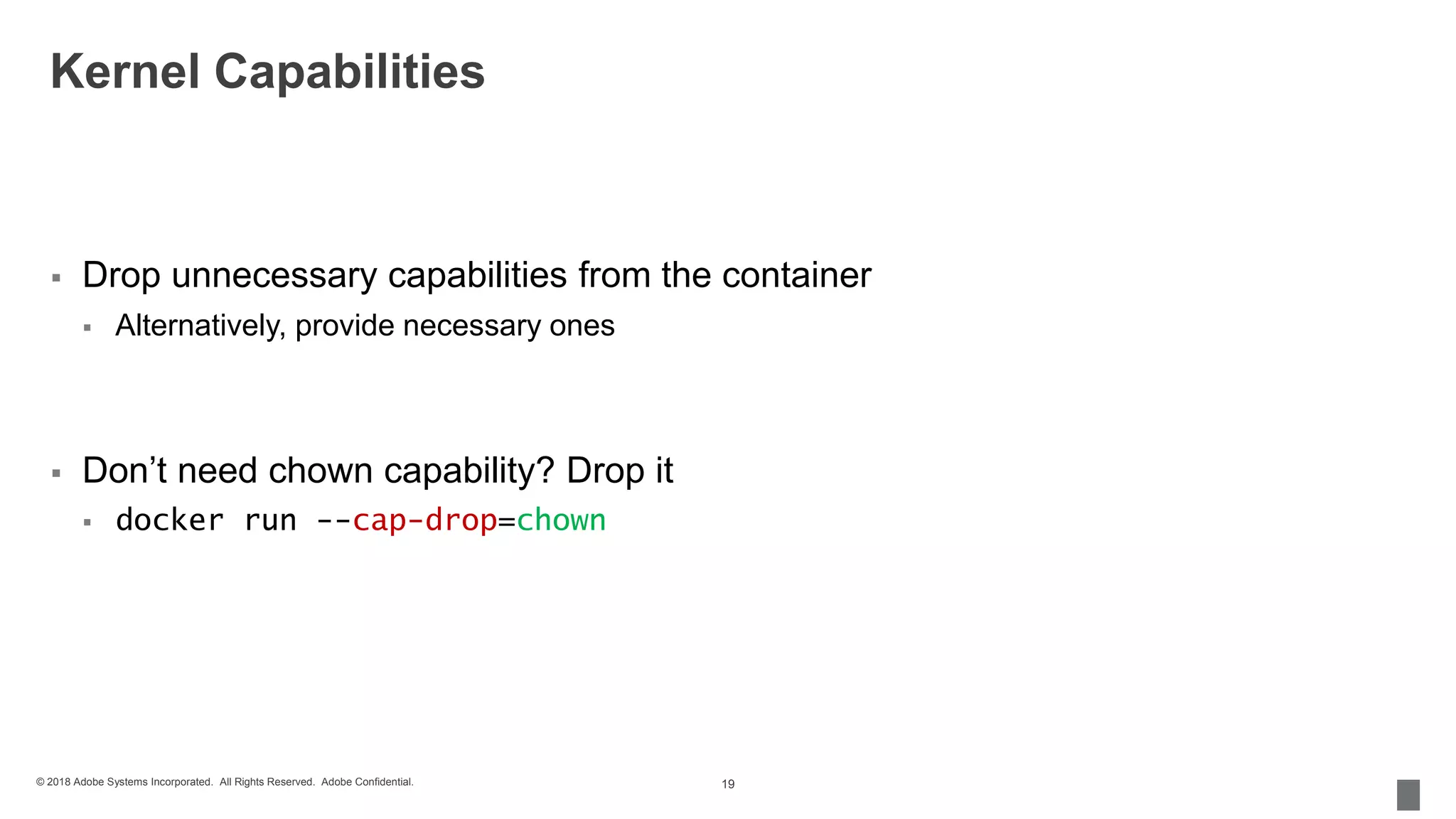
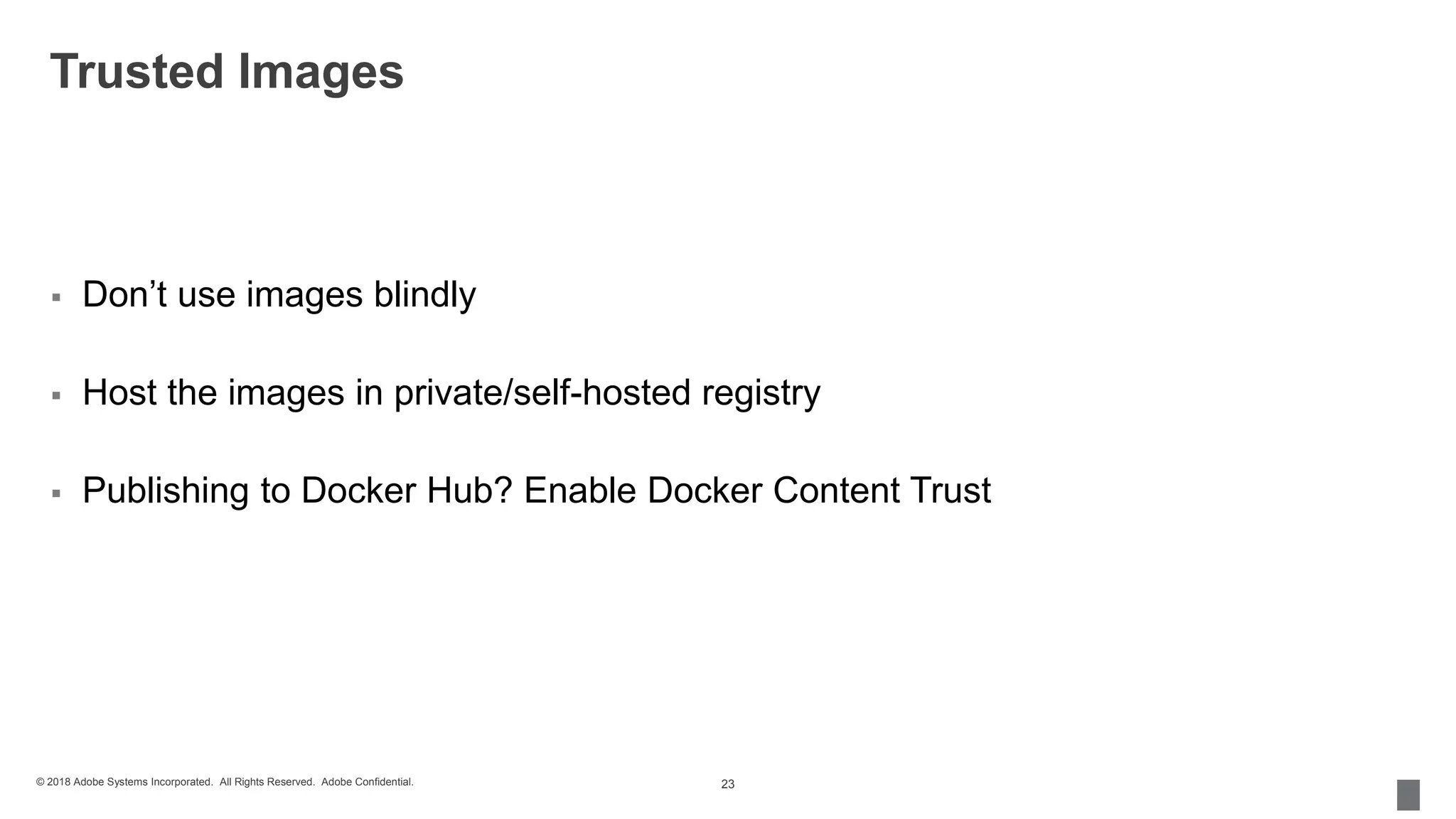
