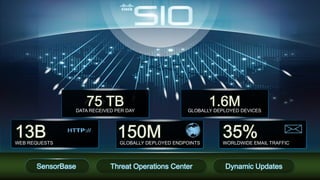
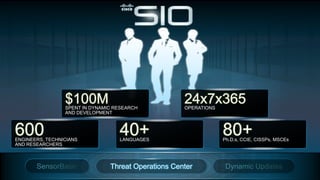
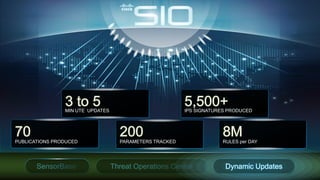
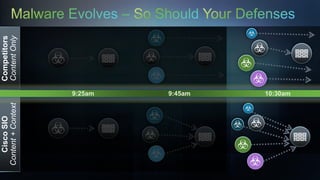
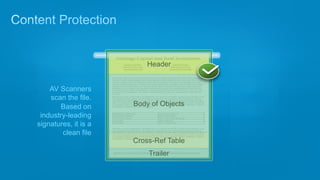
Cisco's Security Intelligence Operations (SIO) uses a global network of sensors and security researchers to detect threats. The SIO detects threats through analyzing data from over 1.6 million globally deployed devices and 75 terabytes of data received daily. It maintains a database called SensorBase that contains threat intelligence and telemetry data to provide context around potential threats. The SIO can then issue dynamic updates to security policies and signatures across Cisco's product line to block emerging threats in real-time.