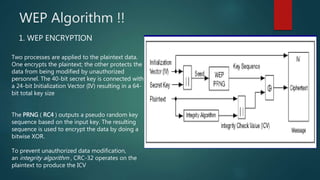
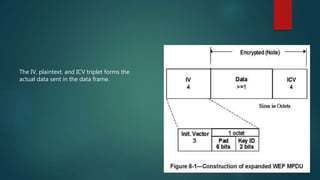
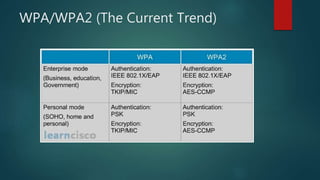
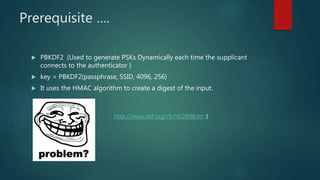
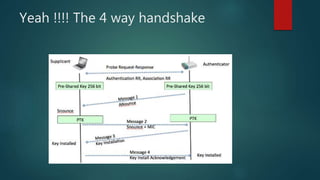
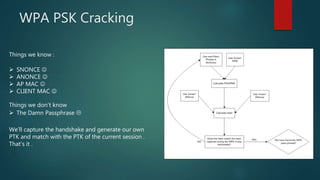
The document is a comprehensive guide on wireless networking, detailing the fundamentals of Wireless LAN (WLAN), its security protocols like WEP and WPA, and common vulnerabilities. It covers topics such as wireless sniffing, authentication processes, and various attack methods including WPS attacks and advanced techniques like PixieWPS. The author also provides essential security tips to safeguard wireless networks and acknowledges various resources for further learning.