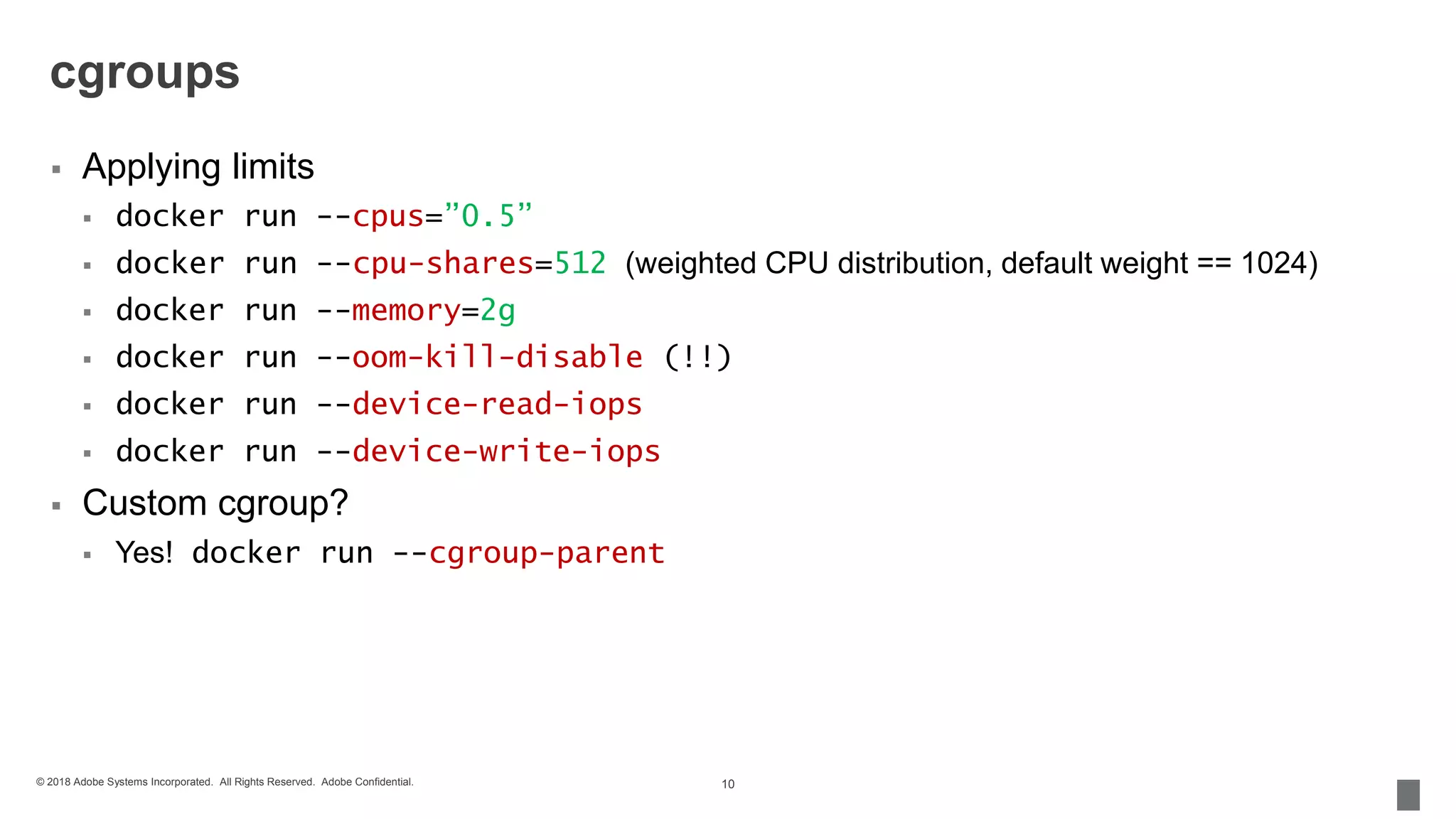
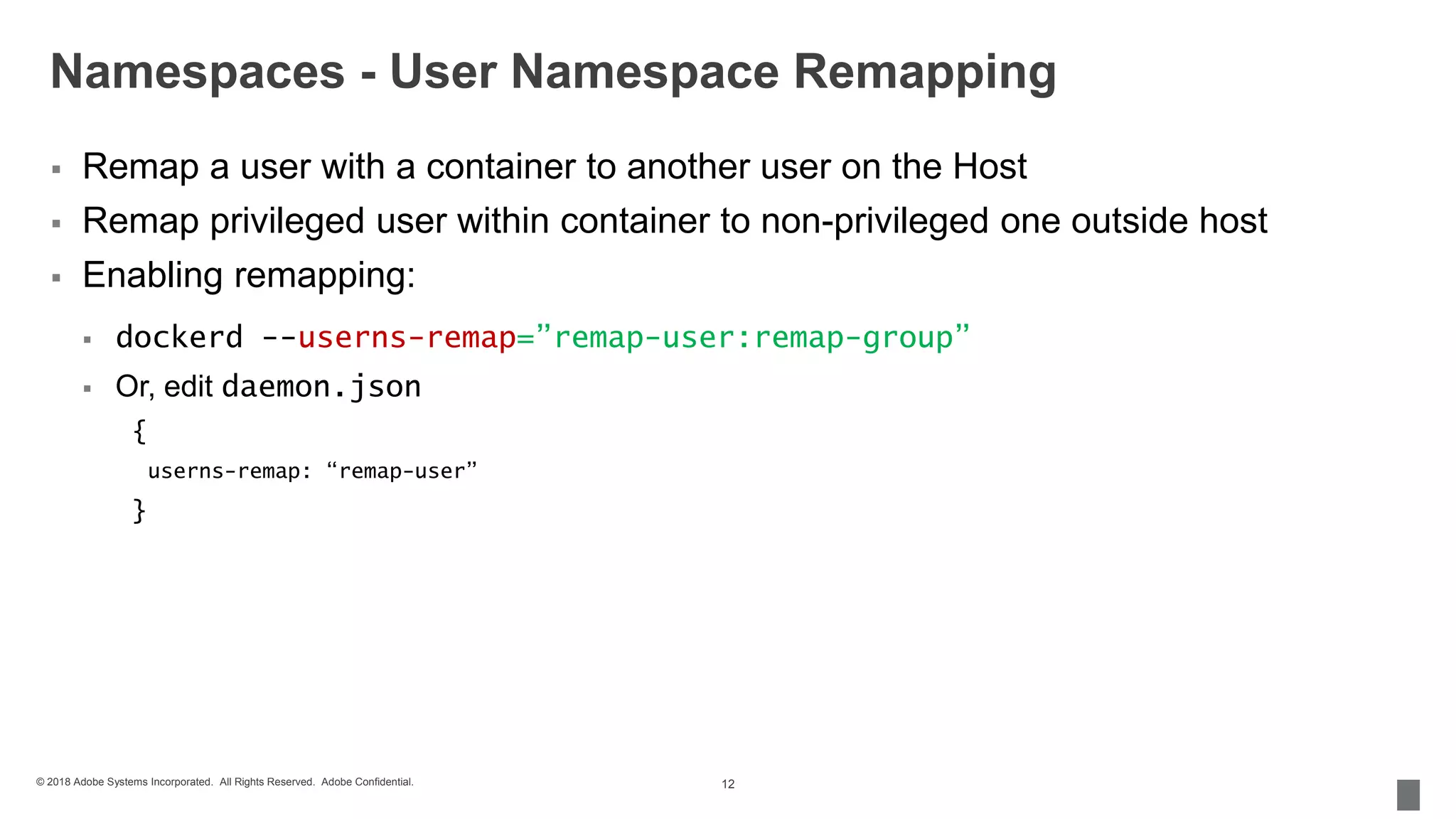
