Embed presentation



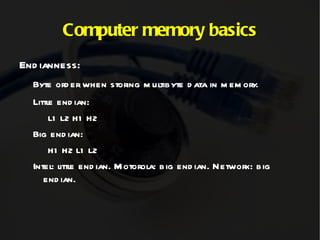

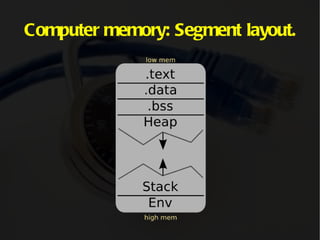
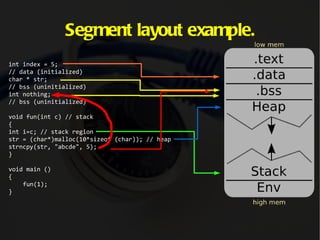

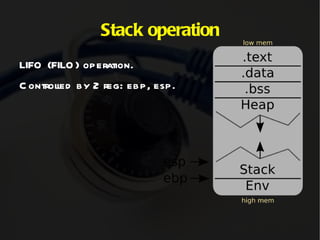
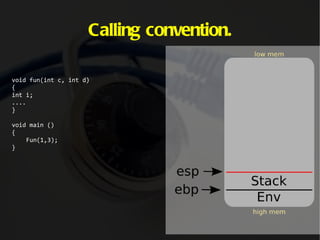
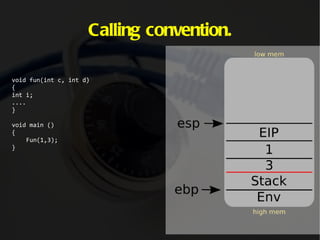
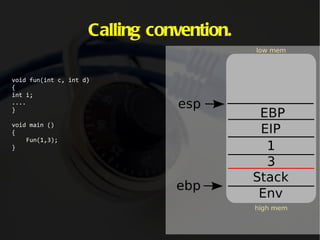
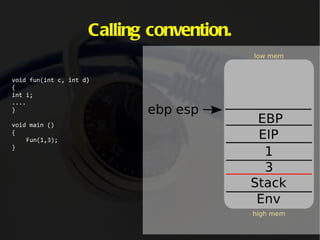



The document discusses computer memory layout and calling conventions. It explains that programs are stored in segments like text, data, bss, heap and stack. The stack grows downward while the heap grows upward. When a function is called, parameters are pushed onto the stack and the instruction pointer is saved. The function then saves the base pointer and allocates space for local variables below it on the stack. A buffer overflow occurs when a program writes more data to a buffer than it was allocated to hold. Shellcode is program code designed to be injected and executed from the stack.

















