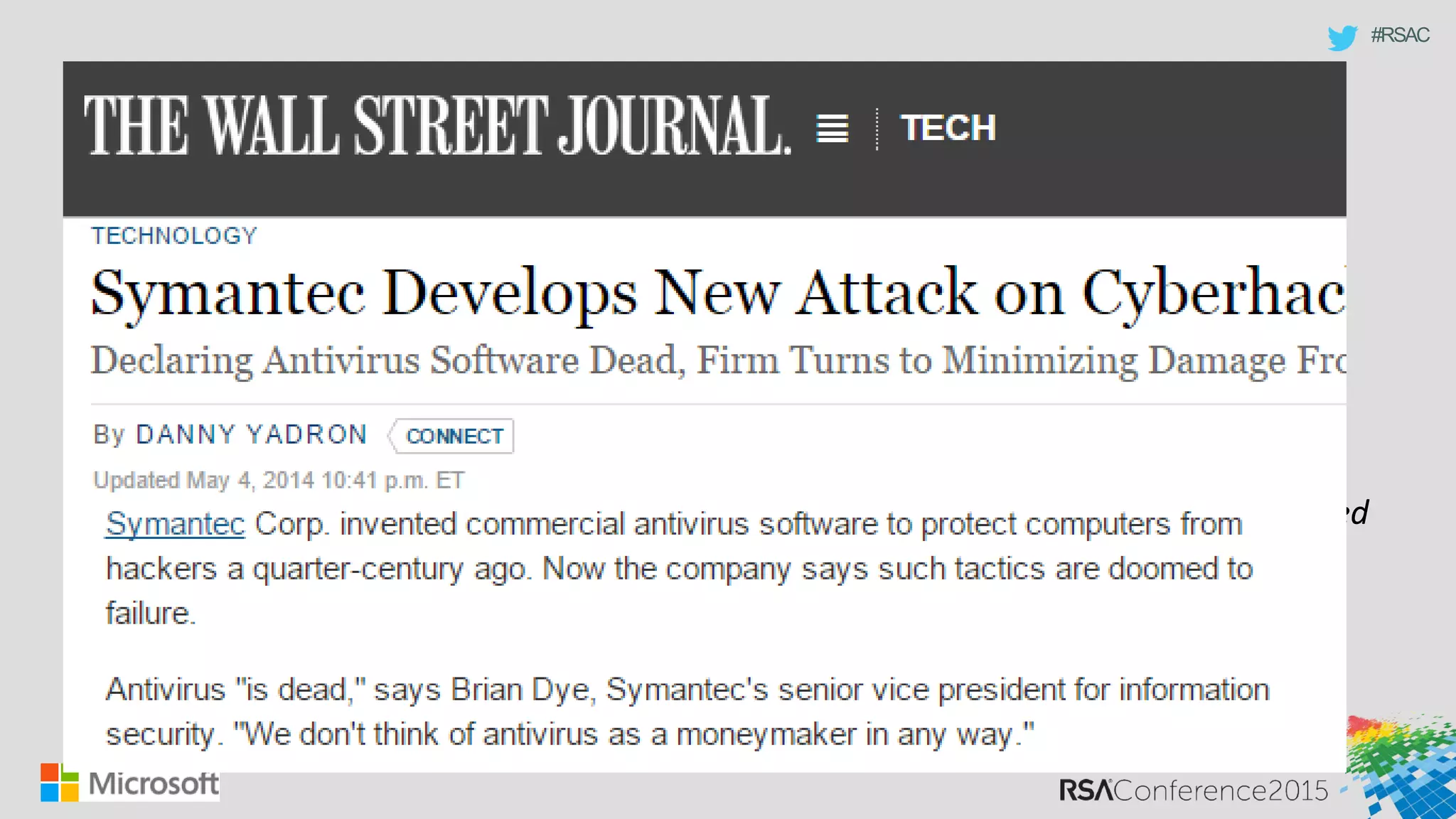
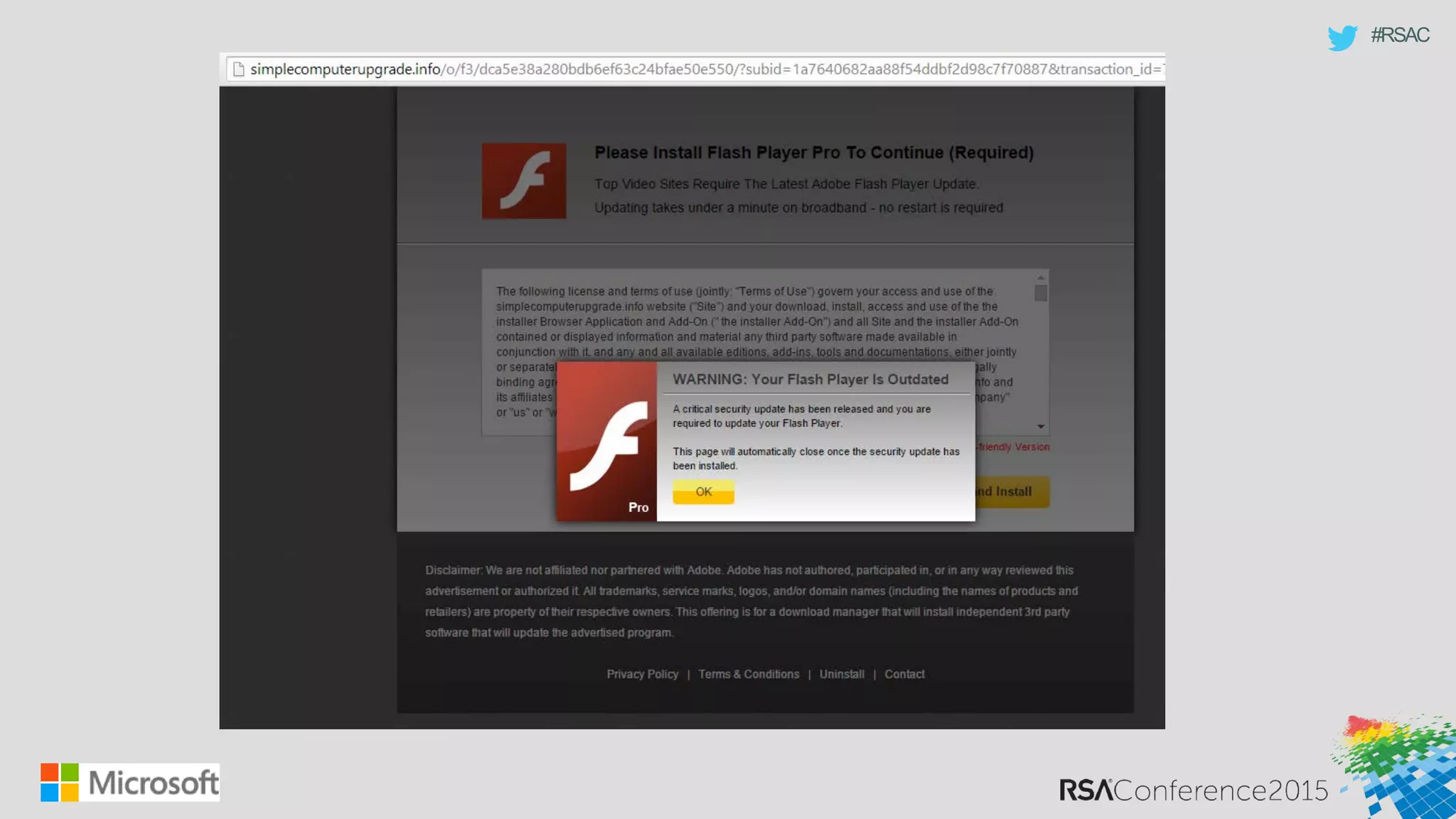
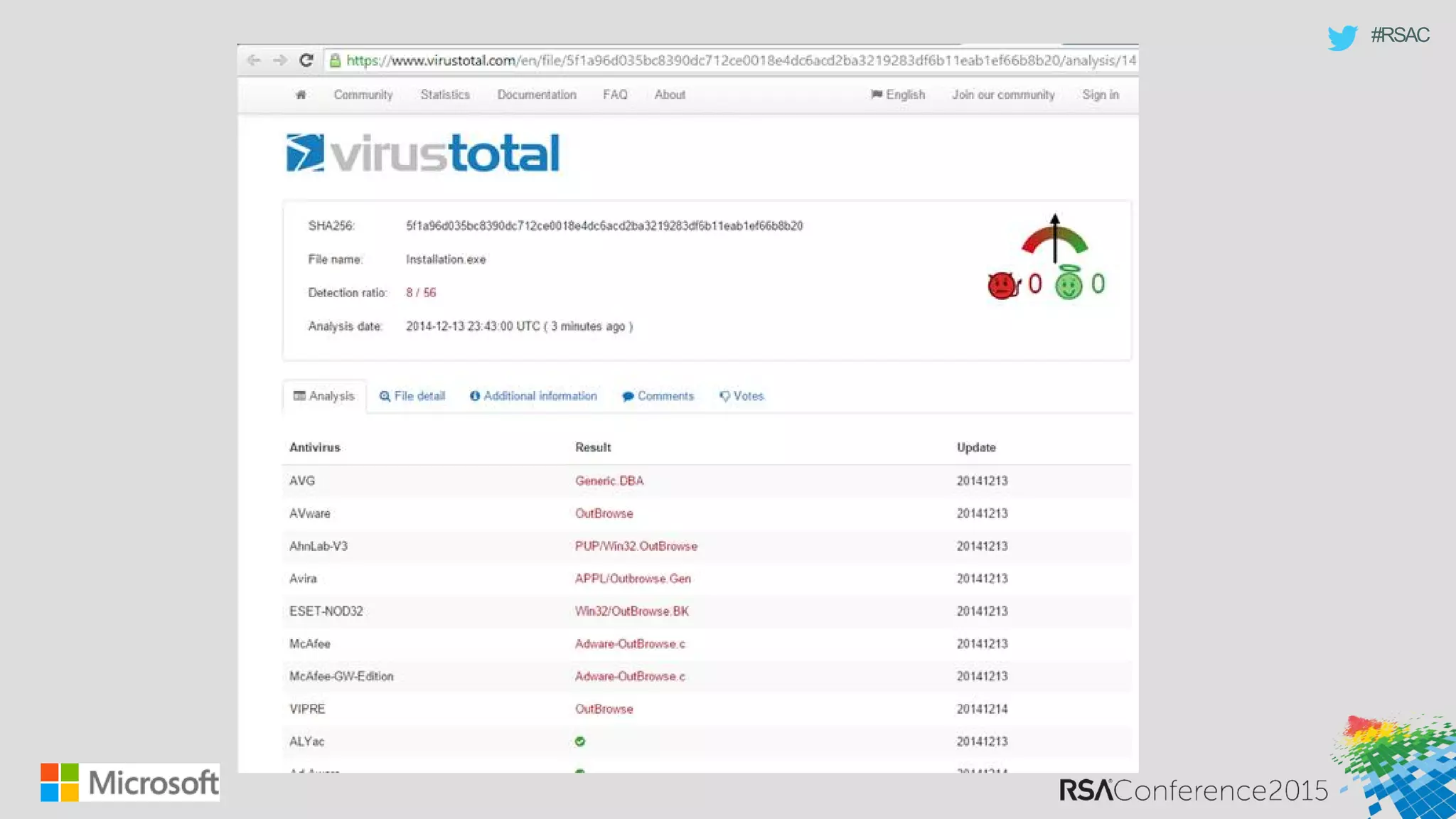
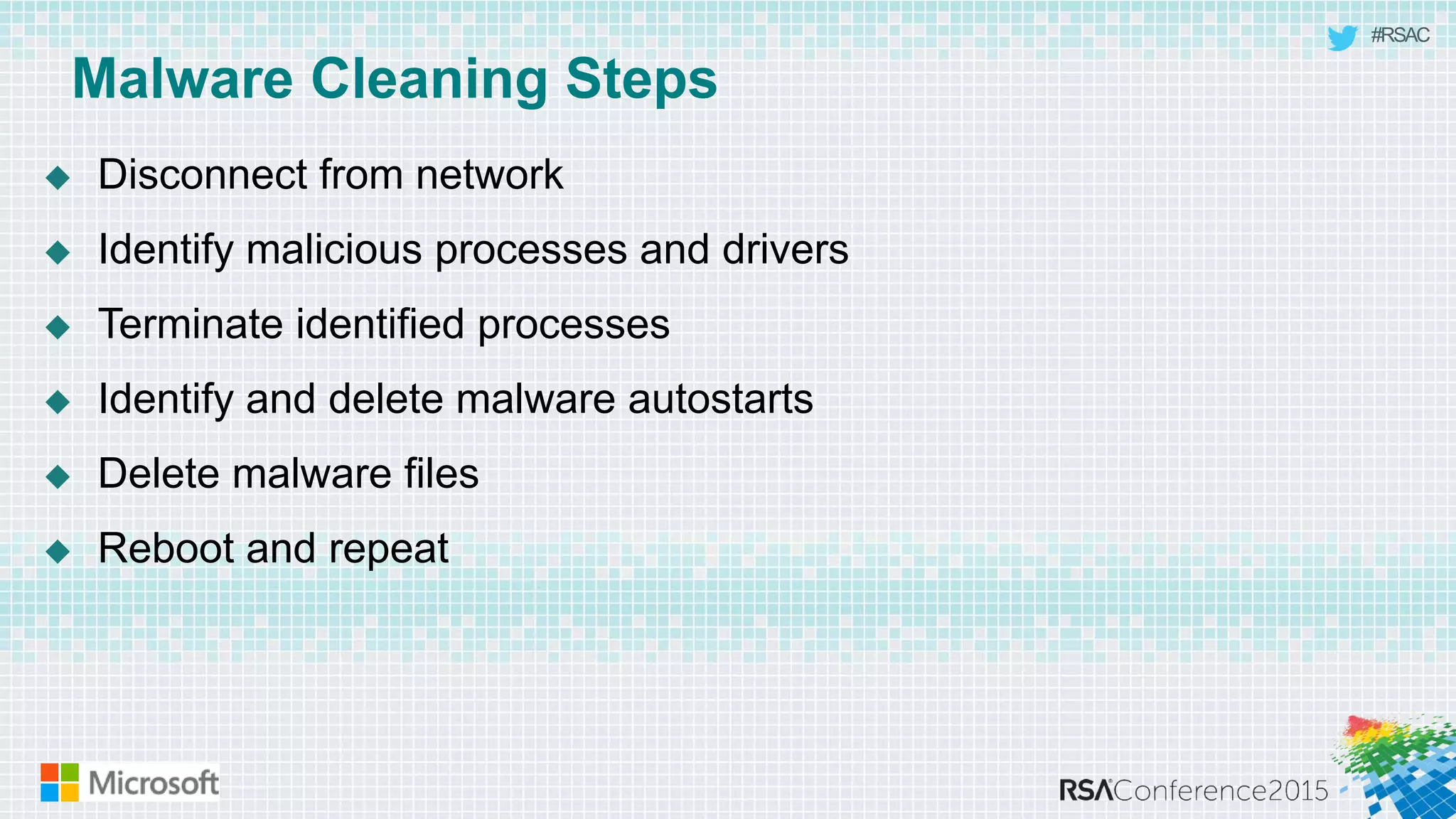
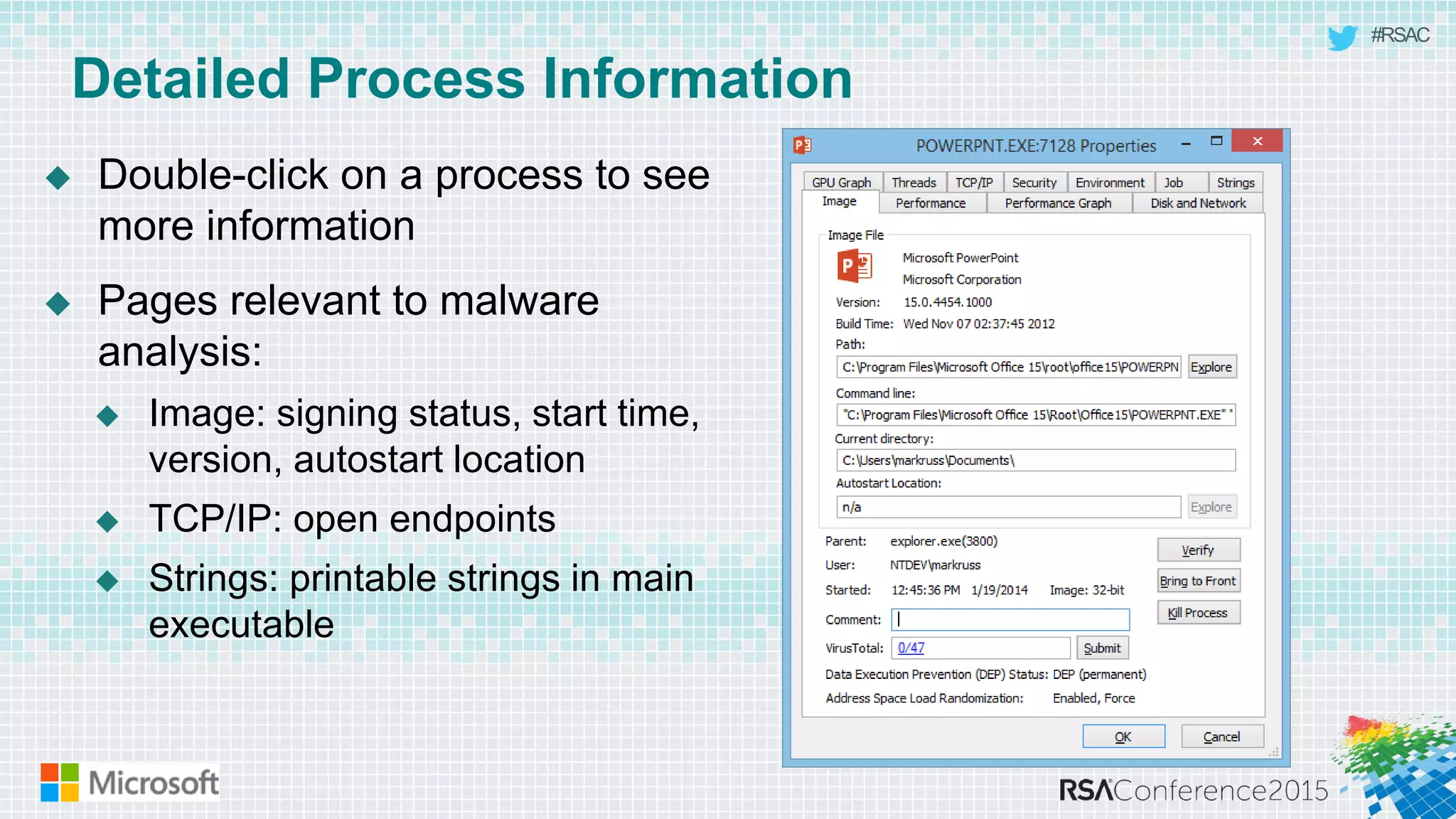
