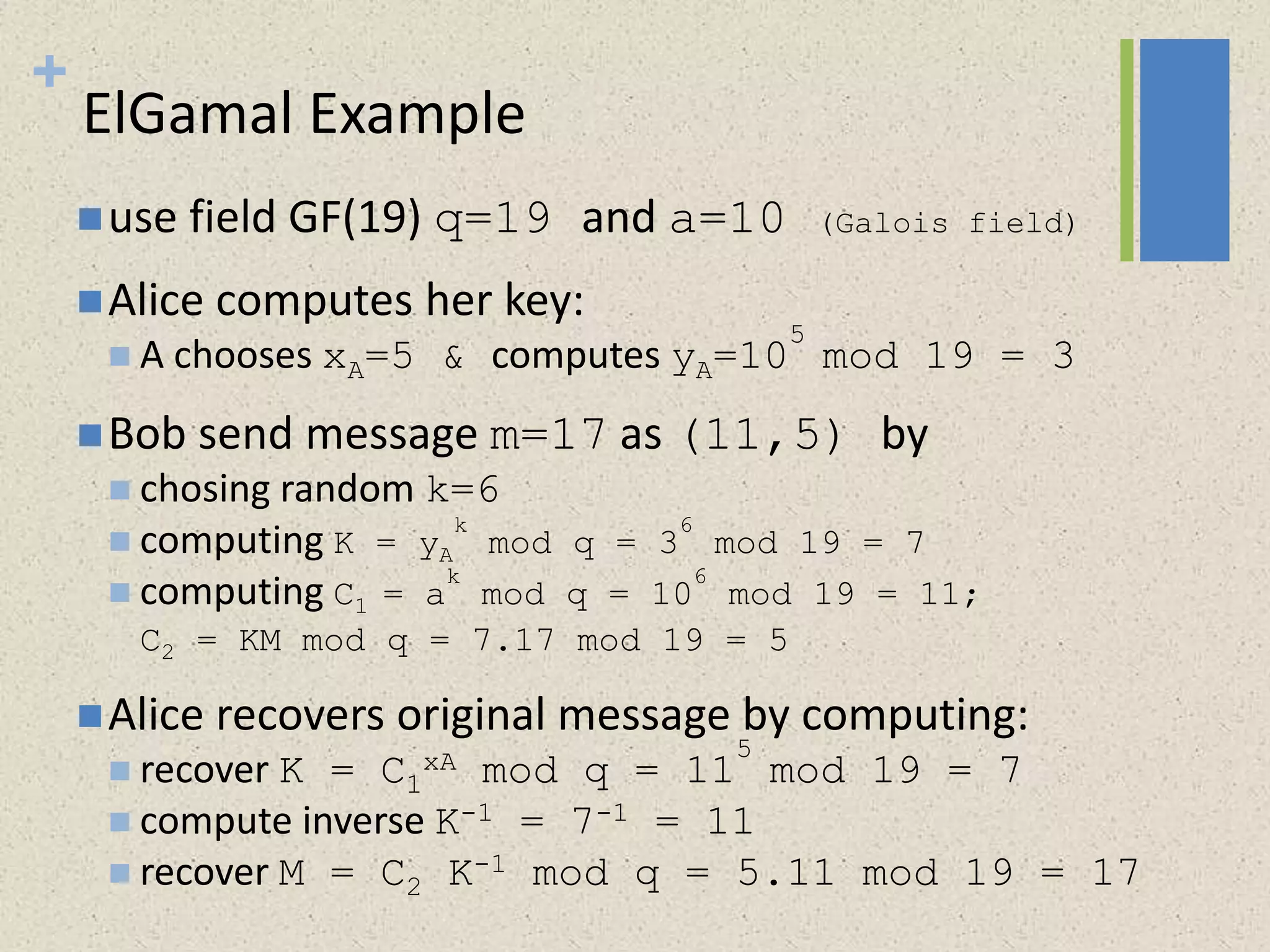
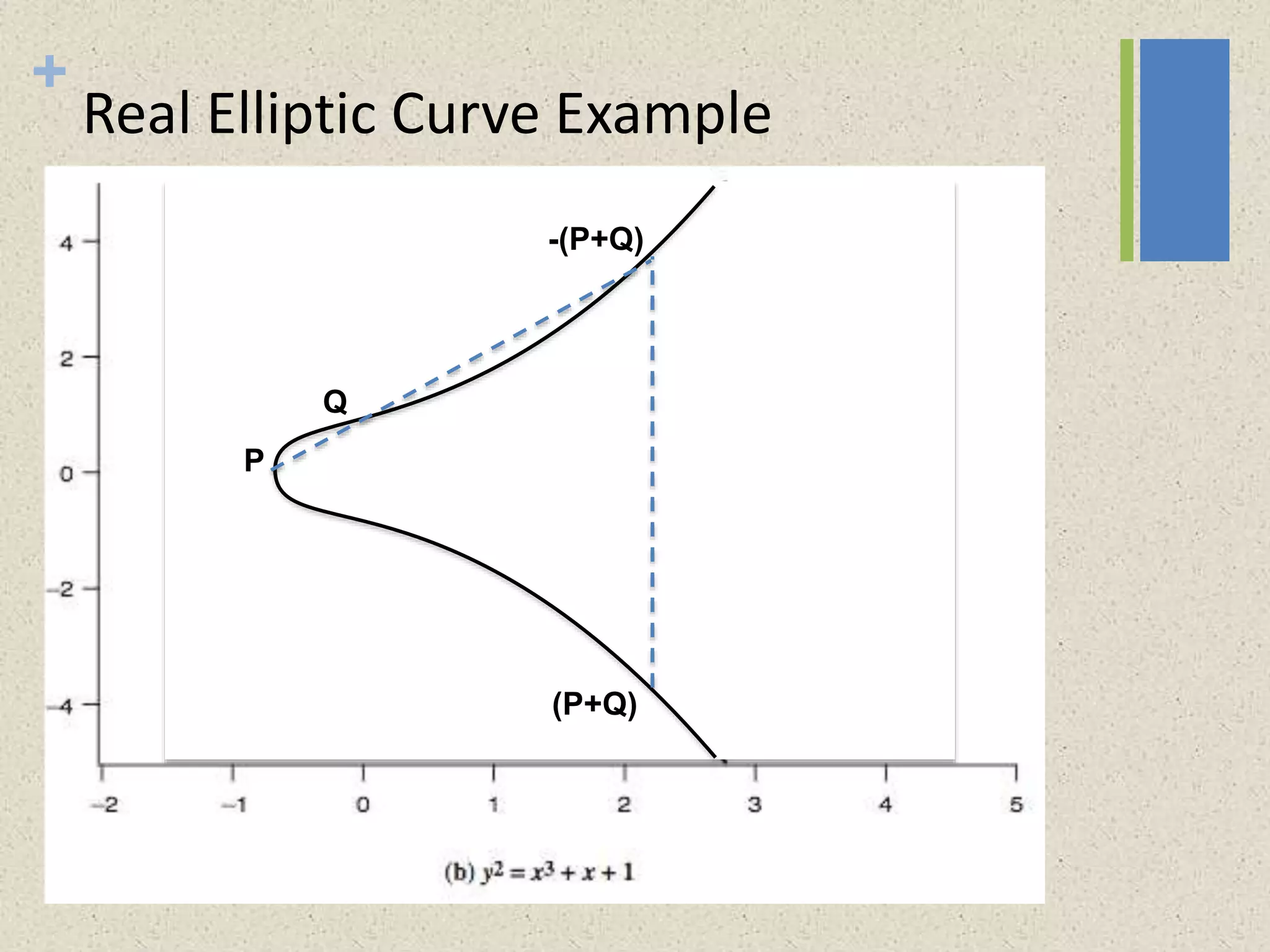
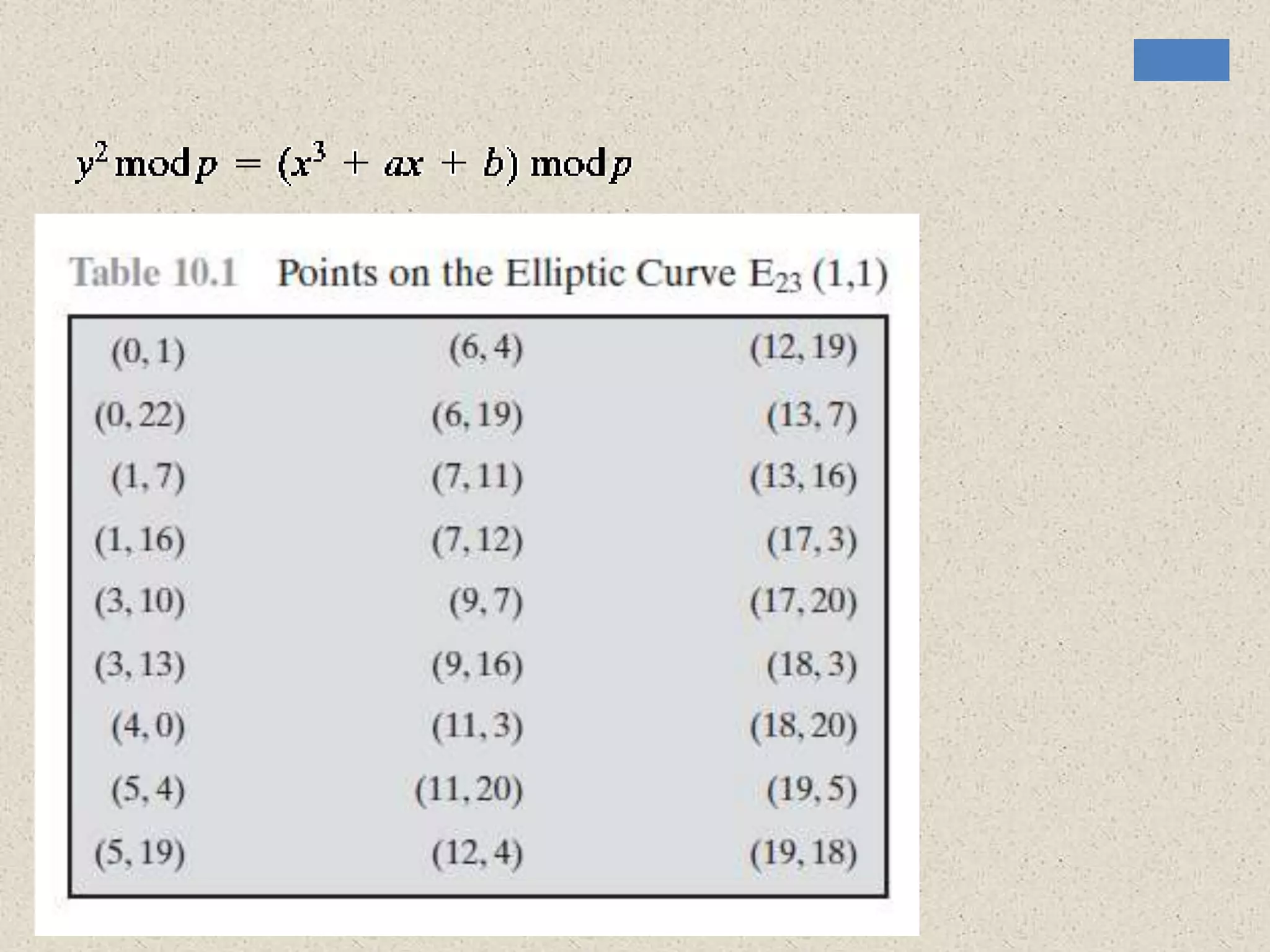
