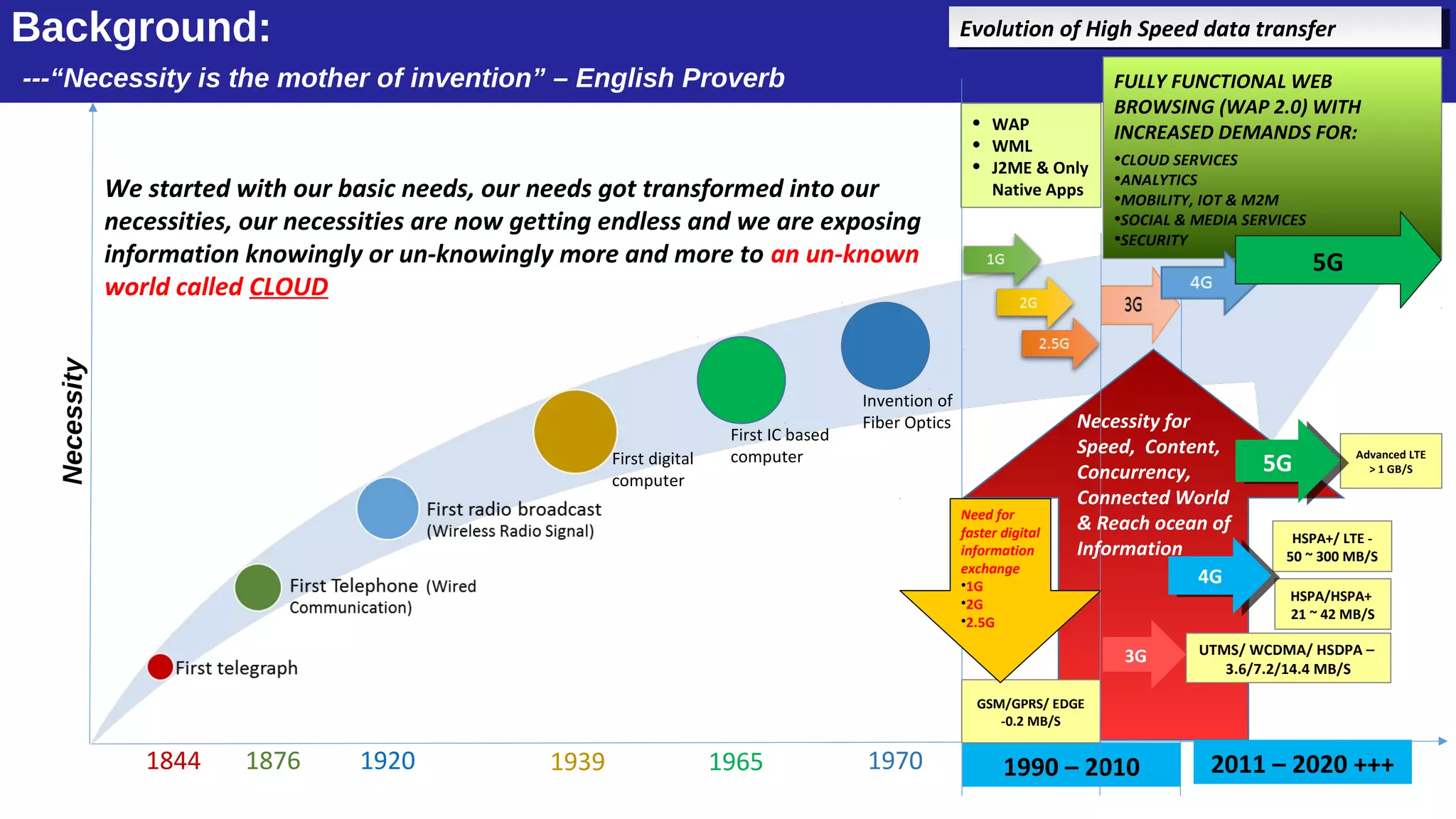
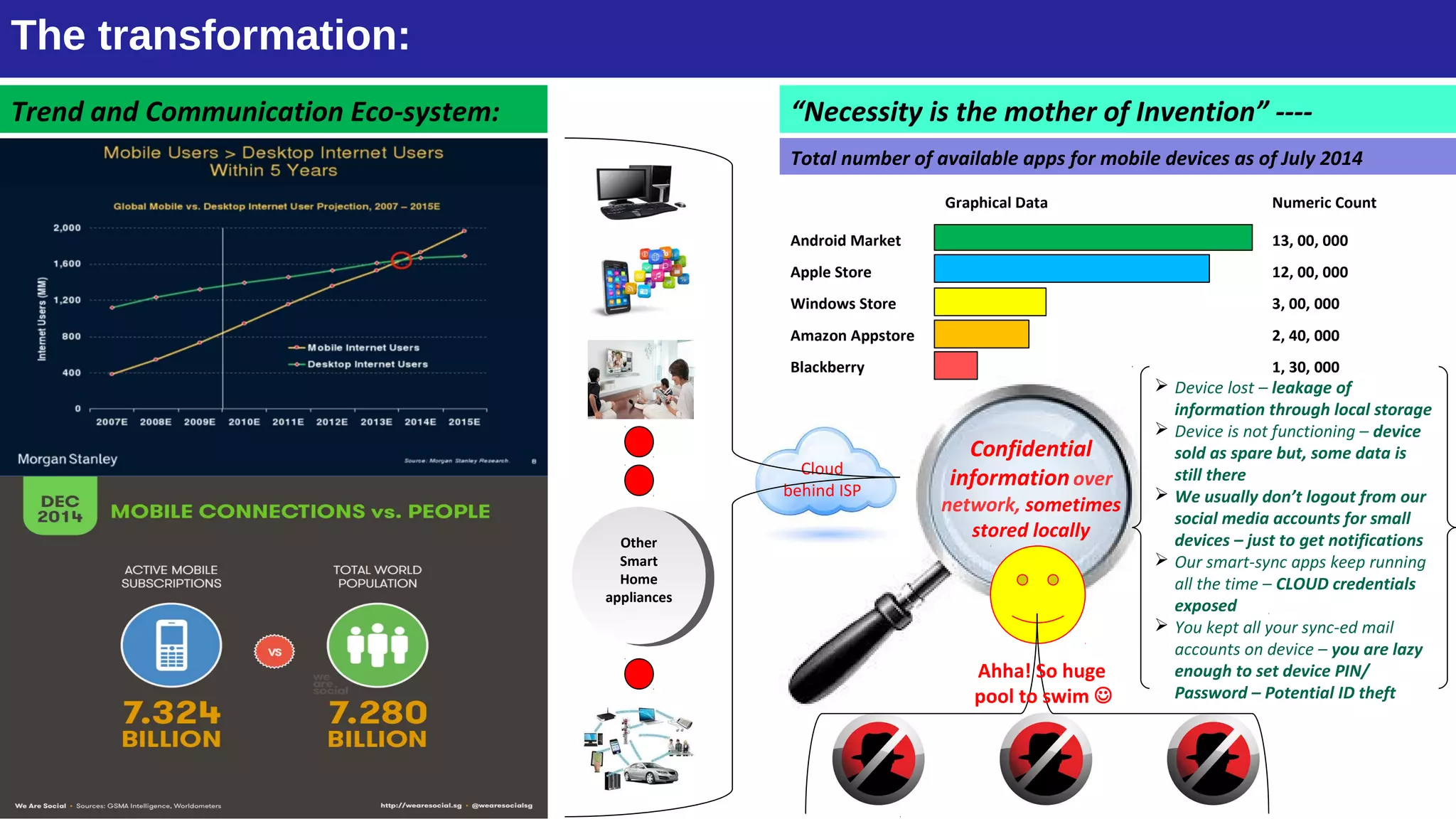
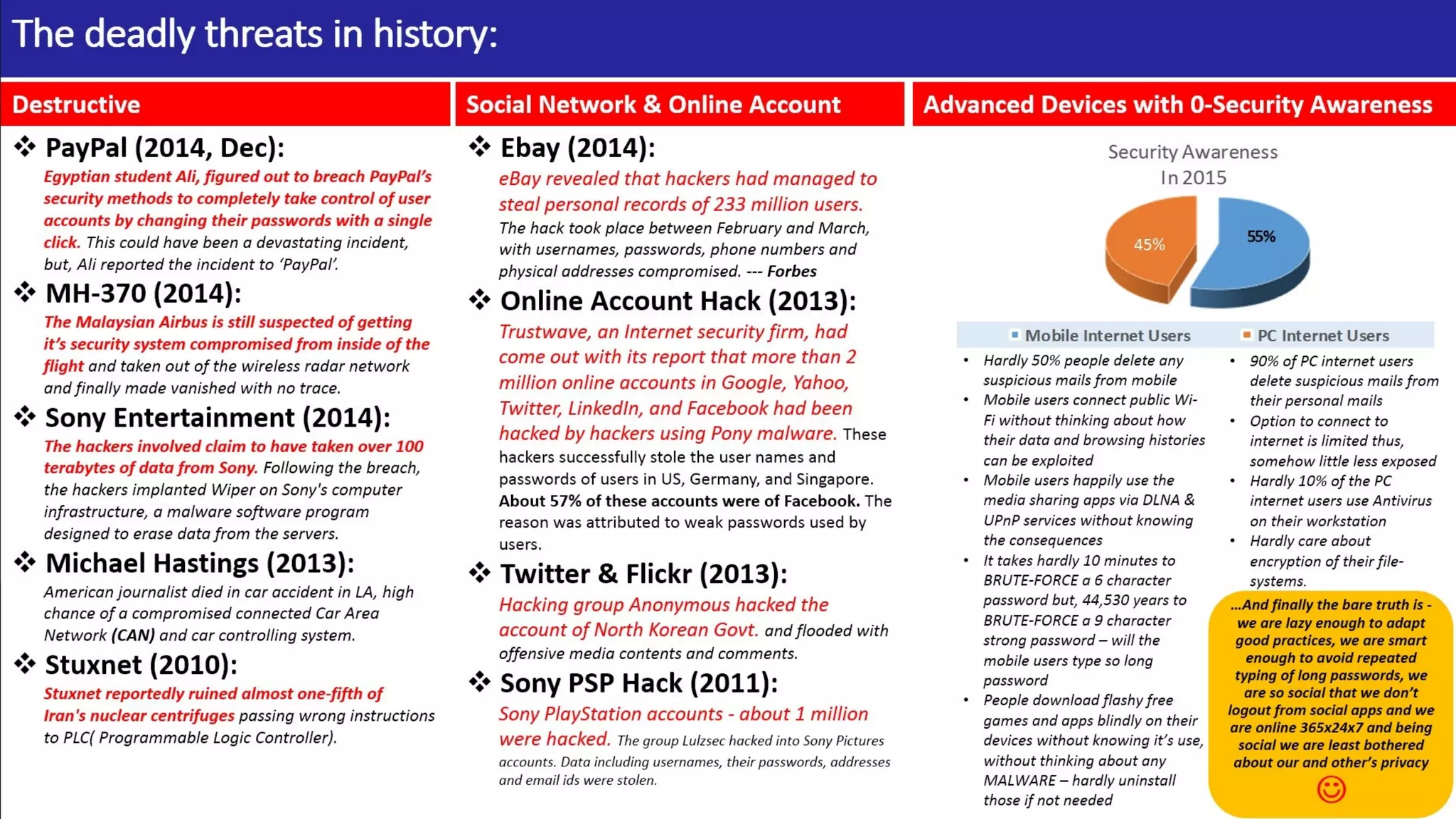