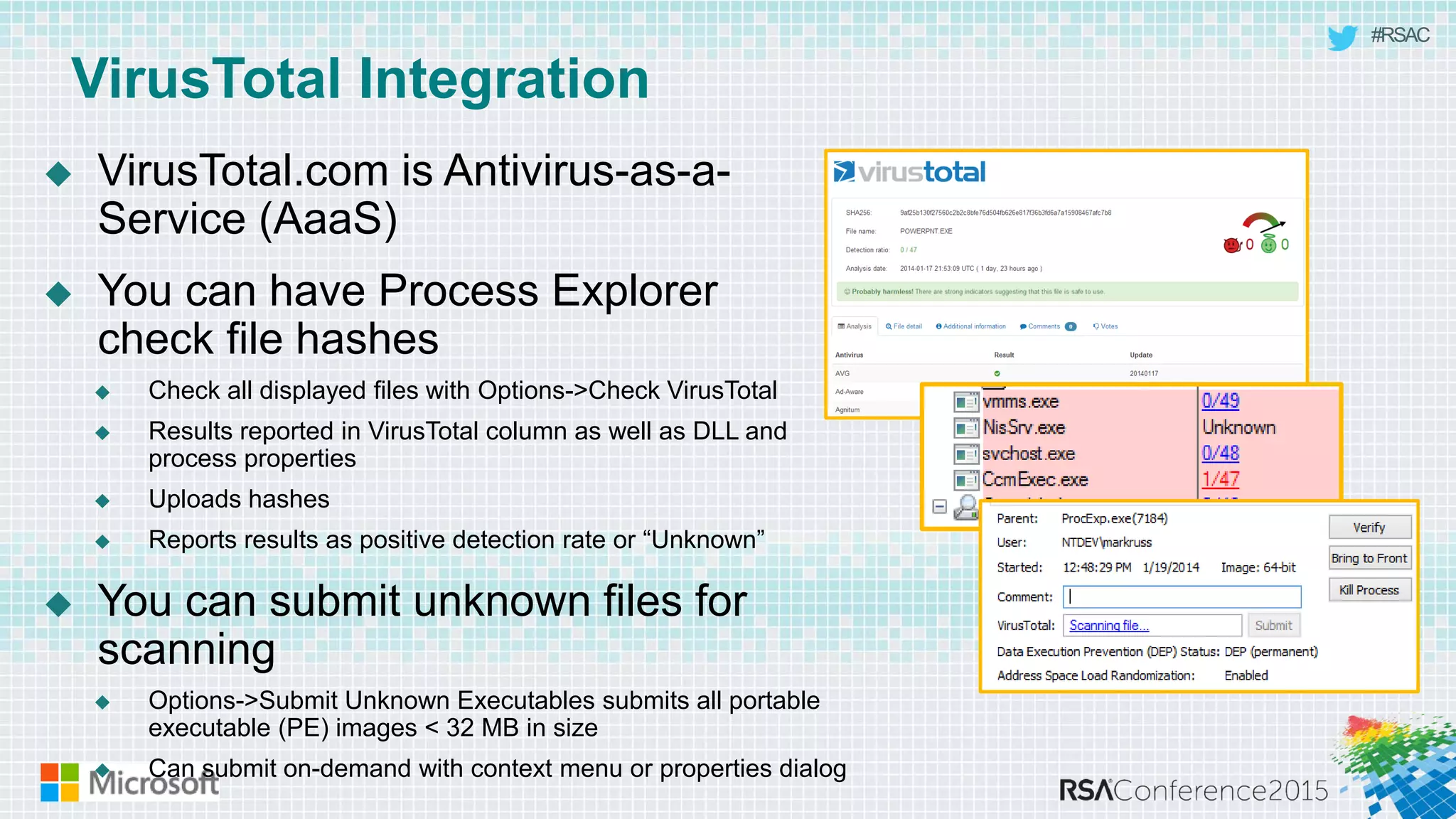
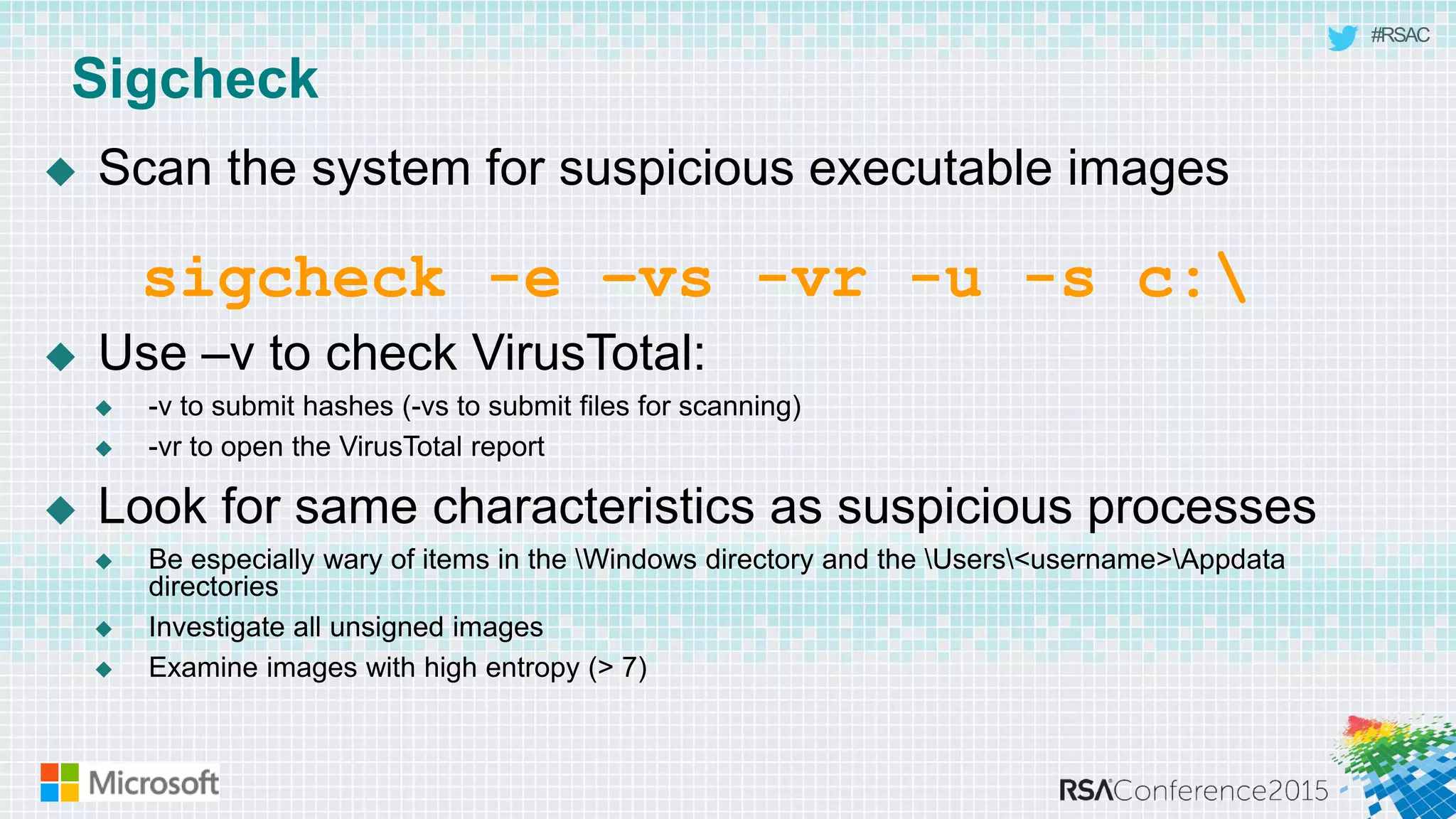
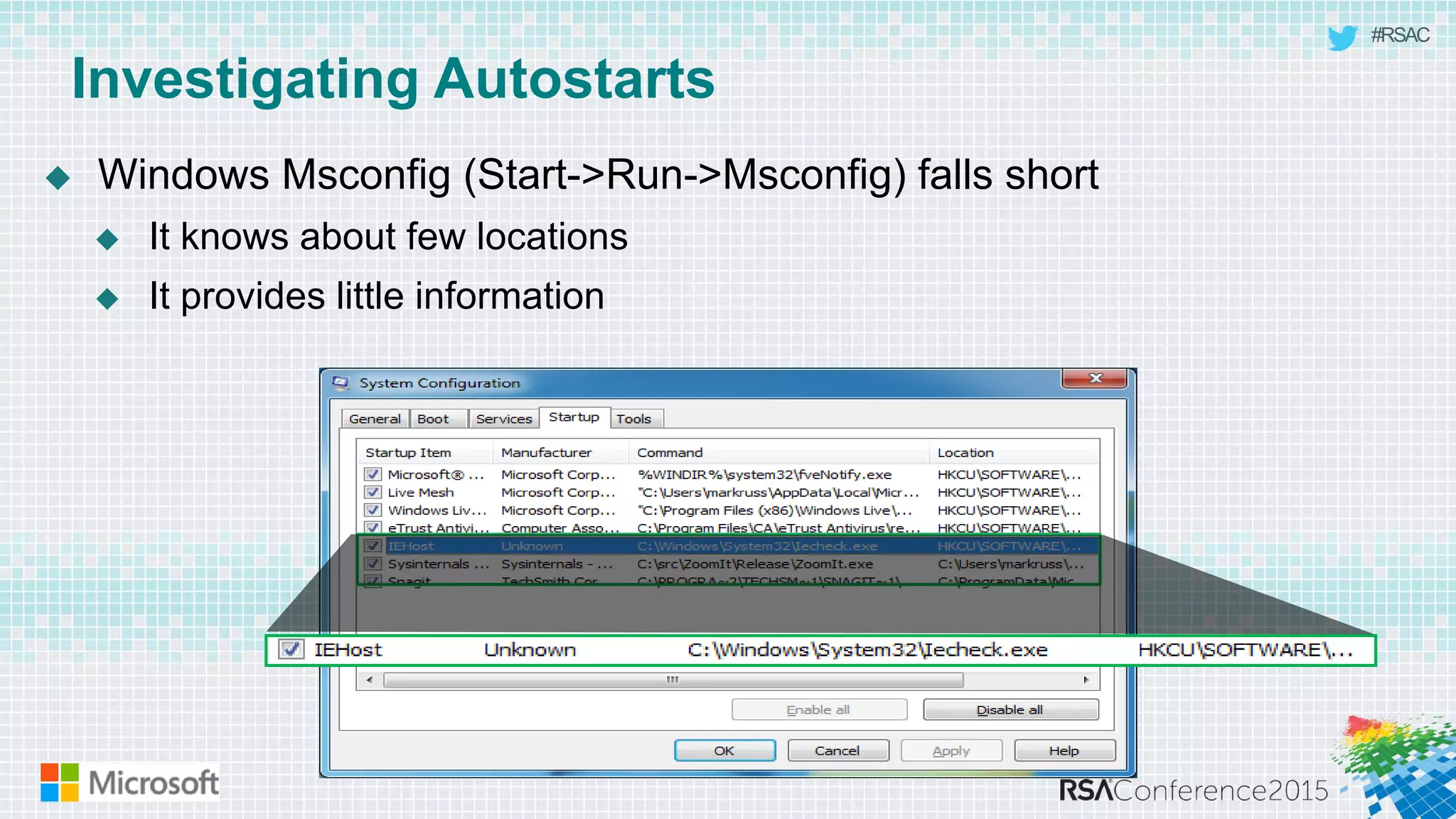
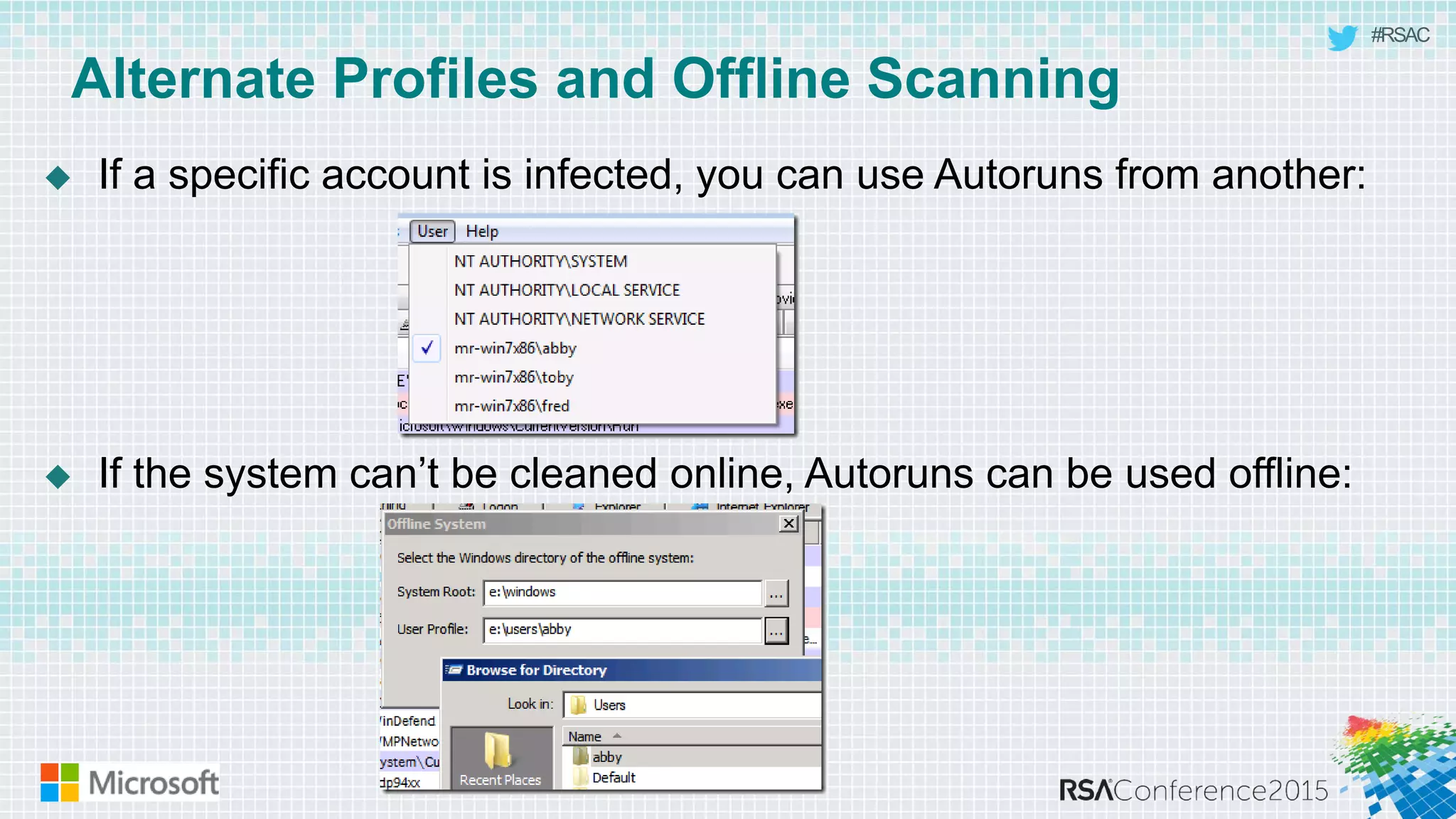
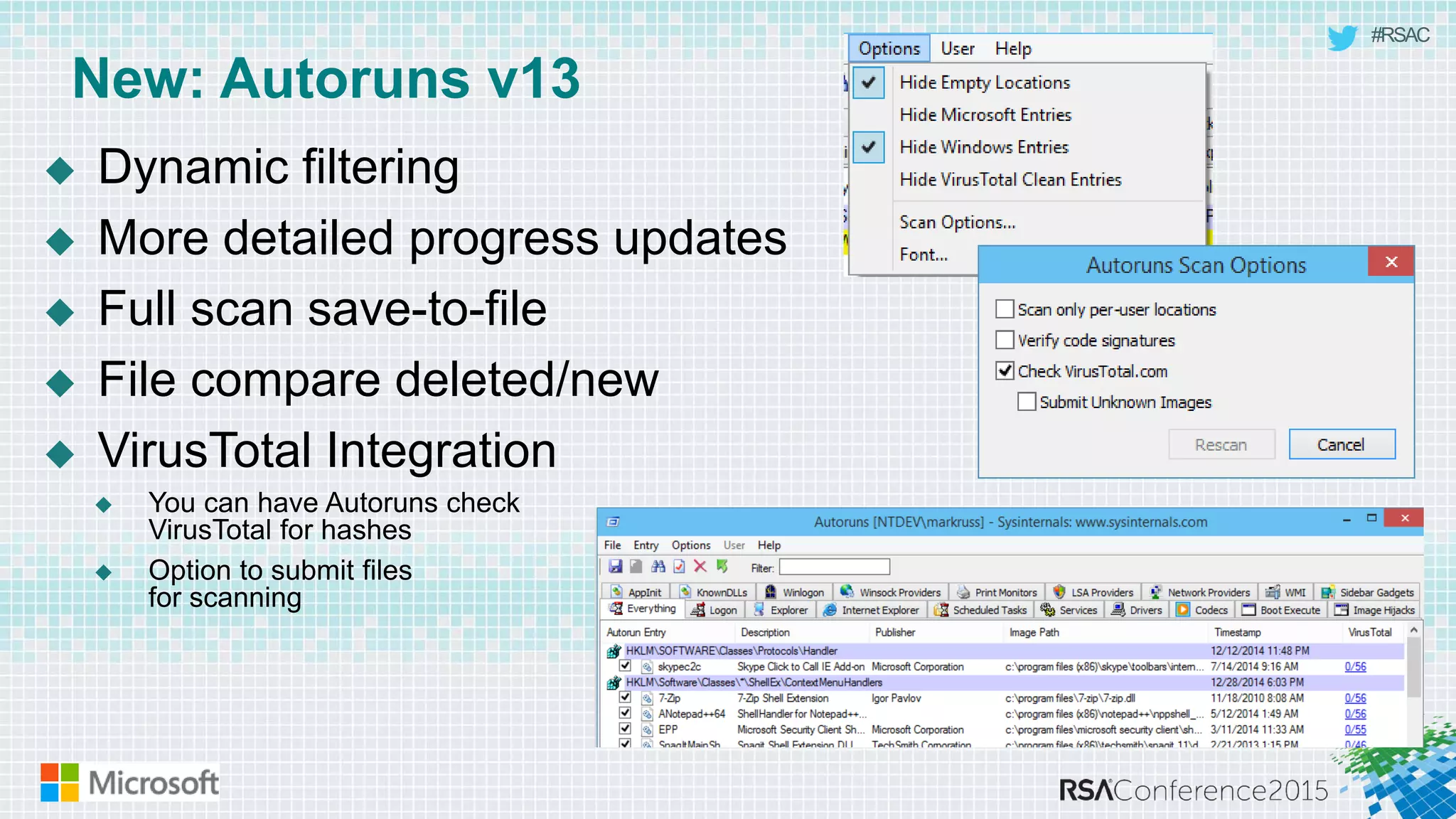
