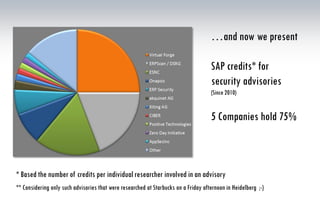
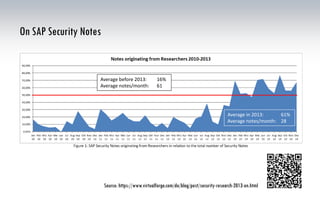
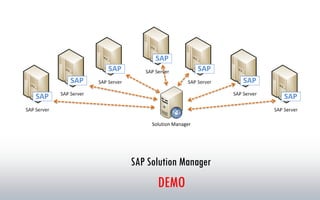
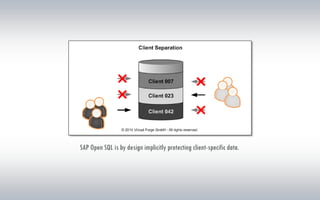
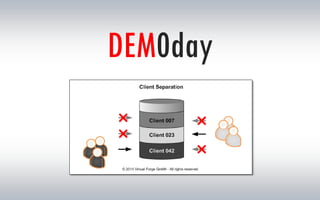
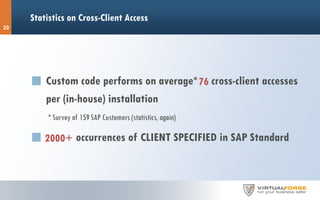
The document discusses the risks associated with hosted SAP environments, highlighting vulnerabilities in SAP Solution Manager and the implications of multi-system and single-system hosting. It emphasizes the high attack surface of SAP systems and the potential for cross-client access vulnerabilities that could impact data confidentiality and integrity. The authors, both SAP security researchers, advocate for proactive security measures and regular audits to mitigate these risks.