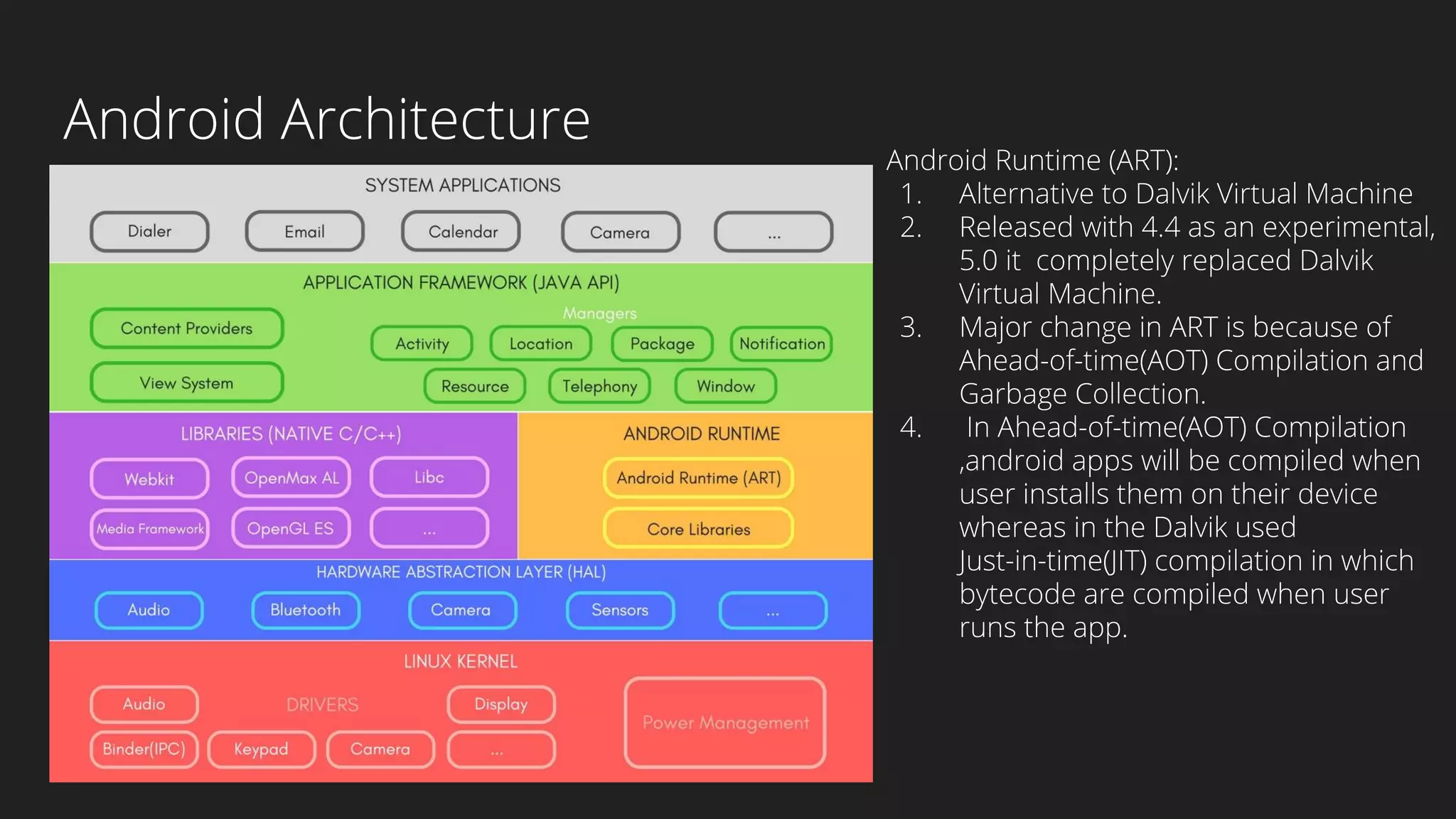
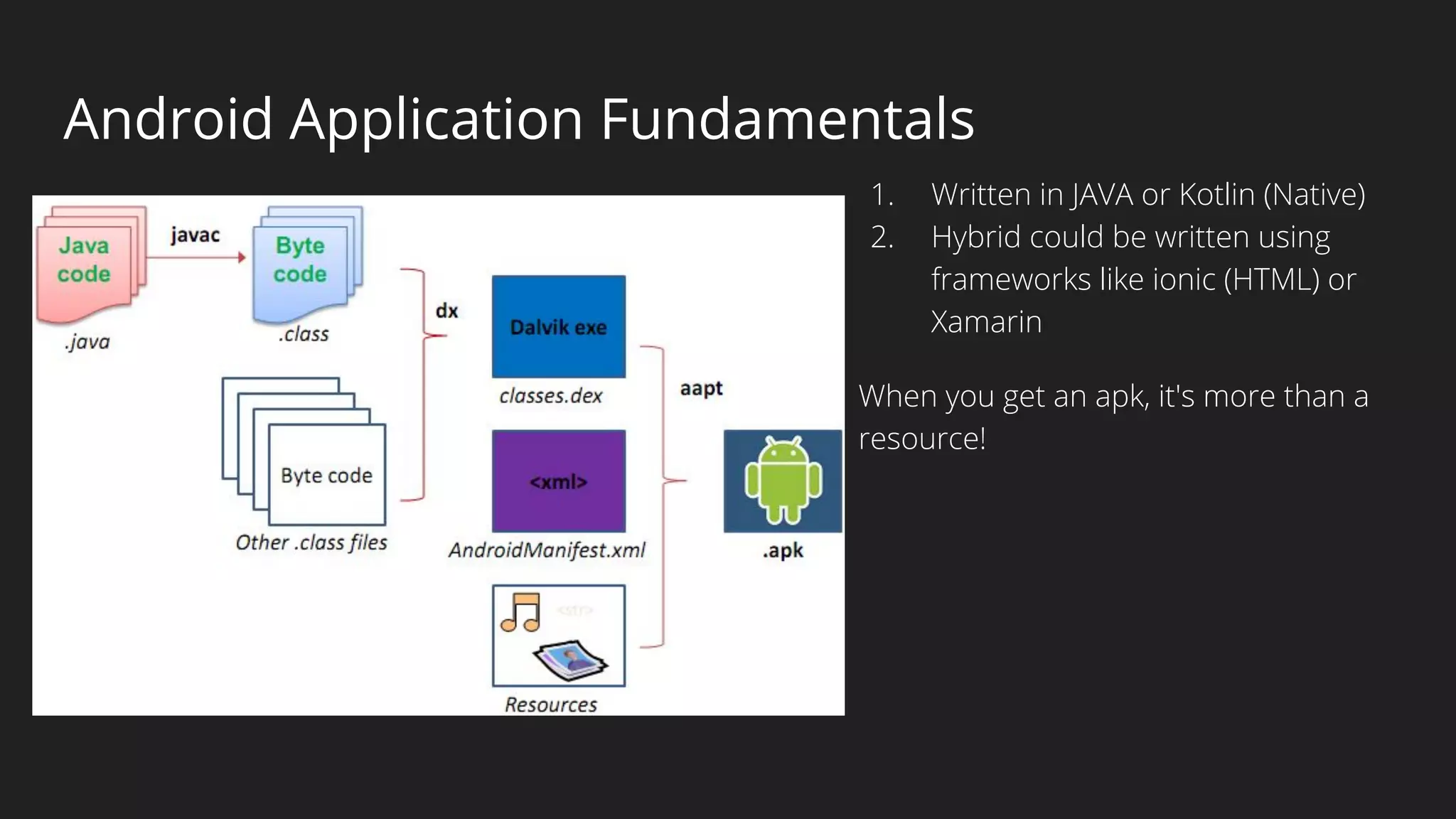
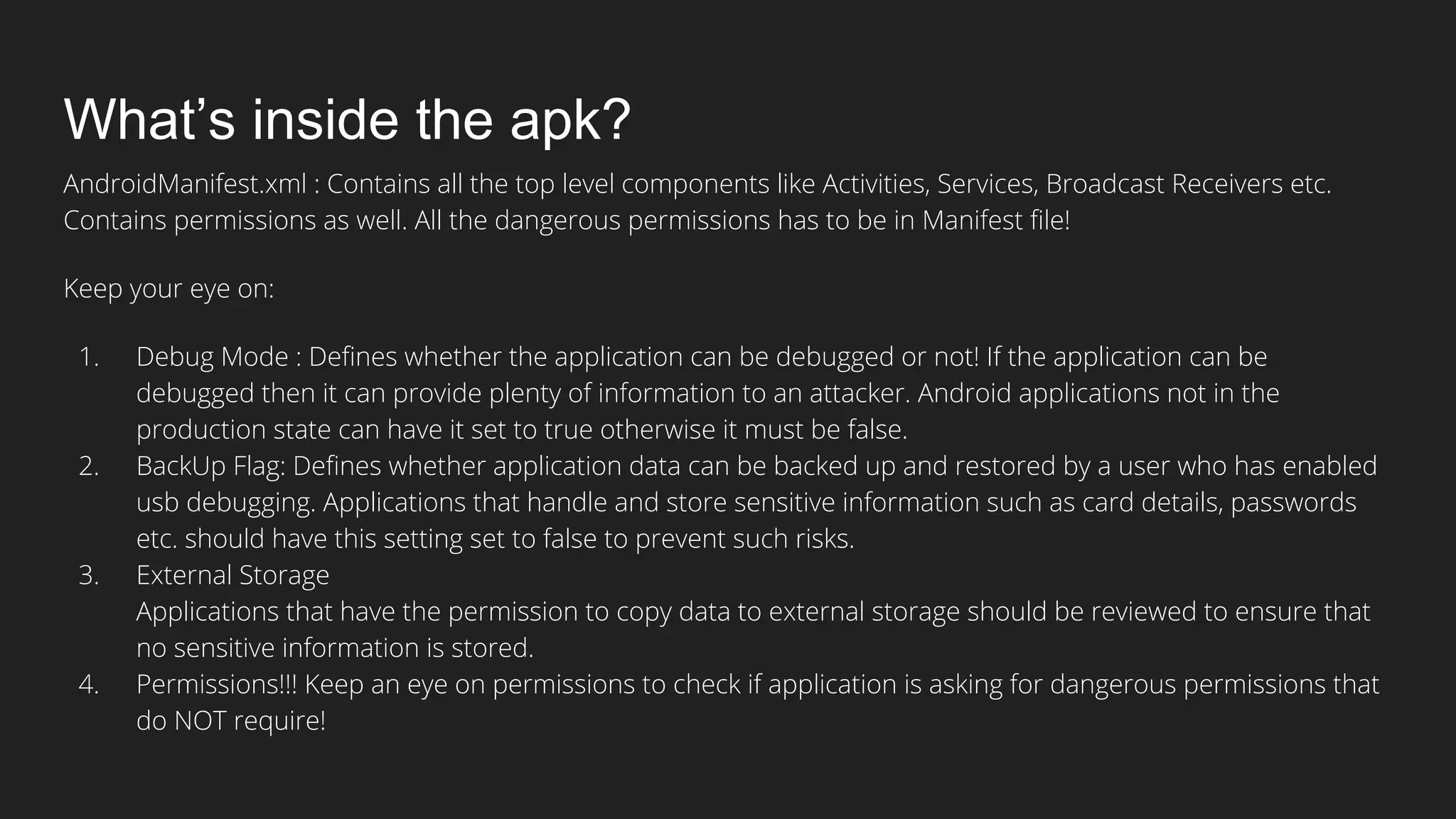
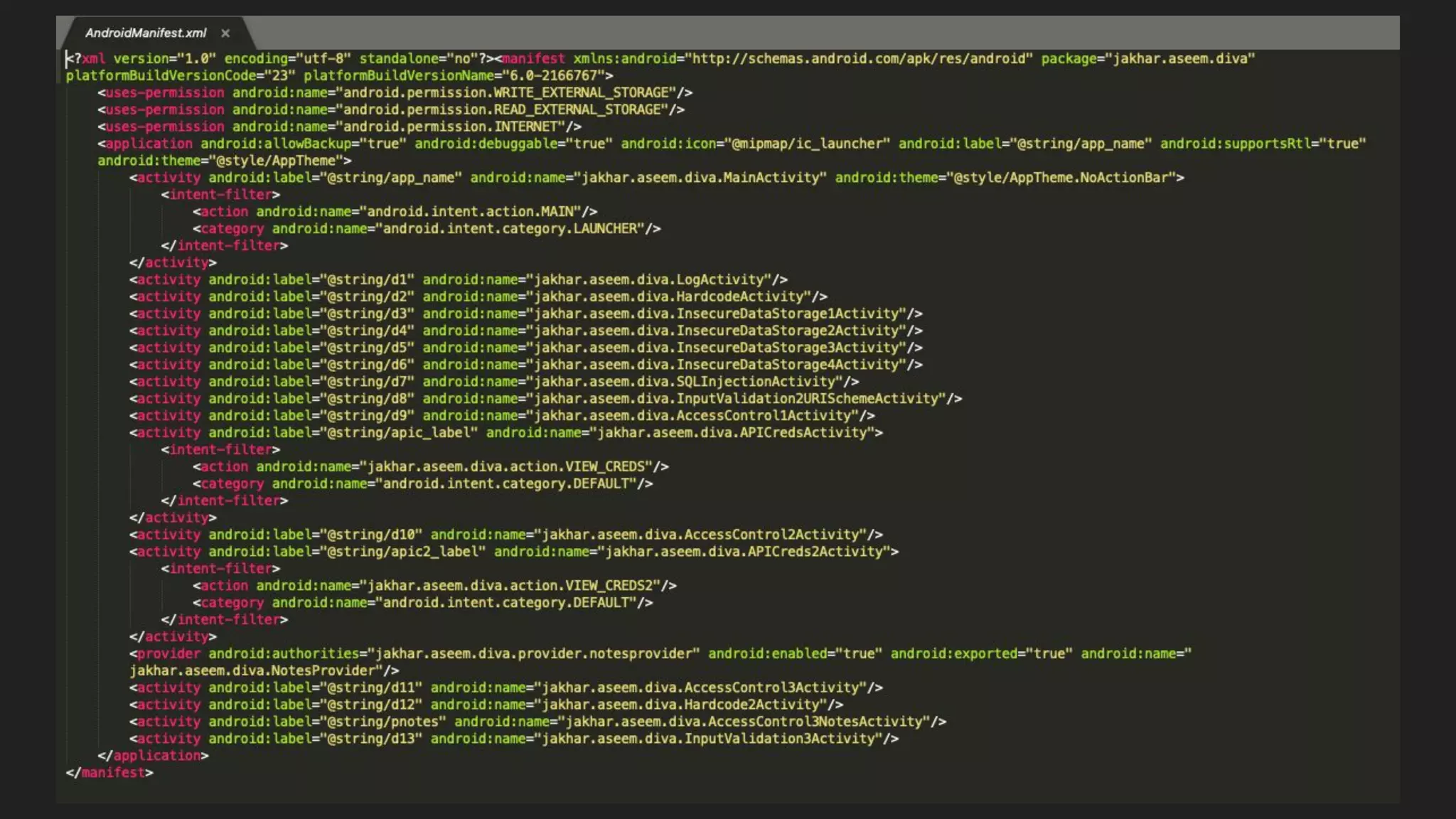
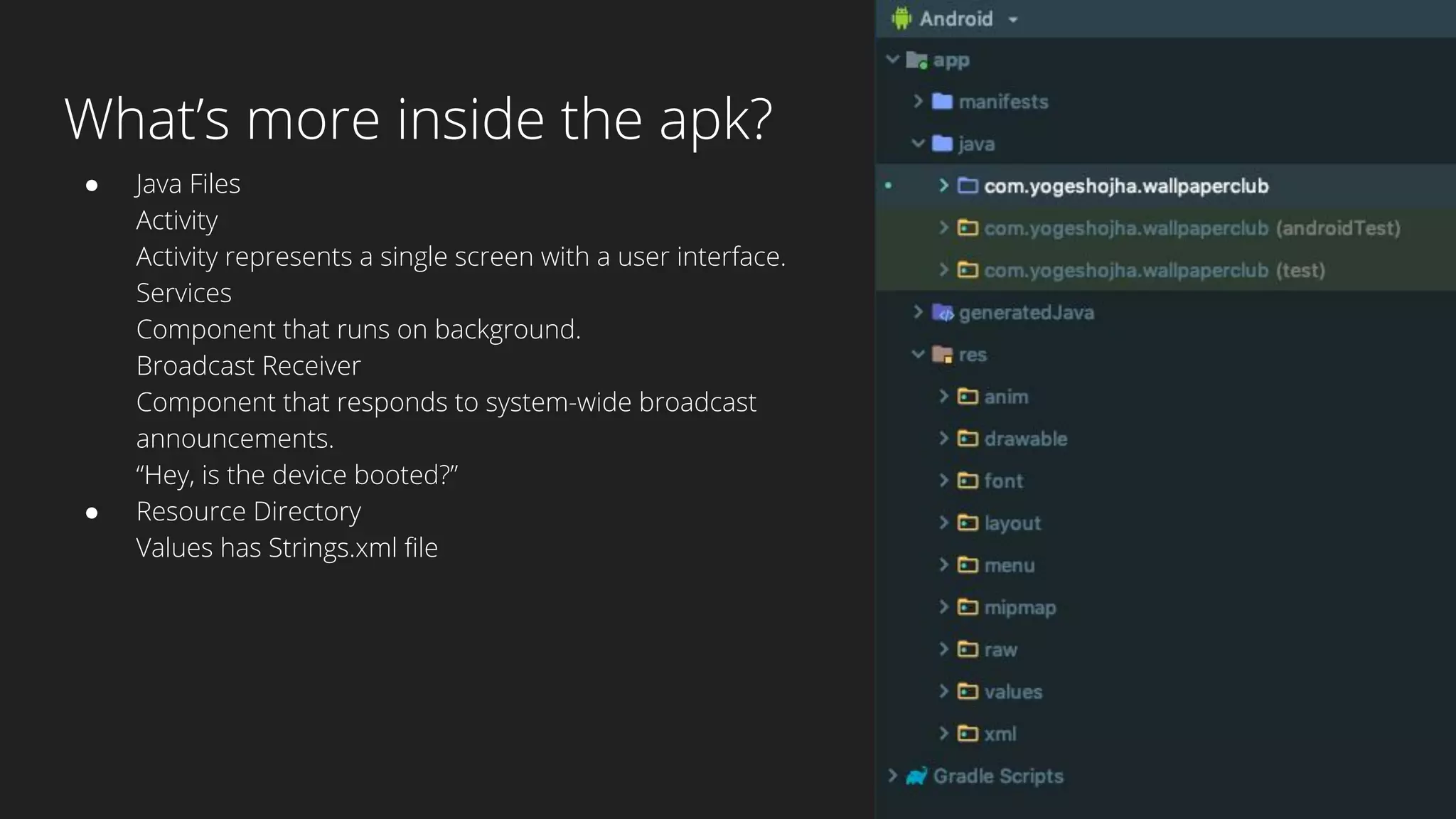