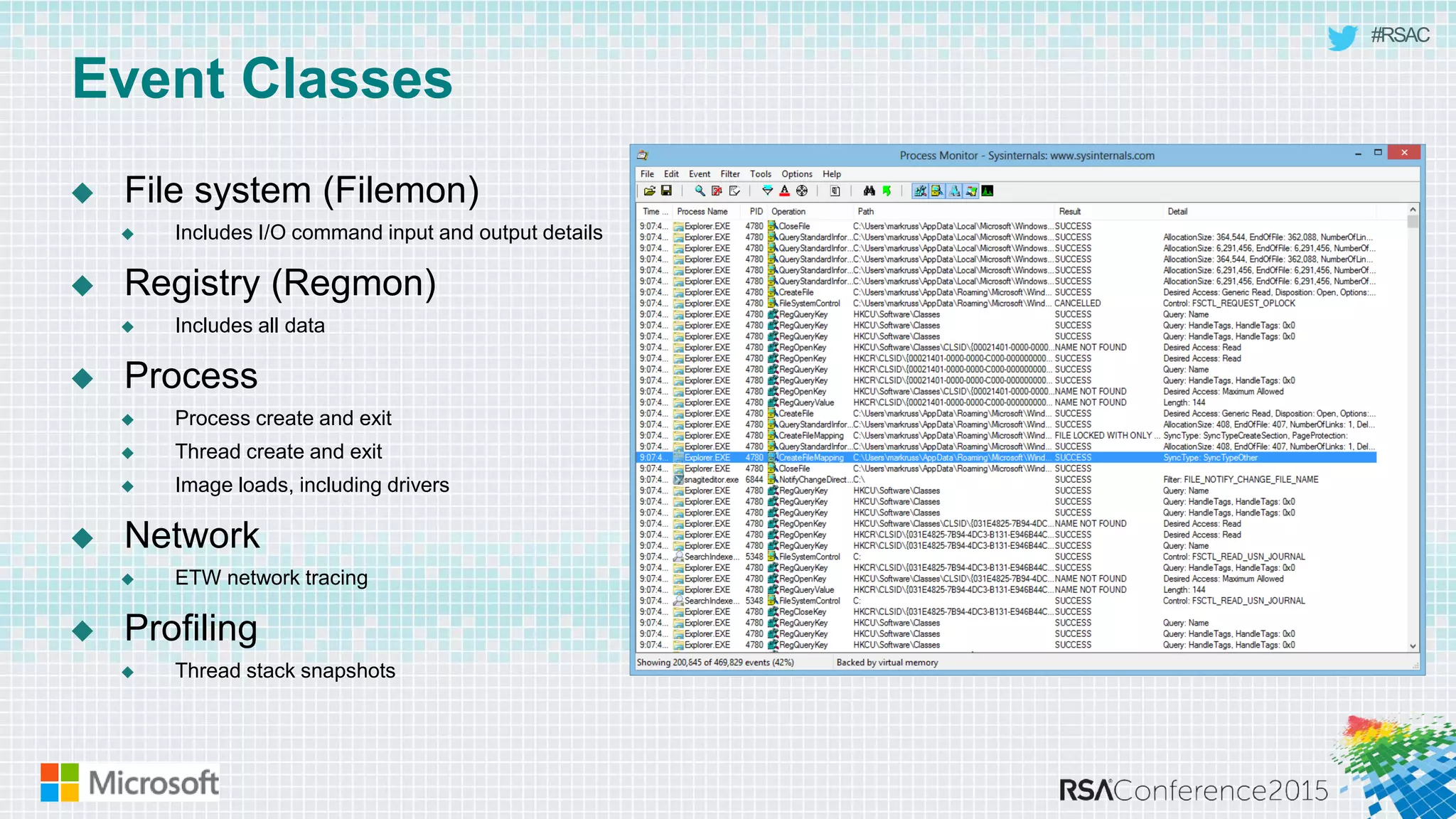
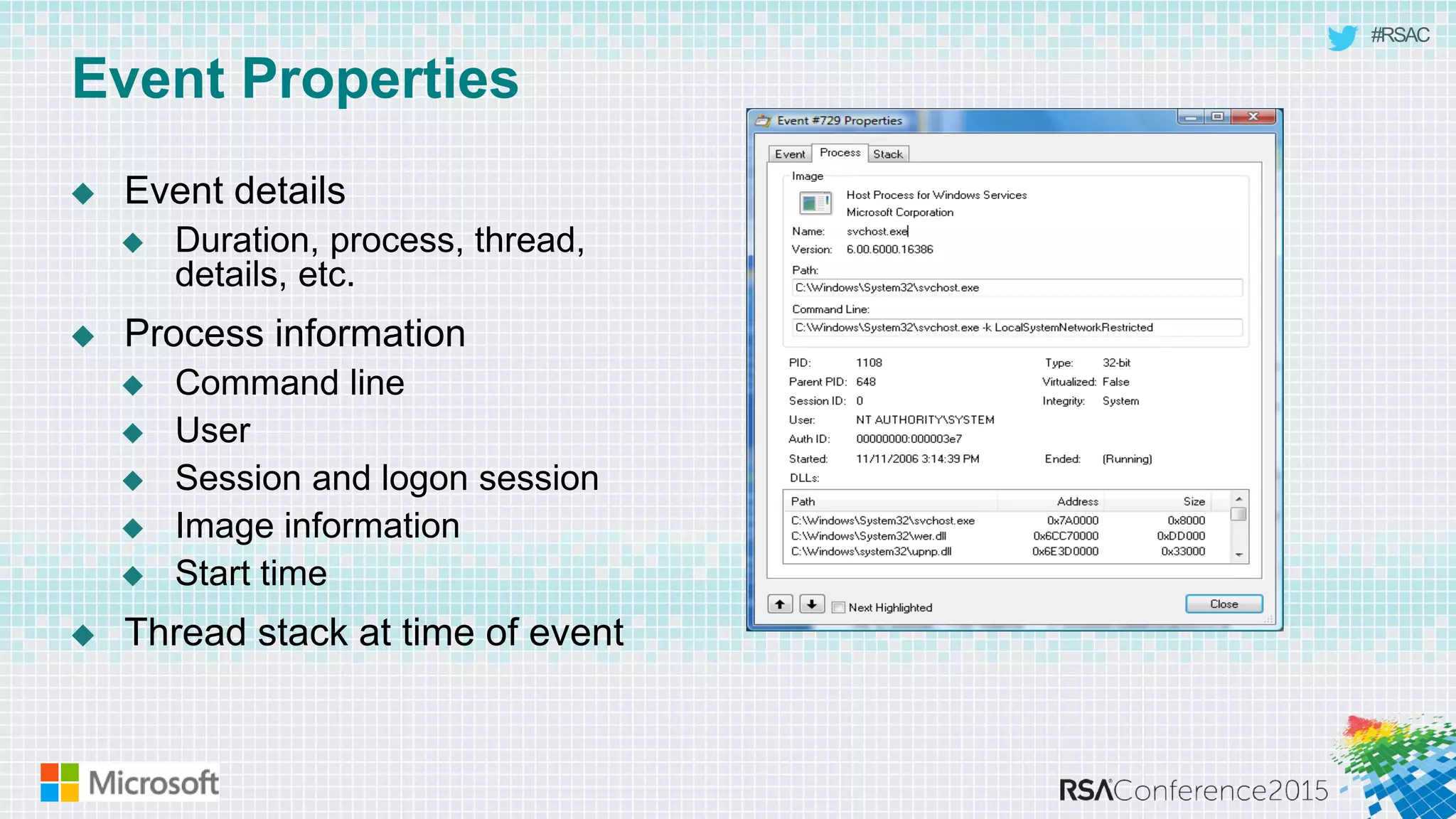
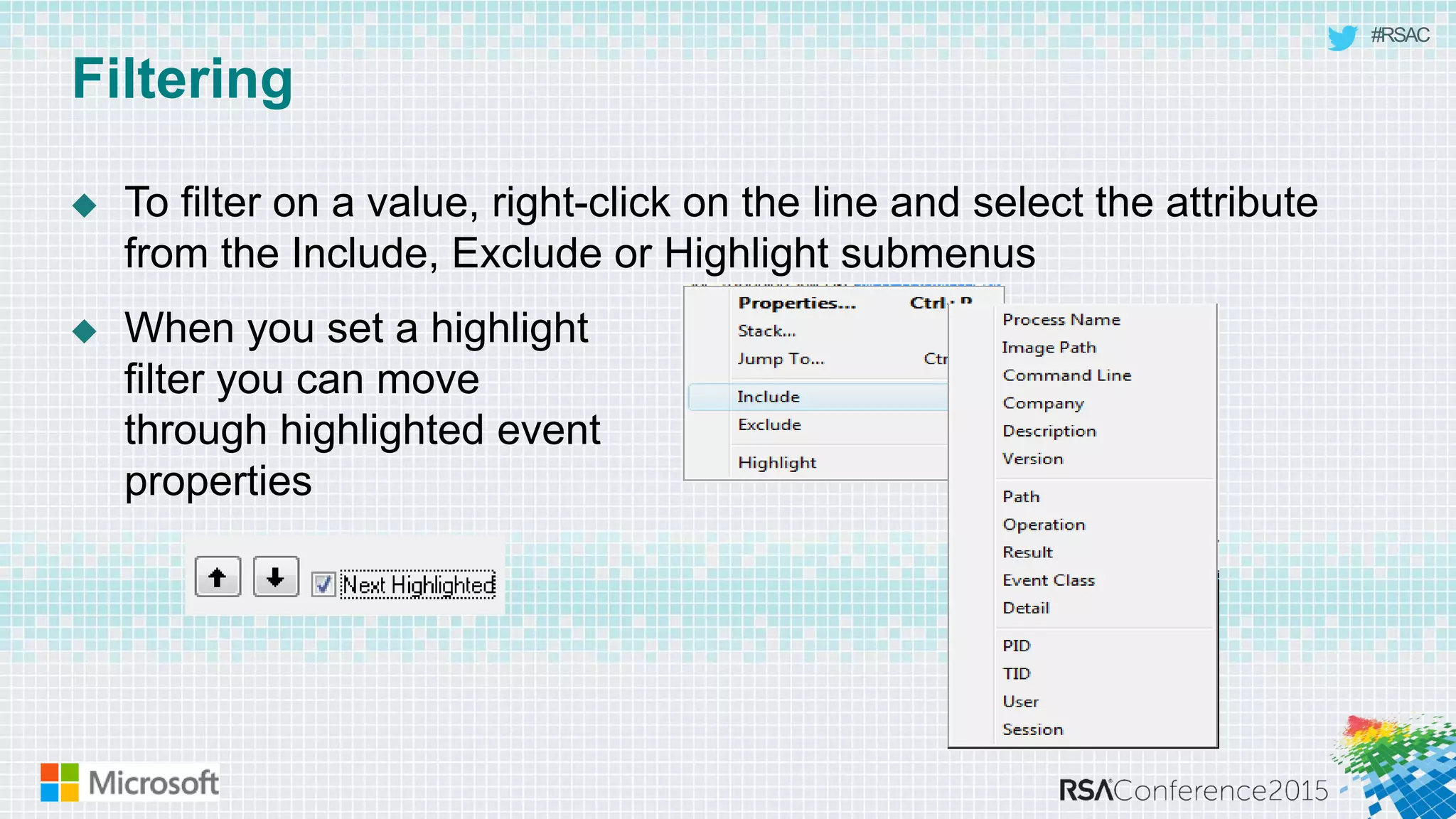
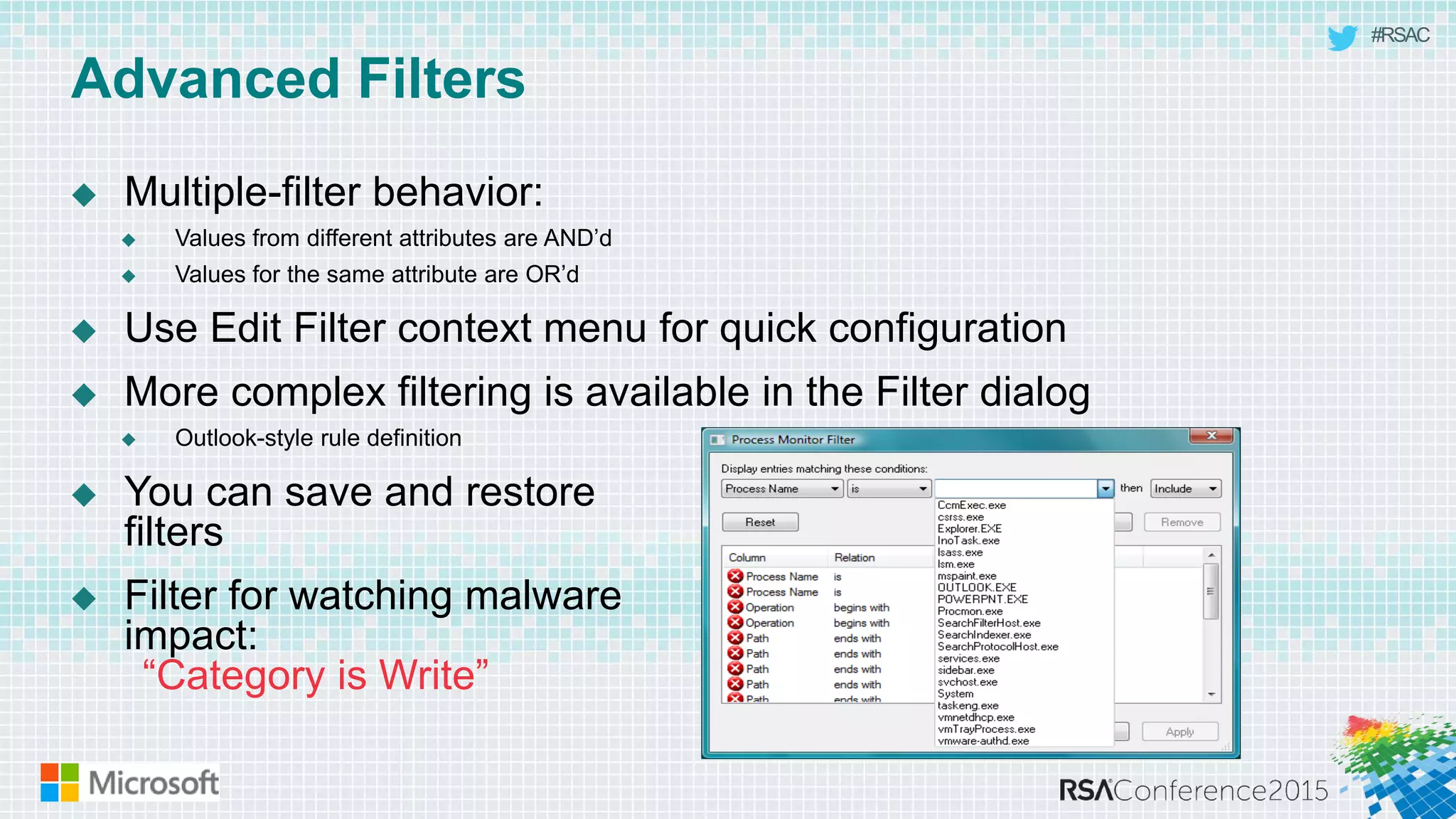
