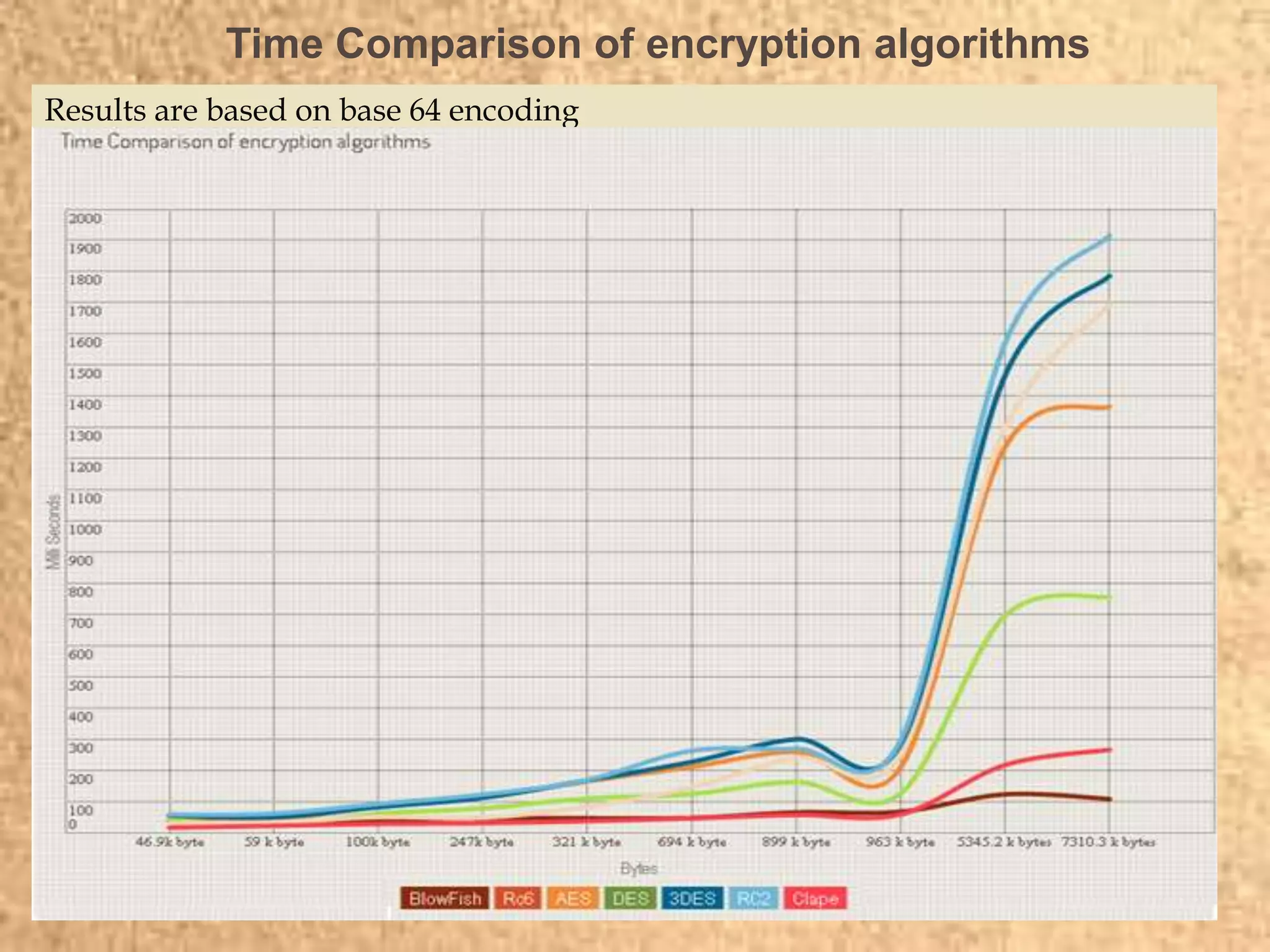
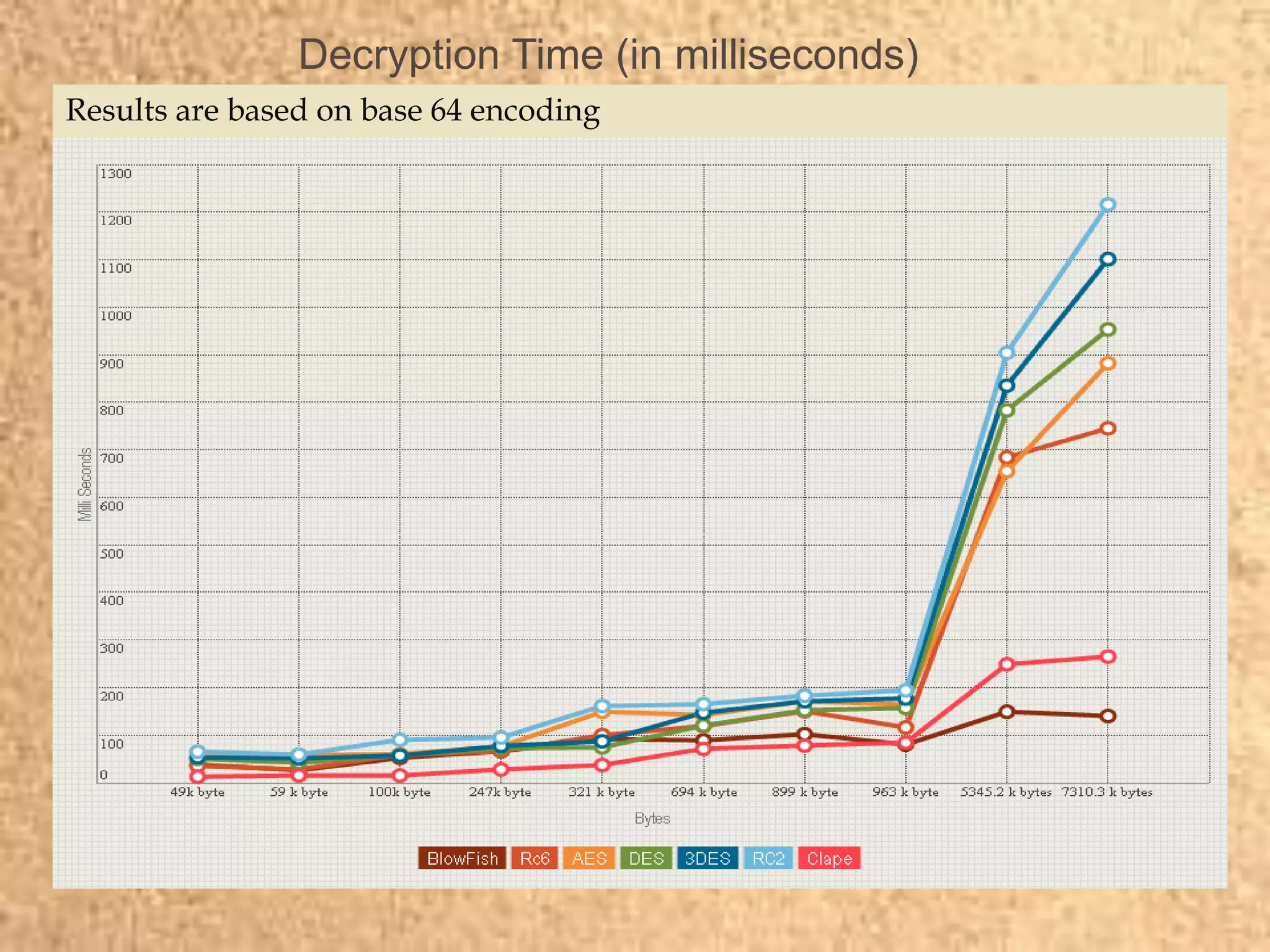
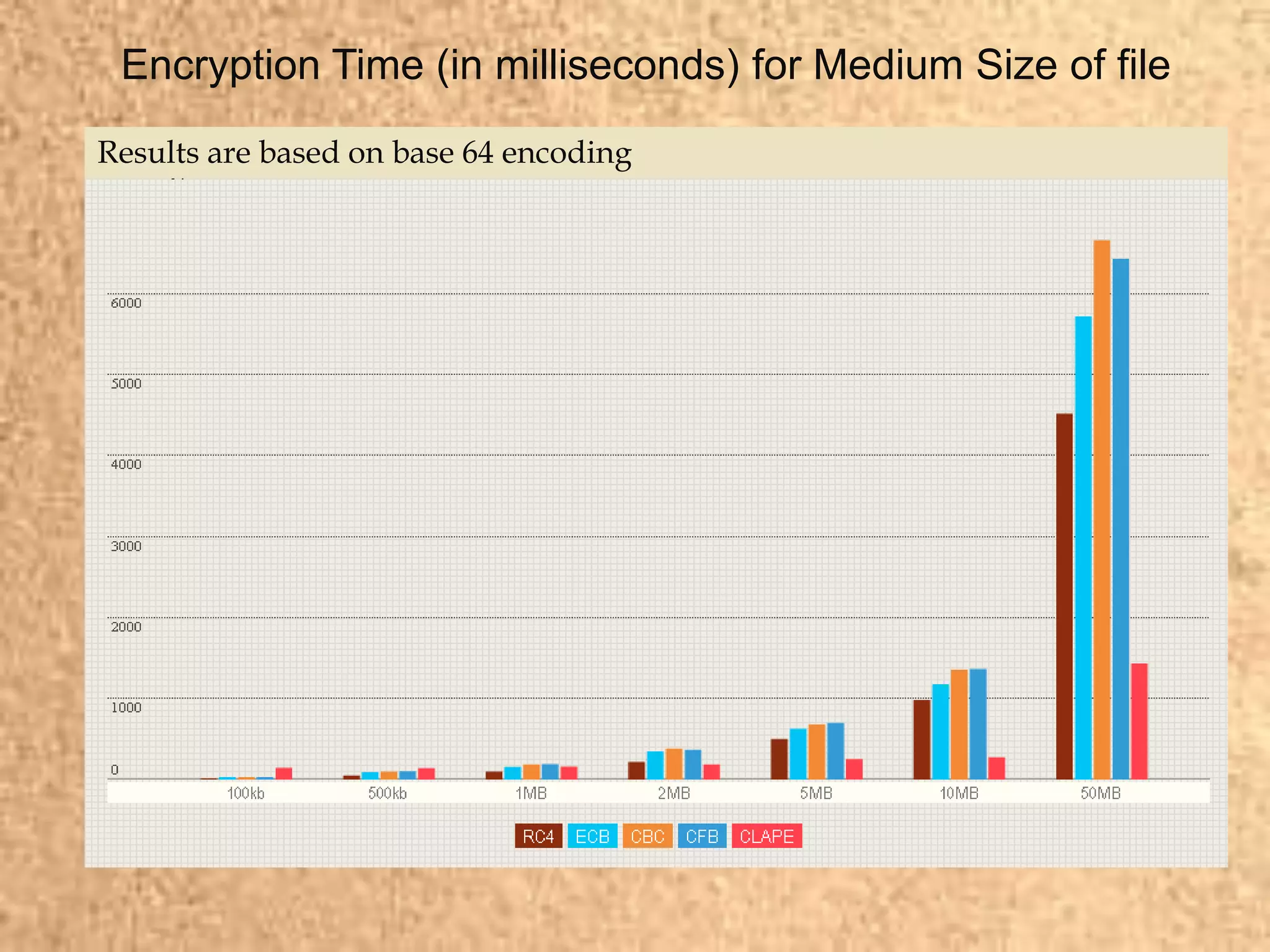