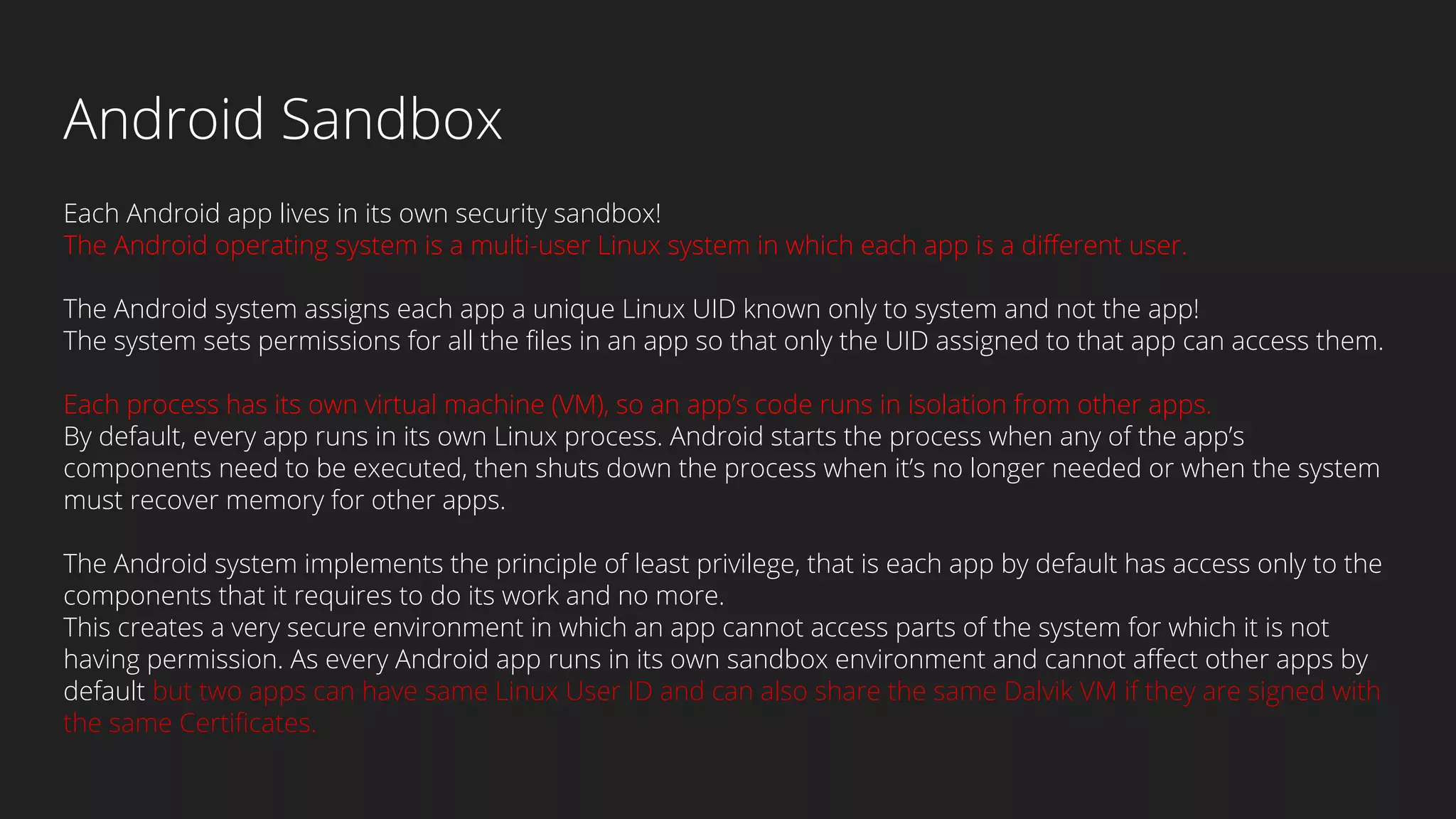
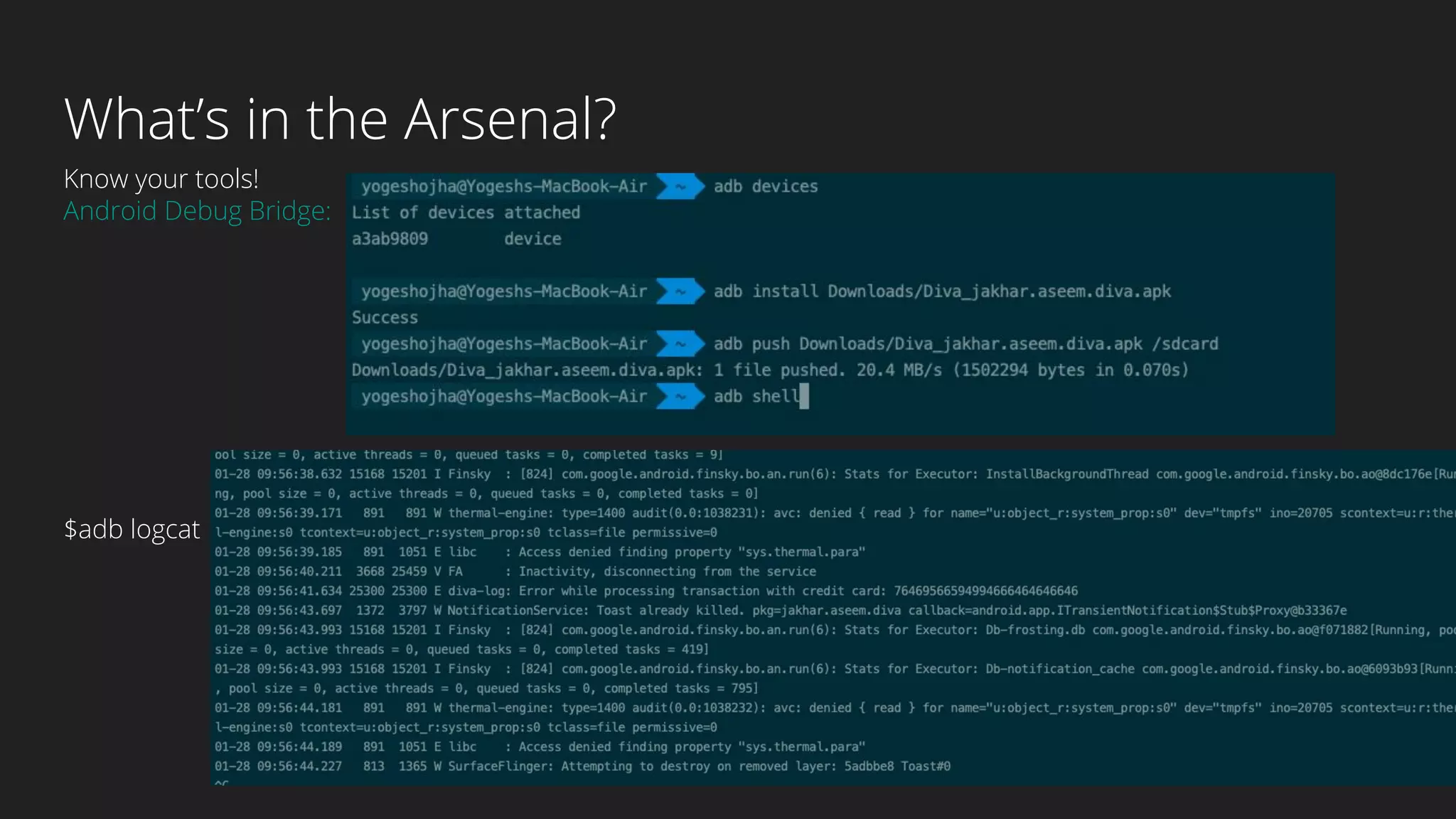
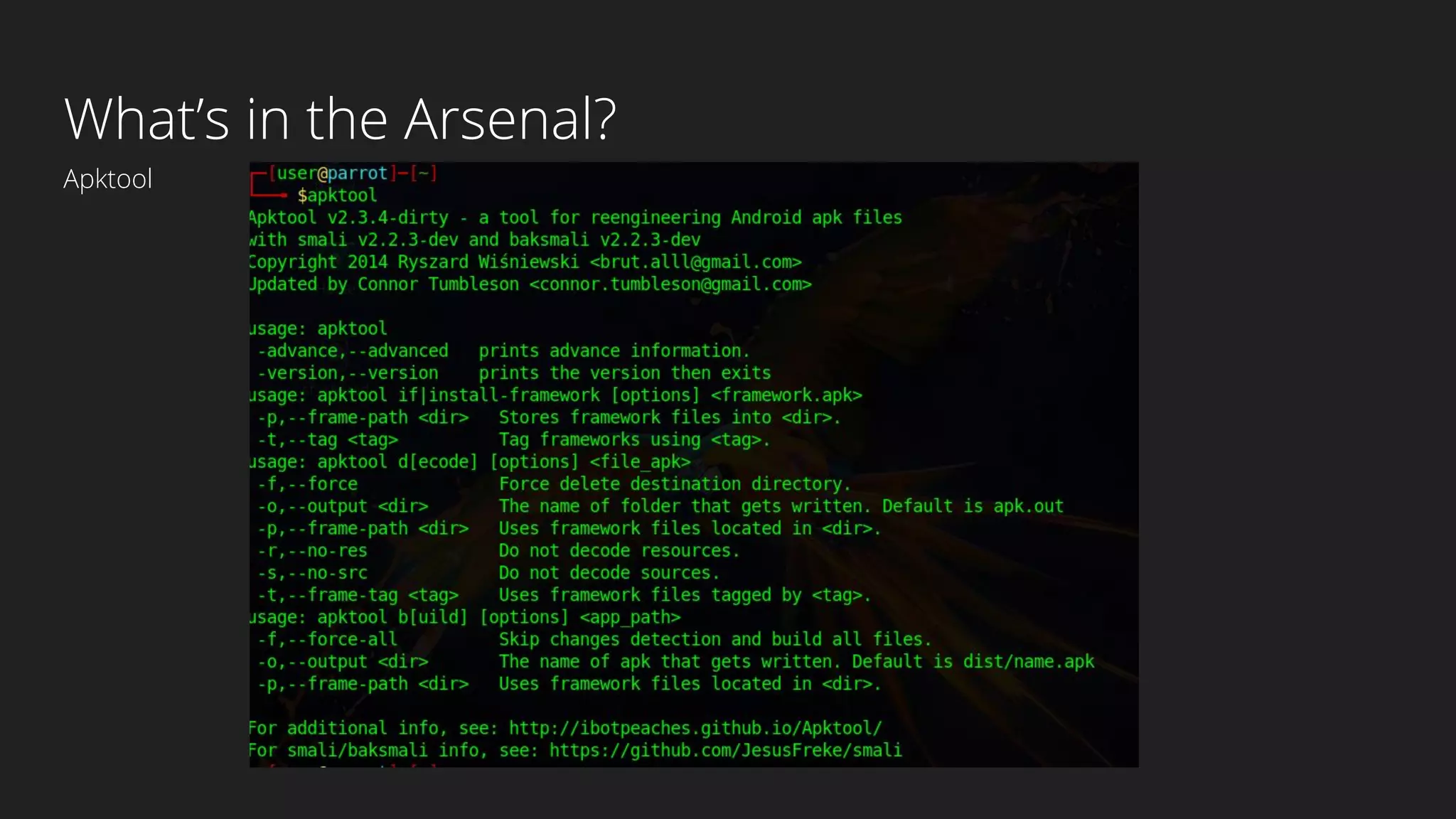
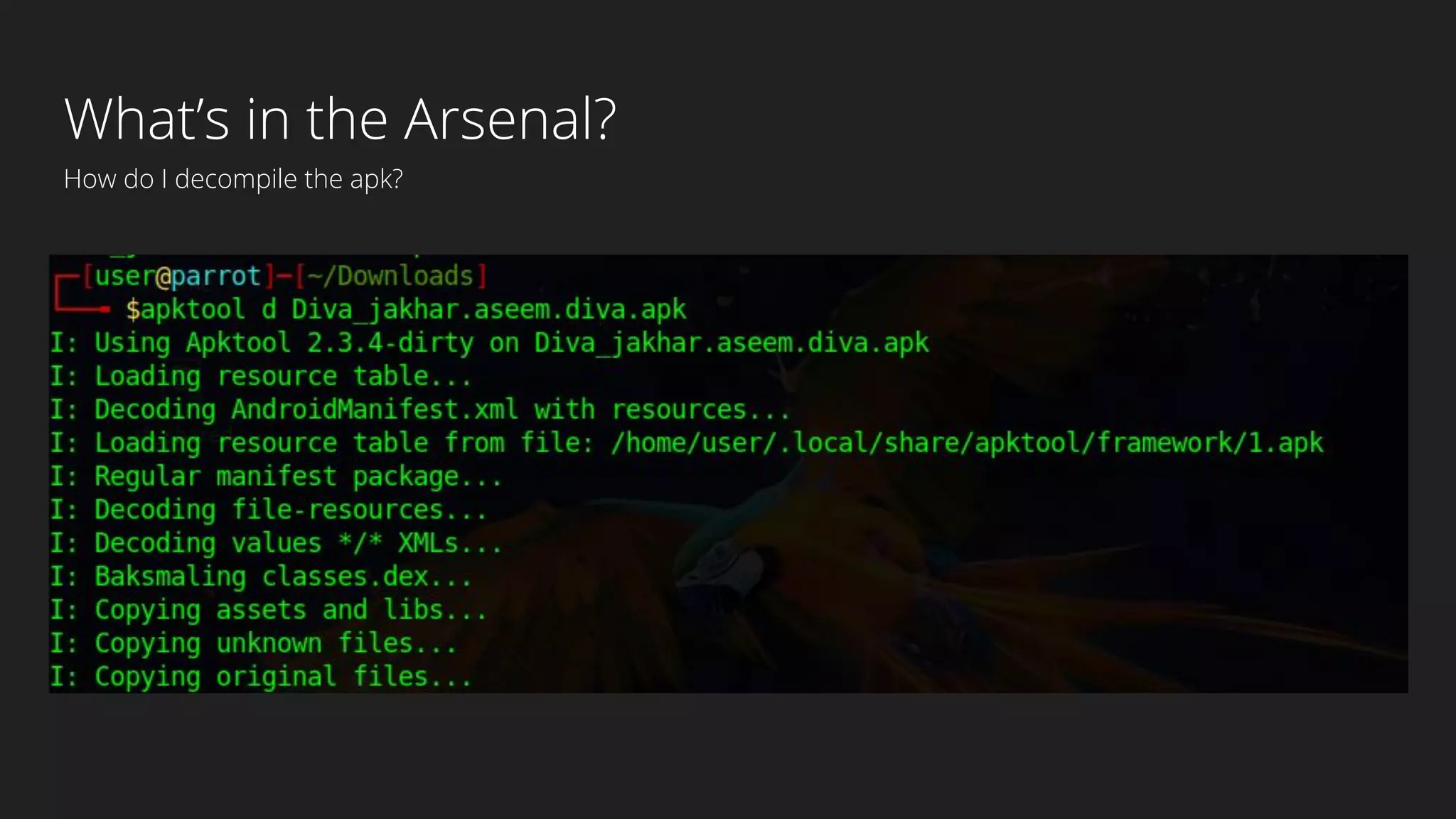
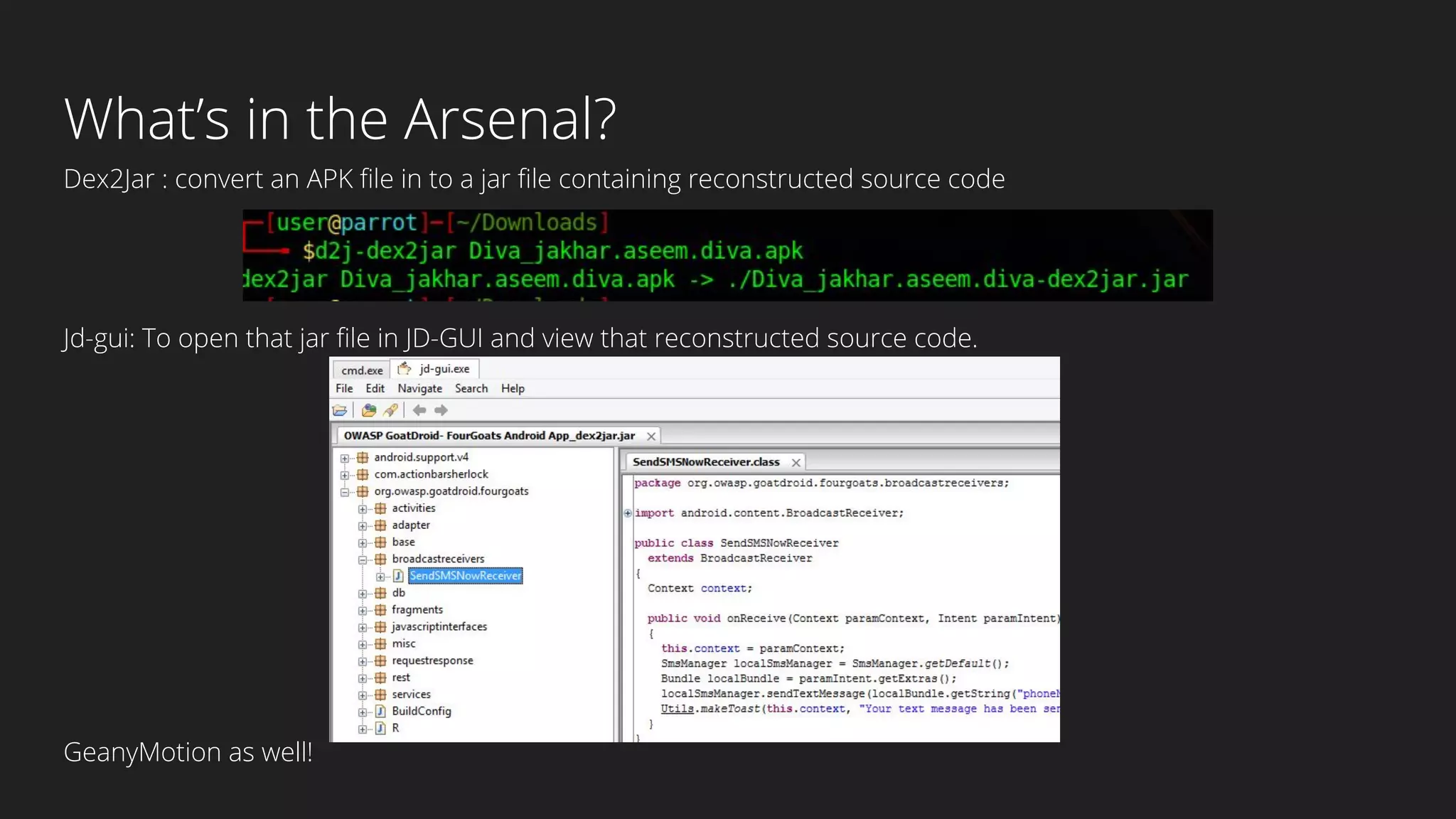
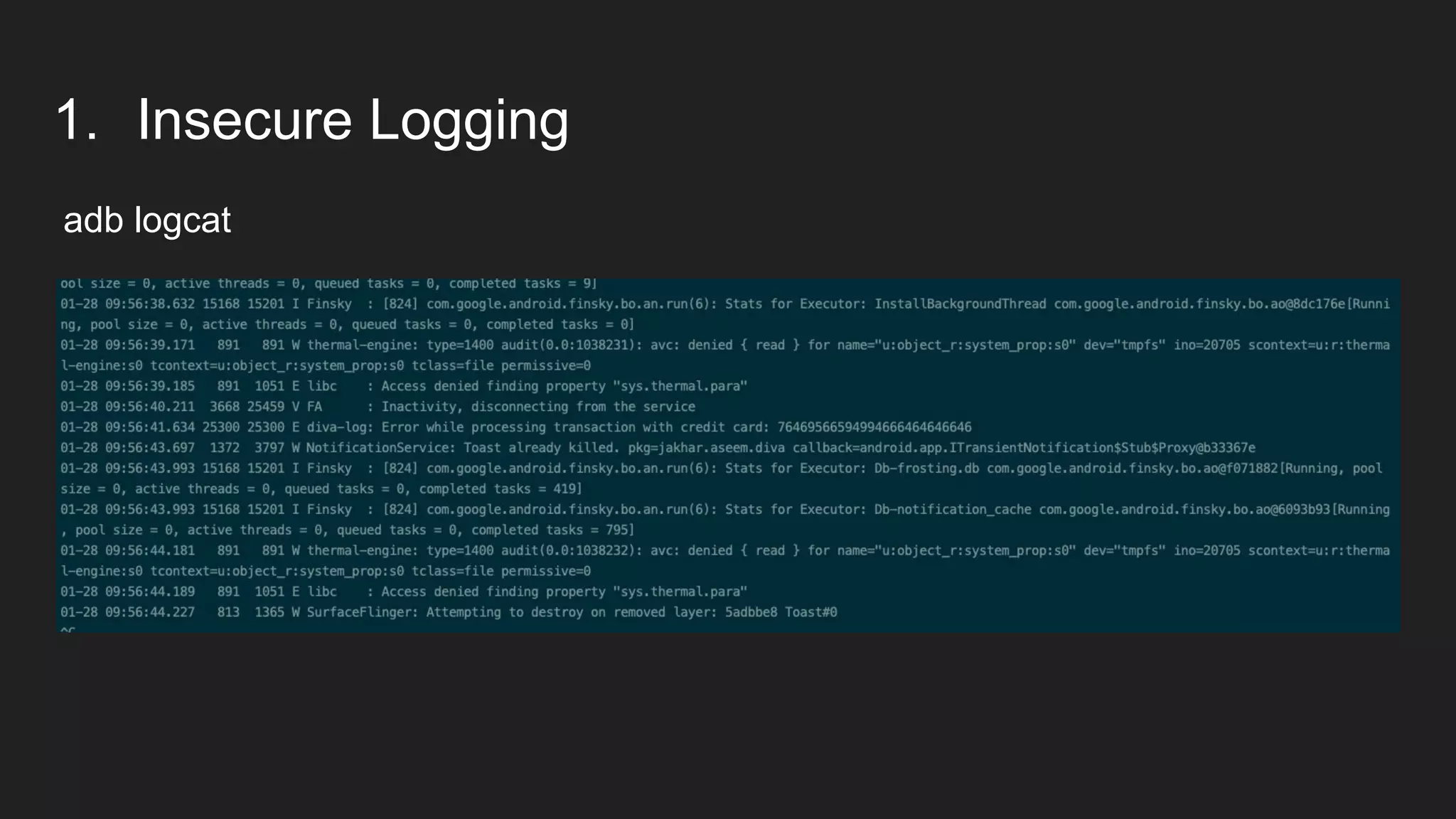
