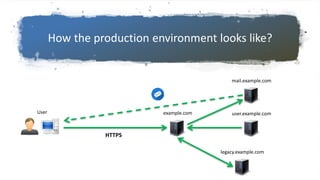
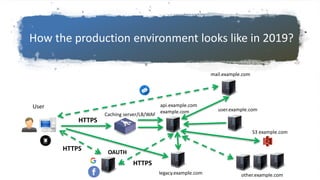
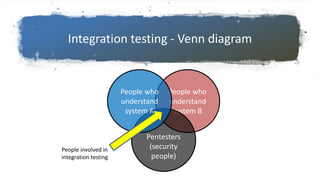
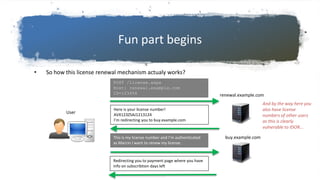
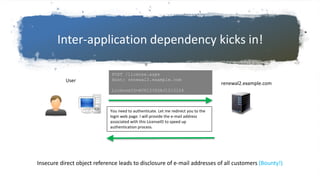
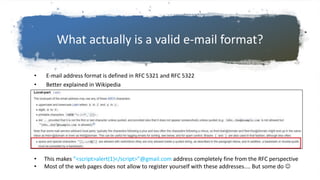
This document discusses hunting for vulnerabilities across interconnected applications. It describes two cases where the author found multiple vulnerabilities by exploring dependencies between applications. In the first case, they discovered vulnerabilities by interacting with a desktop application and related web applications from the same company, finding 5 vulnerabilities including XSS issues and information disclosures. In the second case, they used a single sign-on system across multiple applications to introduce persistent XSS vulnerabilities. The document advocates considering how applications integrate and interact to uncover "inter-application vulnerabilities" that may not be found through isolated testing.