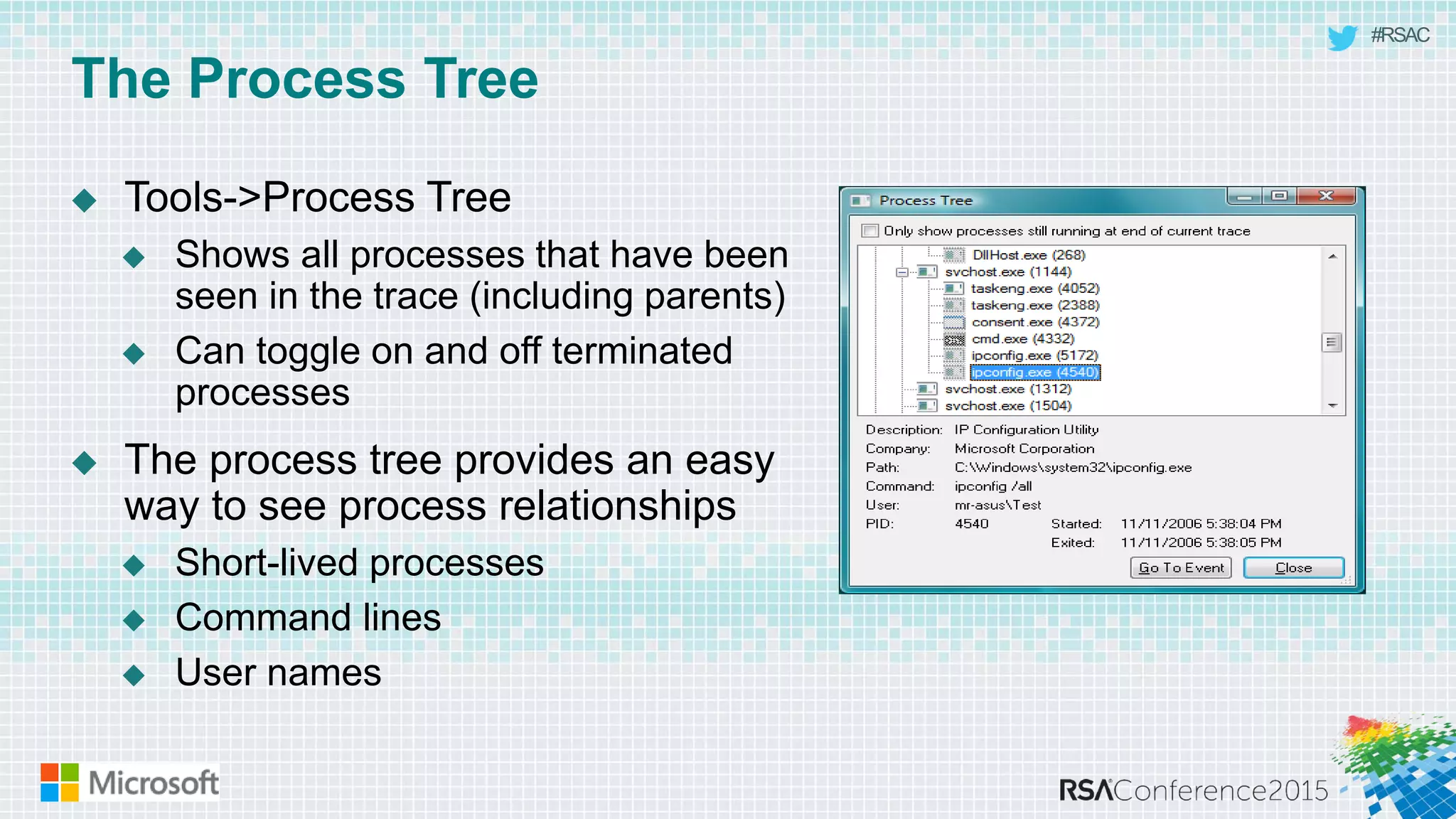
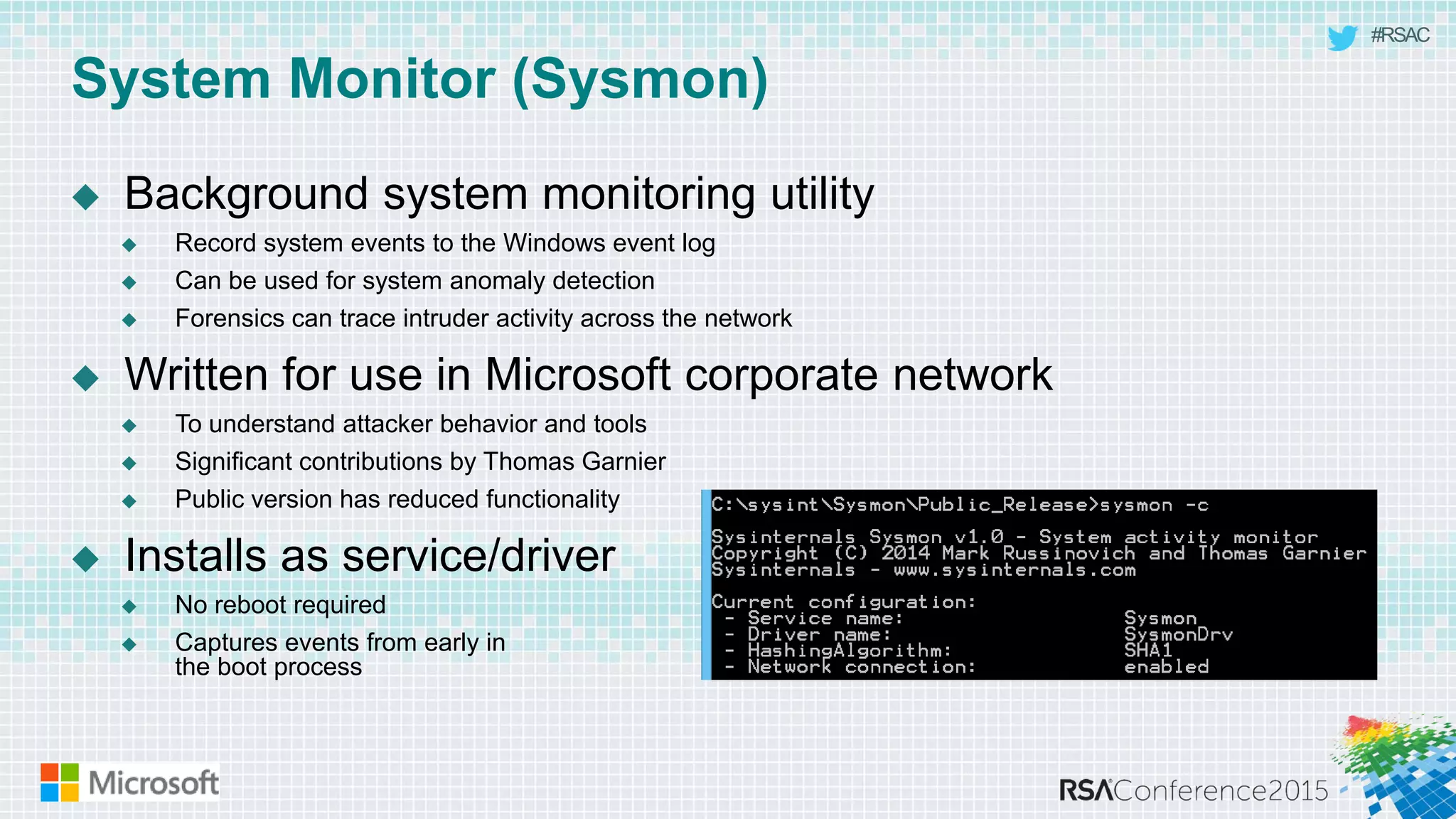
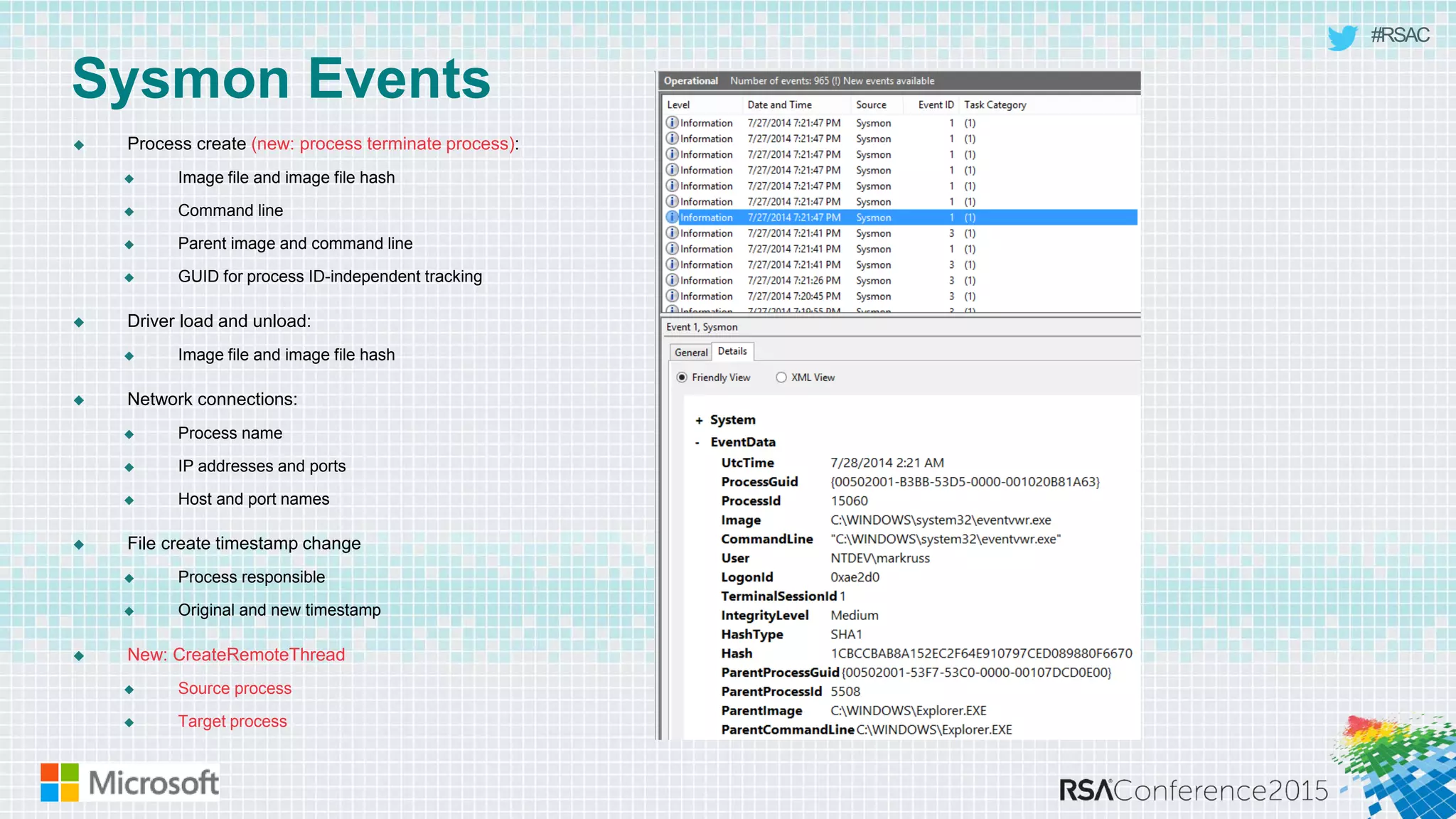
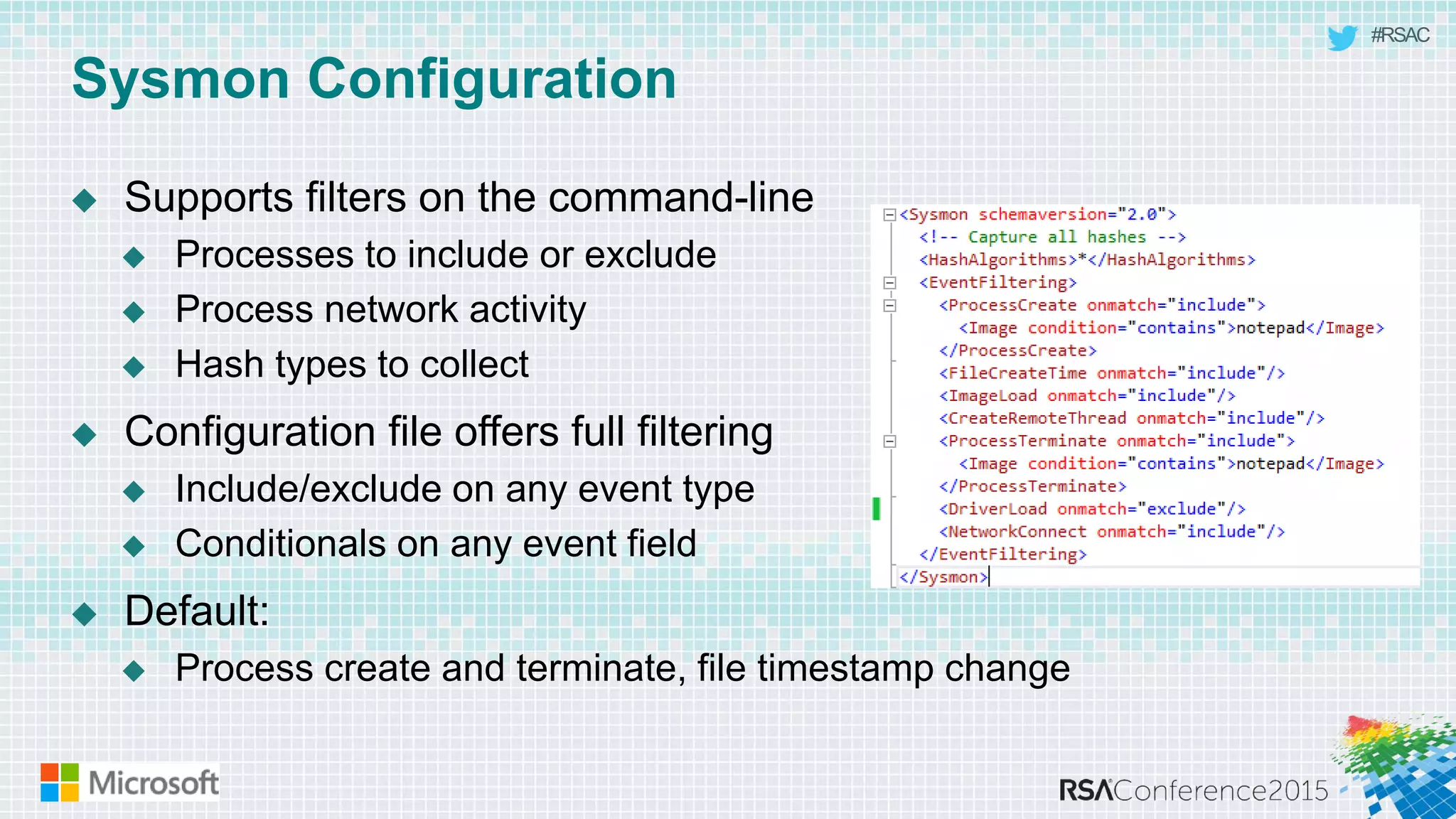
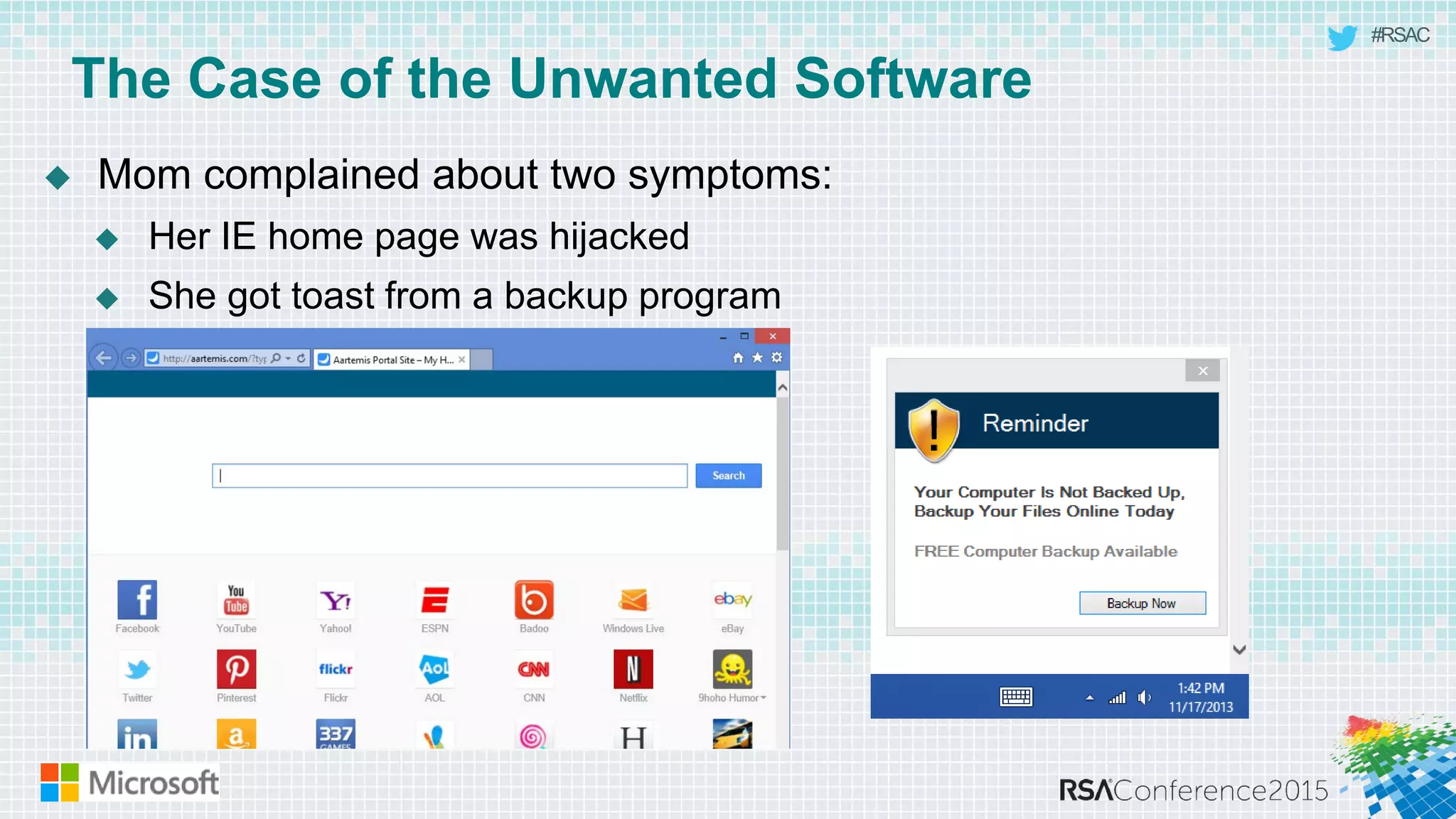
