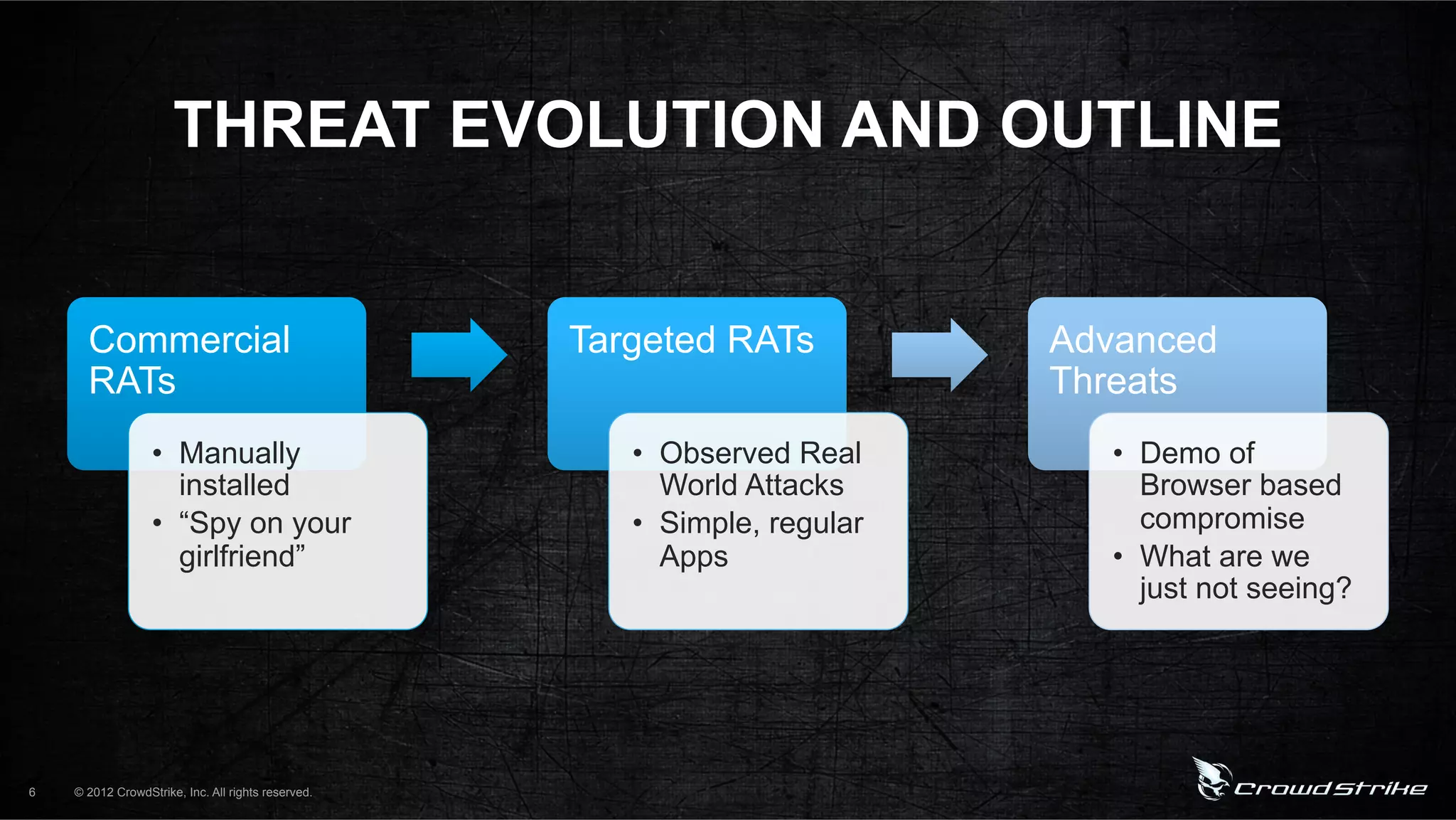
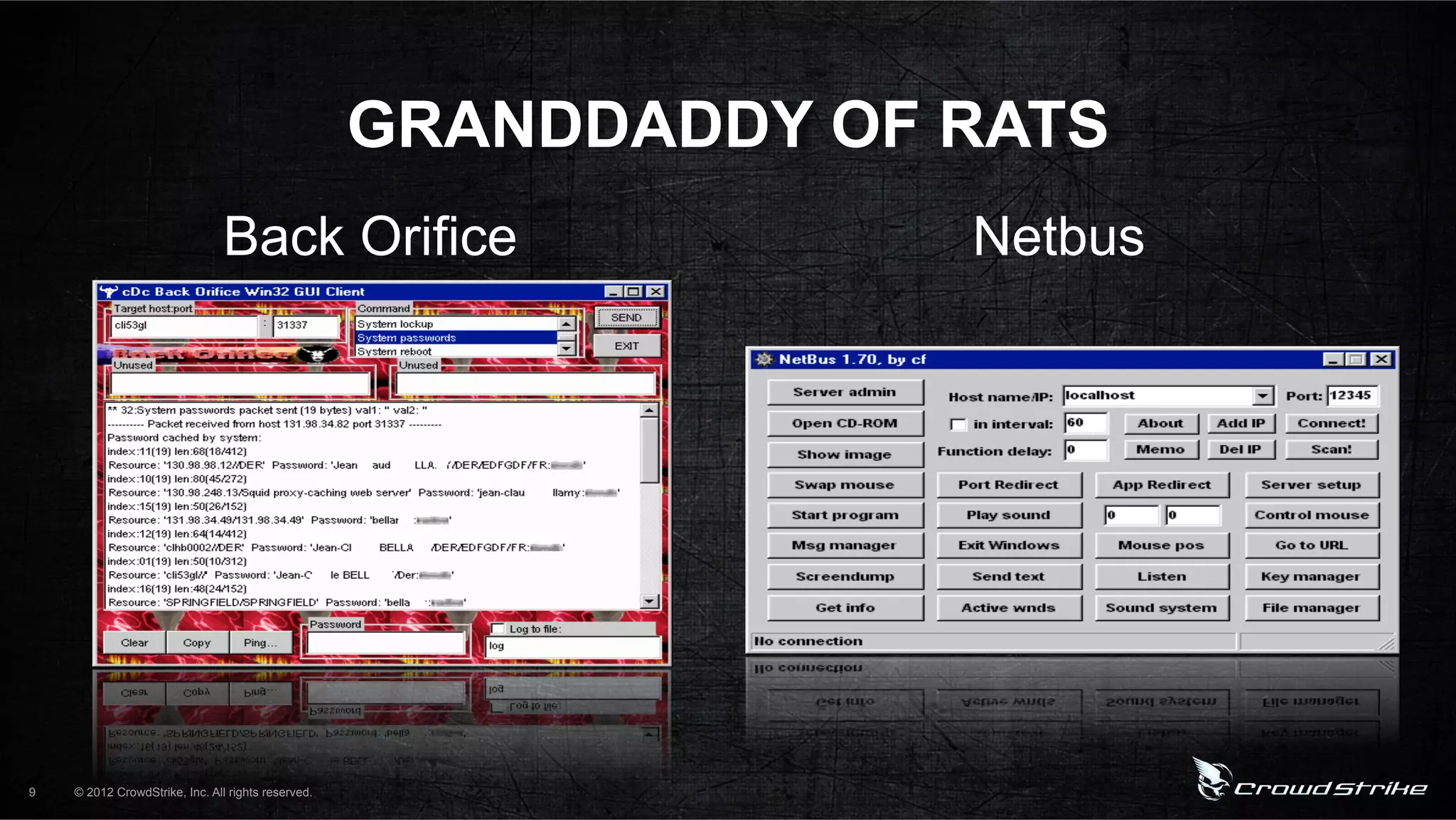
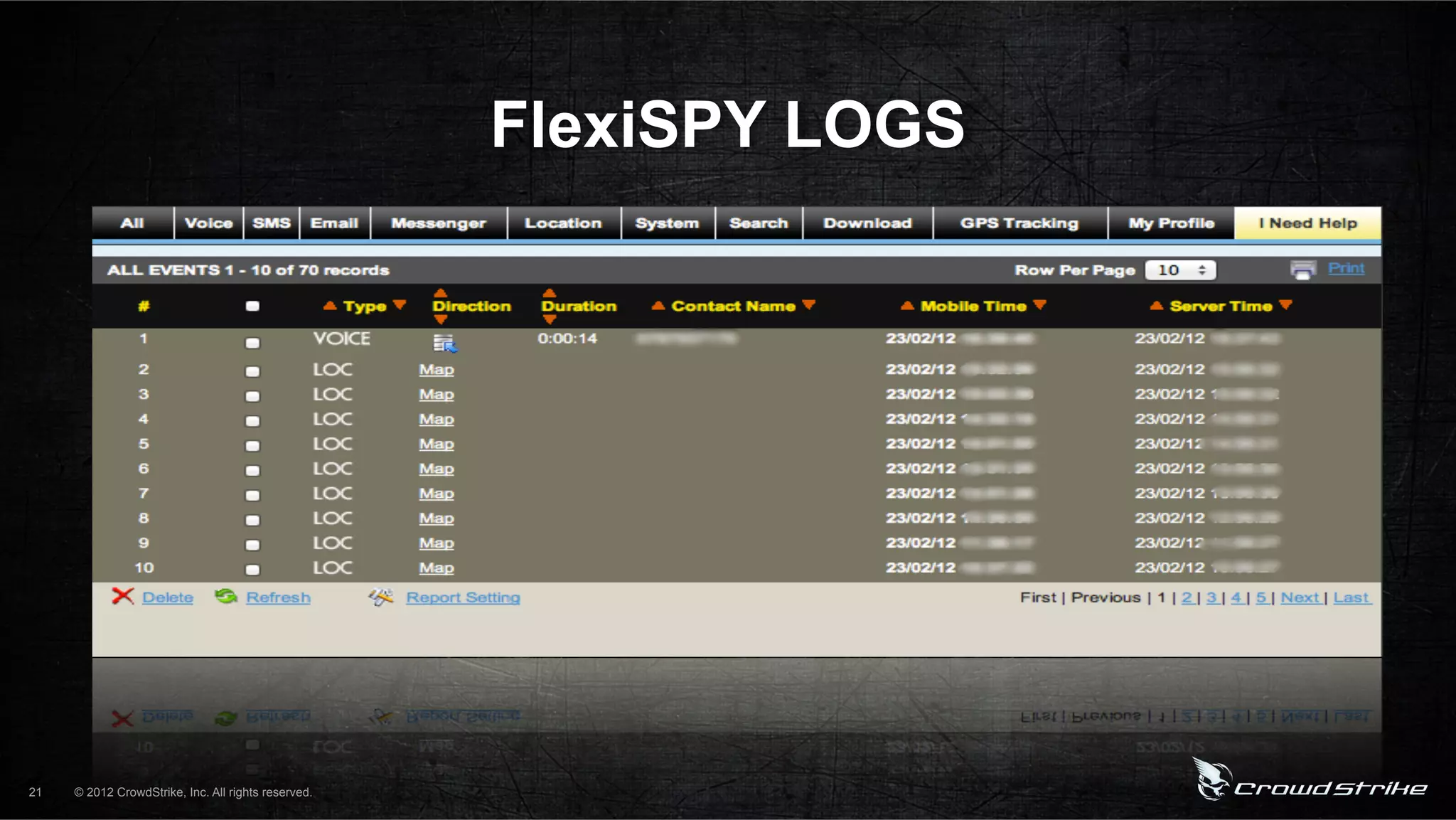
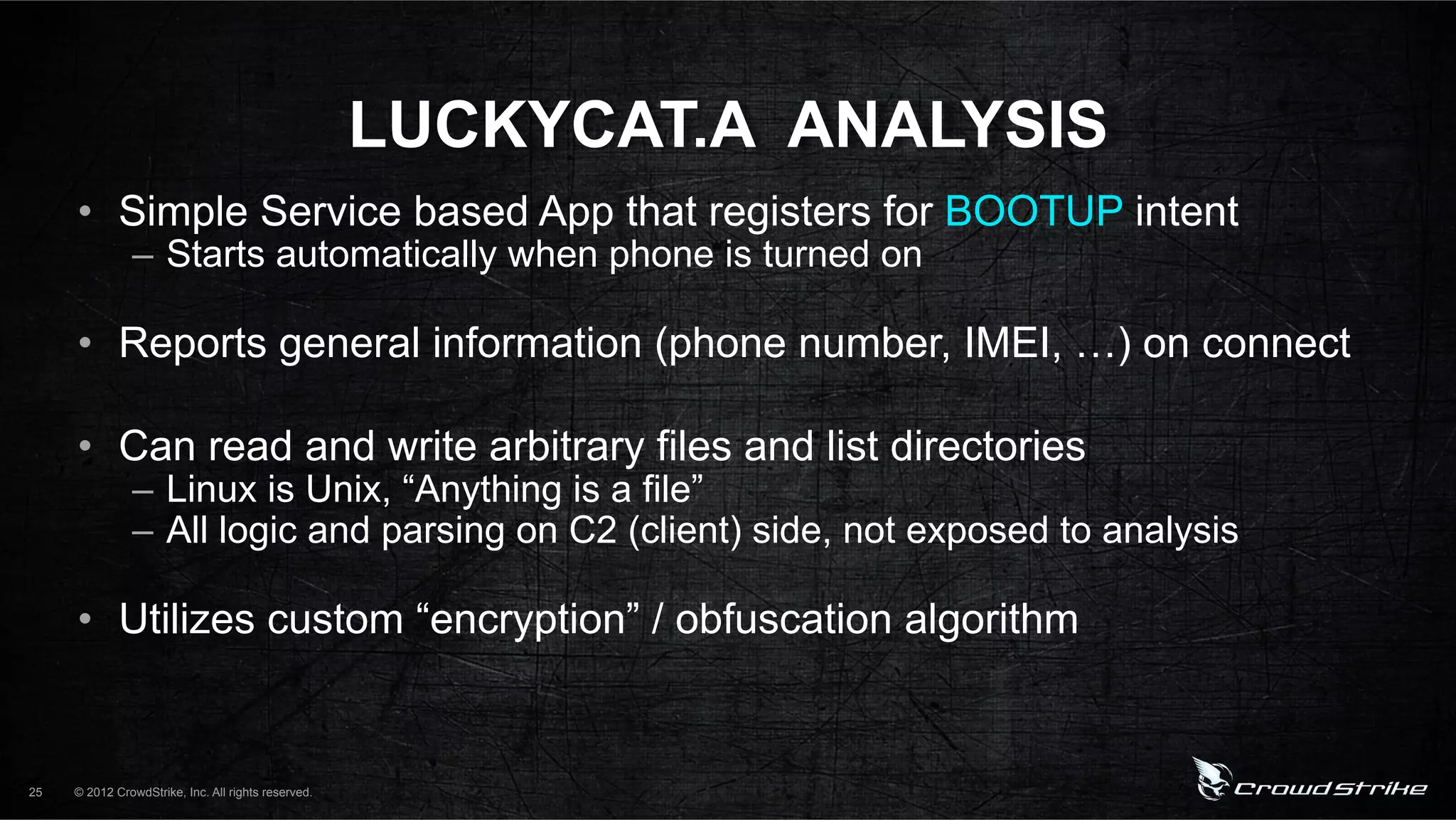
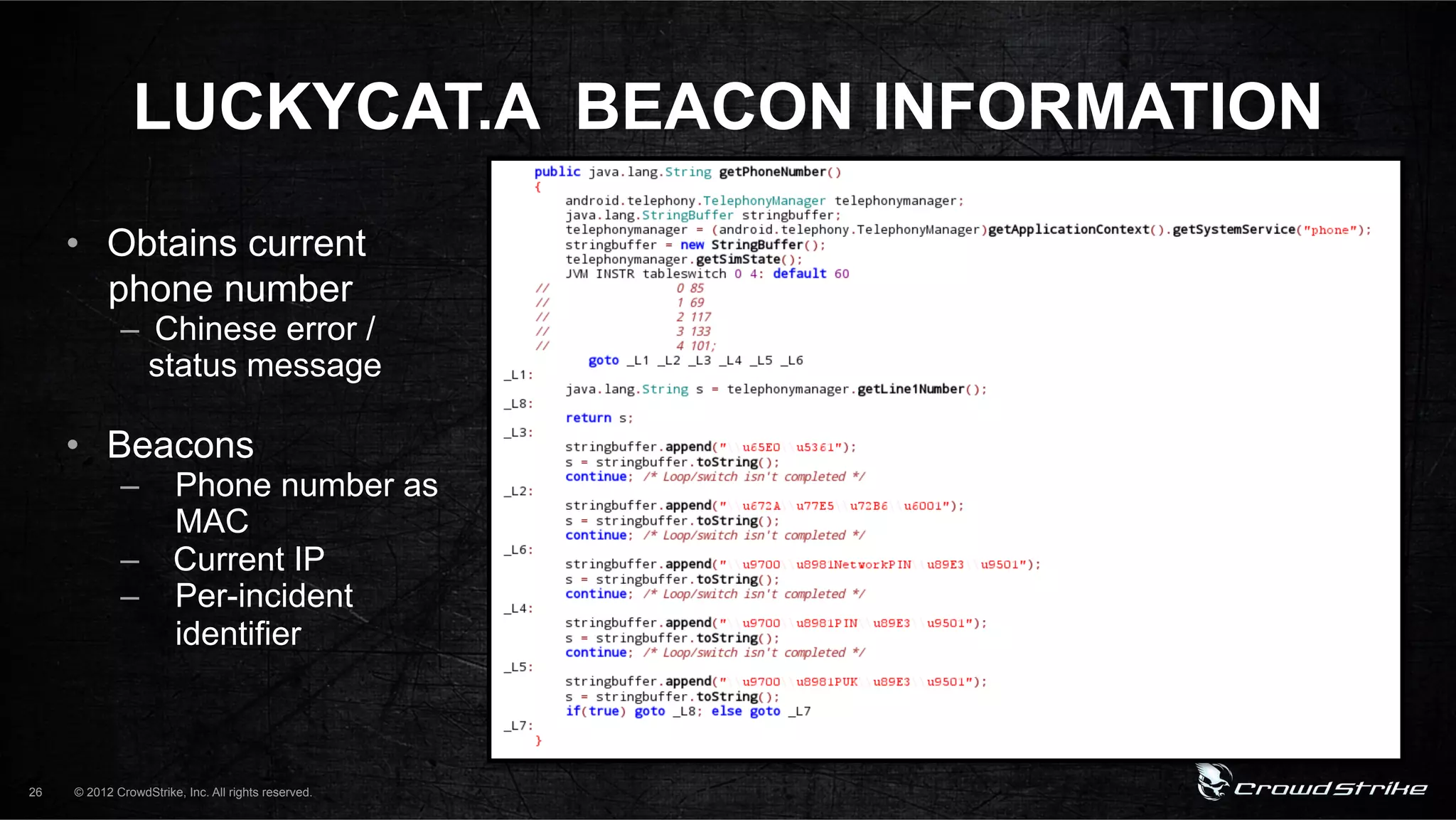
