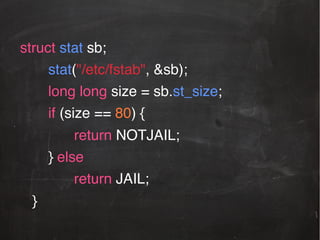
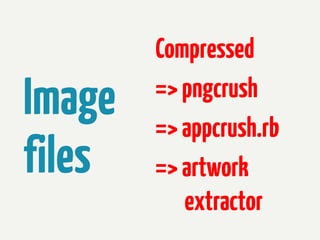
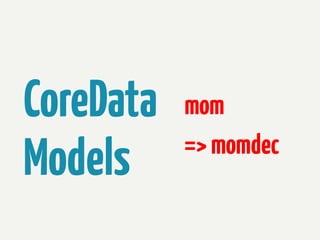
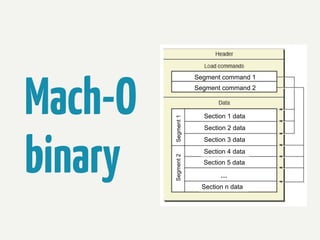
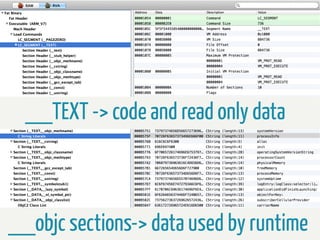
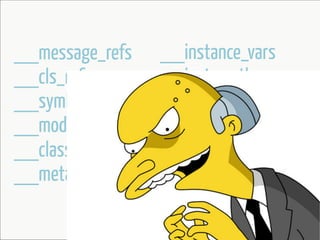
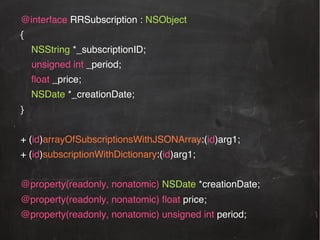
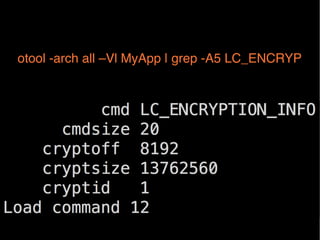
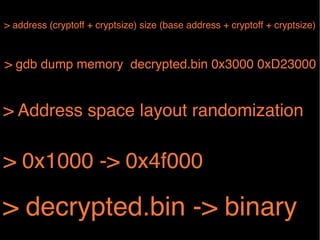
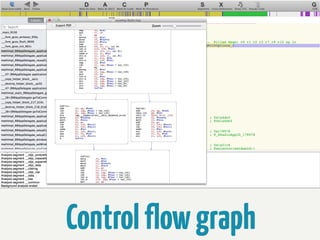
The document provides information about reverse engineering iOS apps. It discusses analyzing apps both externally using traffic sniffing and SSL proxying tools like Charles, and internally by disassembling, decompiling, and debugging the app binary and resource files. The internal analysis involves using tools like otool, class-dump, Hopper, and IDA to disassemble and decompile the binary and analyze the Mach-O structure, Objective-C metadata, and control flow. It also discusses analyzing techniques like decrypting encrypted binaries and models, extracting image and interface files, and working with the app at runtime using Cycript. The document notes additional protection techniques apps may use like SSL pinning, method obfuscation, string obfuscation, and



























![- (void)connection:(NSURLConnection *)connection
willSendRequestForAuthenticationChallenge:
(NSURLAuthenticationChallenge *)challenge {!
…!
NSData *remoteCertificateData =
CFBridgingRelease(SecCertificateCopyData(certificate));!
NSString *cerPath = [[NSBundle mainBundle]
pathForResource:@"MyLocalCertificate" ofType:@"cer"];!
NSData *localCertData = [NSData dataWithContentsOfFile:cerPath];!
if ([remoteCertificateData
isEqualToData:localCertData]) {!
[[challenge sender] useCredential:credential
forAuthenticationChallenge:challenge];!
} else {!
[[challenge sender]
cancelAuthenticationChallenge:challenge];!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-47-320.jpg)
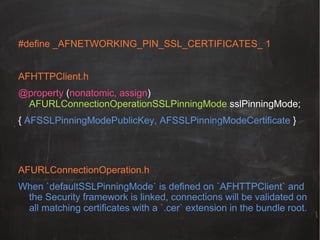



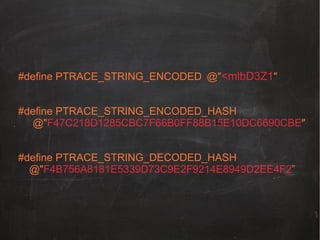
![#define verifyDecodedString(encoded, hashE, hashD, success)
fweybz(encoded, hashE, hashD, success)
static inline NSString * fweybz(NSString *encoded, NSString *hashE,
NSString *hashD, BOOL *success) {
NSString *decoded = decodedString(encoded);
if (success != NULL) {
*success
= (decoded && [hashFromString(encoded)
isEqualToString:hashEncoded] &&
[hashFromString(decoded)
isEqualToString:hashDecoded]) ? YES : NO;
return decoded;
}](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-53-320.jpg)