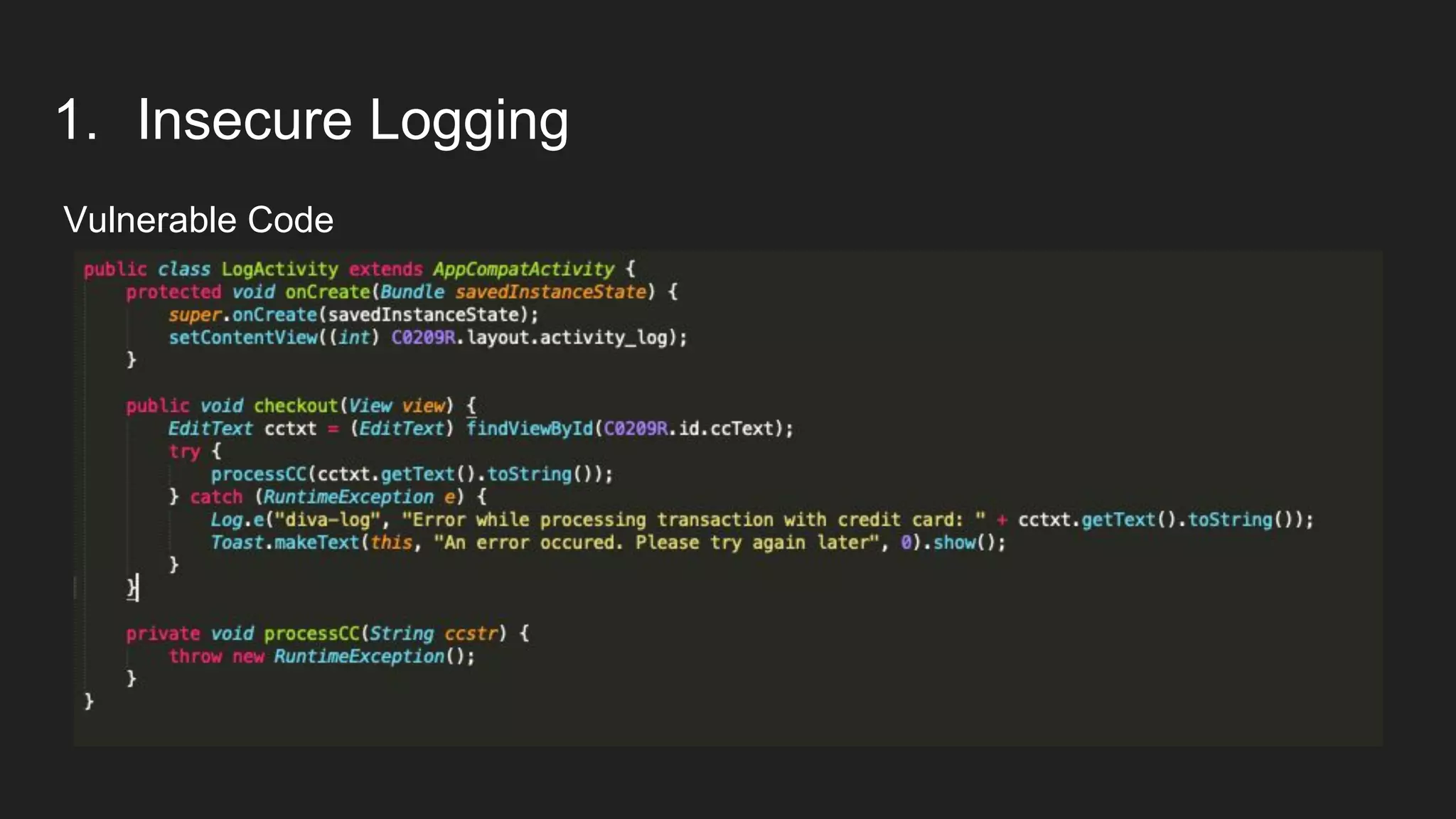
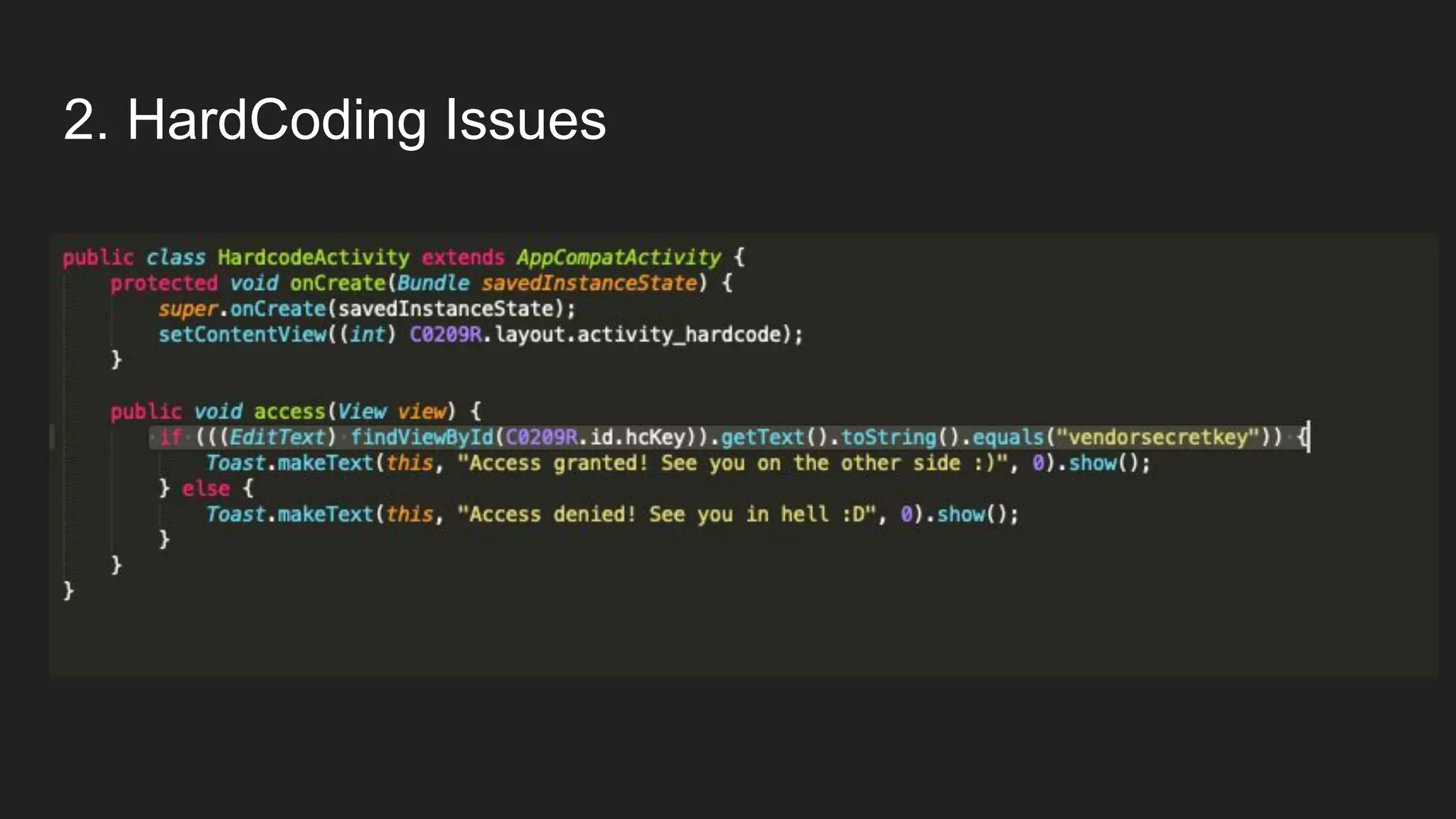
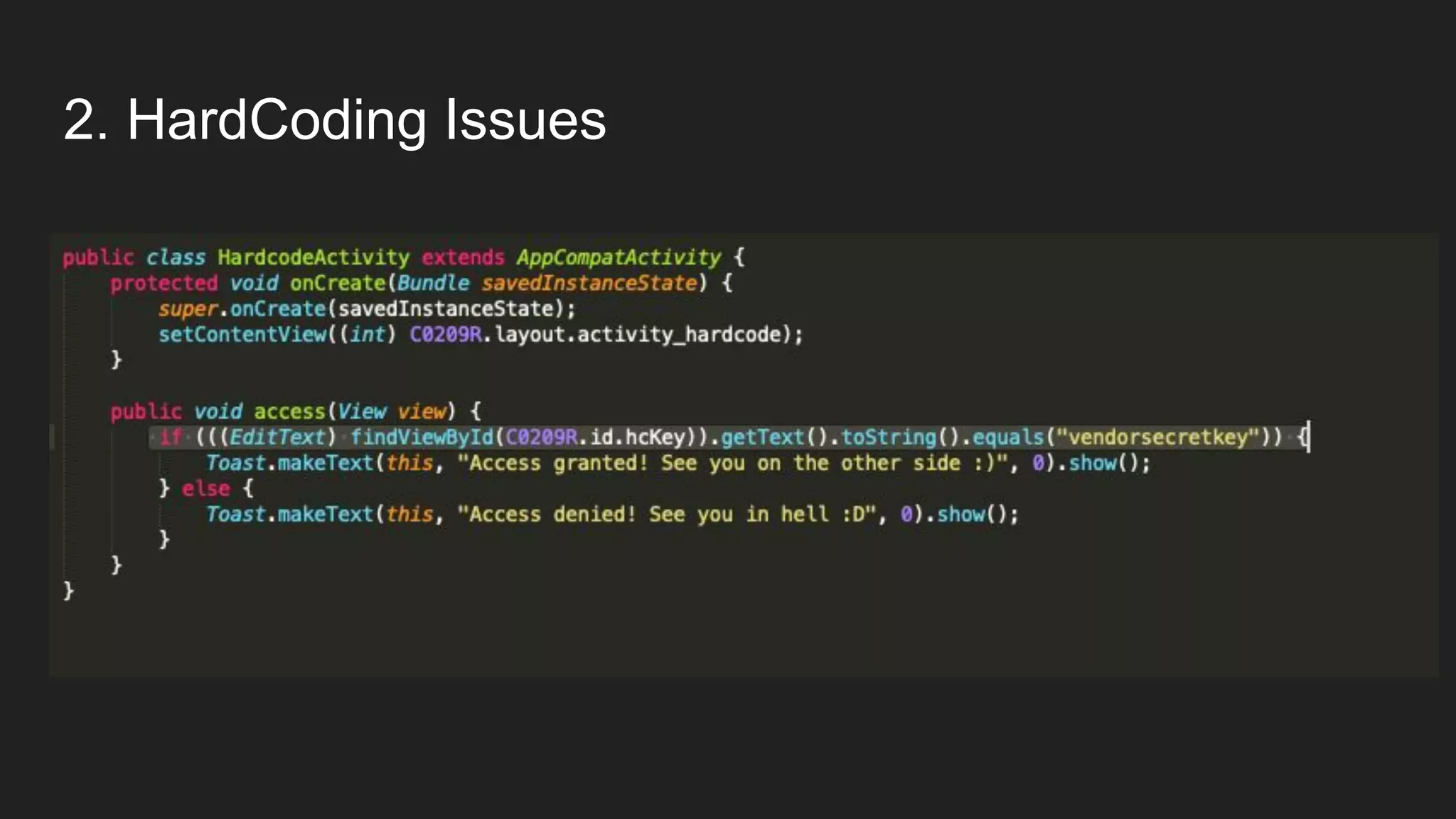
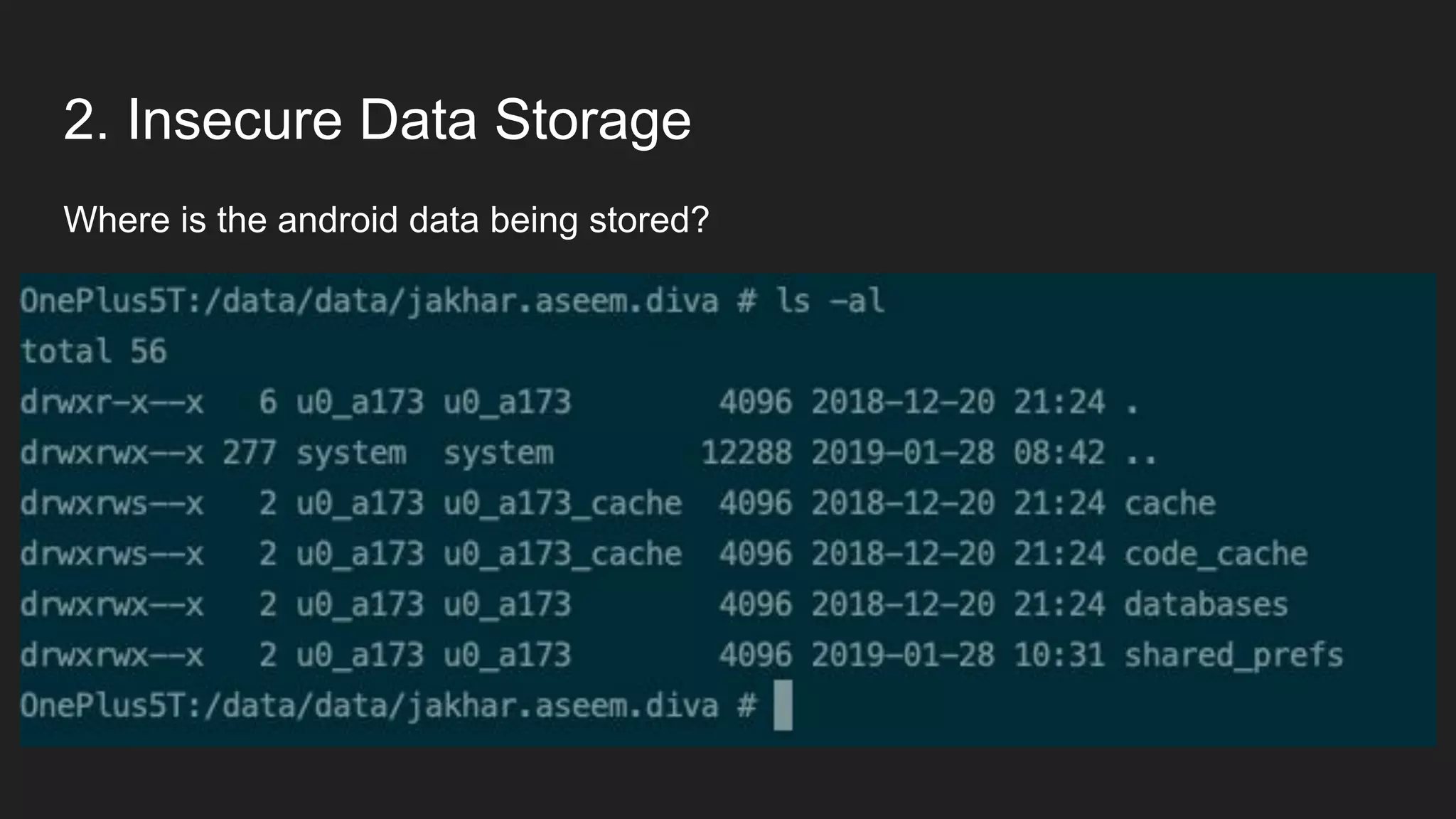
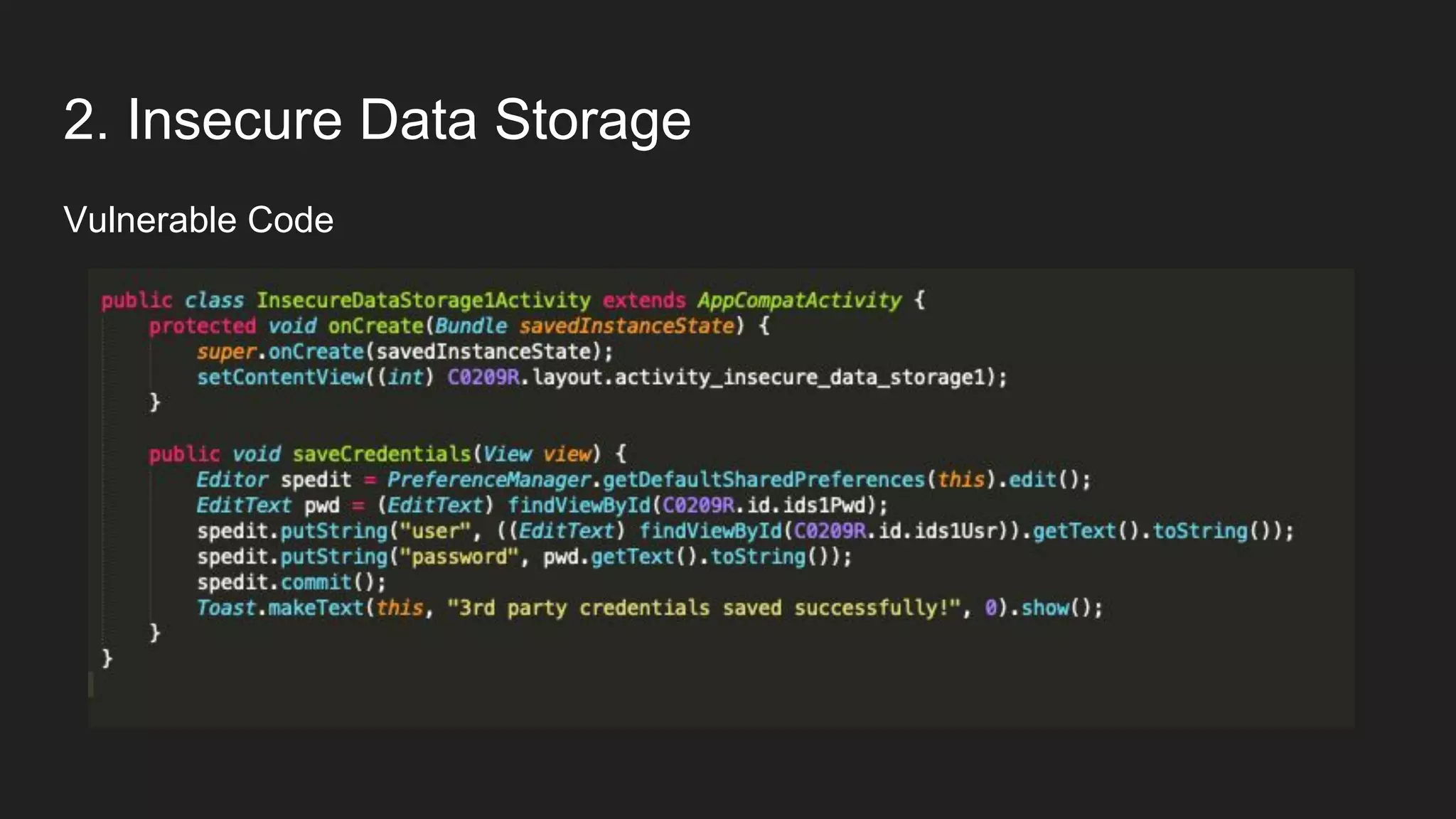