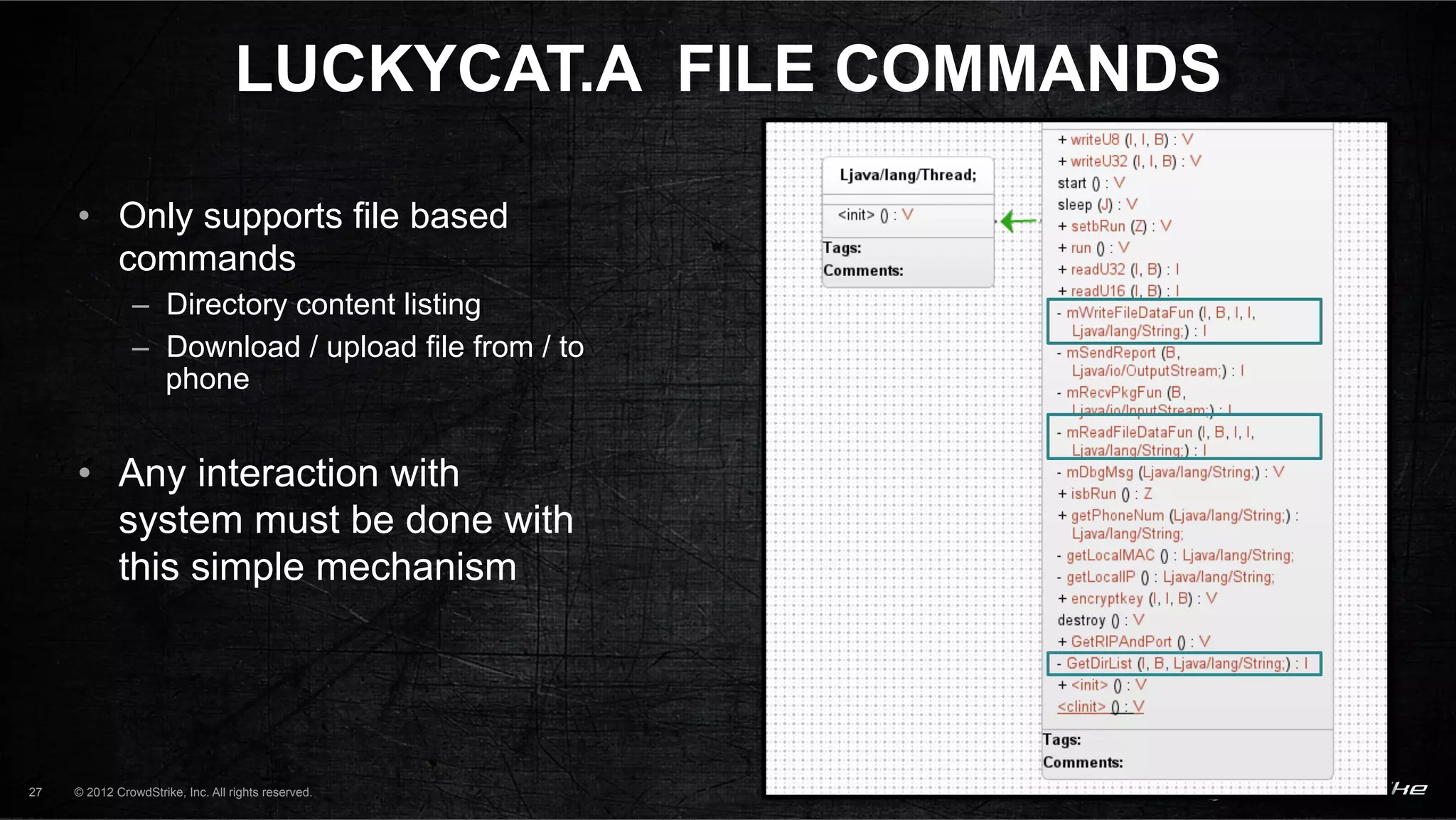
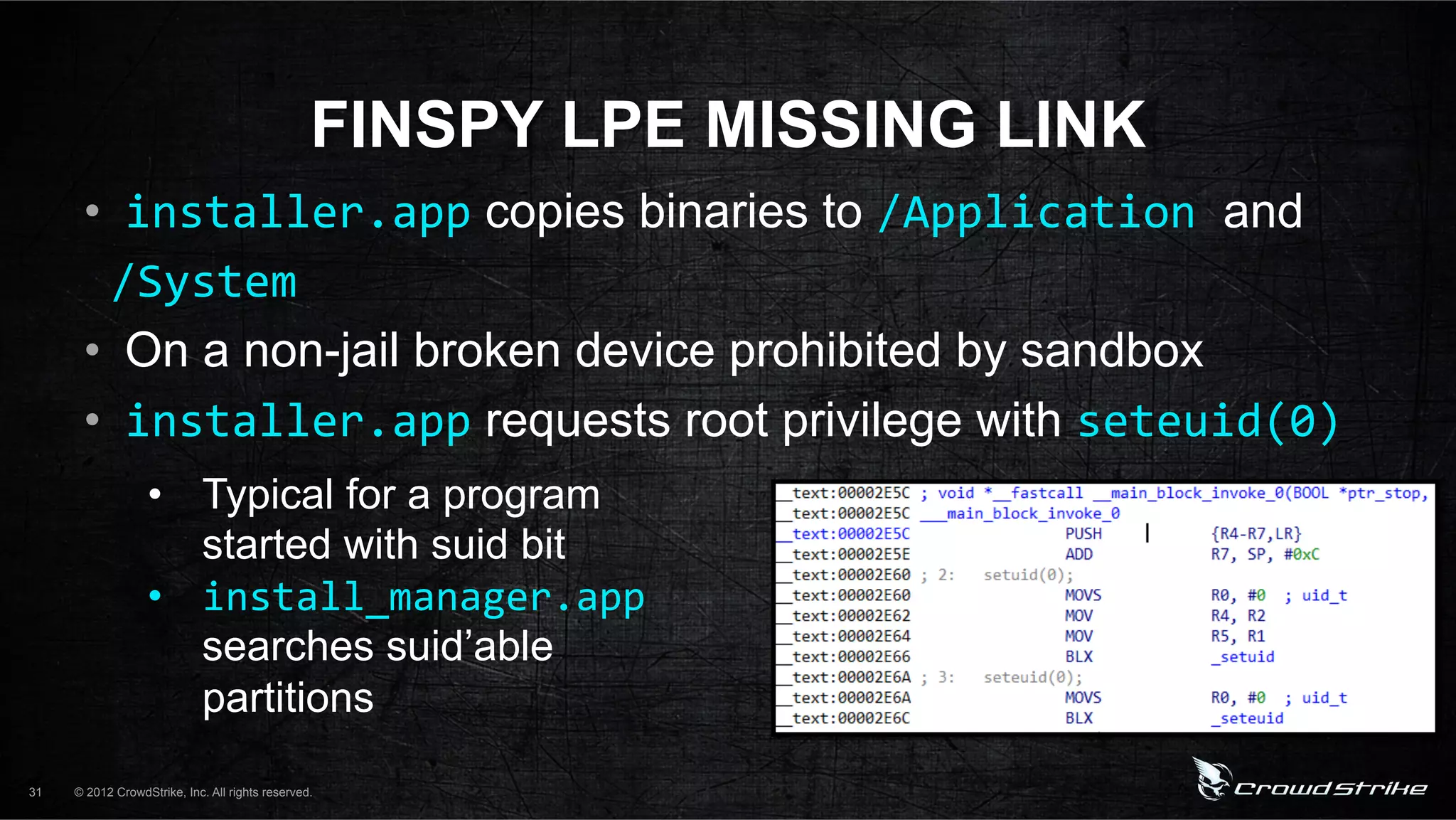
The document introduces CrowdStrike speakers George Kurtz, Georg Wicherski, and Alex Radocea. It then discusses the evolution of threats from commercial remote access tools (RATs) to targeted RATs and advanced threats. Examples of commercial RATs like FlexiSPY and targeted RATs like LuckyCat are analyzed. The feasibility of developing exploits and native Android RATs is also explored.


























![FEASIBILITY FOR NATIVE
RAT FOR ANDROID
• Native stand-alone executables are easily built using the NDK
– Creating a Makefile and a “Hello World” is < 2 hours if familiar with GCC
• Huge amount of new “App Analysis (Dalvik) Experts”
– Has anyone of those ever analyzed native ARM code?
– Can anyone of those handle a simple UPX packed binary?
• No Rootkit required, people barely look at native processes
– Native processes do not show up in Android or 3rd party Task Managers
– Potentially visible in ps%but trivially obfuscated
– strcpy(argv[0],%“…”)%
37 © 2012 CrowdStrike, Inc. All rights reserved.](https://image.slidesharecdn.com/hackingexposedlivemobiletargetedthreatsseptember12-120920101757-phpapp01/75/Hacking-Exposed-Live-Mobile-Targeted-Threats-37-2048.jpg)