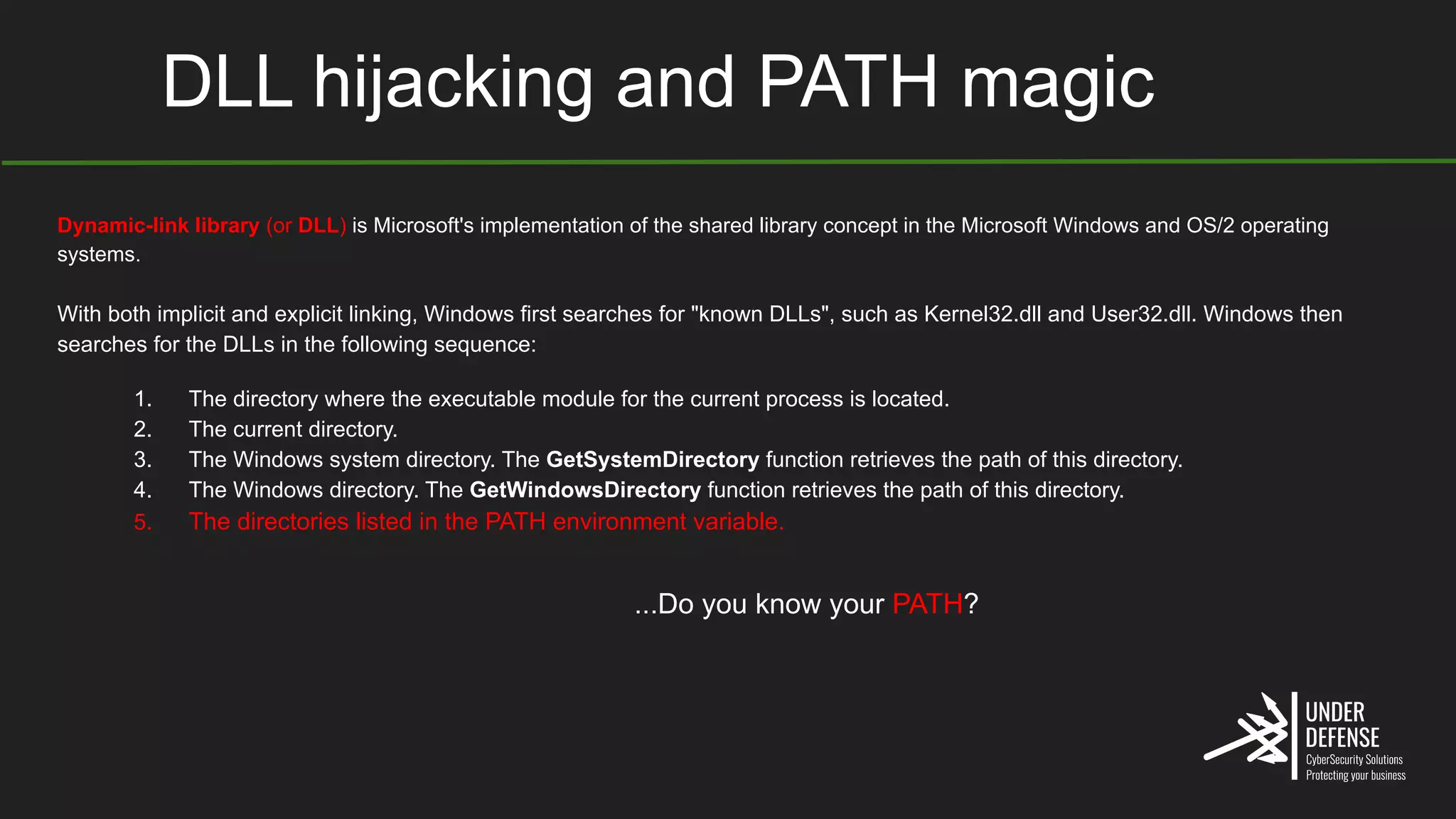
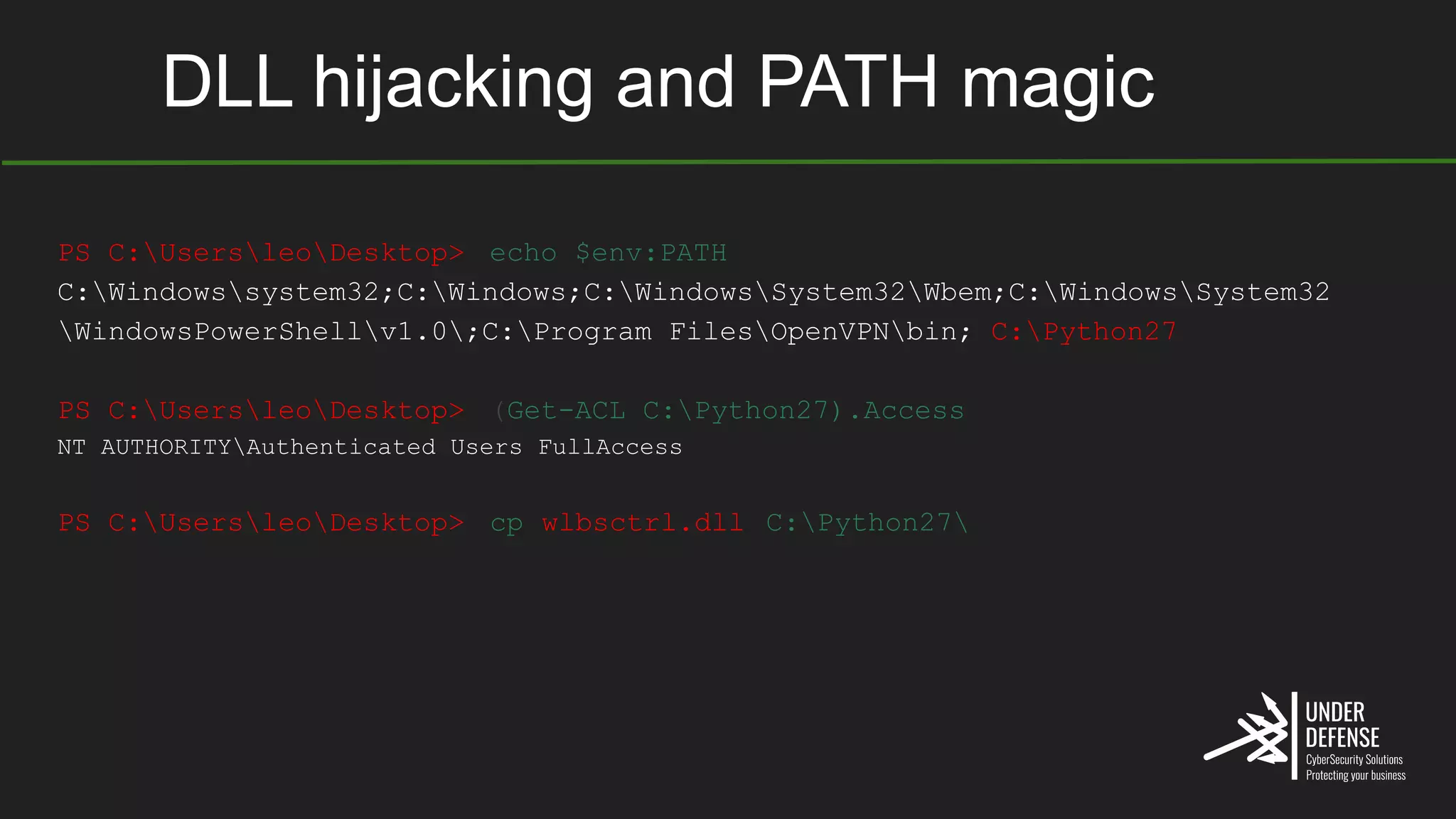
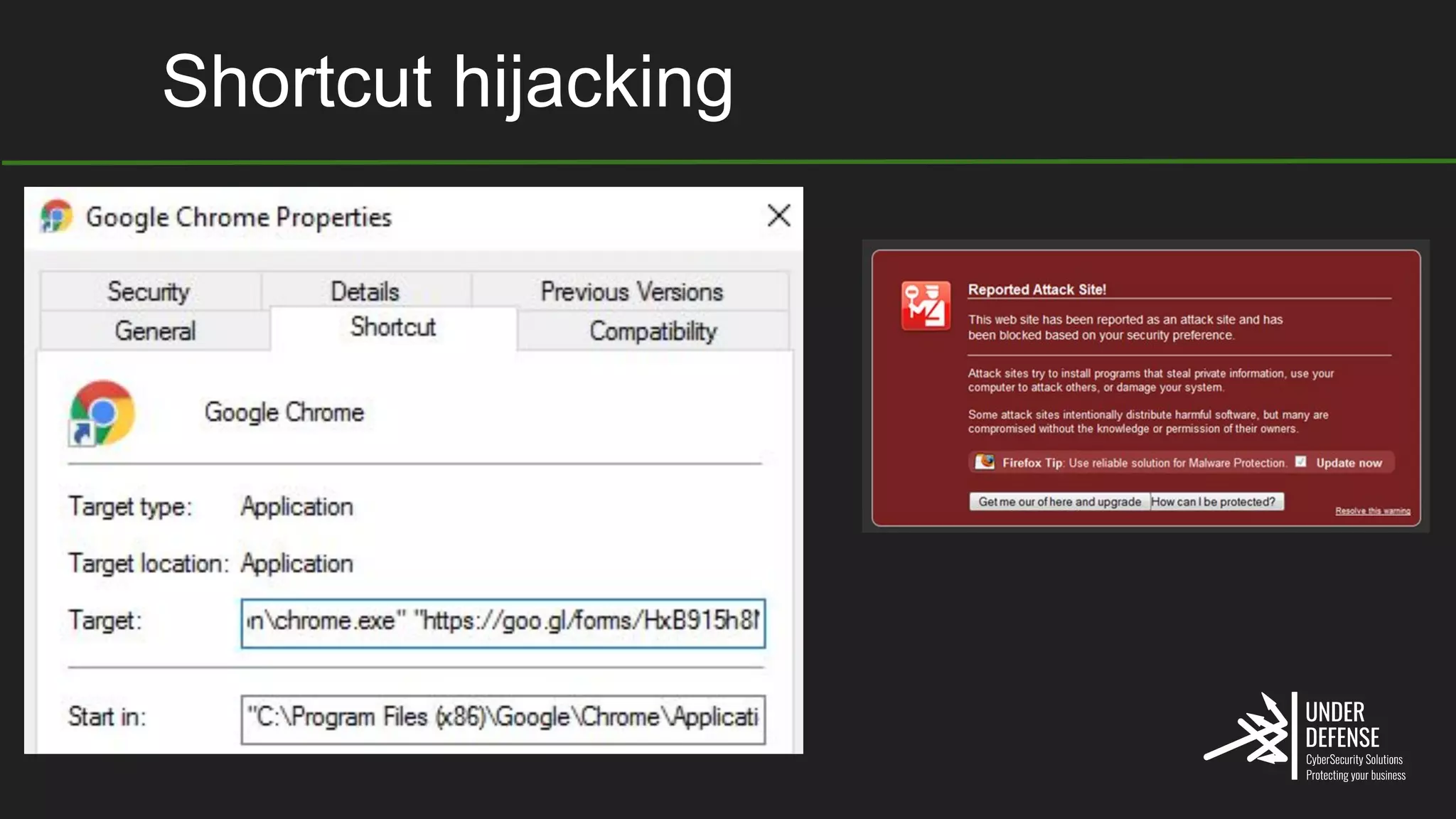
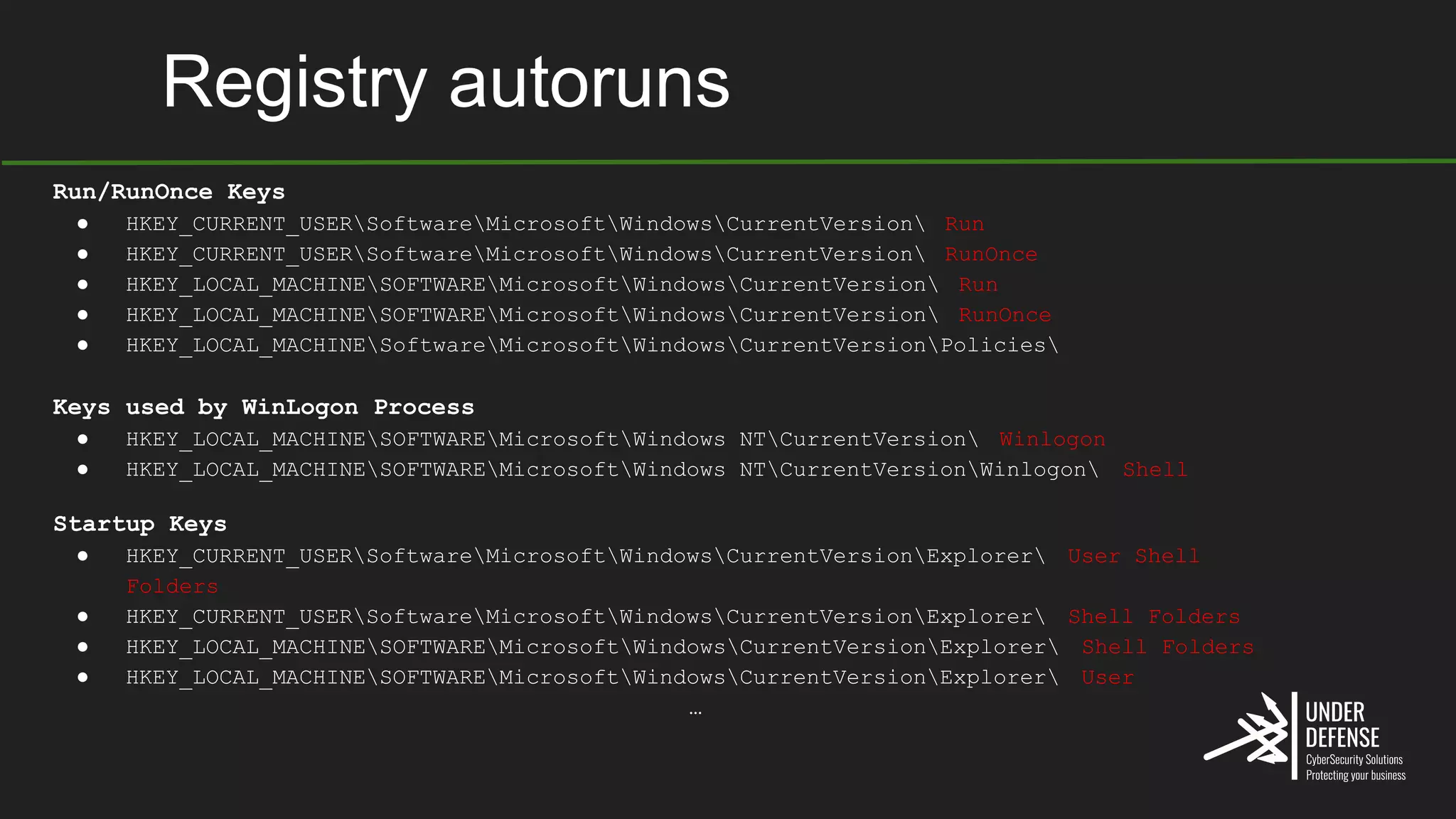