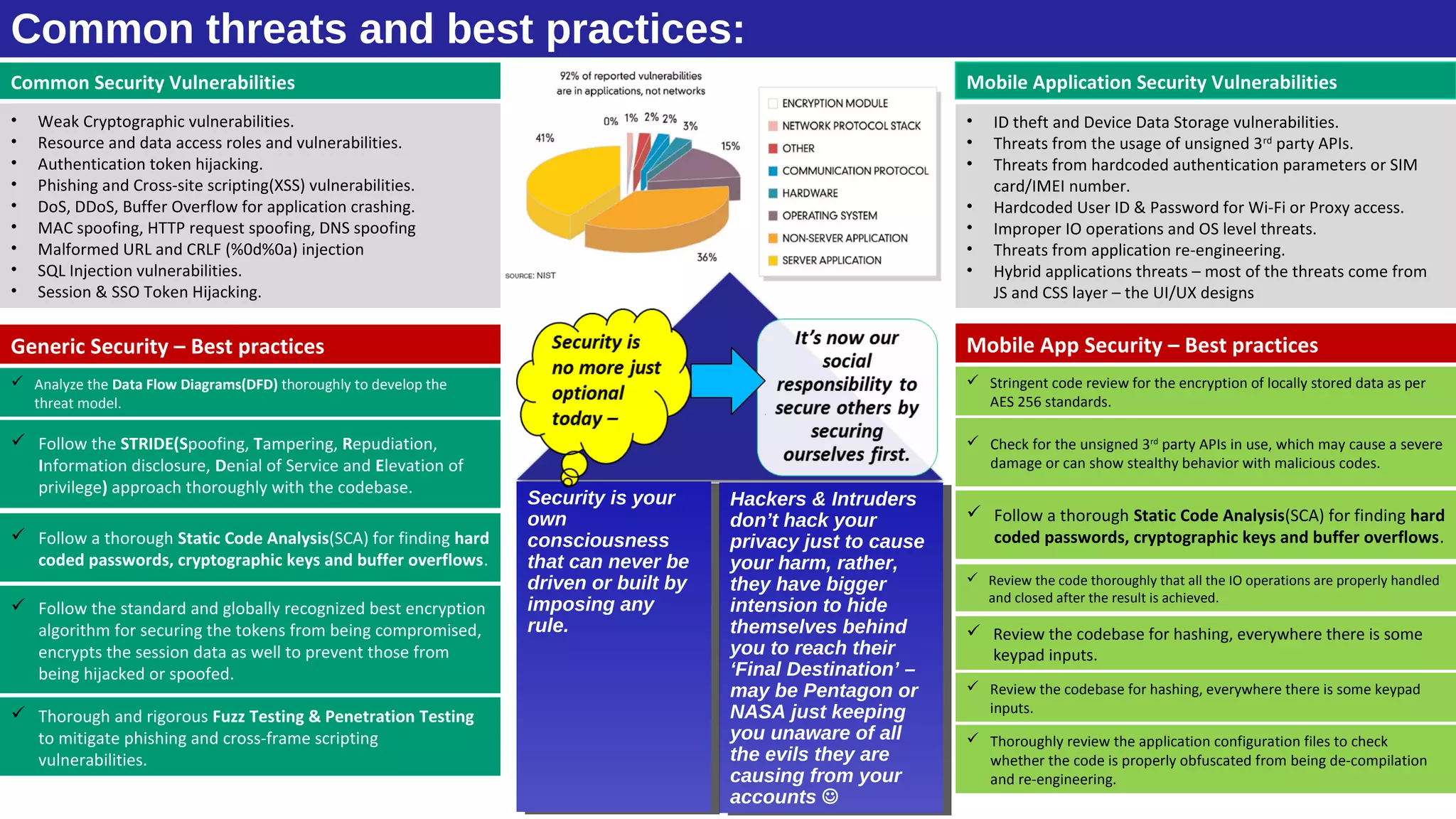
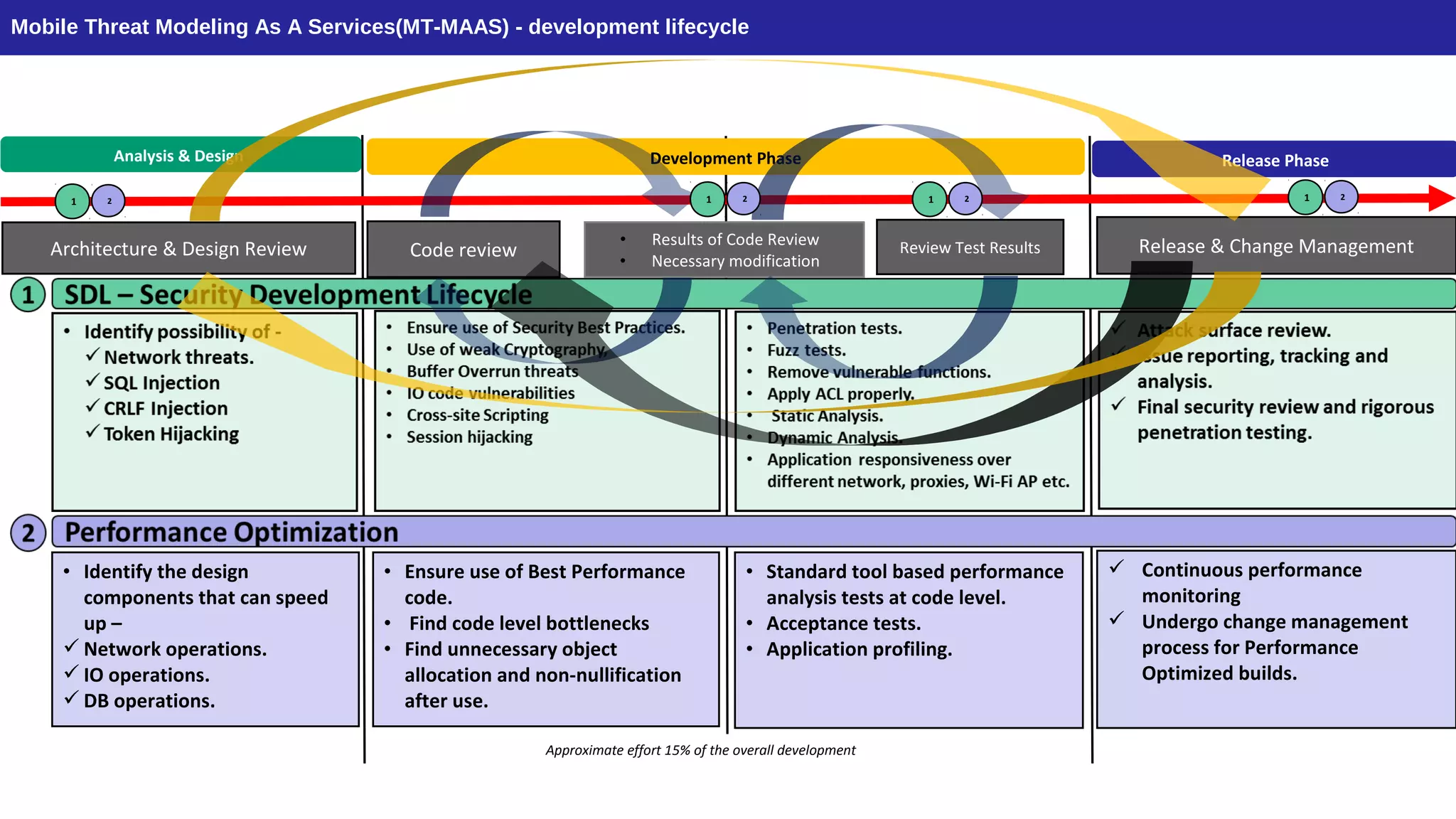
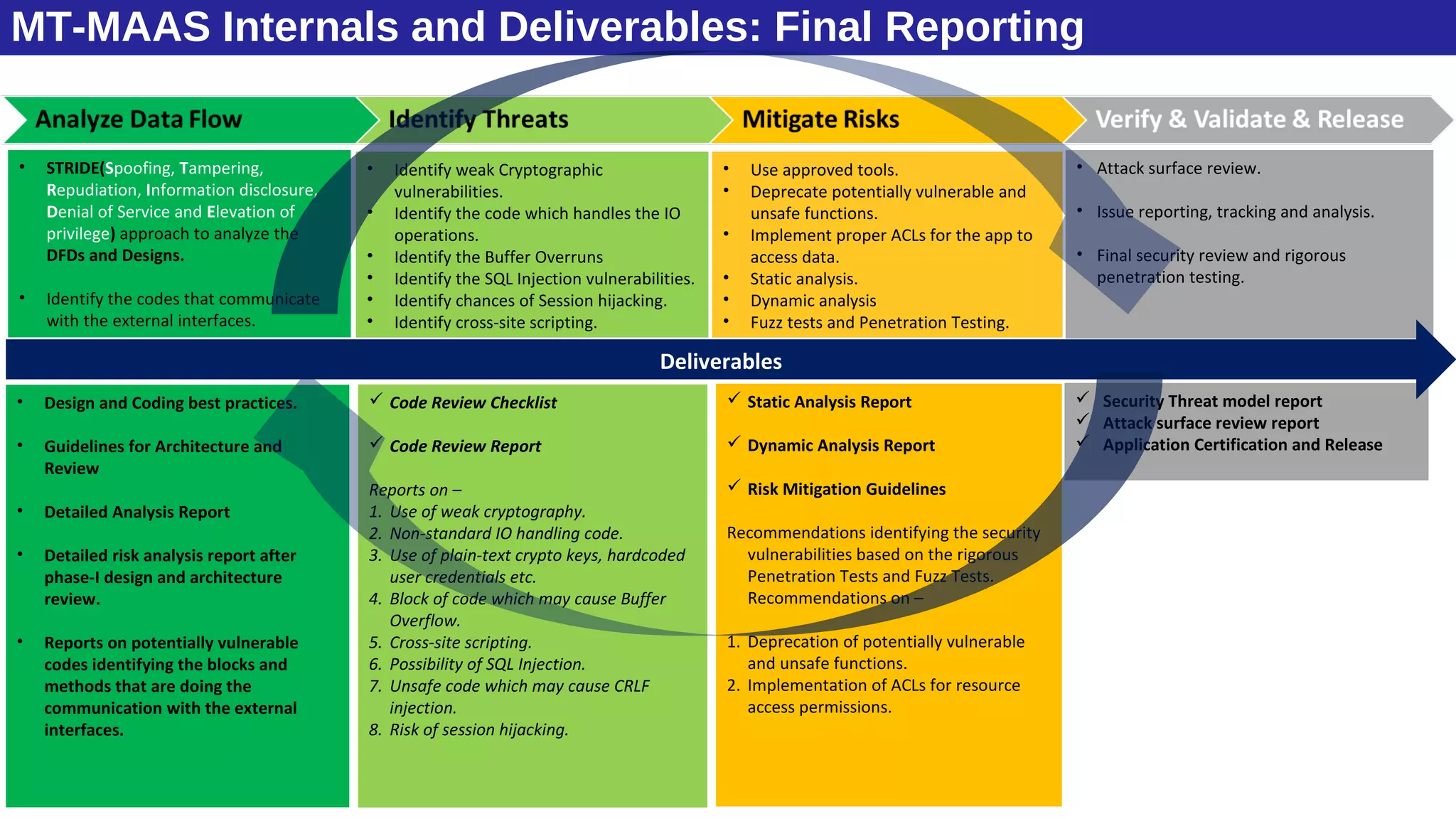
The document discusses the evolution of mobile technology and the increasing threats associated with mobile applications, highlighting common security vulnerabilities such as ID theft, DDoS attacks, and SQL injection. It outlines best practices for mobile app security, including thorough code review, static analysis, and the use of encryption algorithms to safeguard data. Additionally, it introduces Mobile Threat Modeling as a Service (MT-MaaS), detailing its development lifecycle, internal processes, and deliverables for managing security risks in mobile applications.