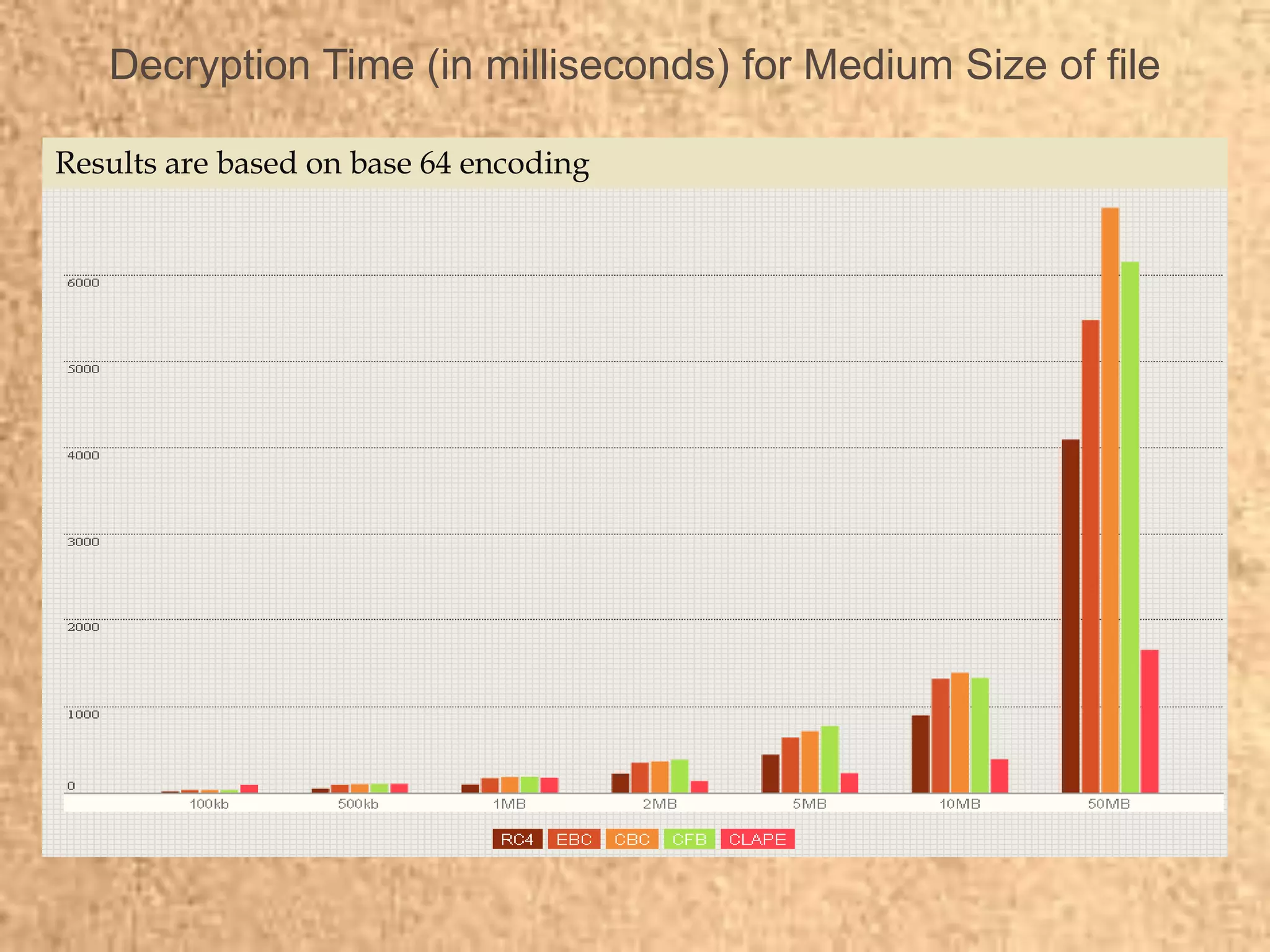
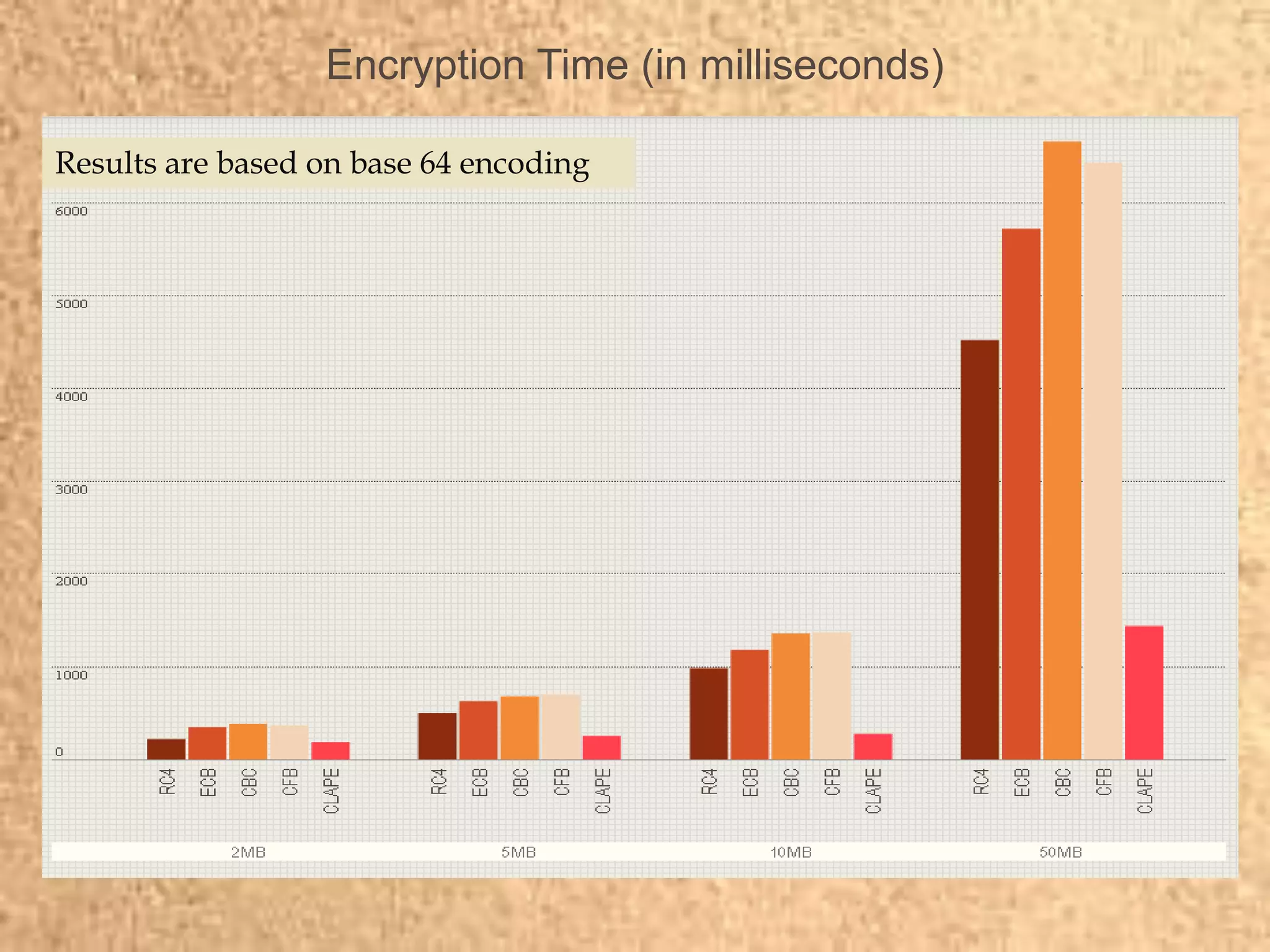
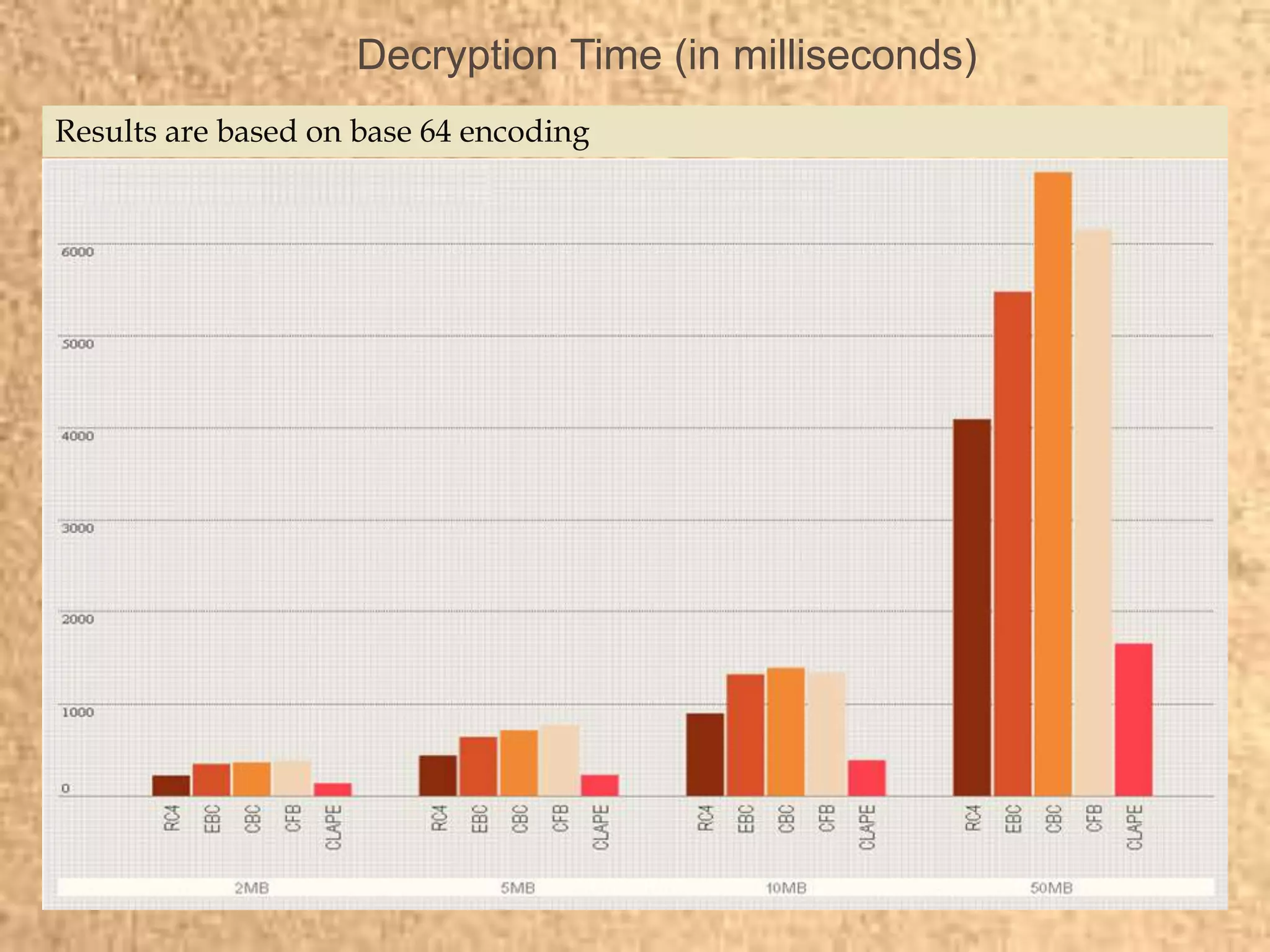