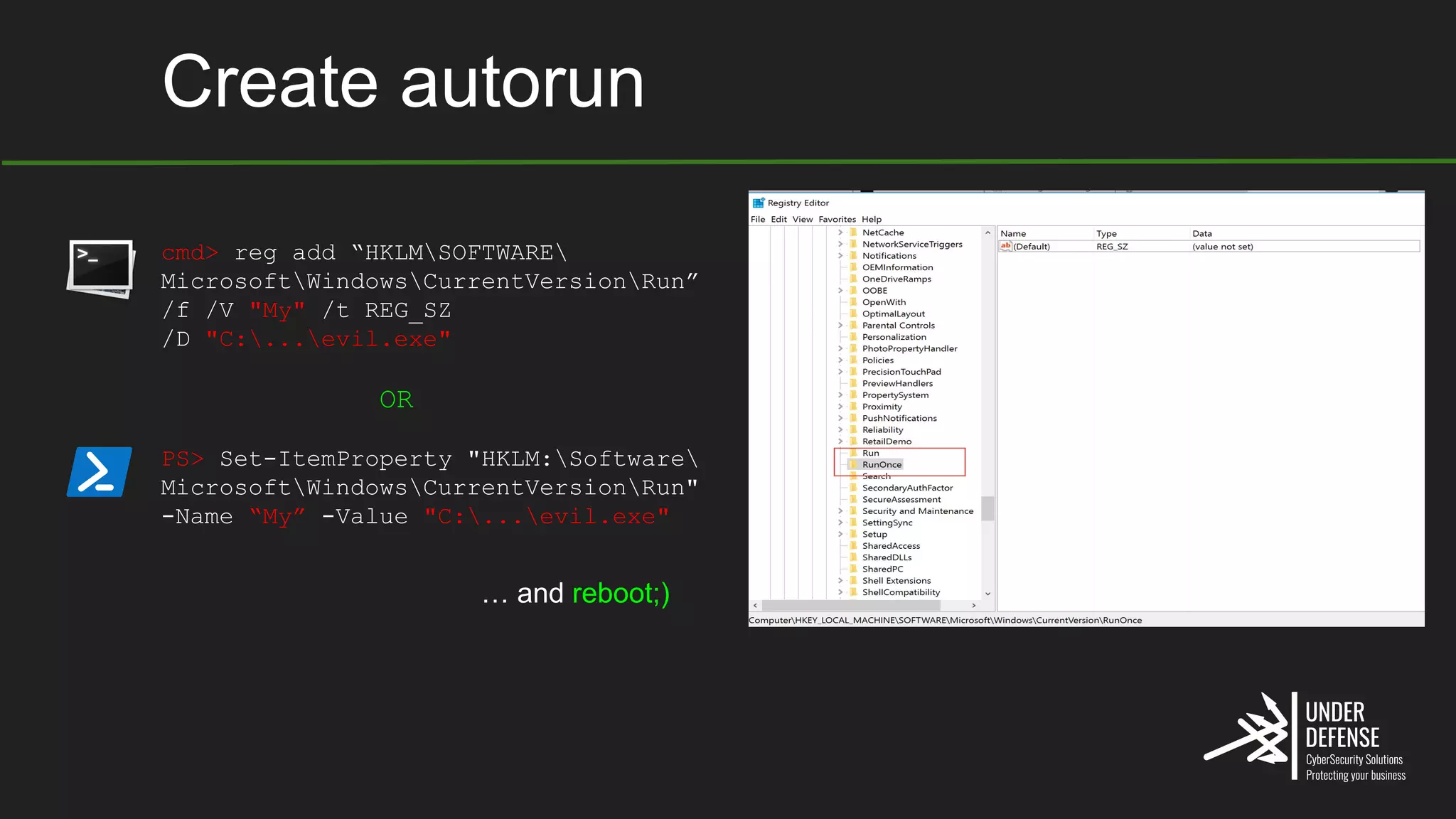
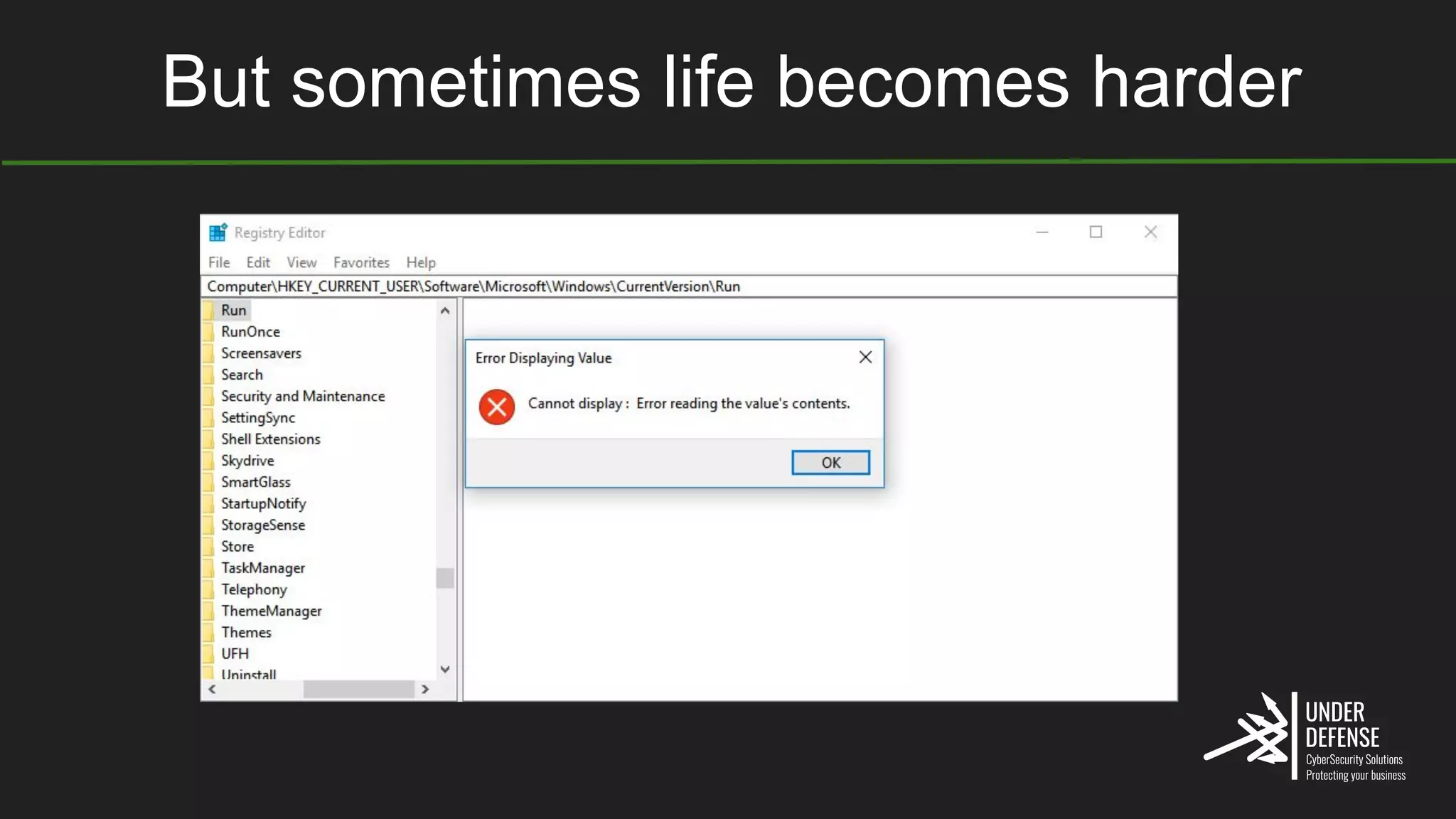
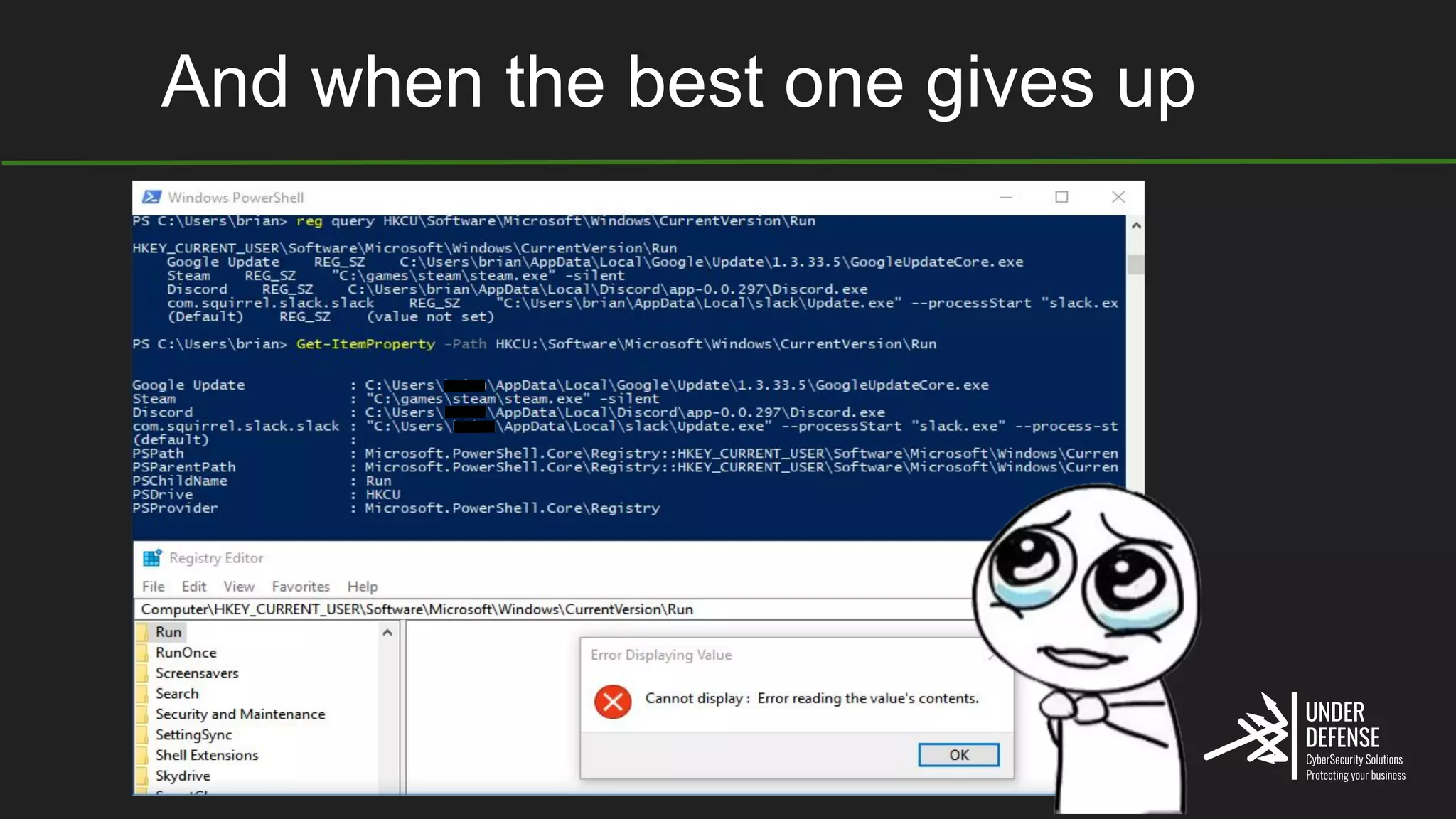
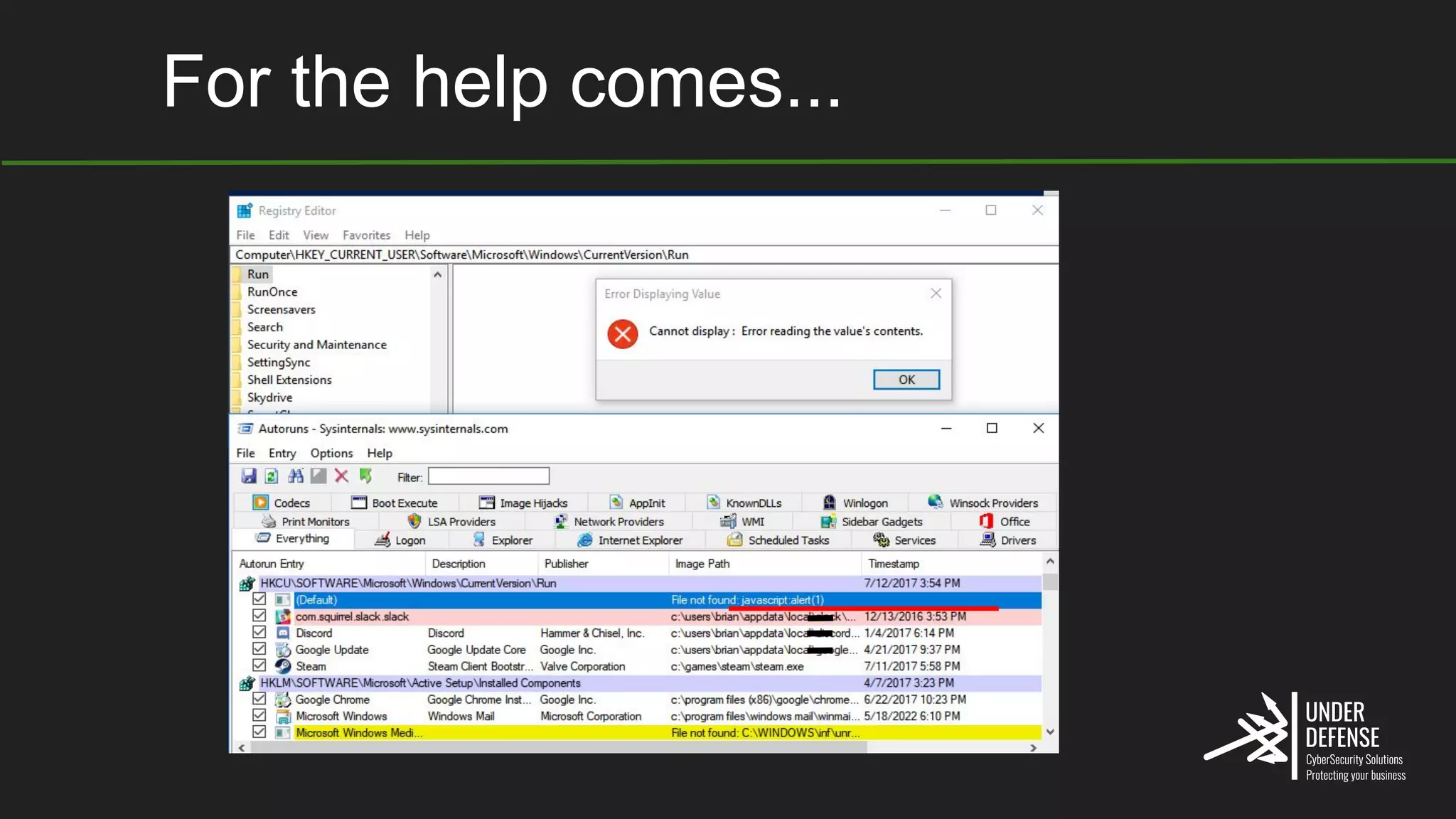
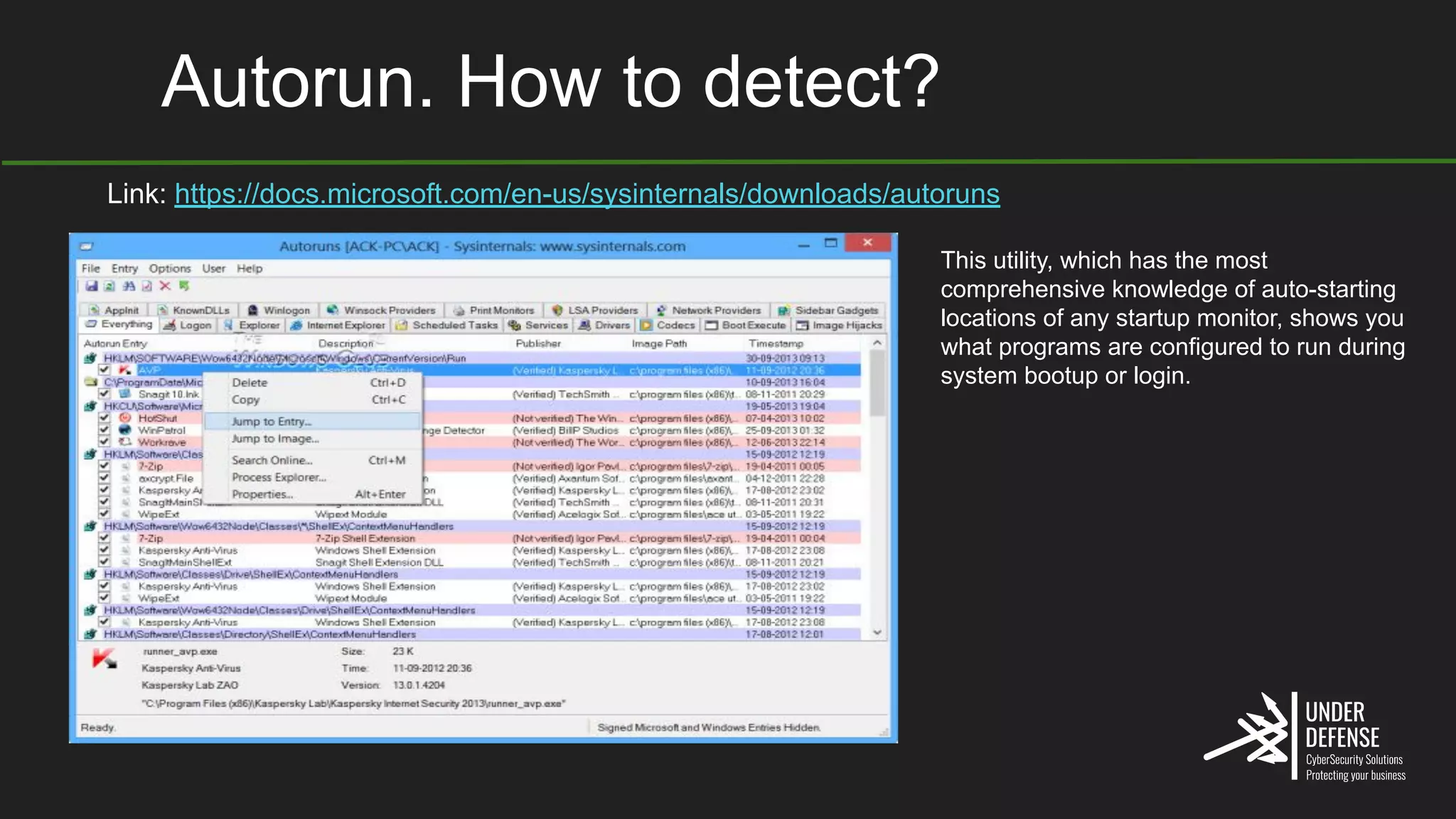
