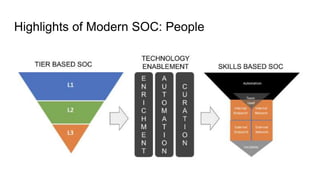
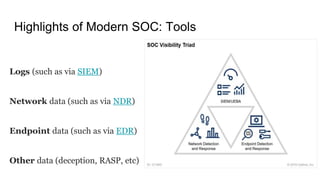
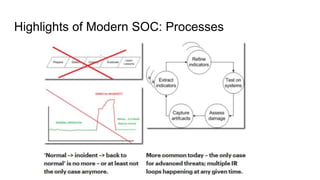
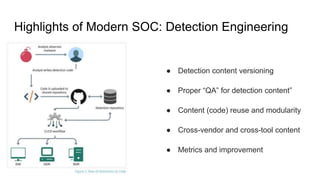
Modern SOCs face expanding attack surfaces, security talent shortages, and too many alerts from numerous tools. A modern SOC organizes teams by skills rather than levels, structures processes around threats instead of alerts, performs threat hunting, uses multiple visibility tools including logs and network data, and automates tasks through SOAR. It consumes and creates threat intelligence, elegantly uses third-party services, and does not treat incidents as rare or center itself around a single tool like a SIEM. A modern SOC recommends handling alerts but recognizing that is not the entire role, making analysts and engineers collaborate, hiring skills over levels, automating routines, and keeping fuzzy tasks for humans while using third parties for some tasks.






![Highlights of Modern SOC: “Help”
“Every modern SOC is a hybrid SOC” -- Anton Chuvakin [source]
THIS OUTSOURCES WELL
- Deeper malware analysis
- Threat intelligence
- SIEM, EDR and other tool
management and tuning
- SOC tool tuning and use case
analysis
- Managed threat hunting
THIS OUTSOURCES BADLY
- Remediation of threats
- Full cycle of incident response
- Insider threat detection
- Business- and application-specific
threat detection
THIS DOES NOT OUTSOURCES AT ALL
- Accountability for security success
- Governance of security program](https://image.slidesharecdn.com/modernsoctrends-201028184734/85/Modern-SOC-Trends-2020-11-320.jpg)
