Embed presentation
Downloaded 24 times



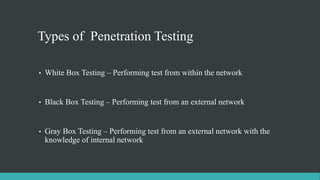




Vulnerability assessment identifies flaws in computers and networks but does not differentiate exploitable flaws from non-exploitable ones, providing companies with a comprehensive view of weaknesses. Penetration testing tests systems to exploit vulnerabilities either automatically or manually, determining security weaknesses to test an organization's security policies. Types of penetration testing include white box within a network, black box externally without network knowledge, and gray box externally with some internal knowledge.