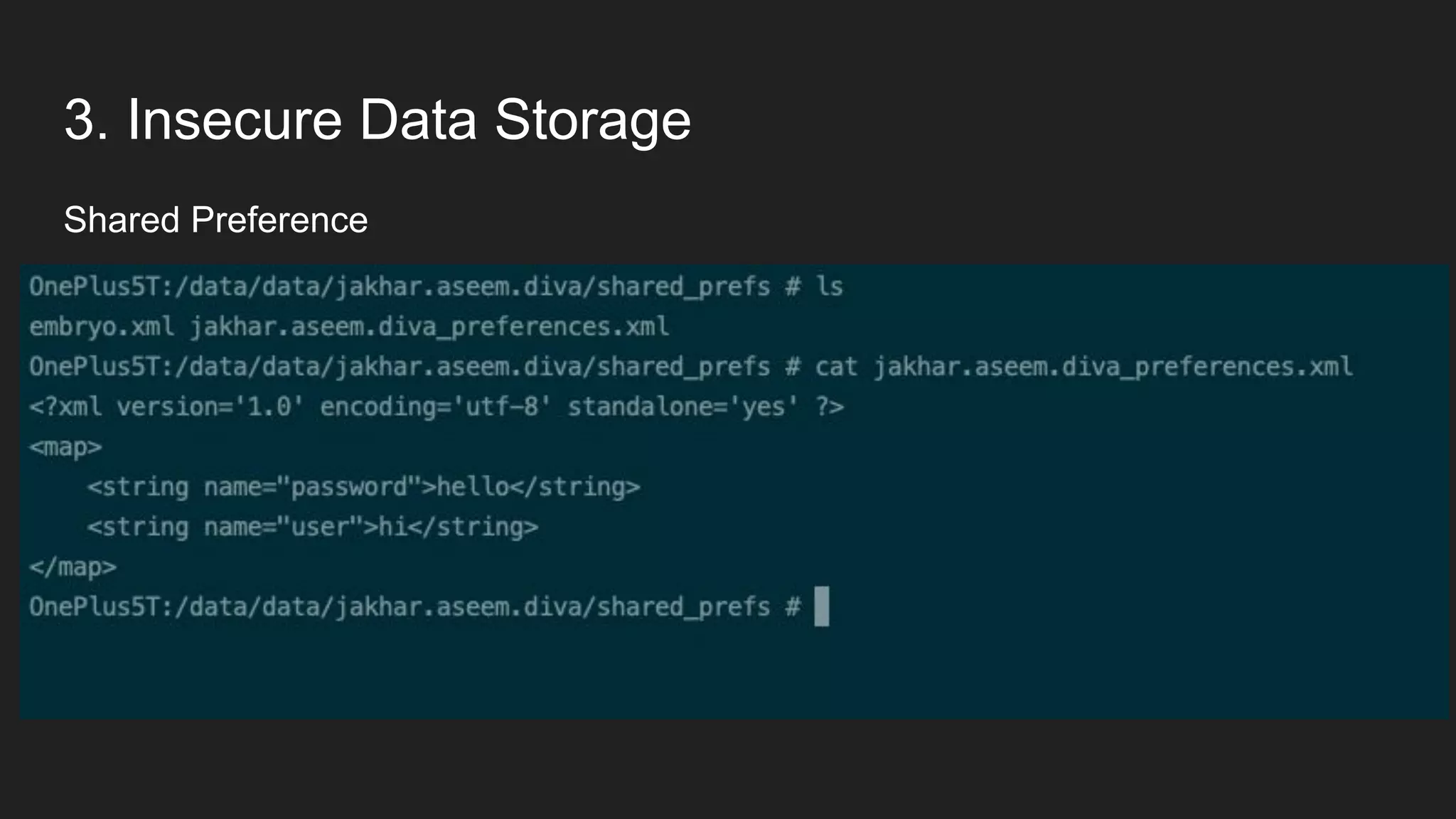
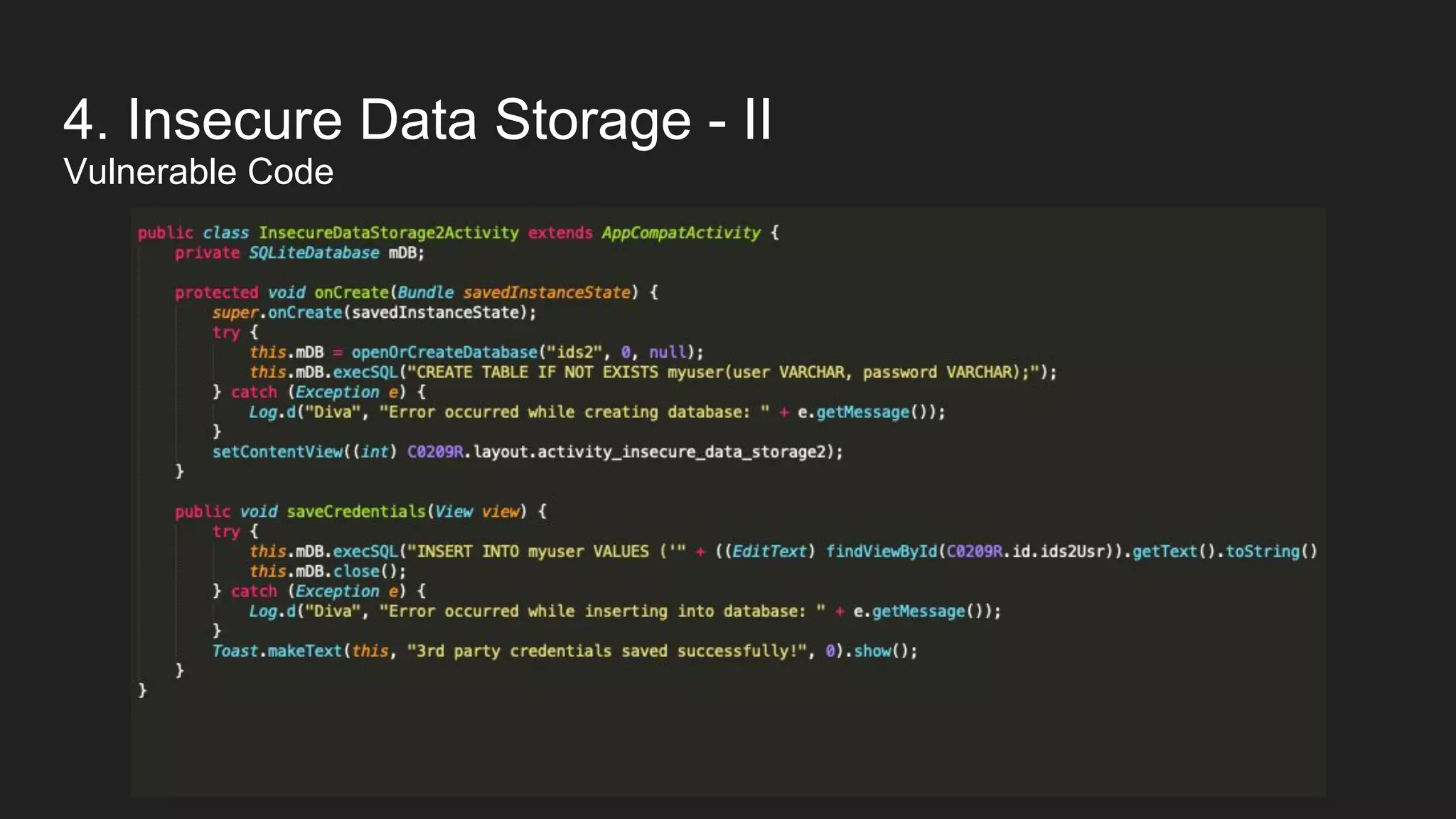
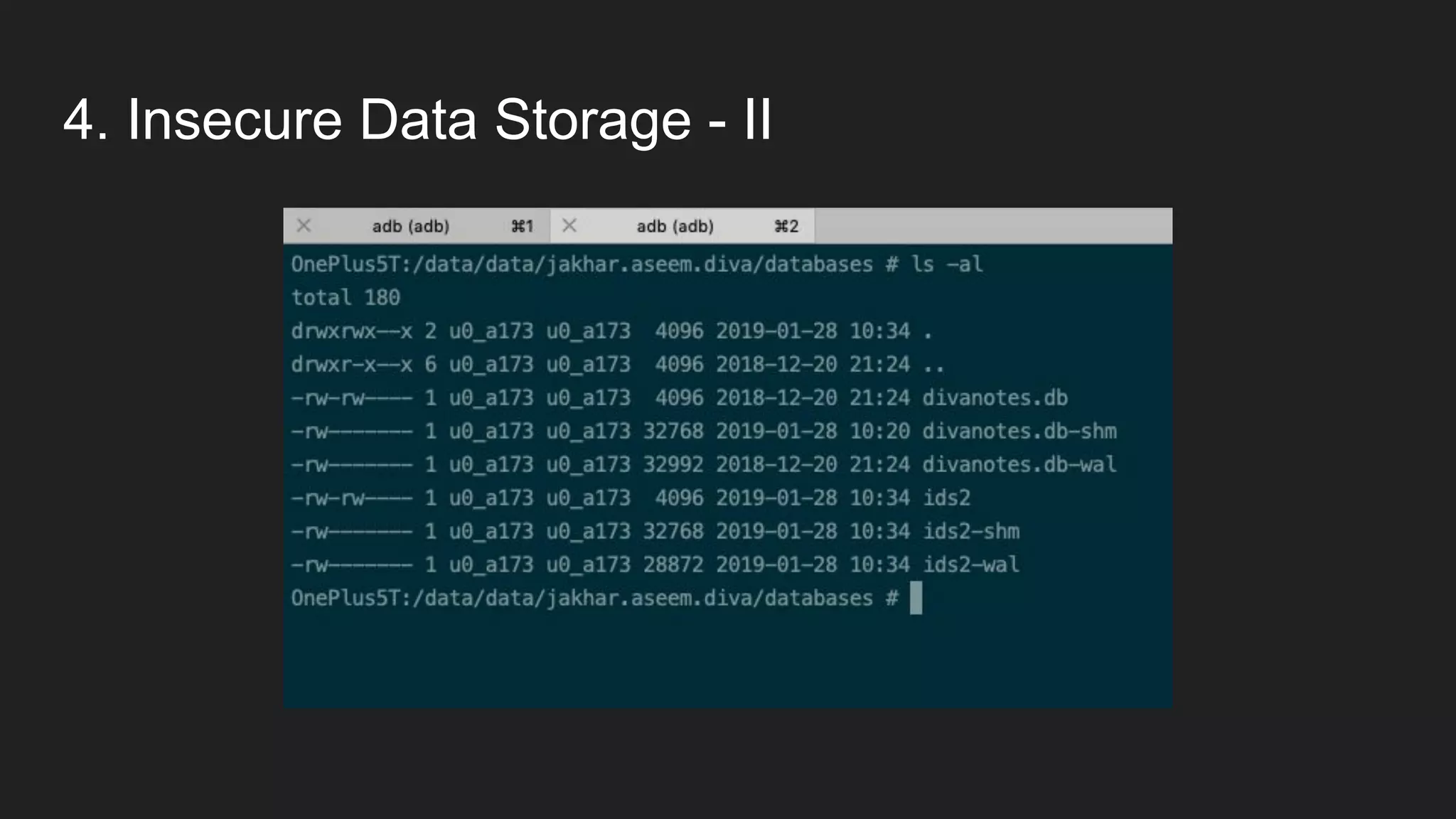
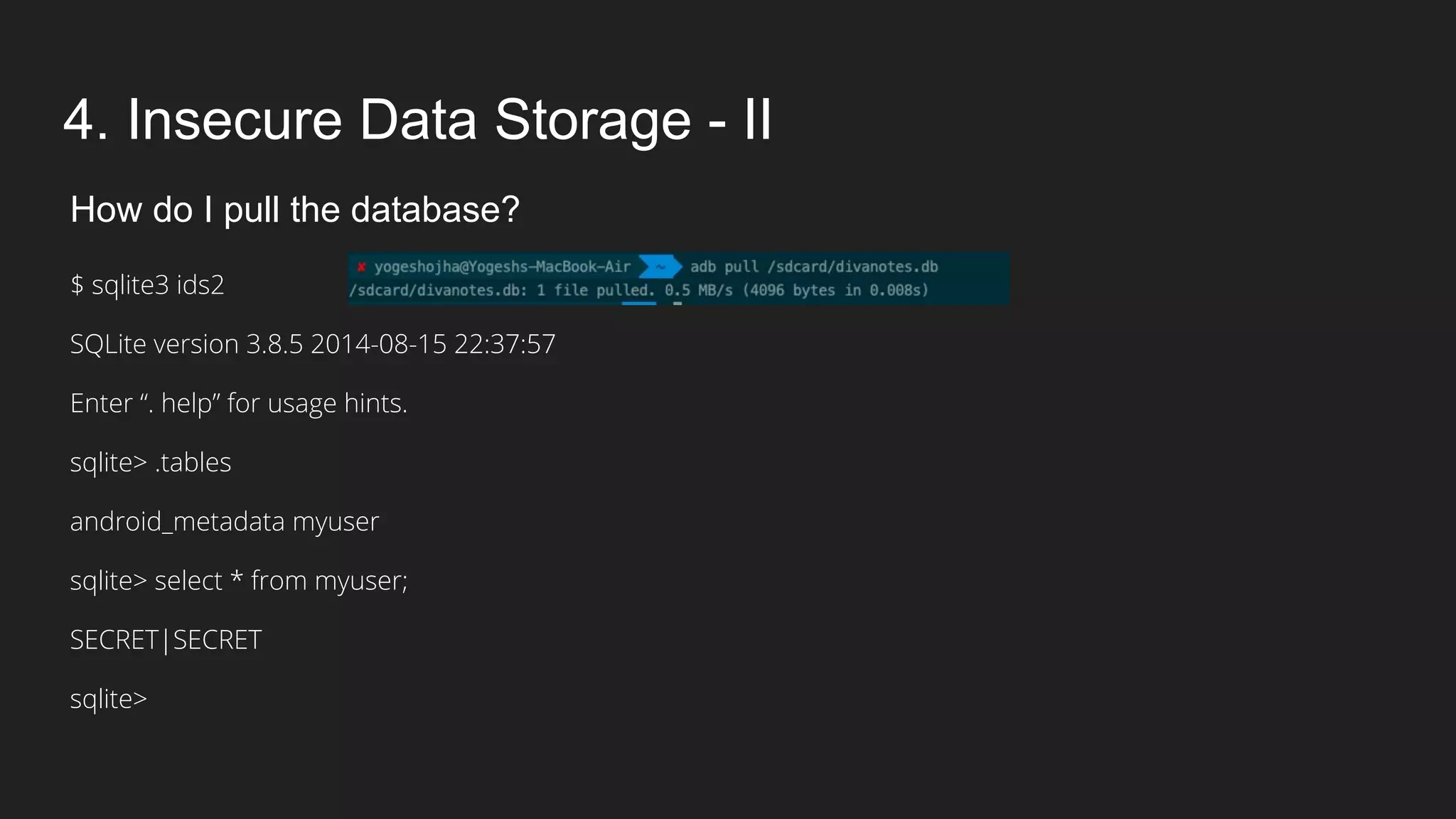
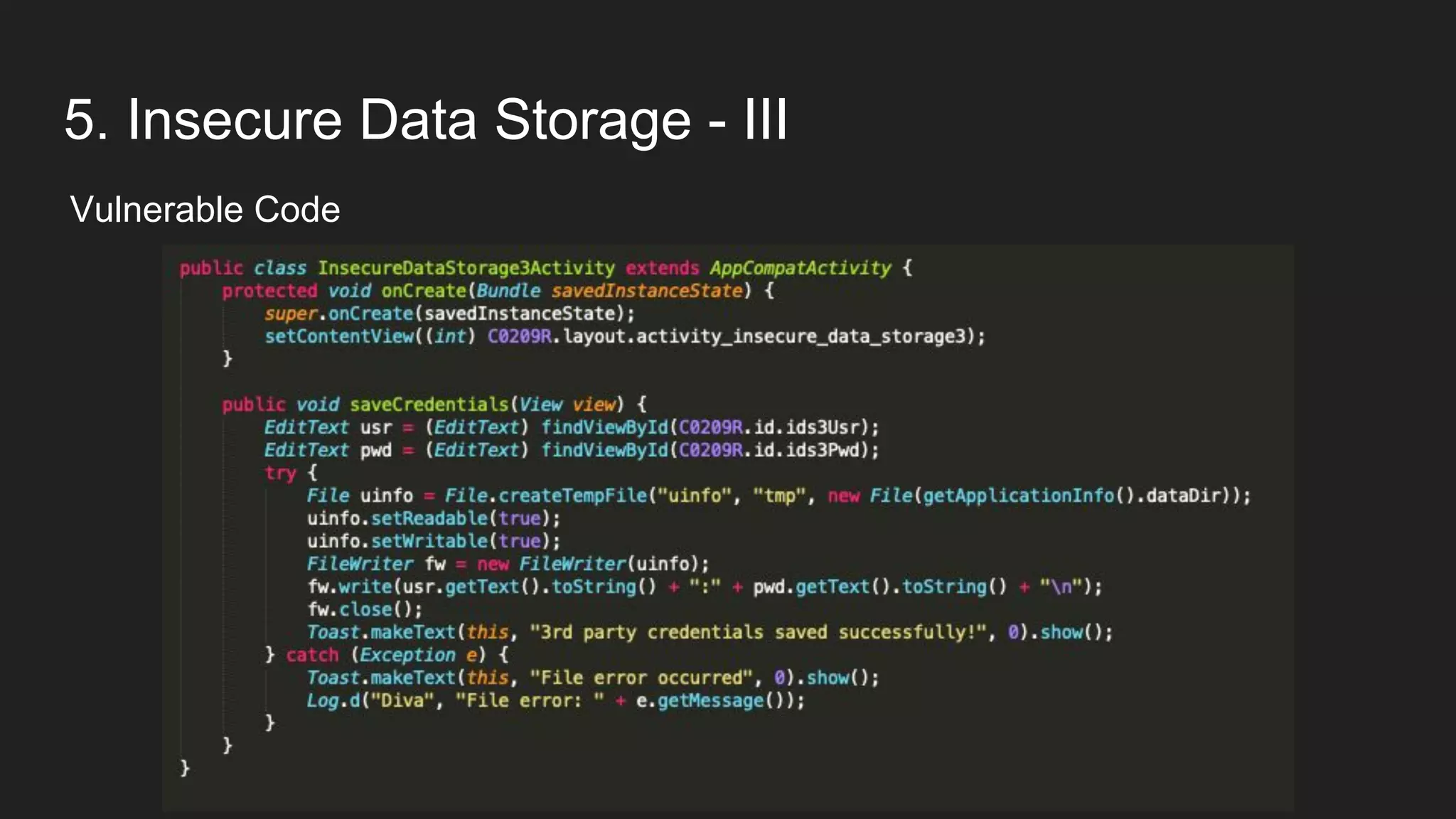