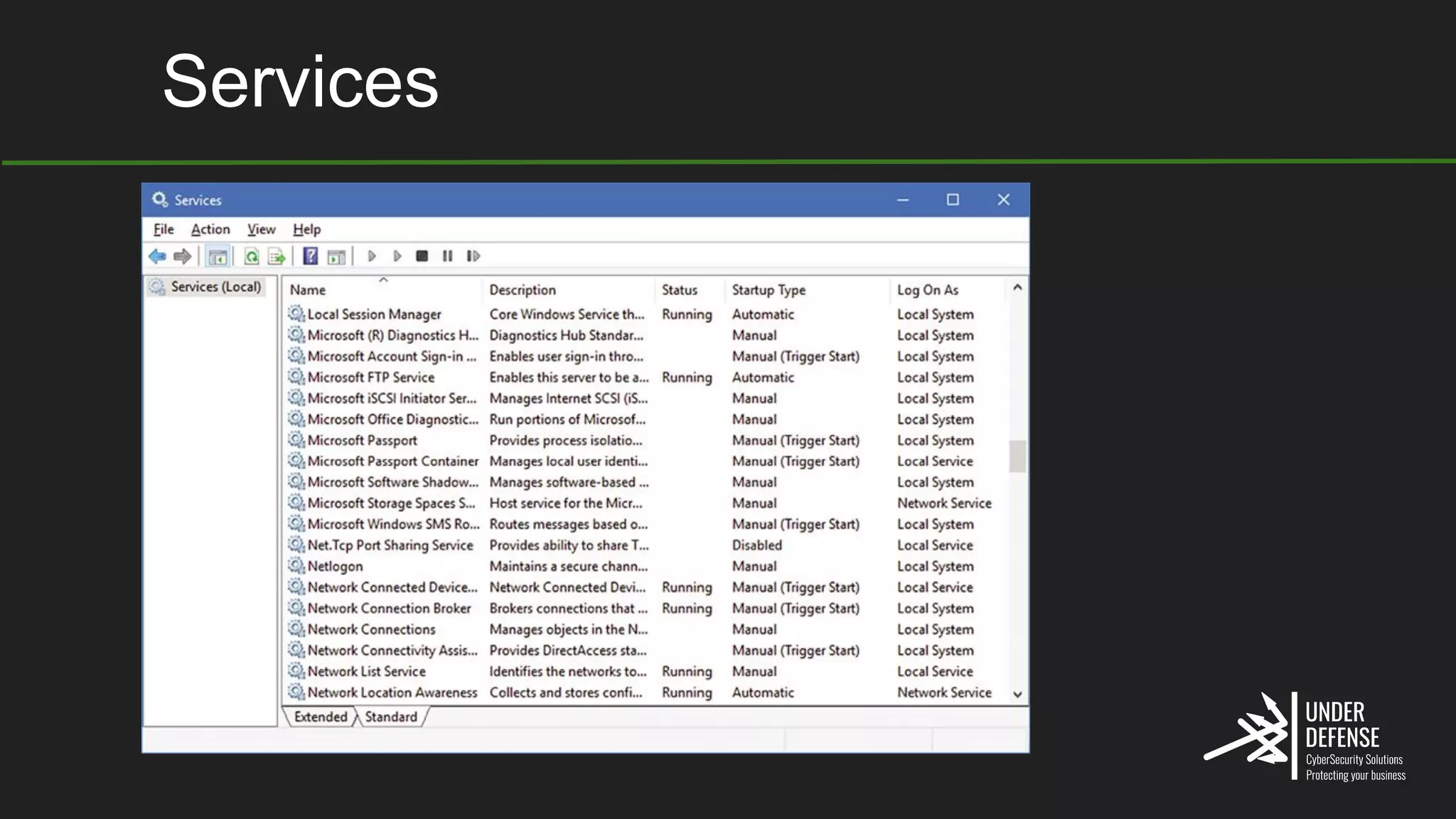
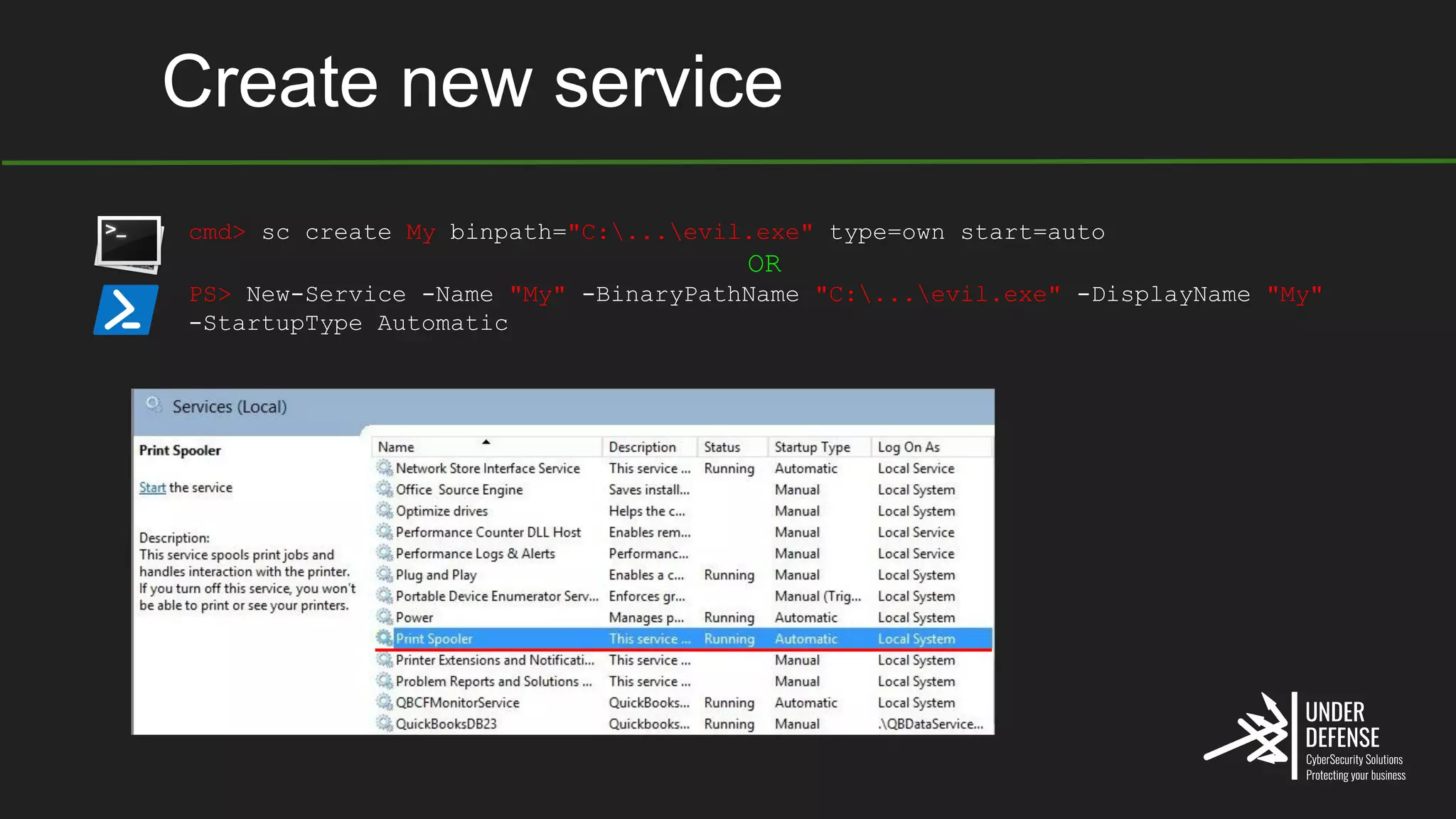
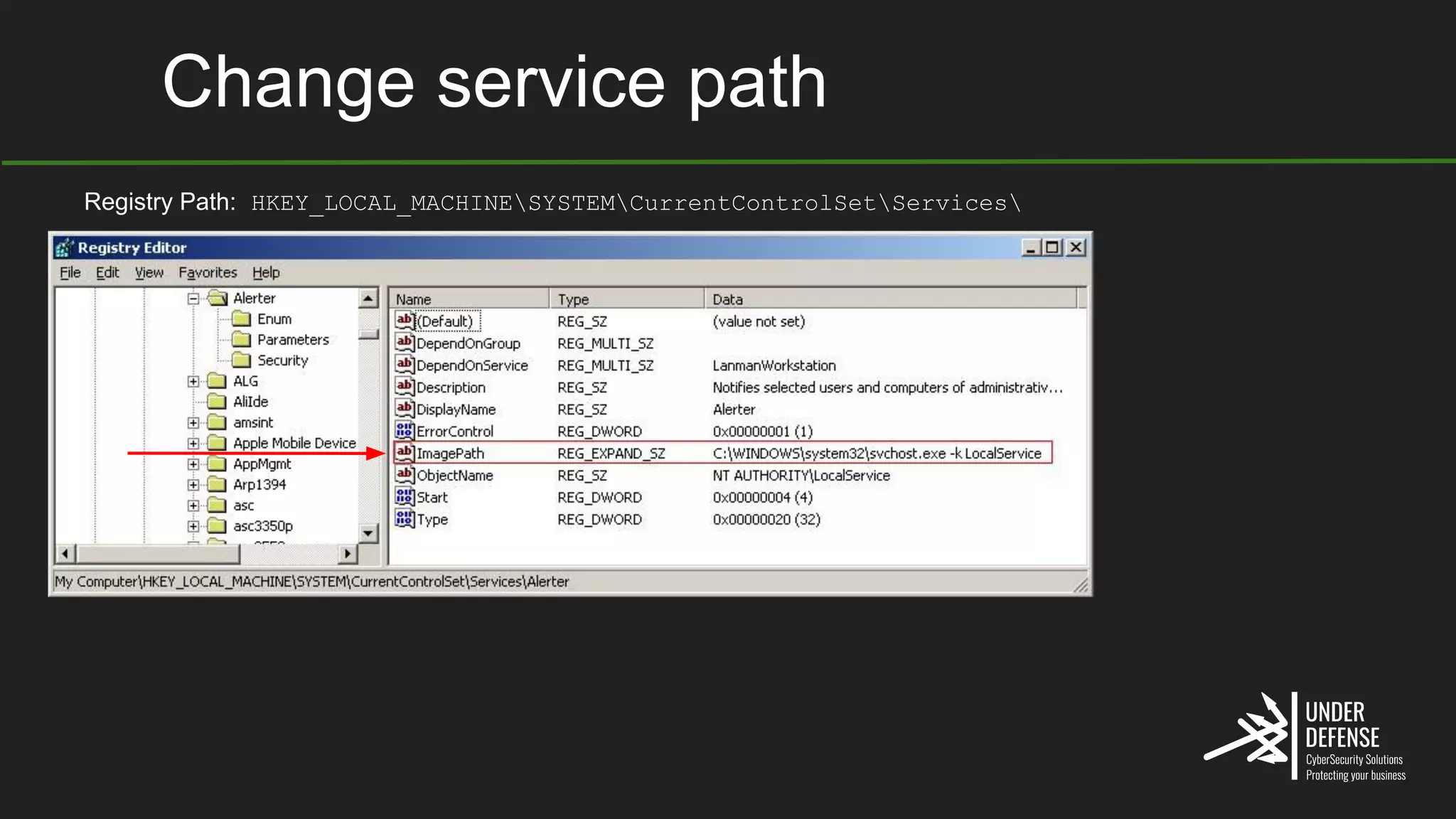
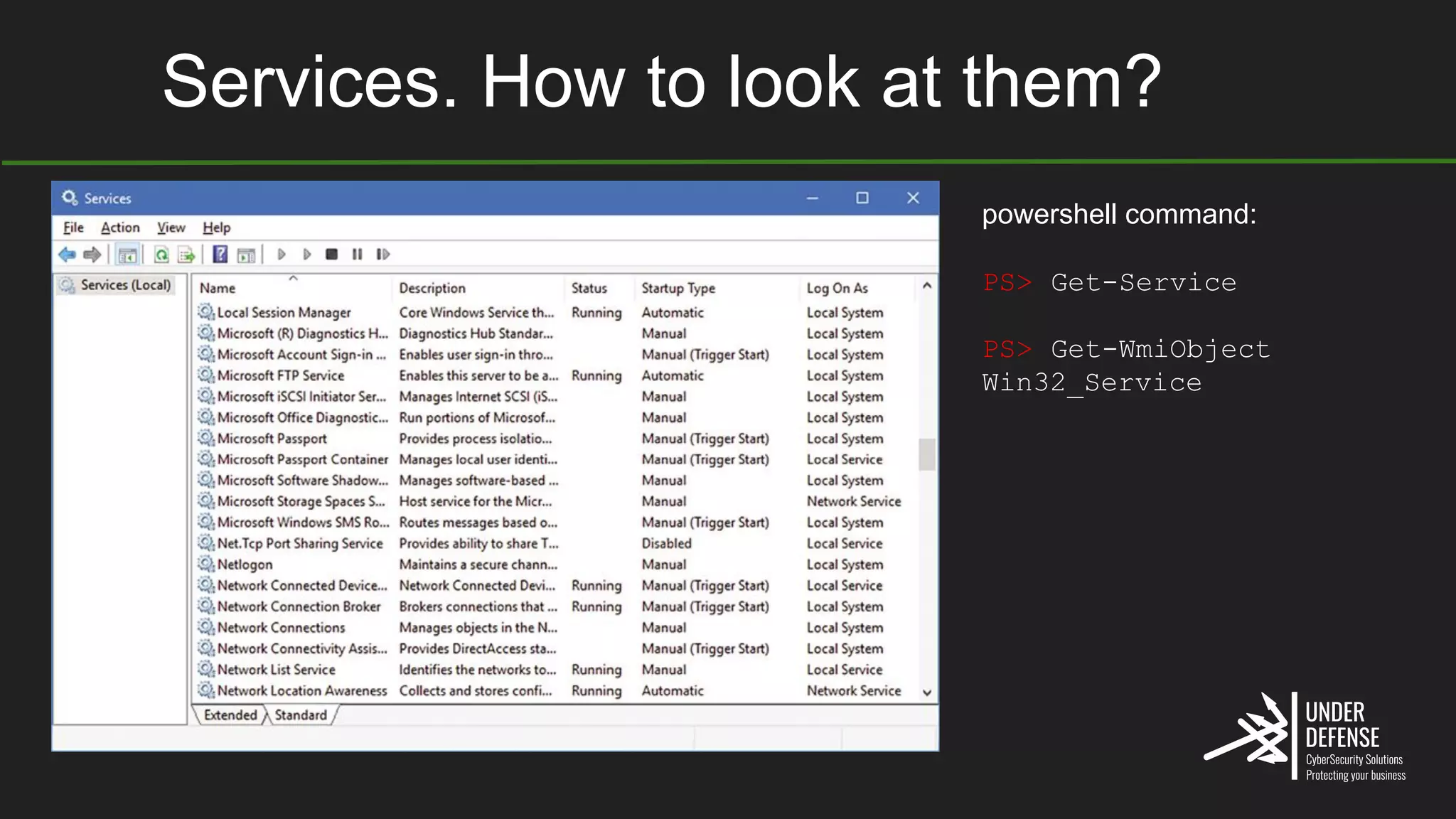
The document covers techniques for achieving and detecting persistence on Windows systems, particularly in the context of cybersecurity. It details methods for using Windows registry keys, services, scheduled tasks, and DLL hijacking to ensure malicious programs run at startup. Additionally, it provides commands for creating autoruns and detecting existing persistence mechanisms.





![Schedule tasks V1 (at). How?
cmd> at 08:00
/EVERY:m,t,w,th,f,s,su
"C:...evil.exe"
(ALWAYS SYSTEM priv)
C:Windowssystem32> at /?
The AT command schedules commands and
programs to run on a computer at
a specified time and date. The
Schedule service must be running to
use
the AT command.
AT [computername] [ [id] [/DELETE] |
/DELETE [/YES]]
AT [computername] time
[/INTERACTIVE]
[ /EVERY:date[,...] |
/NEXT:date[,...]] "command"](https://image.slidesharecdn.com/windowspersistence-211029114540/75/Windows-persistence-presentation-22-2048.jpg)