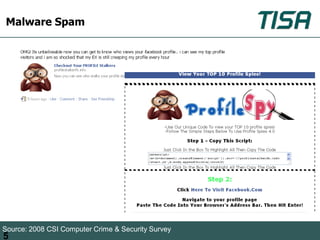
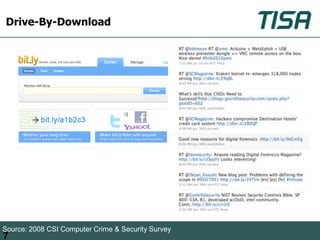
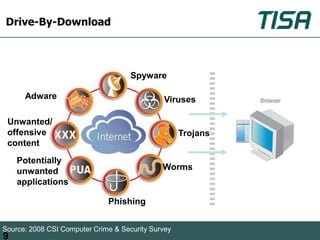
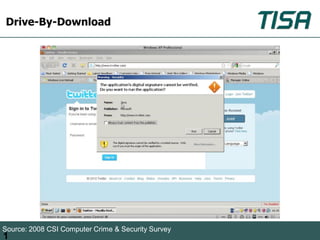
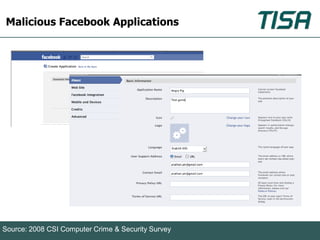
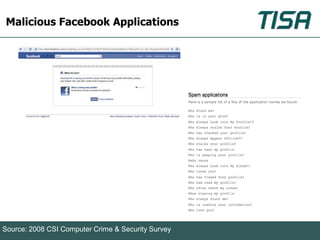
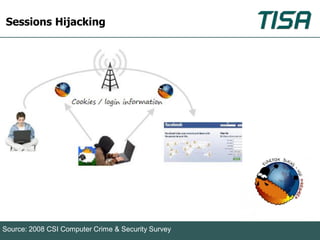
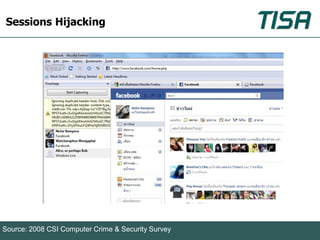
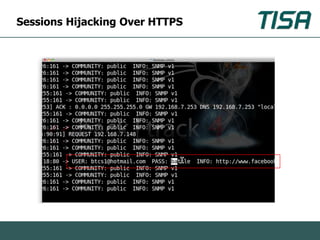
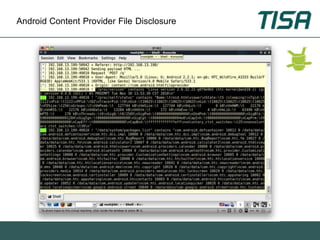
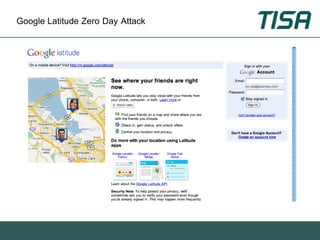
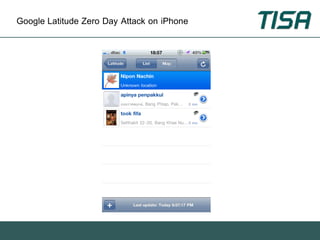
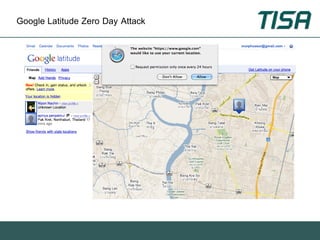
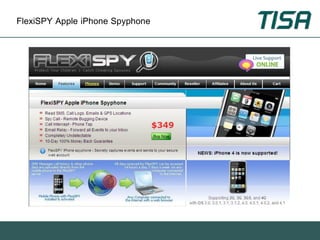
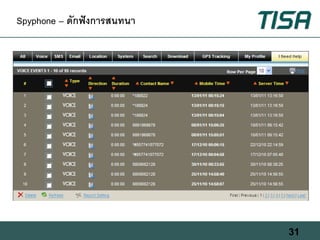
This document summarizes advanced social network and mobile attacks. It discusses threats like malware spam, drive-by downloads, malicious applications, and session hijacking on social networks. It also outlines threats to mobile devices, including vulnerabilities in mobile web browsers, content provider leaks on Android, and zero-day attacks using Google Latitude. Examples are provided of spyware targeting BlackBerry and iPhone users.