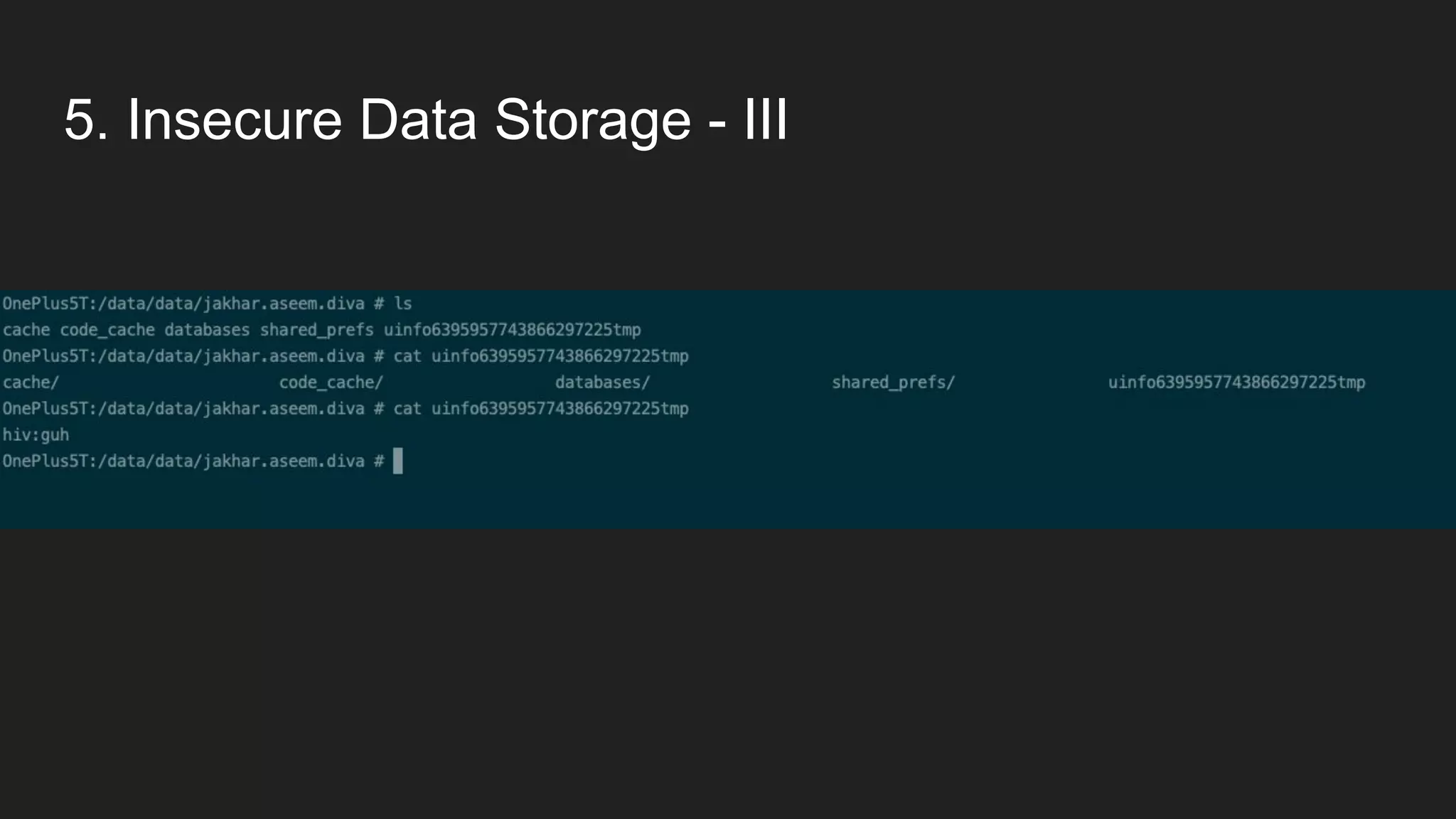
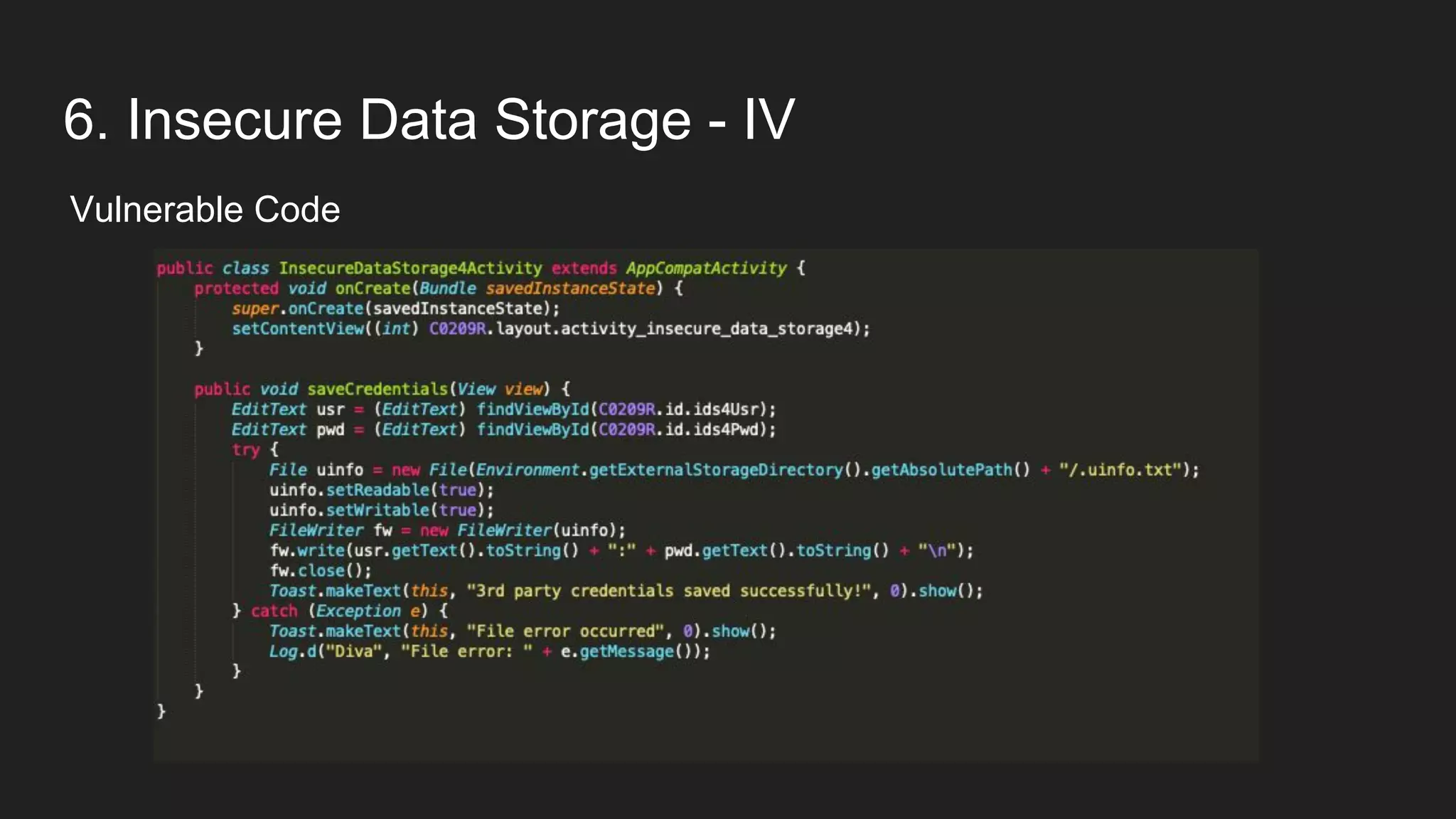
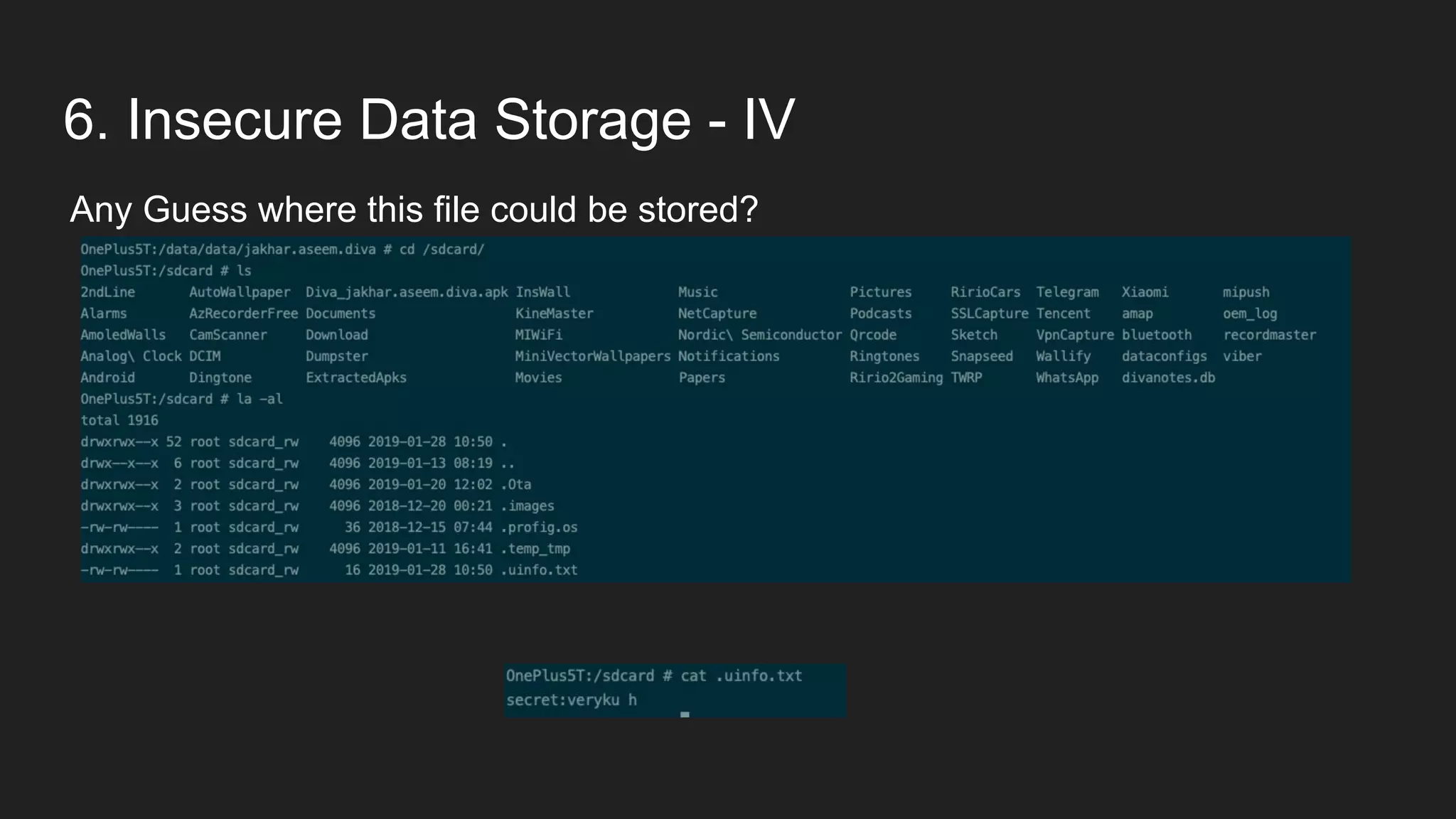
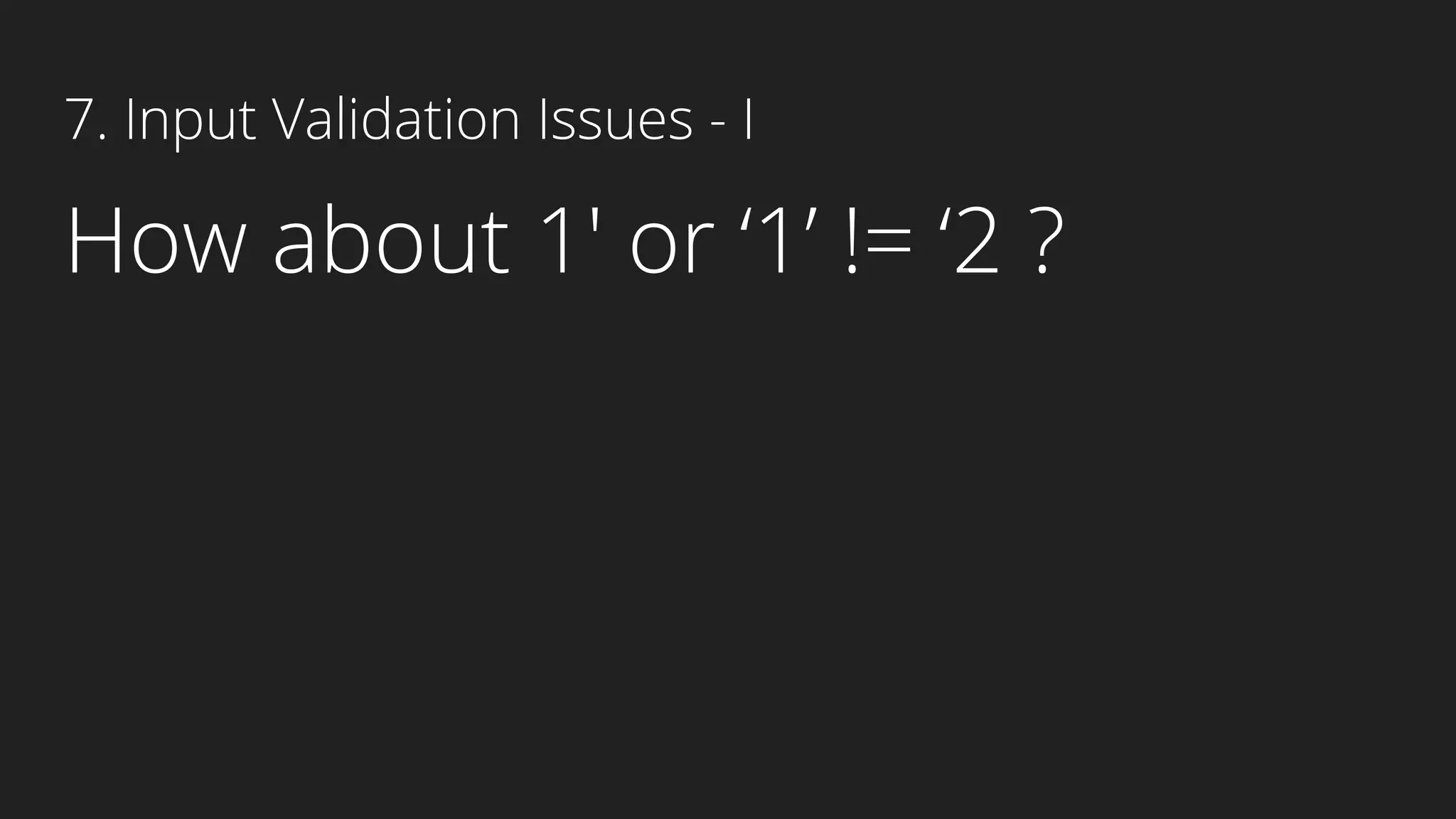
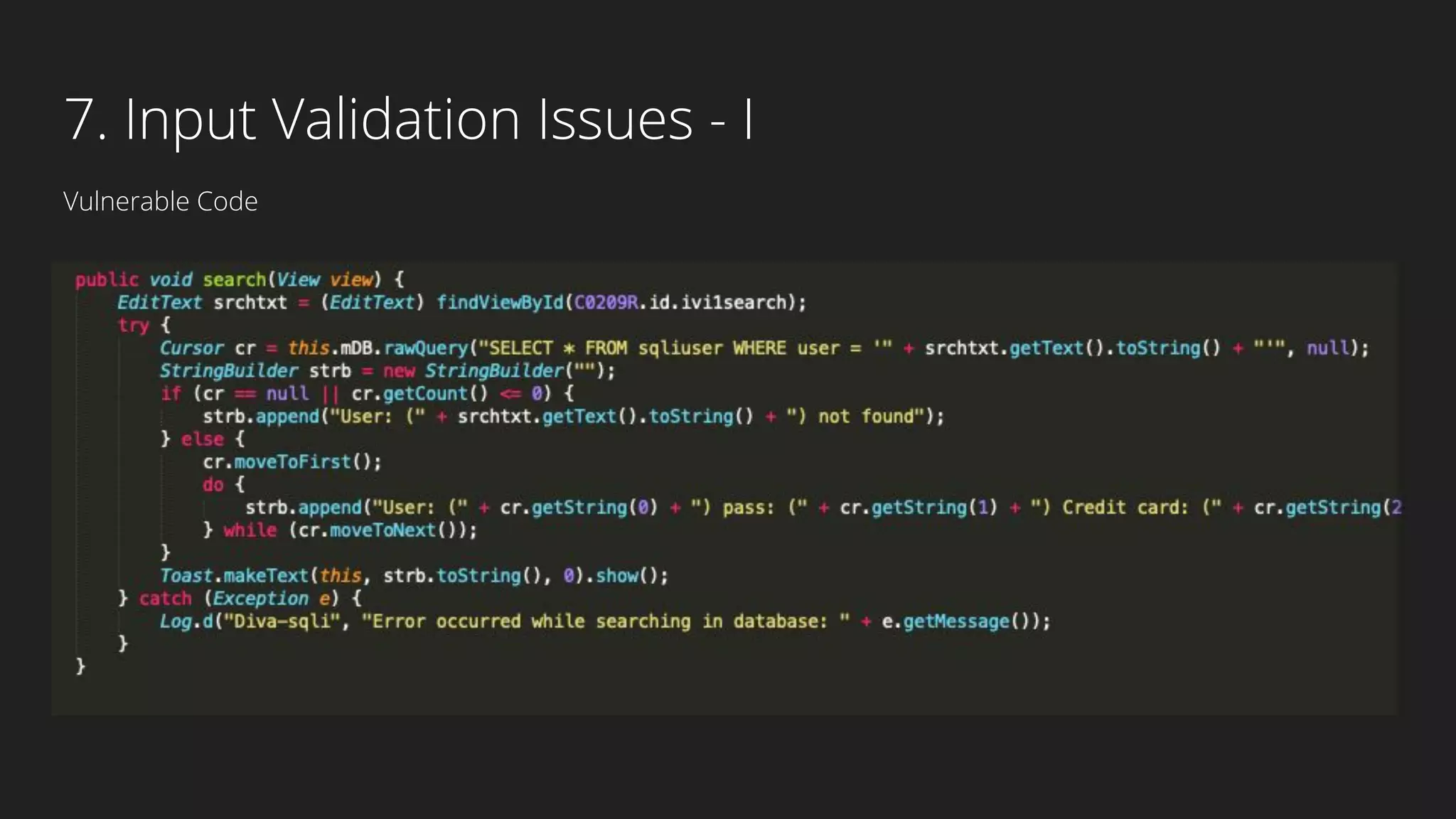
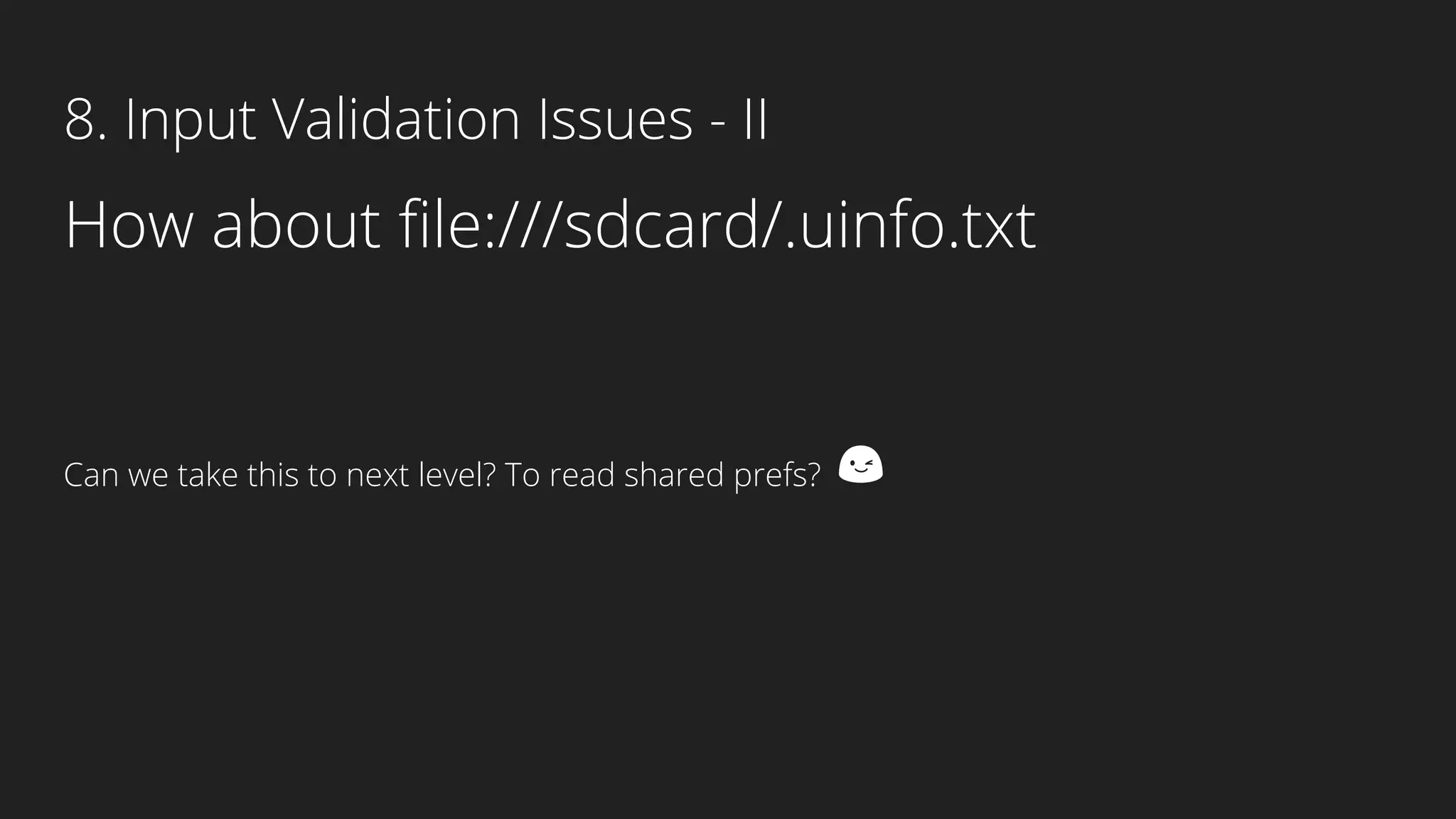
