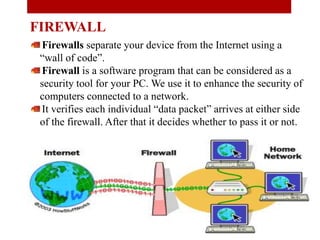
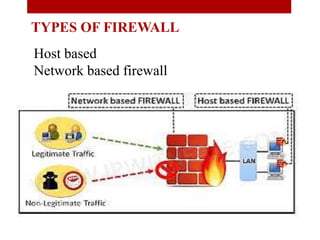
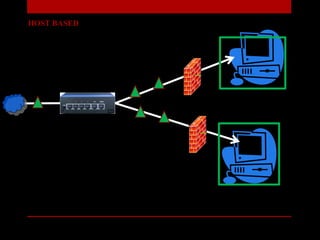
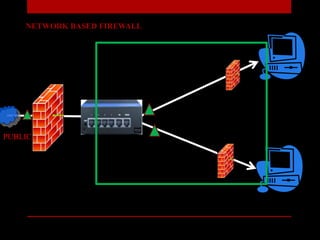
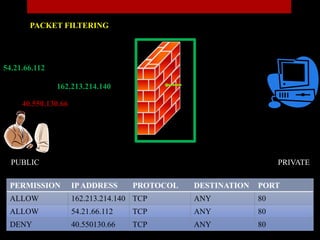
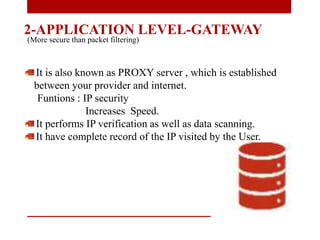
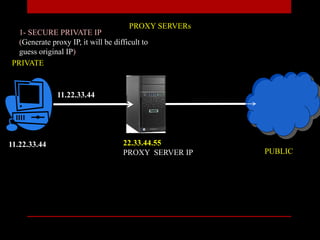
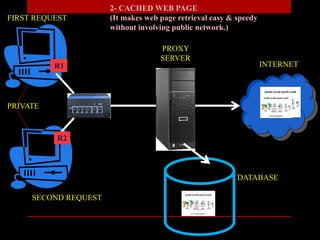
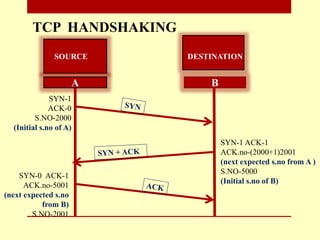
The document presents a seminar on firewalls, detailing their definitions, types, advantages, and disadvantages. Firewalls serve as security barriers for networks, originating in the late 1980s, and can be classified into hardware, software, host-based, and network-based types. The conclusion emphasizes the importance of firewalls in protecting private networks while acknowledging their limitations in guarding against various forms of malware.