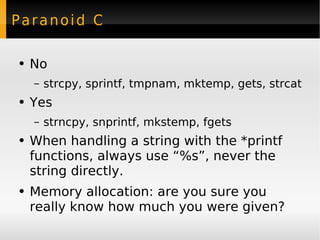
Kees Cook works to keep the Ubuntu operating system secure. His responsibilities include finding new vulnerabilities, checking mailing lists for reports of issues, performing code audits, triaging vulnerabilities by priority, finding or developing patches, testing patches, and publishing updated packages. He discussed various types of software vulnerabilities and mitigation strategies used in Ubuntu to improve security.
![Security For Human Beings Protecting Ubuntu http://outflux.net/oscon/07/security.odp Kees Cook [email_address] [email_address] http://outflux.net/blog/ OSCON 2007](https://image.slidesharecdn.com/os-cook483/75/Os-Cook-1-2048.jpg)







![Security Community Common Vulnerabilities and Exposures http://cve.mitre.org/cve/ The central list of all known security bugs [email_address] private mailing list OSS distributor coordination Researchers, hackers, you name it full-disclosure mailing list bugtraq mailing list http://seclists.org/](https://image.slidesharecdn.com/os-cook483/85/Os-Cook-15-320.jpg)

![Questions? Kees Cook [email_address] [email_address] http://outflux.net/blog/](https://image.slidesharecdn.com/os-cook483/85/Os-Cook-18-320.jpg)