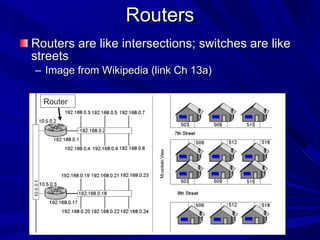
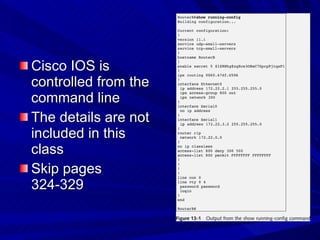
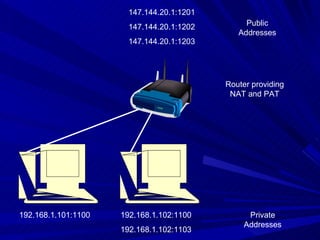
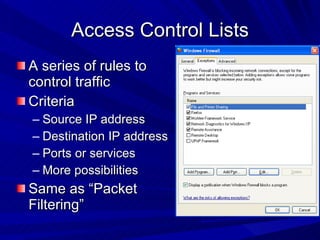
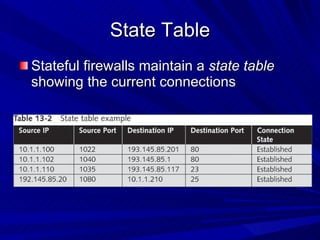
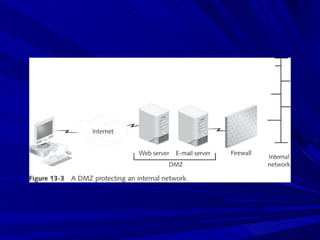
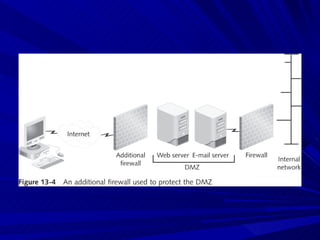
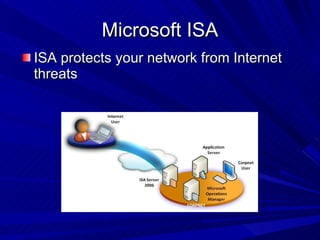
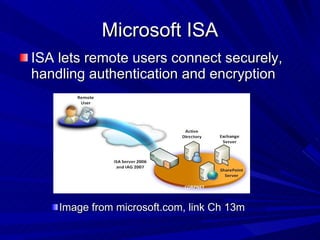
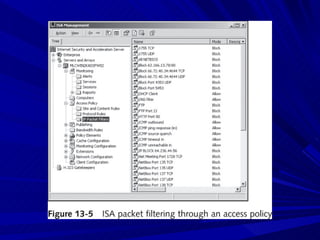
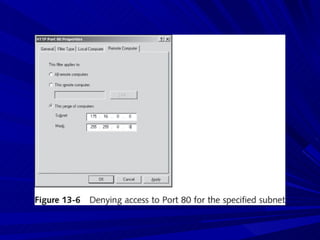
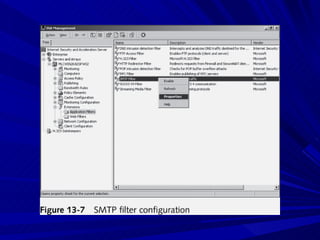
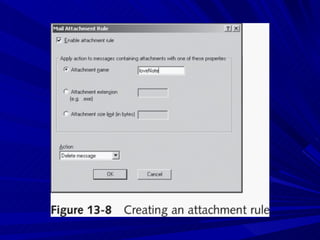
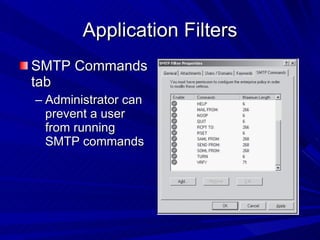
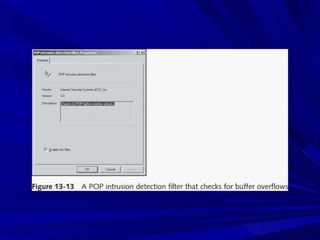
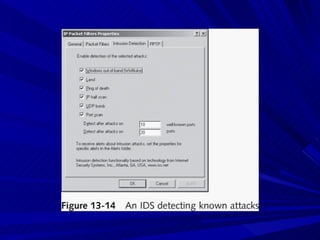
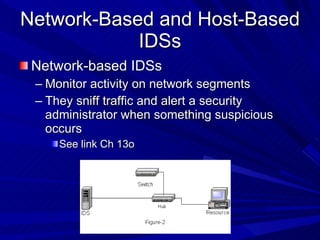
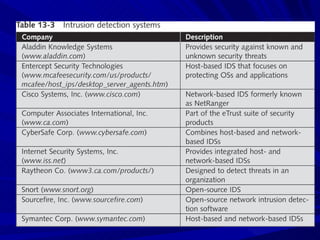
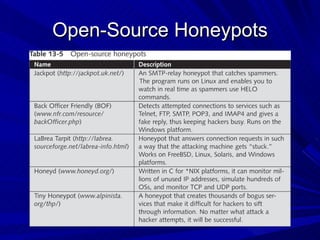
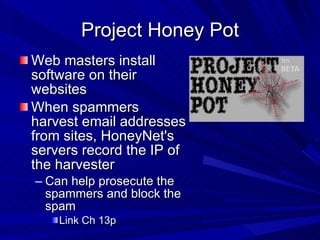
The document describes various network security devices including routers, firewalls, intrusion detection systems, and honeypots. It discusses how routers direct network traffic, common firewall technologies like network address translation and stateful packet inspection, and examples of firewall products from Cisco and Microsoft. It also covers how intrusion detection systems monitor network traffic for attacks and how honeypots are used to trap hackers by appearing vulnerable but containing no important data.