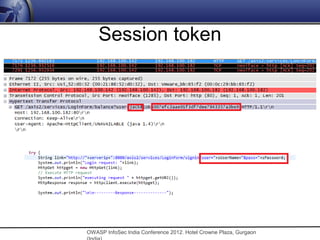
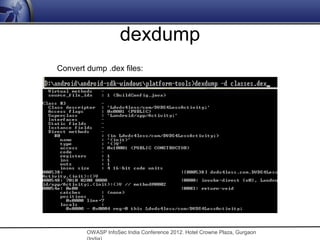
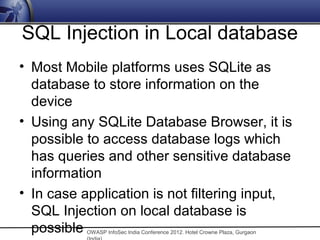
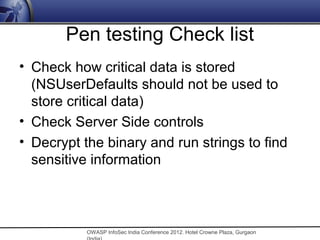
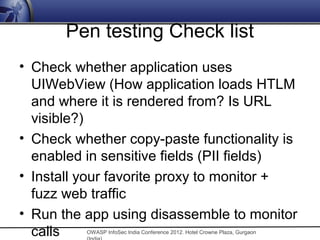
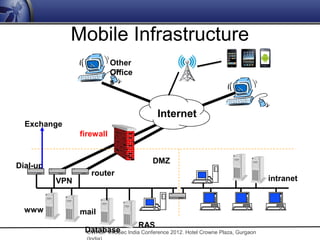
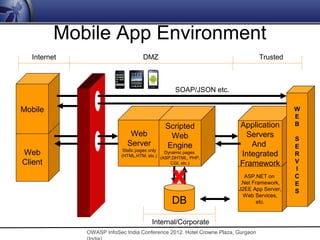
The document discusses security issues related to mobile applications. It notes that mobile applications now store and process data both on the client and server sides, exposing them to vulnerabilities on both ends. Common vulnerabilities include insecure storage of sensitive data like credentials on the device, and insecure network communication that allows man-in-the-middle attacks when mobile devices use untrusted networks. The document advocates for effective security testing of mobile applications to identify and address such risks.


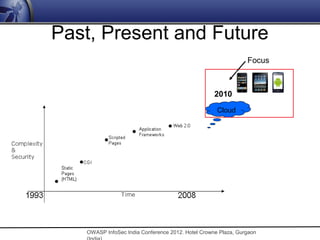
![Enterprise Technology Trend
• 2007. Web services would rocket from $1.6
billion in 2004 to $34 billion. [IDC]
• 2008. Web Services or Service-Oriented
Architecture (SOA) would surge ahead.
[Gartner]
• 2009. Enterprise 2.0 in action and penetrating
deeper into the corporate environment
• 2010. Flex/HTML5/Cloud/API
• 2012. HTML5/Mobile era.
OWASP InfoSec India Conference 2012. Hotel Crowne Plaza, Gurgaon](https://image.slidesharecdn.com/mobileappsec-120830061303-phpapp01/85/Mobile-Application-Security-Effective-methodology-efficient-testing-3-320.jpg)
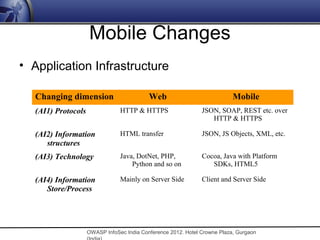
![Mobile Changes
• Security Threats
Changing dimension Web Mobile
(T1) Entry points Structured Scattered and multiple
(T2) Dependencies Limited • Multiple technologies
• Information sources
• Protocols
(T3) Vulnerabilities Server side [Typical • Web services [Payloads]
injections] • Client side [Local Storage]
(T4) Exploitation Server side exploitation Both server and client side
exploitation
OWASP InfoSec India Conference 2012. Hotel Crowne Plaza, Gurgaon](https://image.slidesharecdn.com/mobileappsec-120830061303-phpapp01/85/Mobile-Application-Security-Effective-methodology-efficient-testing-11-320.jpg)