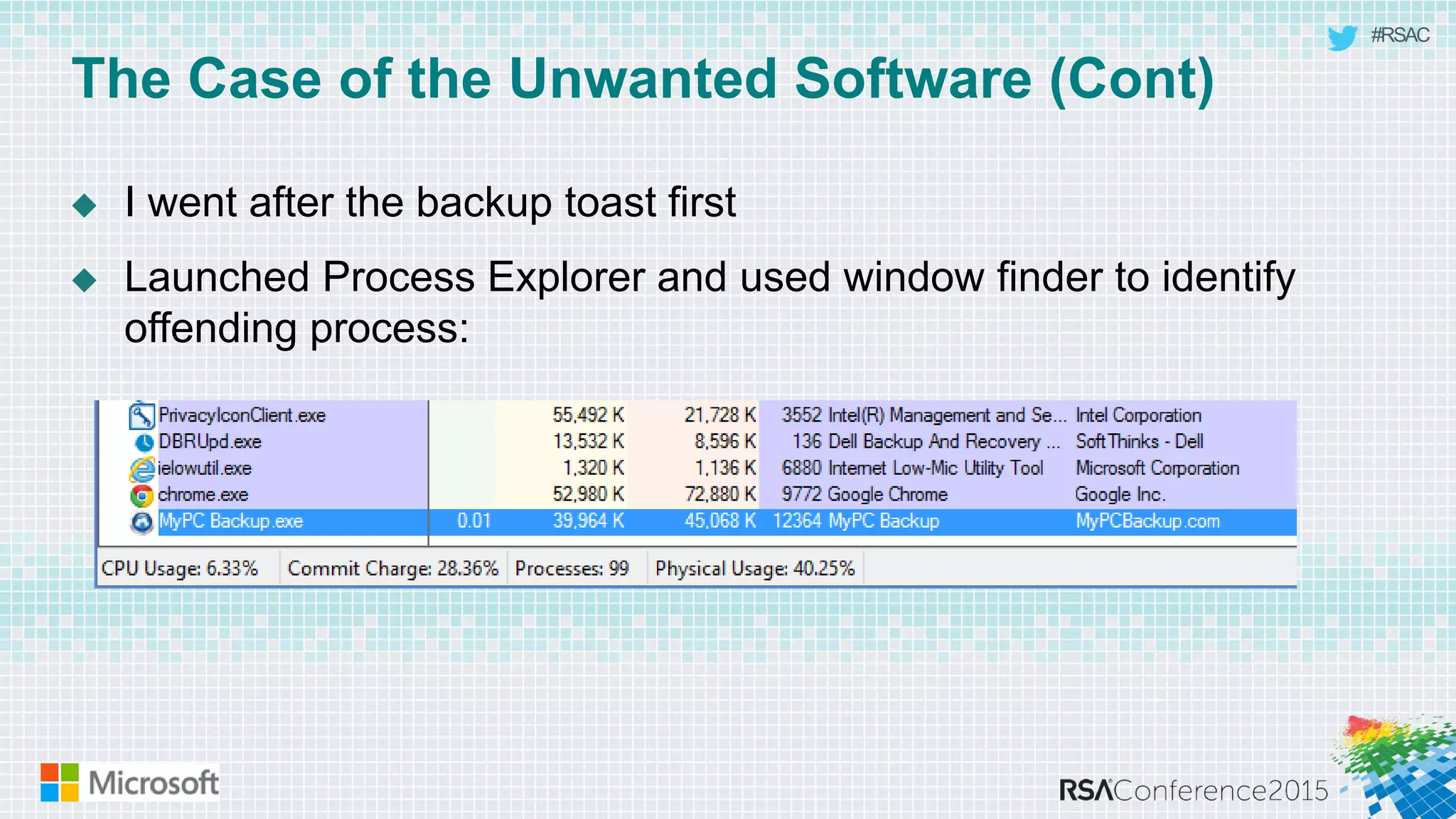
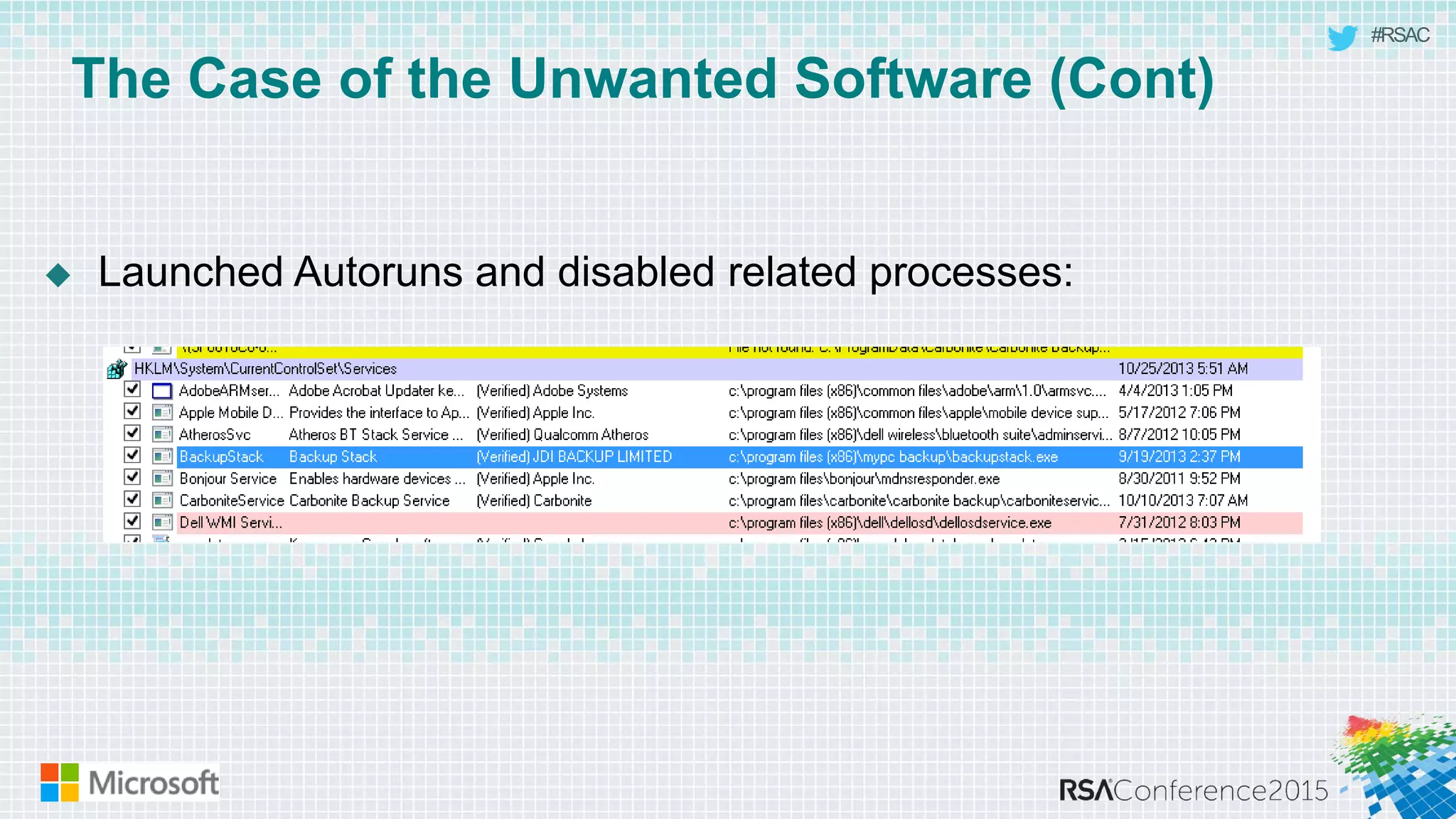
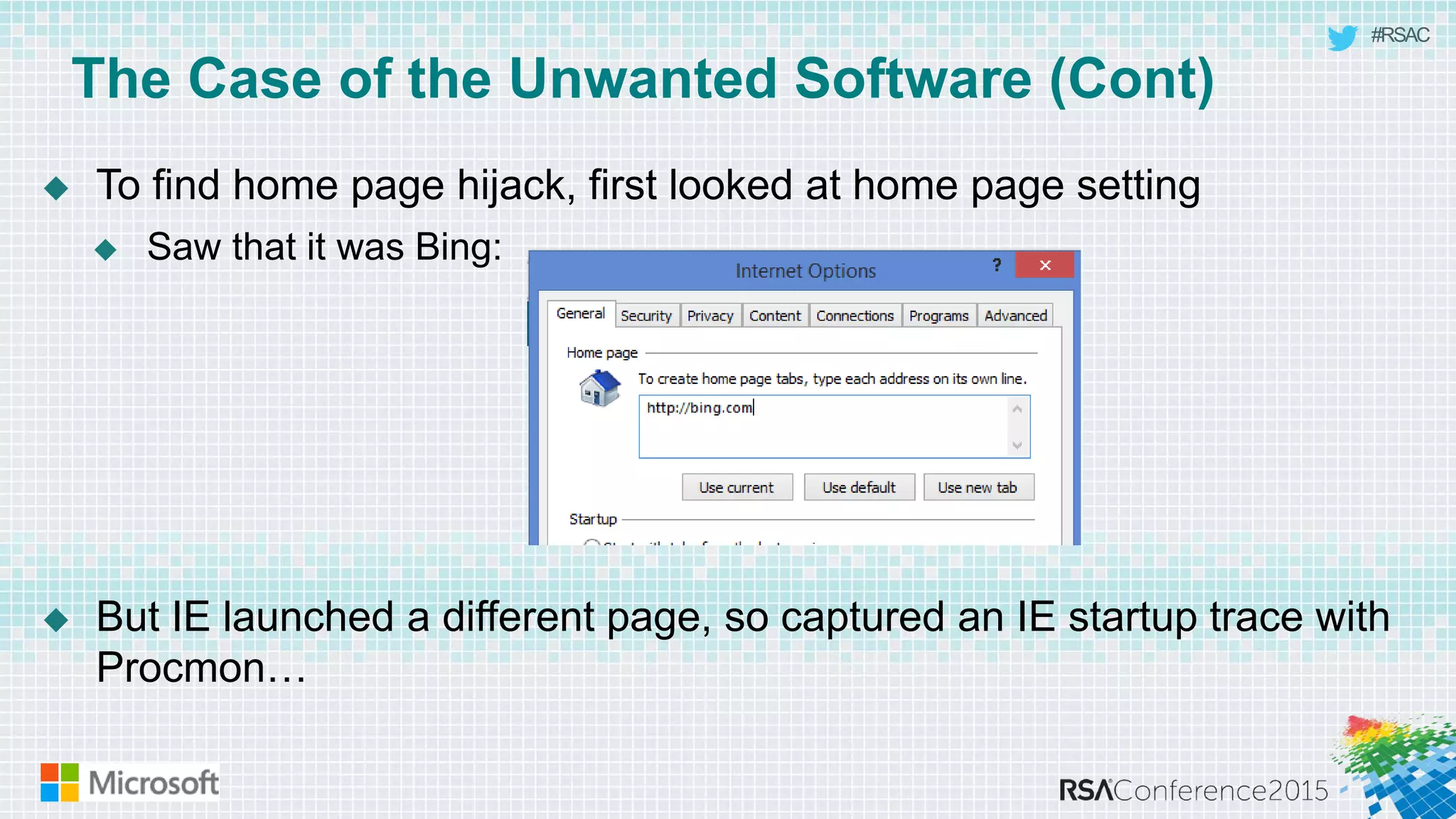
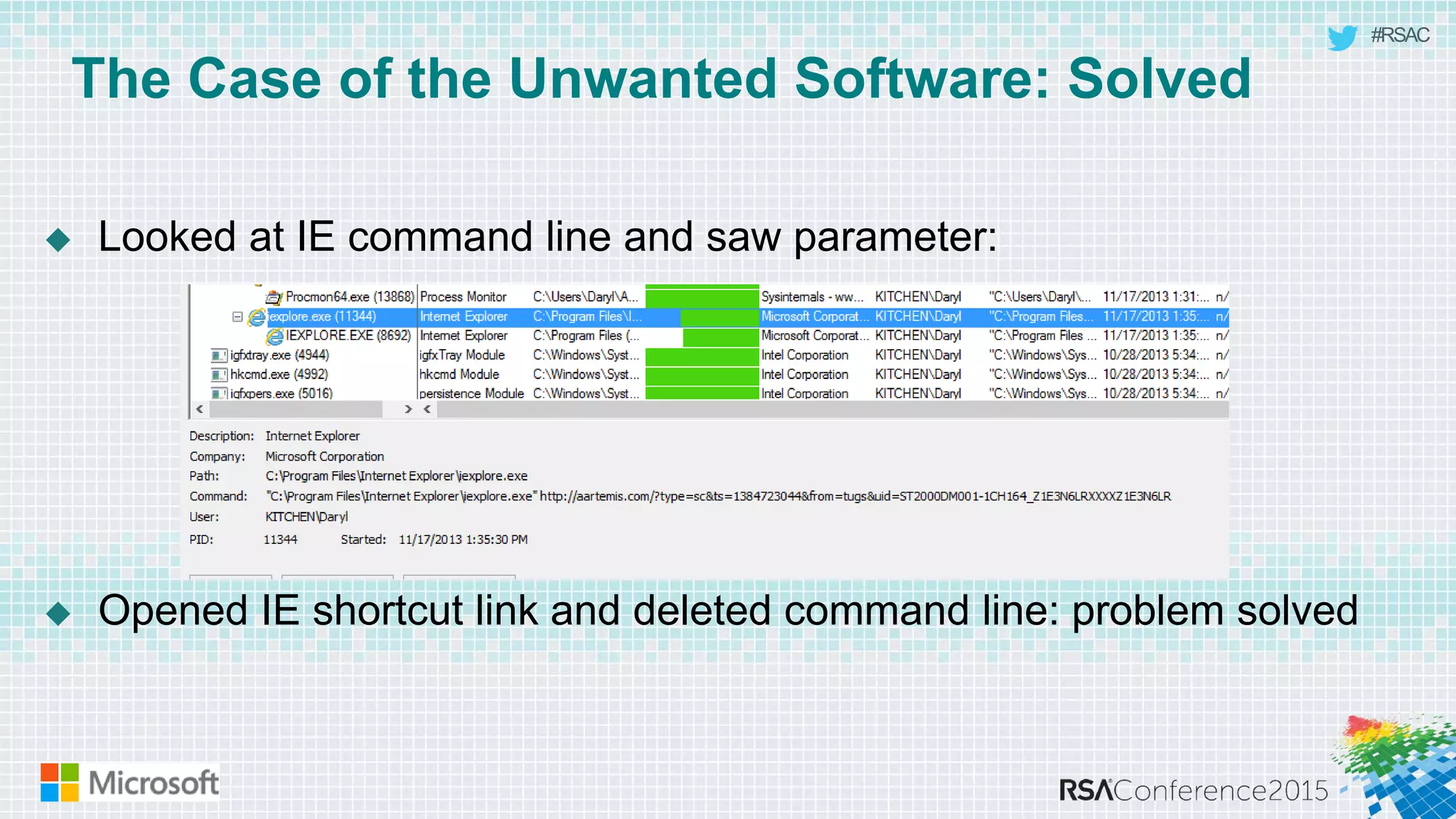
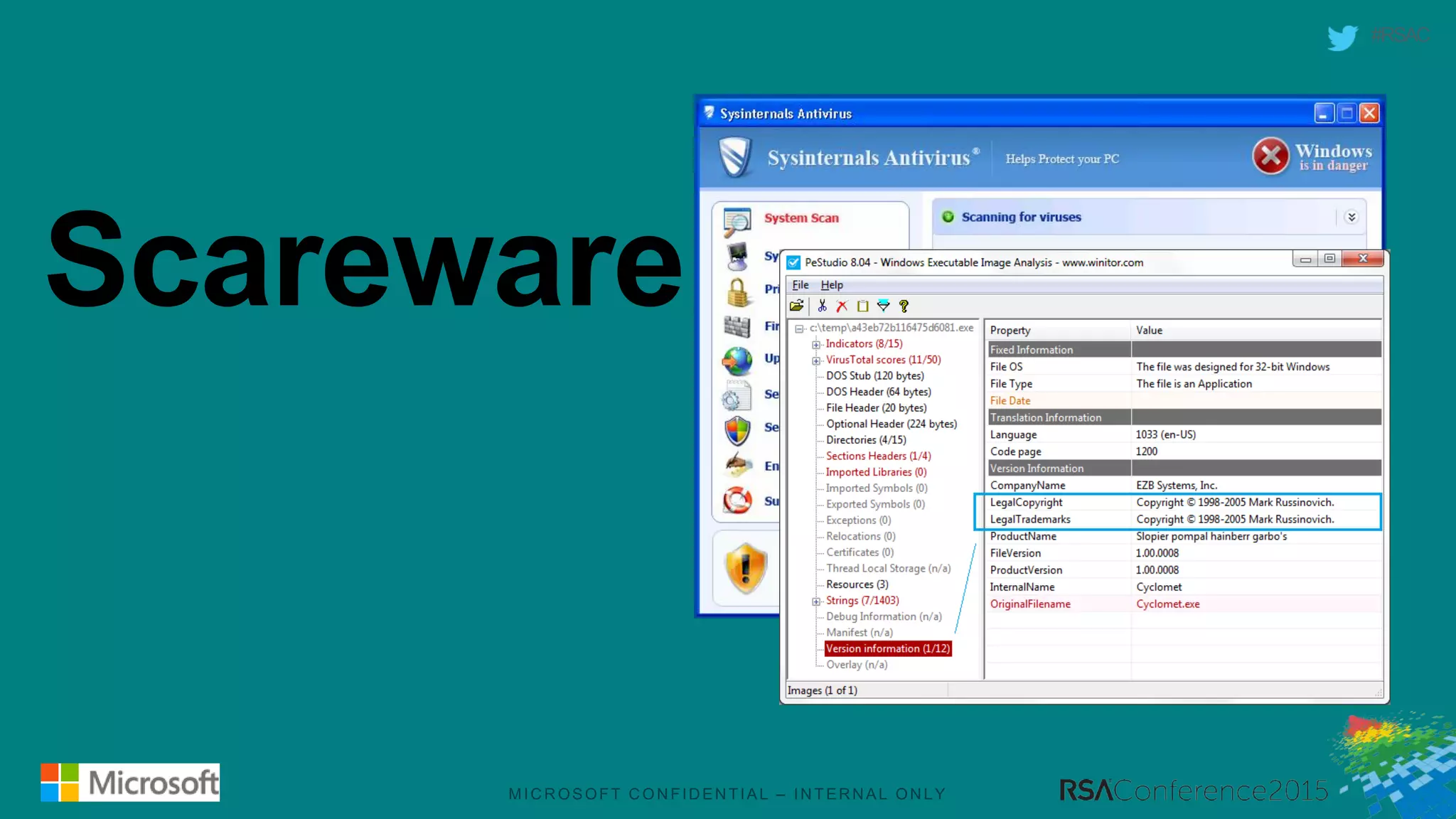
This document discusses tools from the Sysinternals suite that can be used for malware hunting and cleaning infected systems. It describes Process Explorer for investigating processes, Autoruns for identifying malware autostarts, and Process Monitor for tracing malware activity. The tools provide detailed system information that can help identify malicious processes, files, and registry entries associated with an infection. The document provides an overview of the key features of each tool and how they can be used together to analyze a compromised system and remove malware.