Embed presentation
Downloaded 34 times




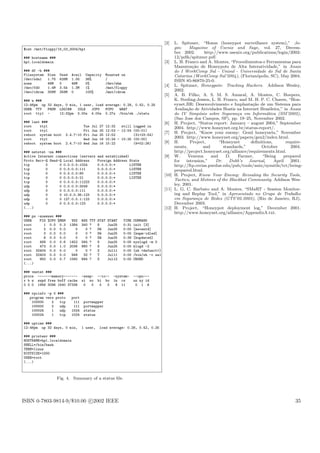

The document discusses the maintenance procedures and tools for honeypots in the Brazilian honeynet project, detailing automation scripts that facilitate the management of high-interaction honeypots. It outlines the deployment, monitoring, and deactivation processes, emphasizing the importance of documentation and standardized data collection. The paper describes procedures to minimize human error and streamline the recovery and analysis of compromised honeypots.