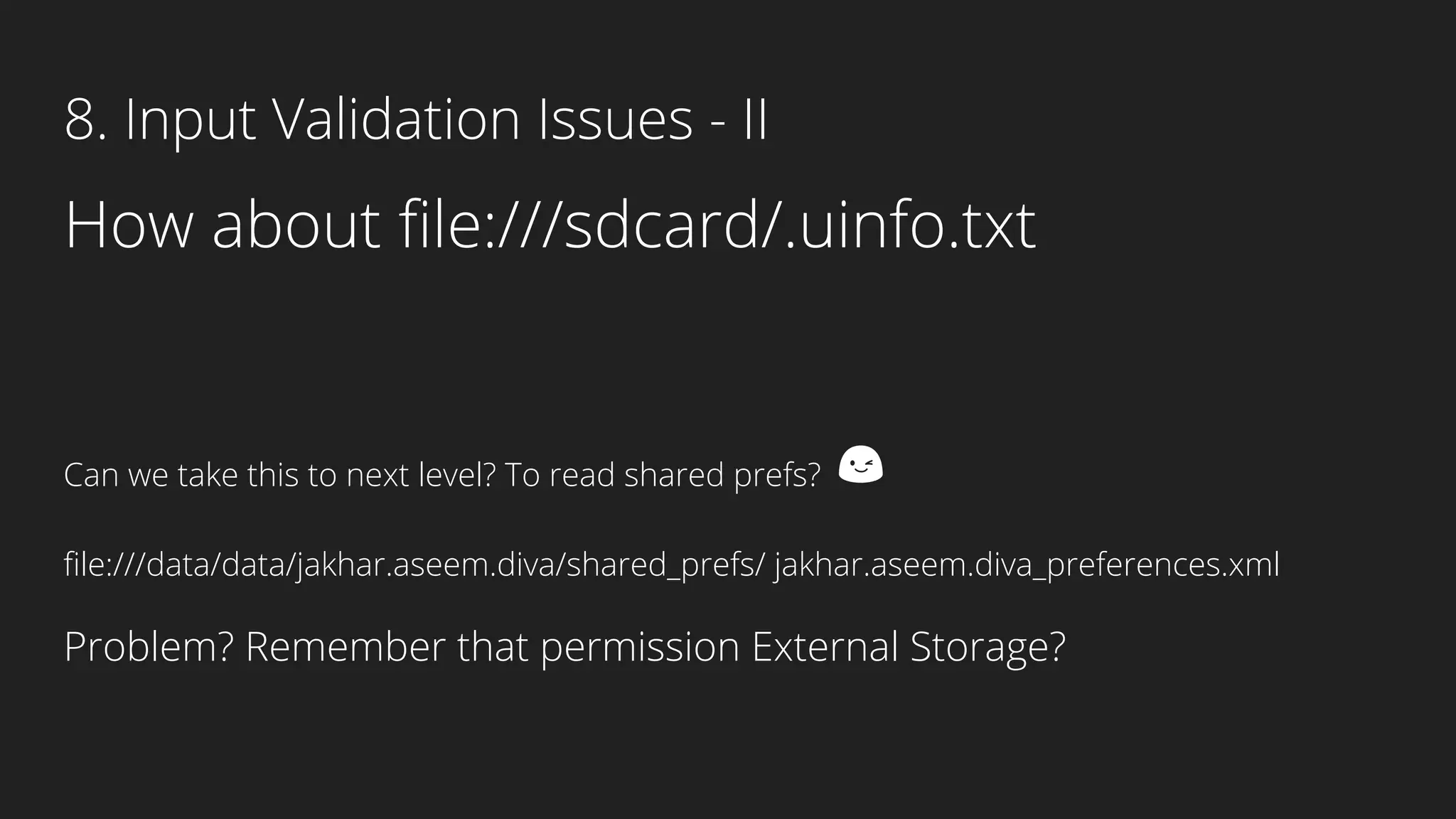
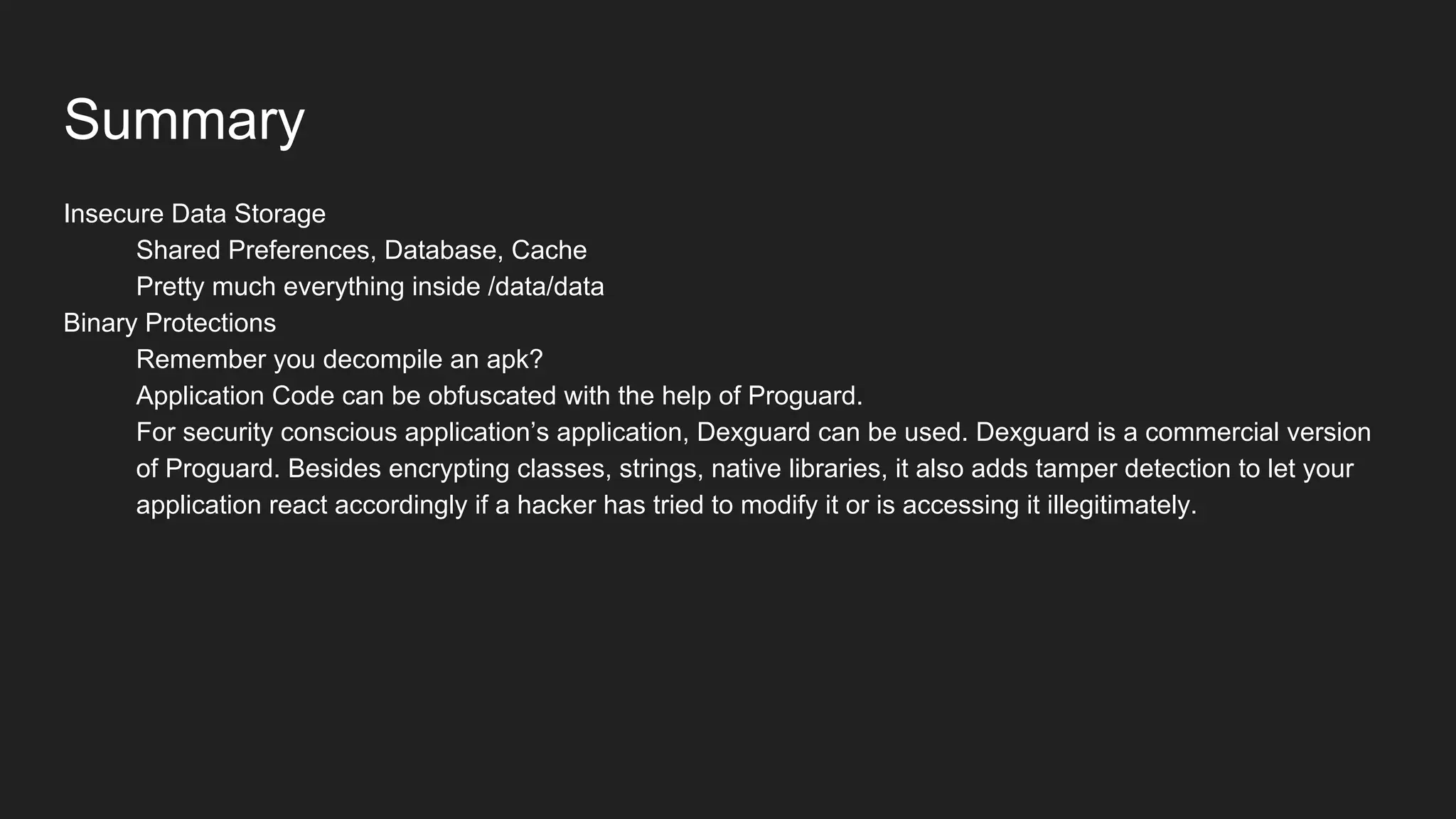
This document provides an overview of Android security and penetration testing. It discusses the Android runtime environment and application fundamentals. It then examines the contents of an Android APK file, including the AndroidManifest.xml and code files. The document outlines the Android sandbox security model and various tools for decompiling and analyzing APKs. It introduces the DIVA vulnerable Android app and demonstrates several common security issues like insecure data storage, input validation problems, and ways to capture network traffic.