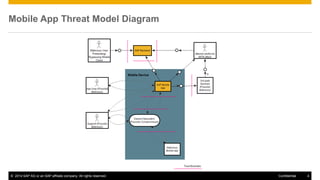
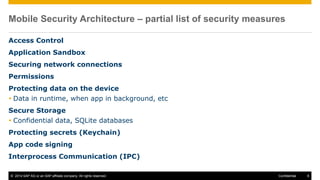
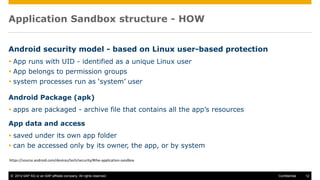
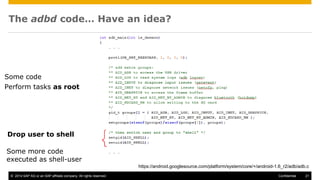
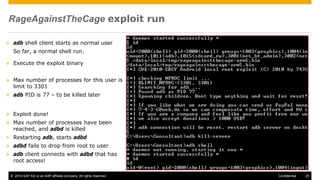
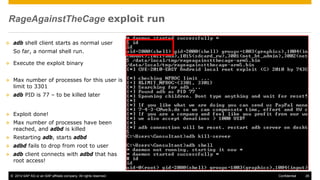
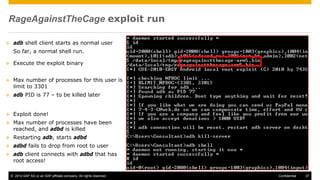
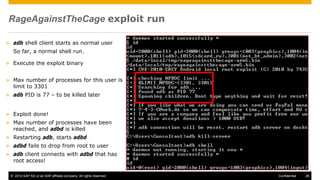
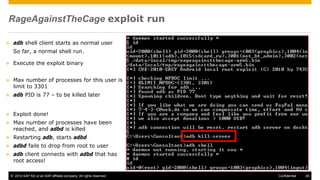
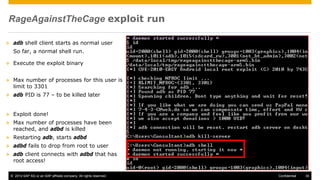
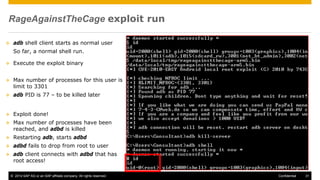
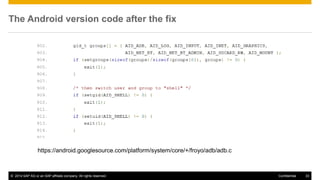
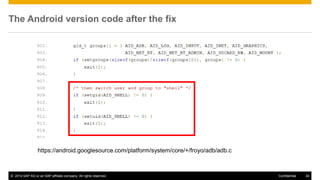
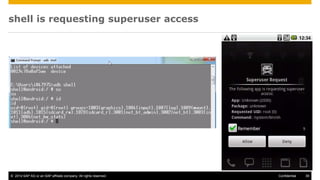
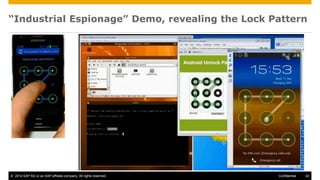
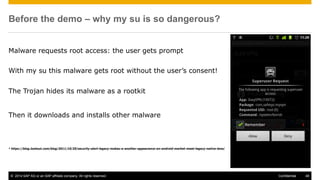
The document discusses mobile security architecture, focusing on Android security measures and the implications of rooting. It outlines vulnerabilities exploited by hackers, the methodology behind the rooting process, and examples of specific exploits such as 'rageagainstthecage'. Additionally, it highlights the potential security risks associated with granting root access on Android devices.