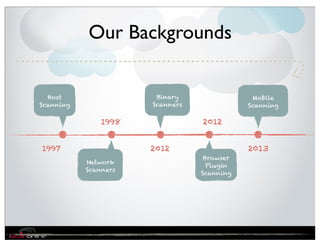
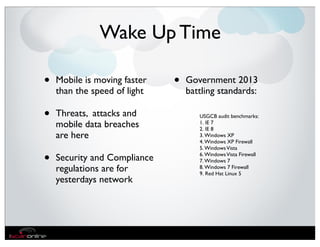
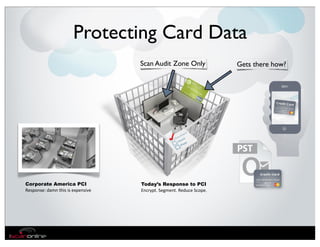
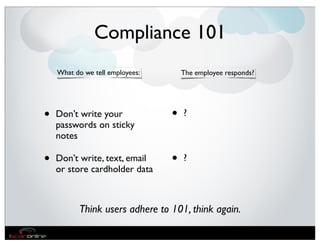
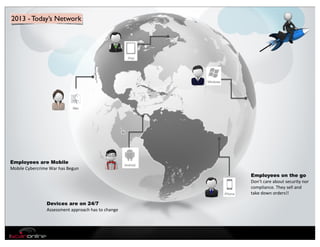
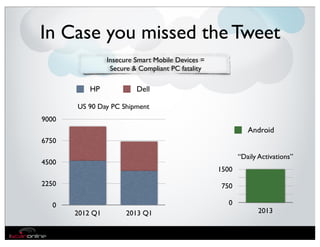
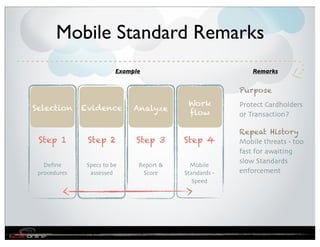
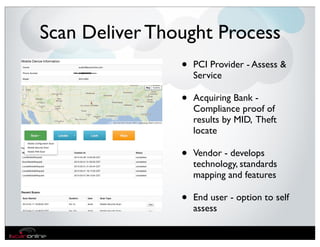
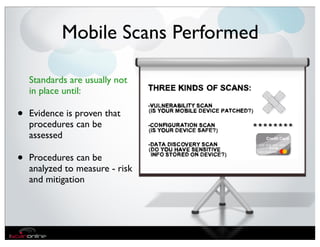
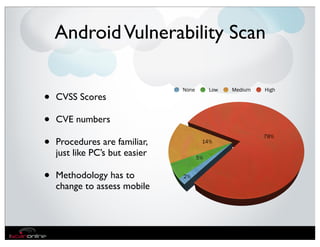
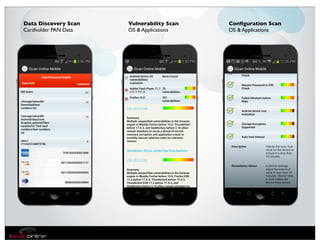
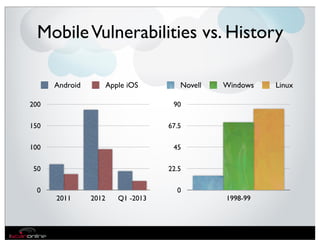
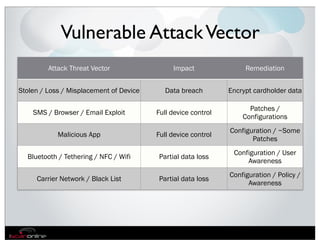
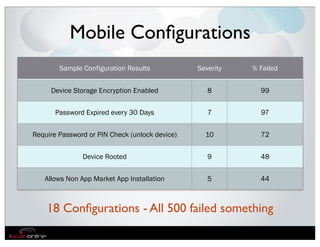
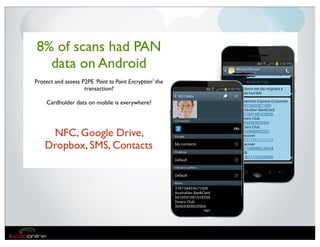
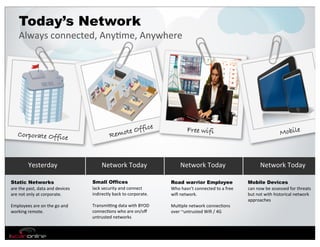
The document discusses the evolution of mobile security and compliance challenges faced by corporate America in light of the PCI DSS standards. It highlights the rapid growth of mobile device use and associated threats, emphasizing the need for updated security protocols to address vulnerabilities in mobile environments. Strategies such as encryption, employee training, and enhanced auditing processes are suggested to mitigate risks associated with mobile data breaches.