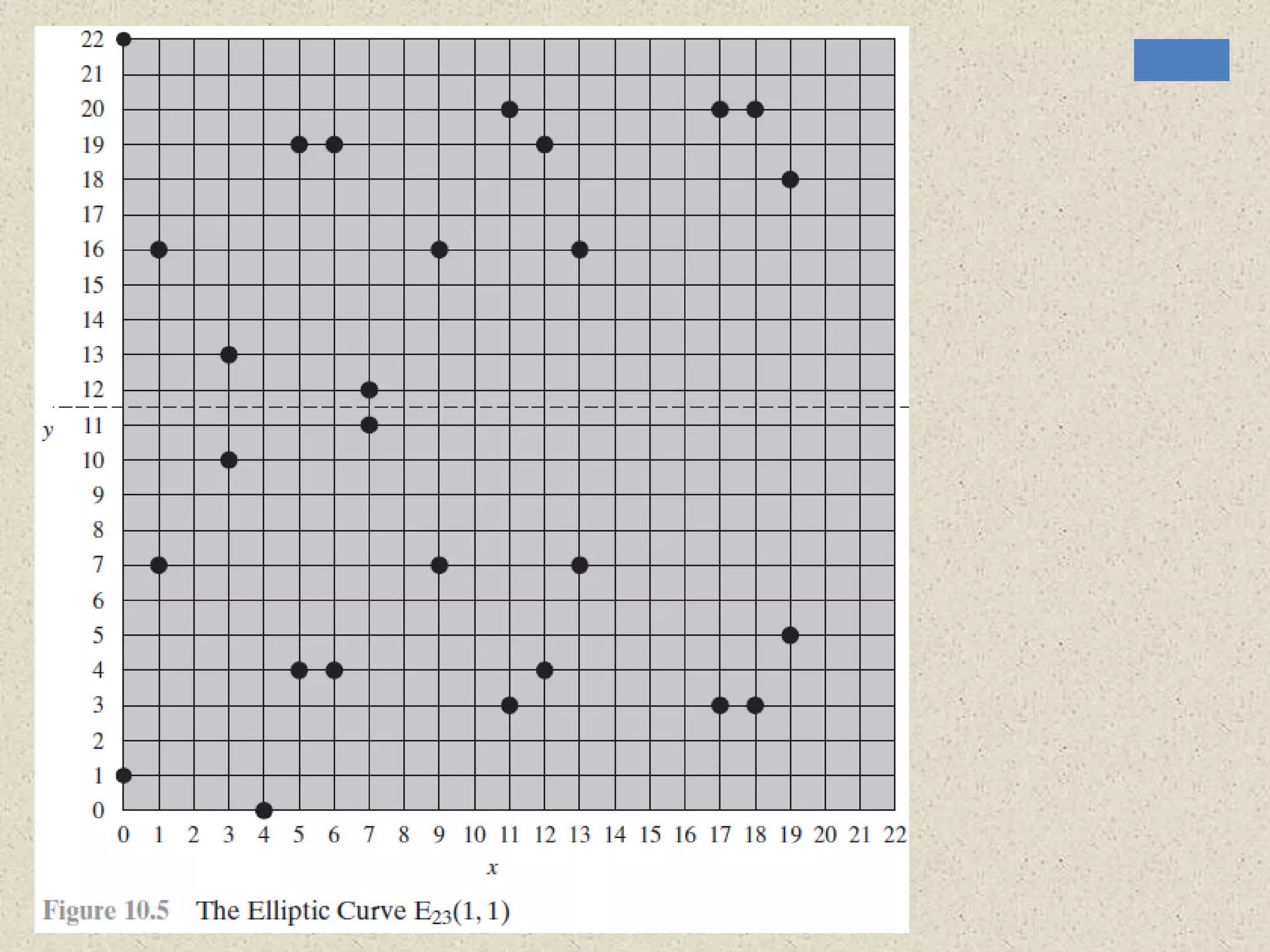
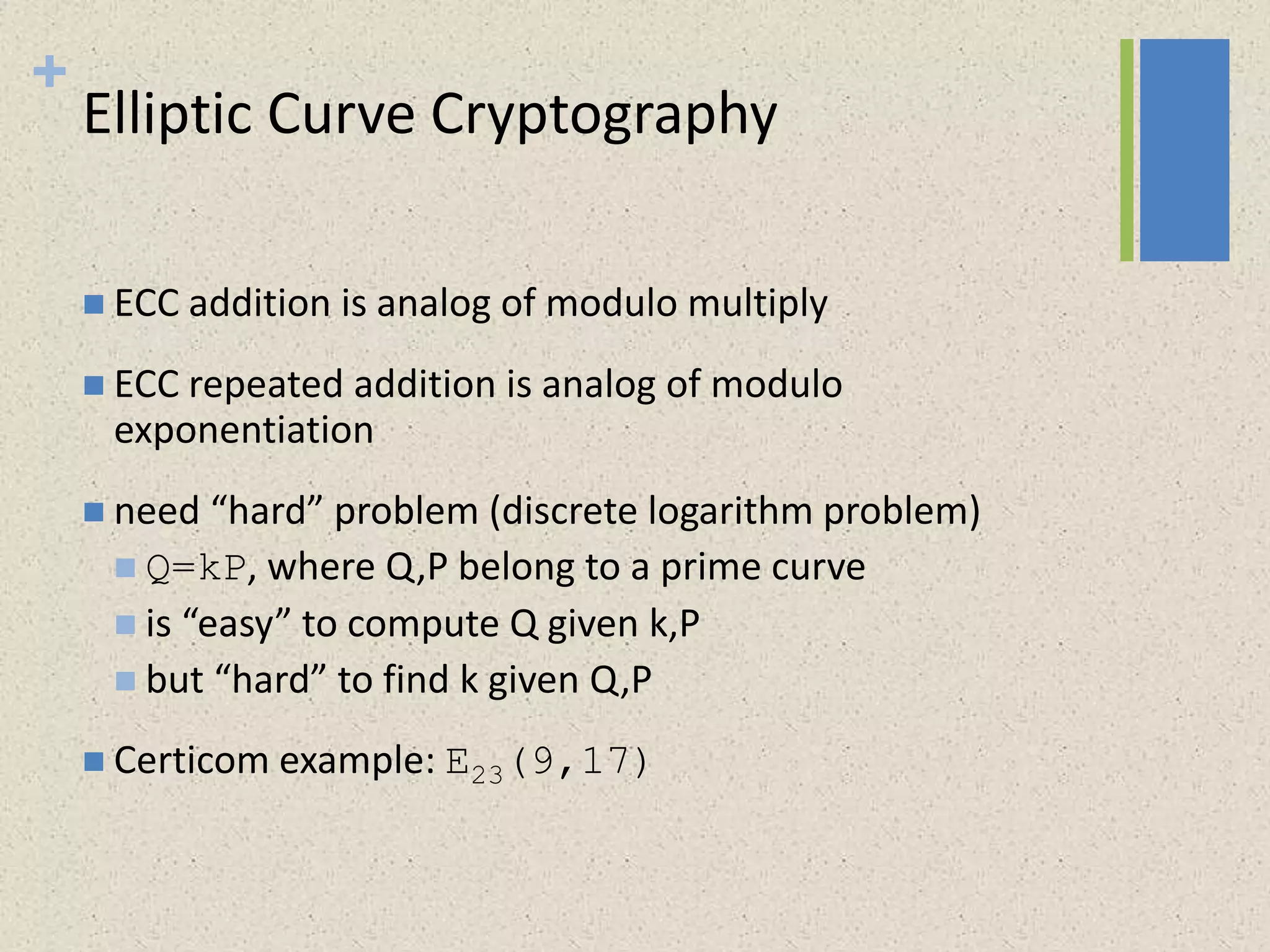
