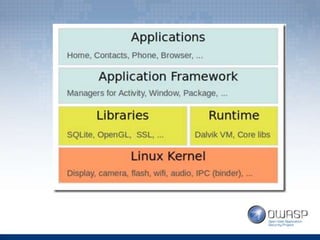
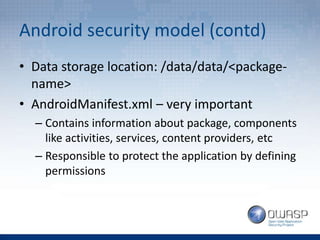
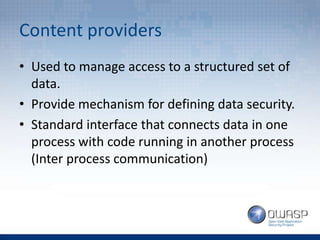
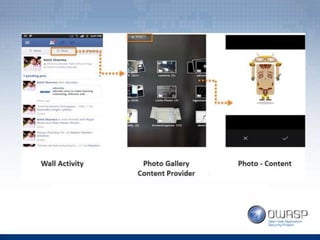
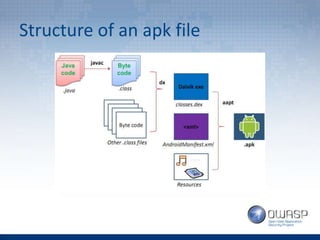
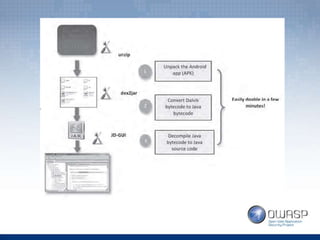
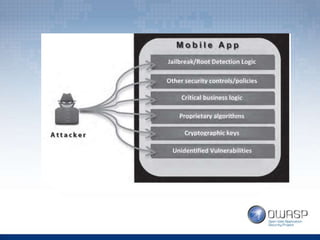
The document covers topics related to Android penetration testing including the Android security model, software stack, content providers, and secure coding practices. The Android security model uses app isolation and each app runs in its own Dalvik Virtual Machine. Content providers manage access to structured app data and enable inter-process communication. Reverse engineering the APK file by extracting and decompiling it is demonstrated as part of the app security testing process. Common insecure practices like hardcoding sensitive data and lack of encryption are also discussed.