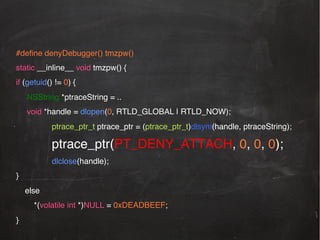

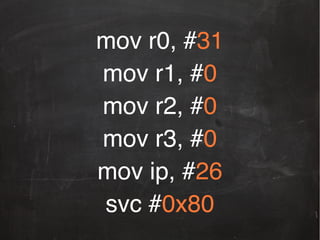
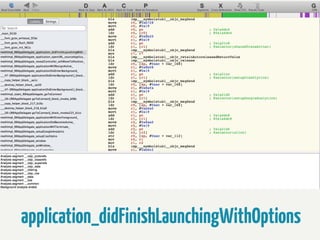
![int main(int argc, char *argv[])!
{!
@autoreleasepool {!
denyDebugger();!
return UIApplicationMain(argc, argv, nil, nil));!
}!
}!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-58-320.jpg)
![+ (PurchaseManager *)sharedManager {!
if (isDebugged())!
!return nil;!
static PurchaseManager *sharedPurchaseManager = nil; !
static dispatch_once_t onceToken;!
!dispatch_once(&onceToken, ^{ !
!!
!sharedPurchaseManager = [[self alloc] init];!
});!
!return sharedPurchaseManager ; !
}!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-59-320.jpg)

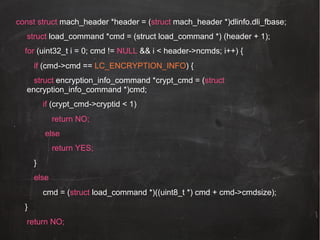
![BOOL isDirectory = NO;
NSString *directoryPath = [[[NSBundle mainBundle]
bundlePath]
stringByAppendingPathComponent:@”SC_Info/”];
BOOL directoryExists = [[NSFileManager
defaultManager] fileExistsAtPath:directoryPath
isDirectory:&isDirectory];
BOOL contentSeemsValid = ([[[NSFileManager
defaultManager] contentsOfDirectoryAtPath:directoryPath
error:NULL] count] == 2);](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-62-320.jpg)
![!NSDictionary *iTunesMetadata = [NSDictionary
!dictionaryWithContentsOfFile:[rootDirectoryPath
!stringByAppendingPathComponent:@”
iTunesMetadata.plist”]];!
!NSString *appleID = iTunesMetadata[appleID];!
NSDictionary *accountInfo =
iTunesMetadata[downloadInfoKey][accountInfo];!
!BOOL isValidAppleID = (appleID.length > 0 &&
![appleID rangeOfString:appleIDMailAddress
!options:NSCaseInsensitiveSearch].location ==
!NSNotFound);!
BOOL isValidDownloadInfo = (accountInfo.count > 0);!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-63-320.jpg)

![BOOL dyLibFound = NO;
NSArray *directoryFiles = [[NSFileManager
defaultManager] contentsOfDirectoryAtPath:
[[NSBundle mainBundle] bundlePath] error:NULL];
for (NSString *filename in directoryFiles) {
if ([[filename pathExtension]
caseInsensitiveCompare:@”dylib”] ==
NSOrderedSame) {
dyLibFound = YES;
break;
}
}!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-65-320.jpg)



![!
NSError *error; !
NSString *jailTest = @”Jailbreak time!";!
[jailTest writeToFile:@"/private/test_jail.txt"
atomically:YES
encoding:NSUTF8StringEncoding error:&error];!
if(error==nil) {!
…!
}!
!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-69-320.jpg)
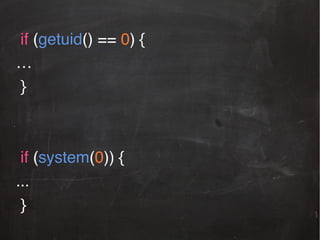
![NSArray *jailbrokenPaths = @[@"/Applications/Cydia.app",!
!
!
!@"/usr/sbin/sshd",!
!
!@"/usr/bin/sshd",!
!
!
!@"/private/var/lib/apt",!
!
!
!@"/private/var/lib/cydia”!
!
!
!@"/usr/libexec/sftp-server",!
!
!
!@"/Applications/blackra1n.app",!
!
!
!@"/Applications/Icy.app",!
!
!
!
!
!
!@"/Applications/RockApp.app",!
!
!!
!
!
!@"/private/var/stash"];!
!
NSString *rooted;!
for (NSString *string in jailbrokenPath)!
if ([[NSFileManager defaultManager] fileExistsAtPath:string]) {!
…!
}!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-71-320.jpg)
![!
!
for (NSDictionary * dict in processes) {!
!NSString *process = [dict
objectForKey:@"ProcessName"];!
!! !if ([process isEqualToString:CYDIA]) {!
!! ! ! !...!
!! ! ! !}!
}!
!](https://image.slidesharecdn.com/iosreverseengineering-131123085932-phpapp02/85/Reverse-Engineering-iOS-apps-72-320.jpg)