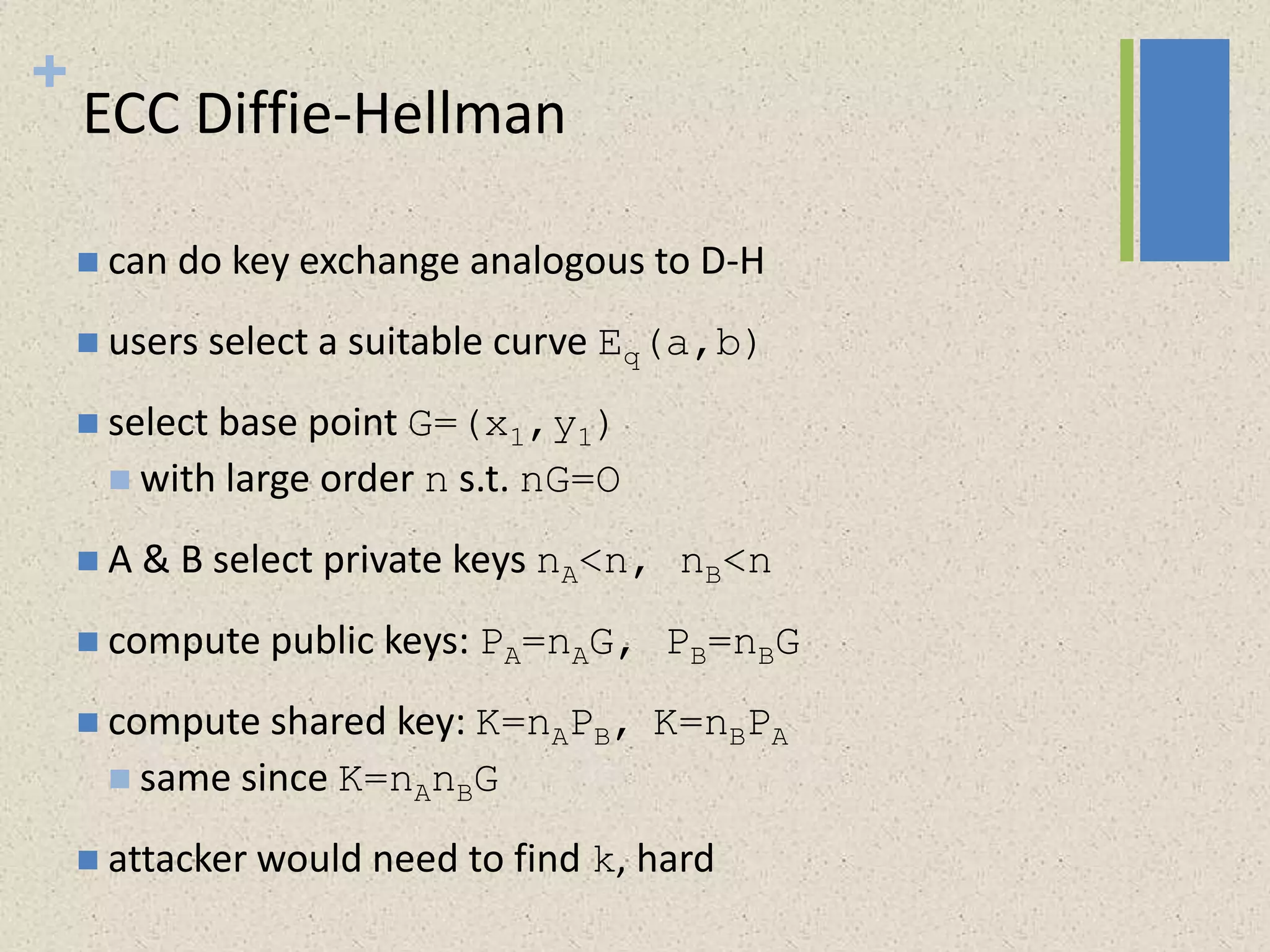
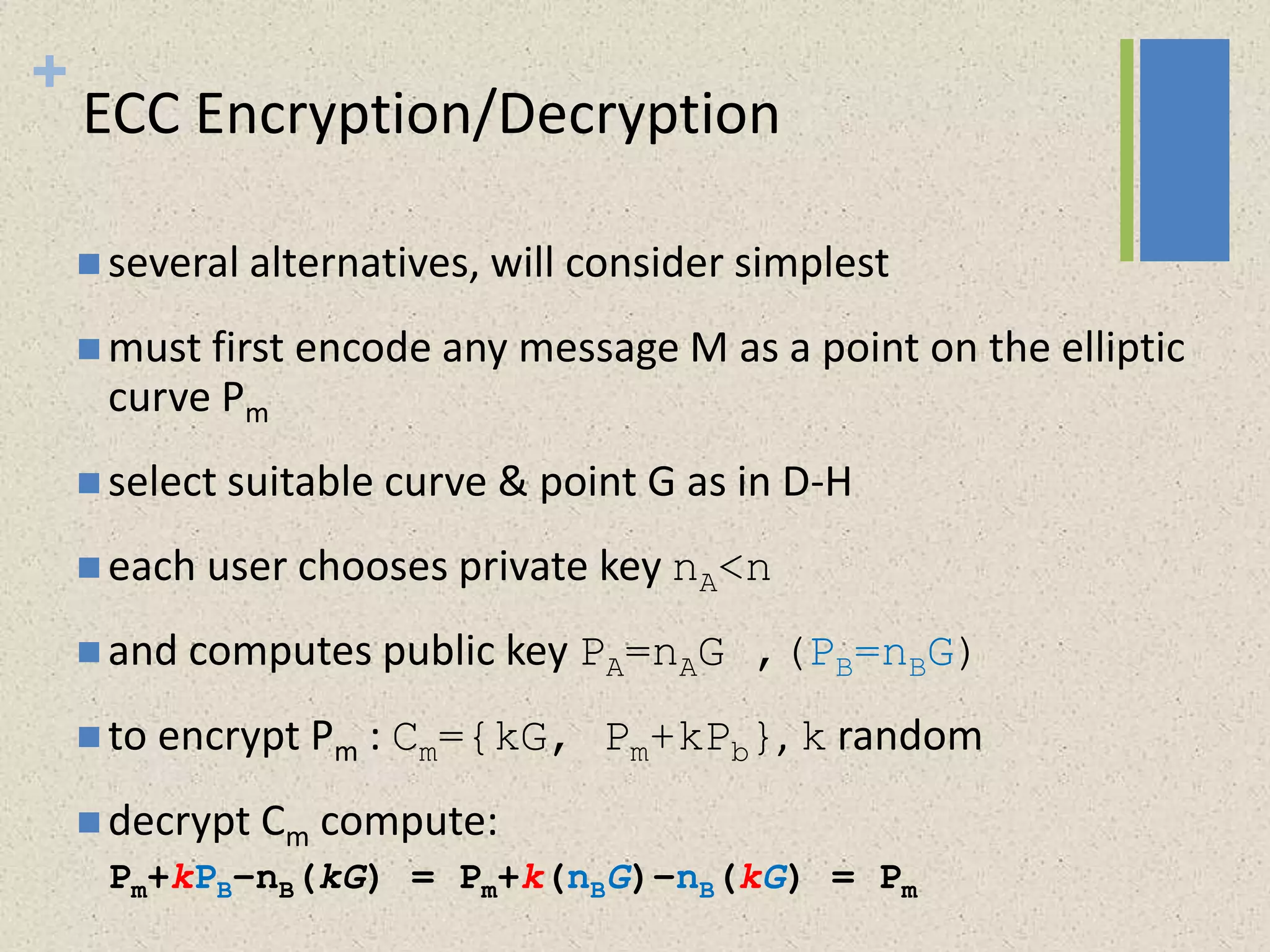
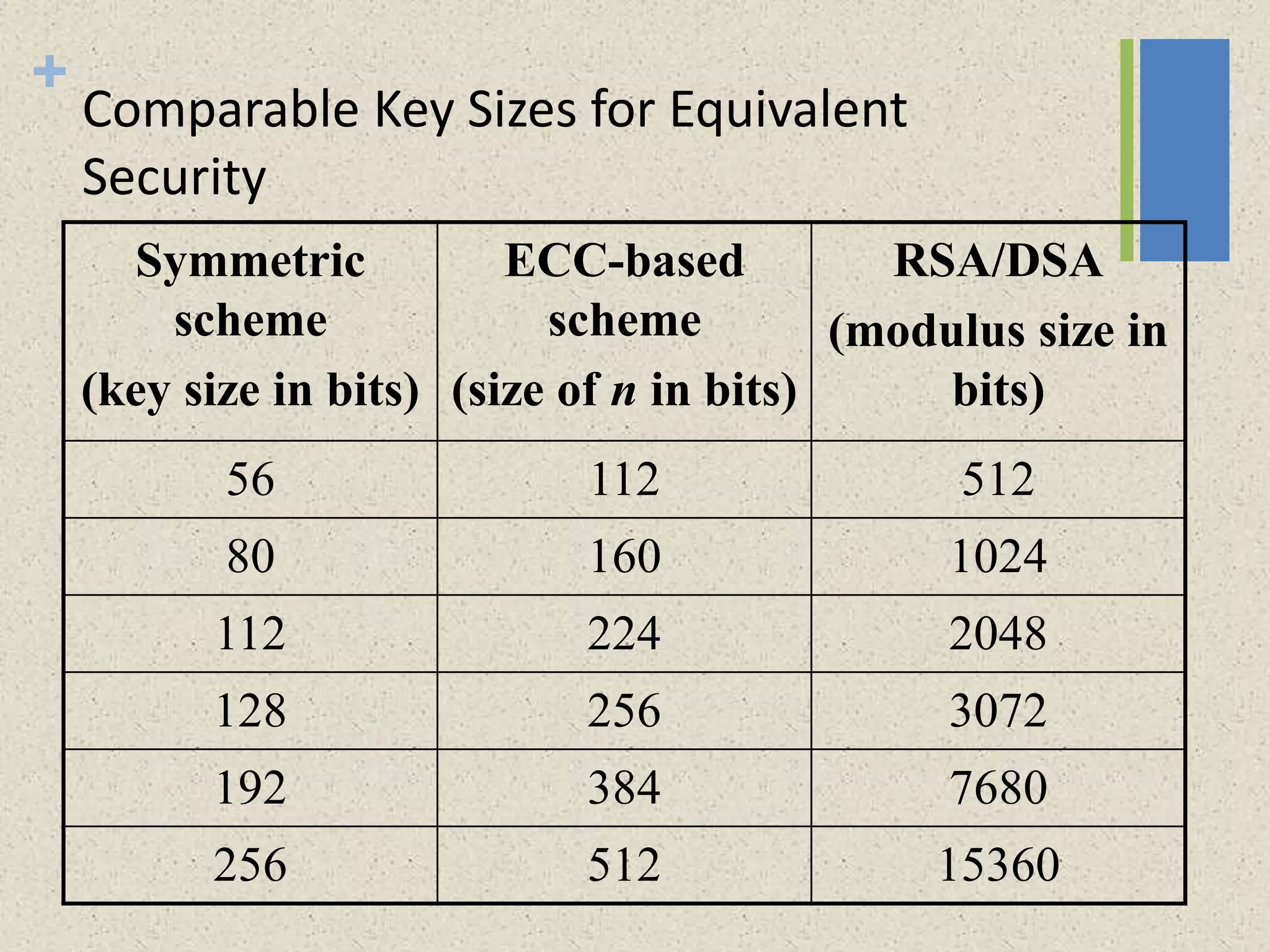