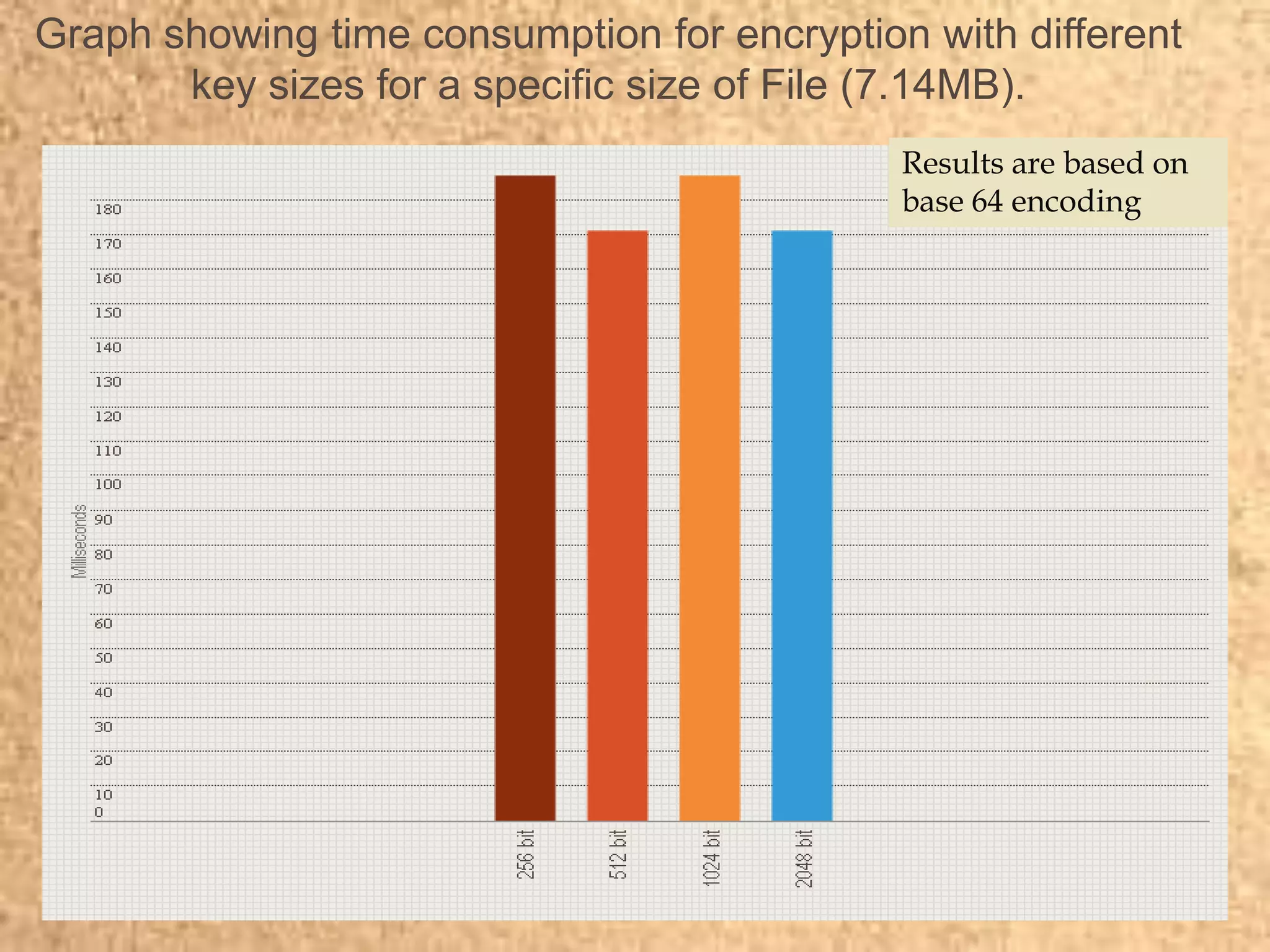
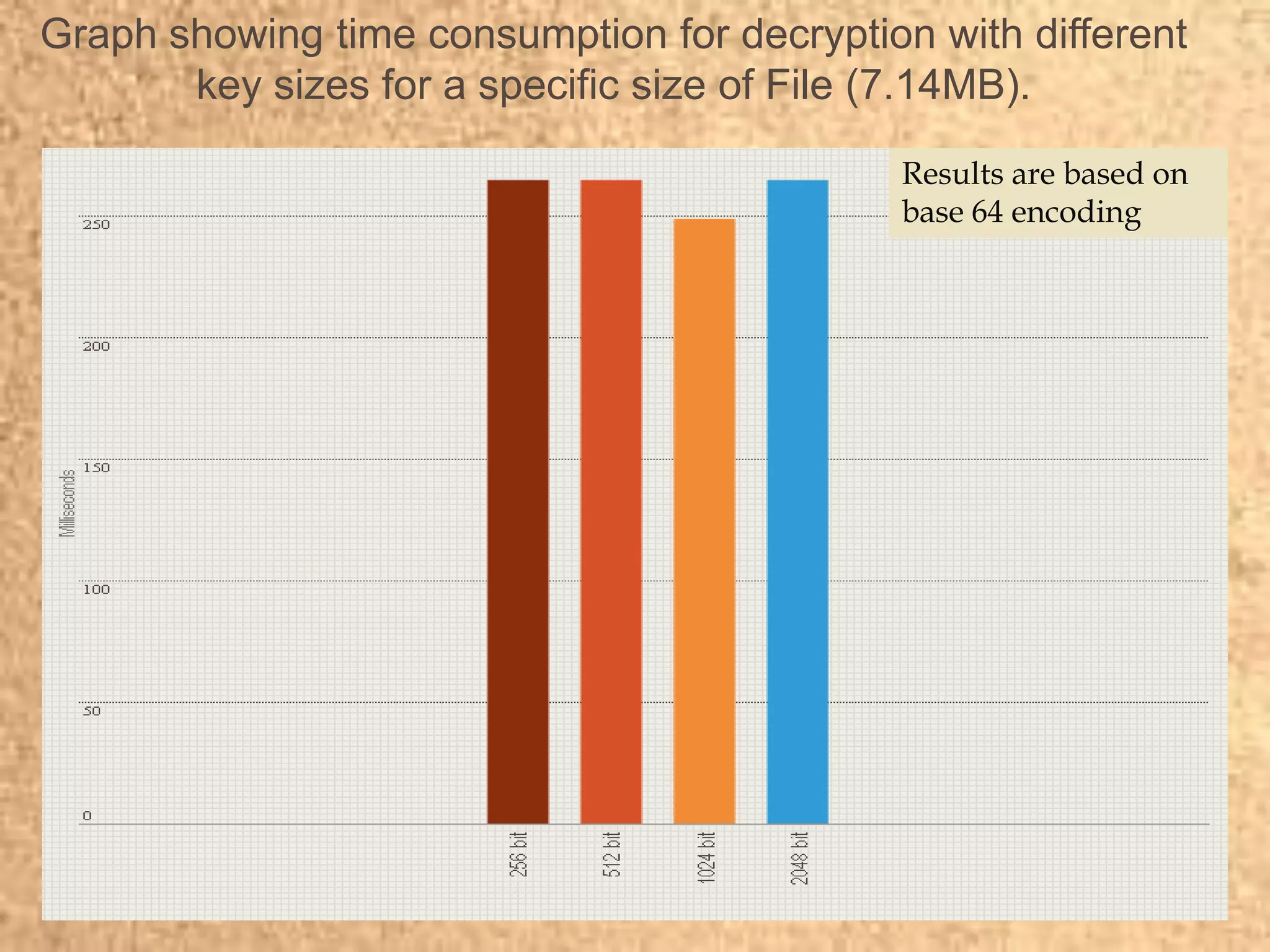
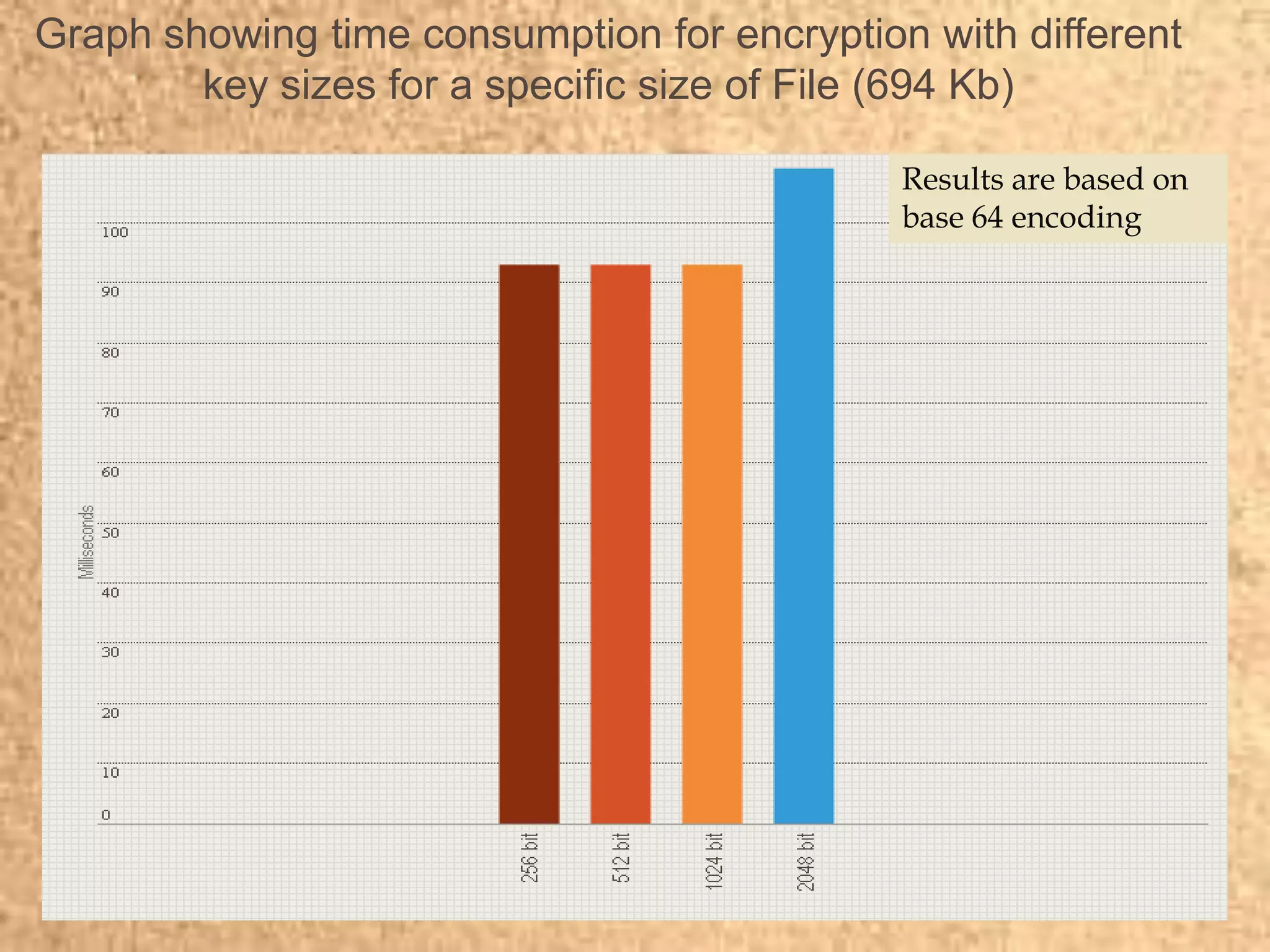
