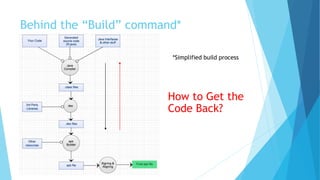
This document discusses techniques for analyzing and exploiting Android applications. It begins by explaining why security is important given people's growing dependency on digital technology and mobile devices. It then discusses decompiling APK files and using tools like Apktool, Dex2Jar, and decompilers to view an app's code. The document also covers using proxies like Burp Suite and Frida to intercept network traffic and manipulate app behavior at runtime. The goal is usually to obtain sensitive data, bypass restrictions, or modify the app. Examples of scenarios explored include tampering with network requests, bypassing security checks, and decrypting encrypted data.