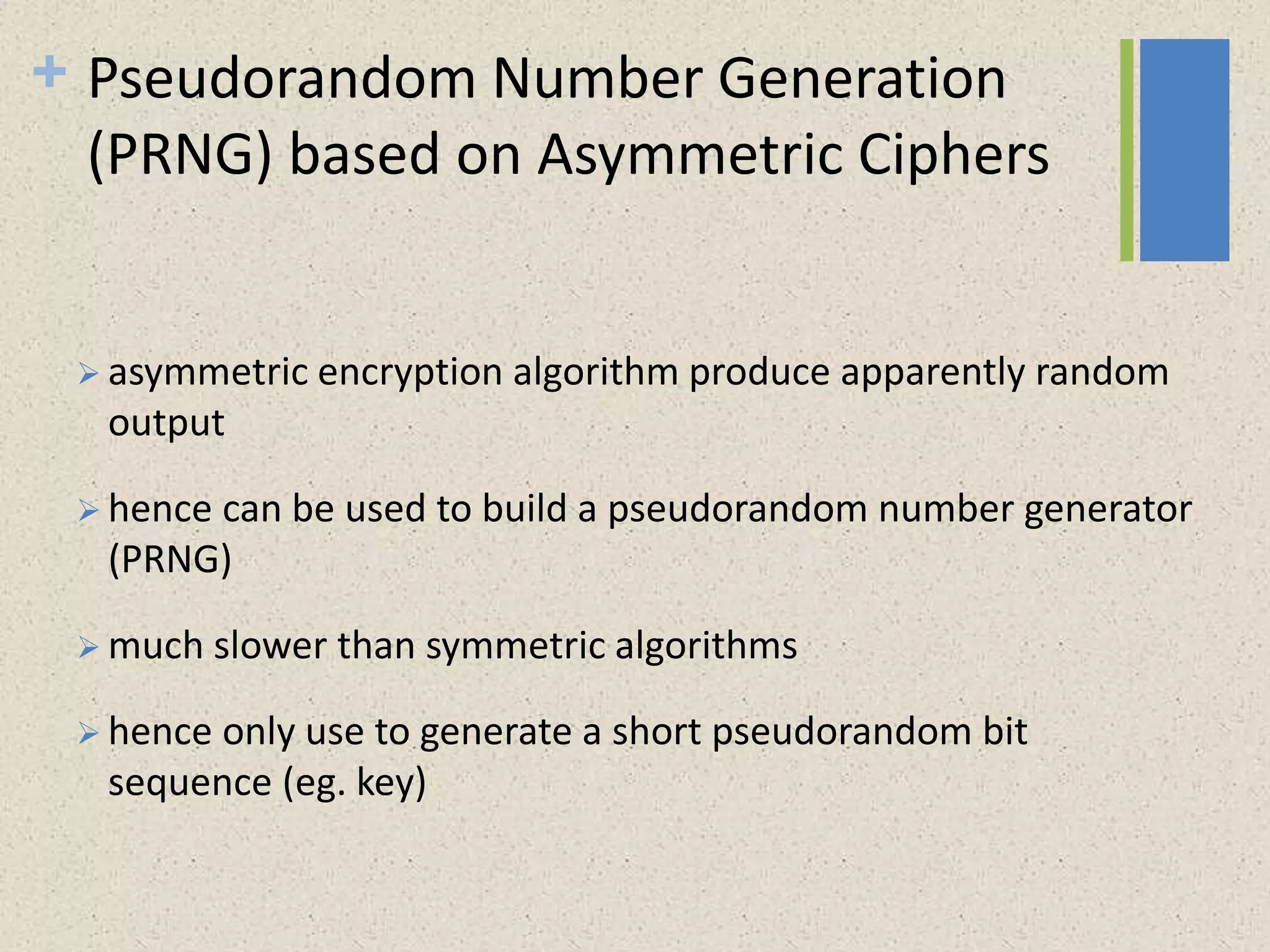
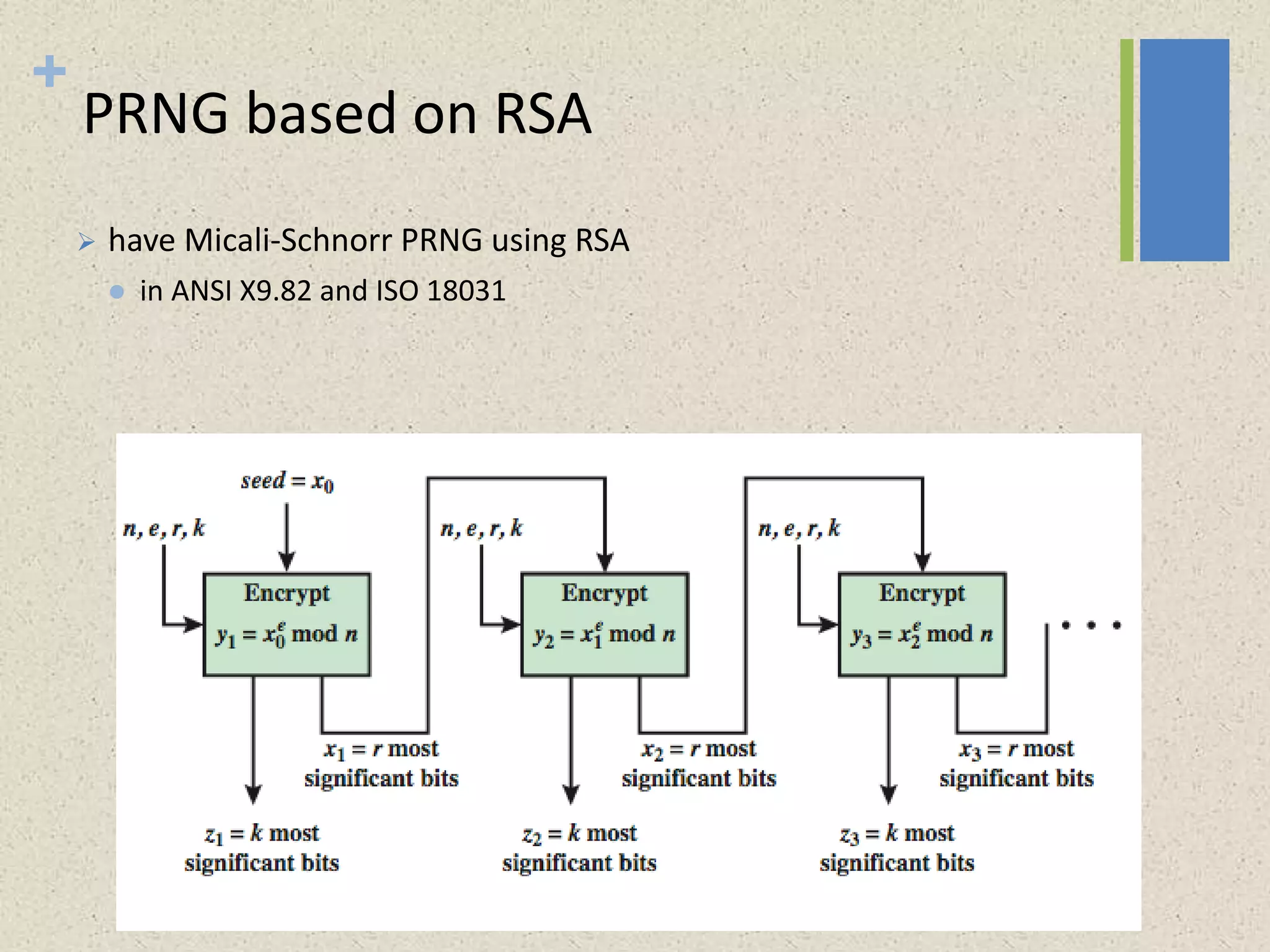
The document provides a comprehensive overview of public key cryptosystems, highlighting key exchange methods such as Diffie-Hellman, ElGamal, and elliptic curve cryptography. It discusses their underlying mathematical principles, security mechanisms, as well as potential vulnerabilities like man-in-the-middle attacks. Additionally, it covers pseudorandom number generation techniques associated with asymmetric cryptography.