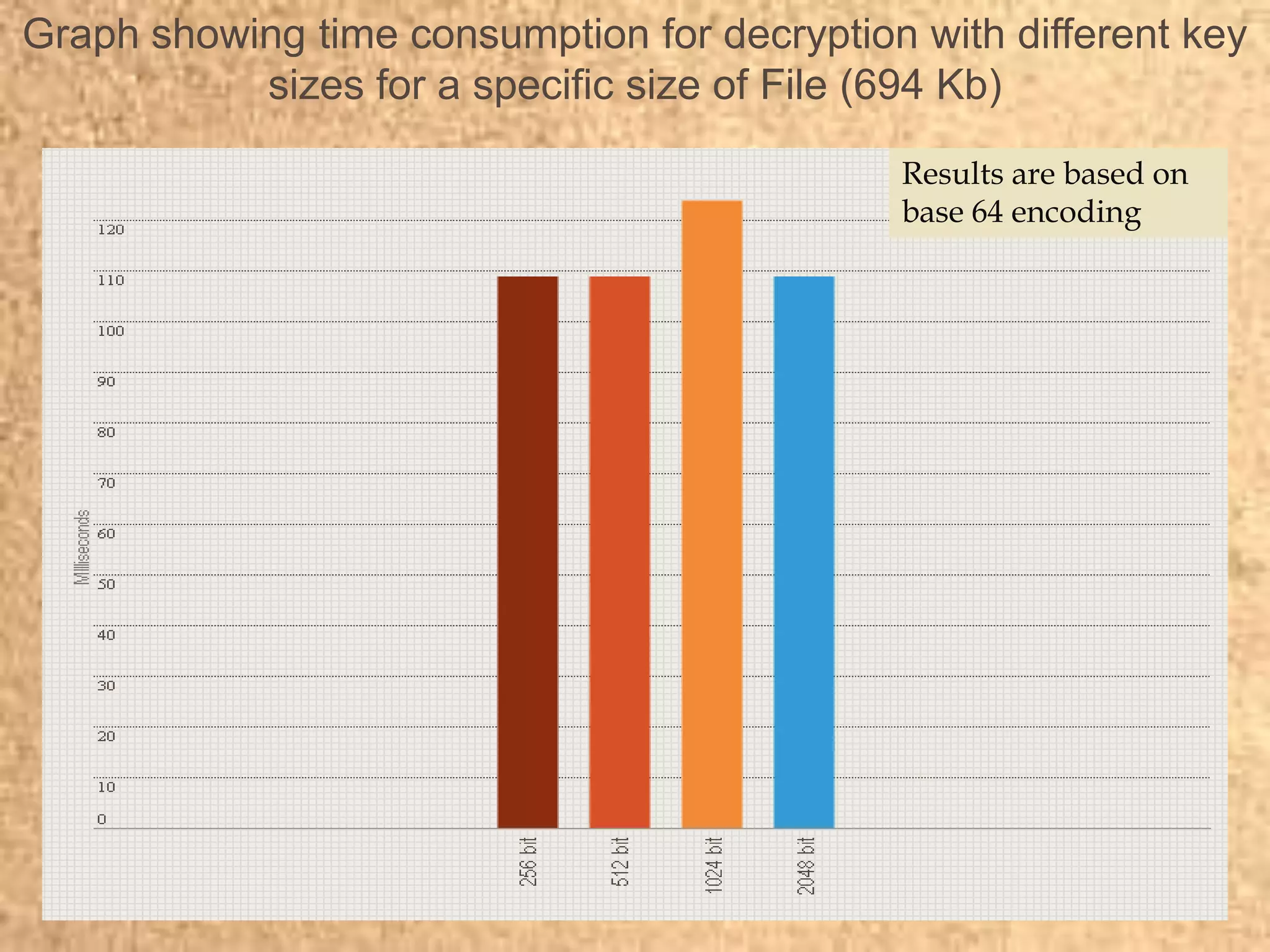
Clape Technologies has developed a symmetric key encryption standard and filed a patent application for it. The encryption method encrypts data multiple times using a password or key, sending the multiple ciphertexts and password. Performance tests show the Clape encryption is faster than AES, DES, 3DES, and other algorithms for various file and key sizes, using only 20% battery power for 600 encryptions of a 5MB file. Clape is seeking validation of its claims through testing and hopes the standard will eventually become widely adopted.