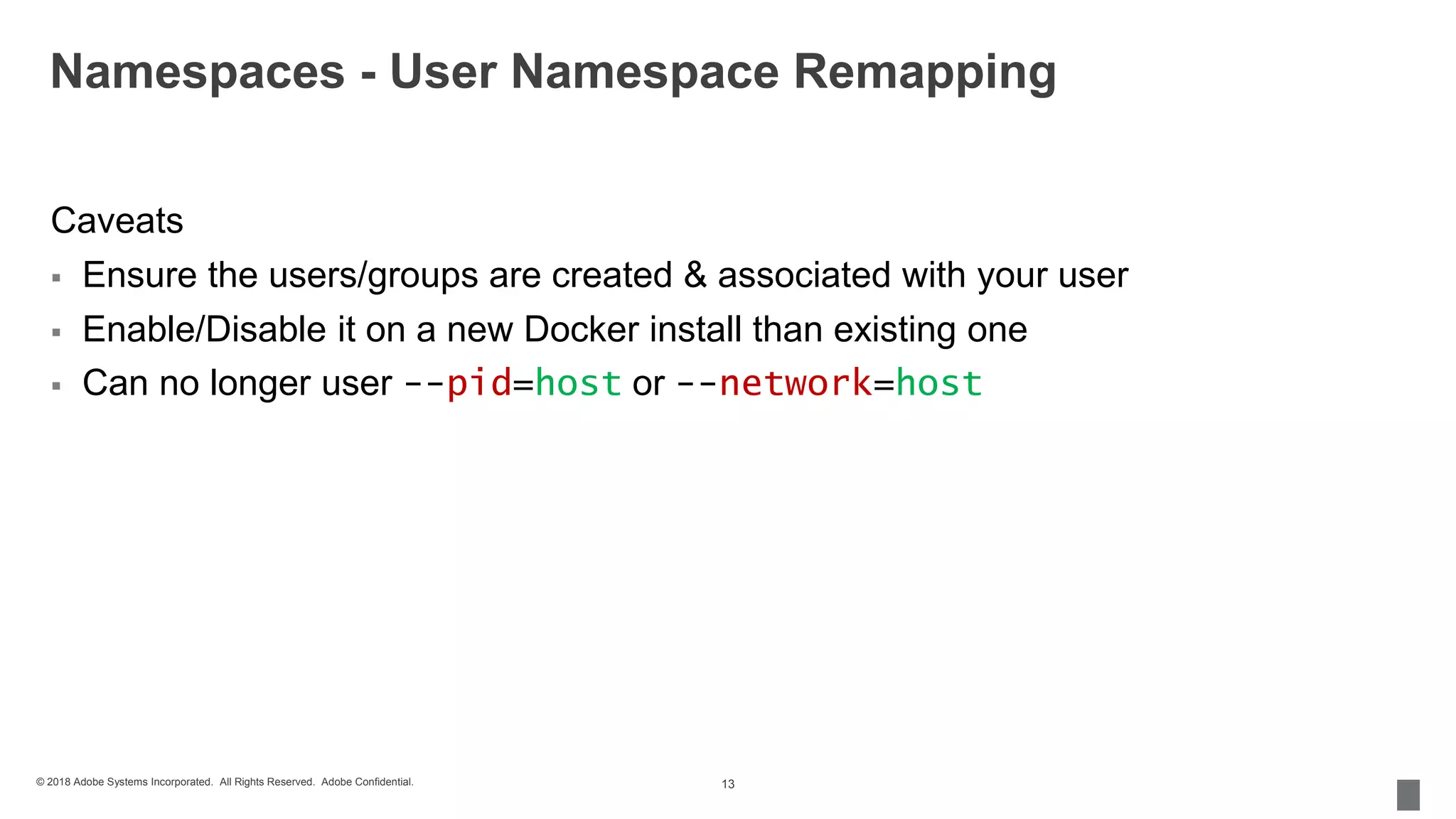
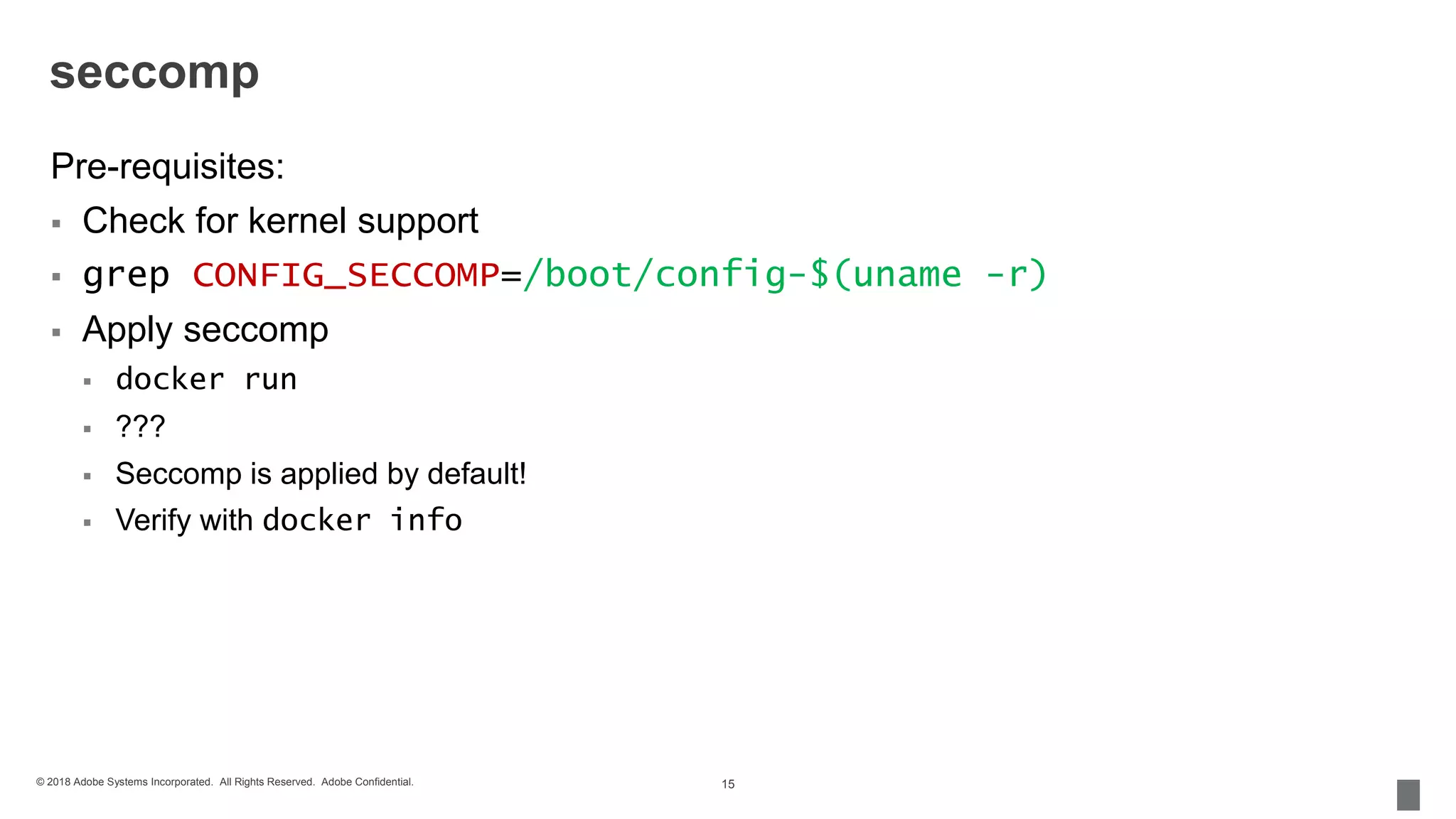
The document discusses security measures for containerization in Docker, detailing mechanisms like control groups (cgroups), namespaces, and seccomp for limiting resource utilization and access. It emphasizes the importance of managing vulnerabilities in images and using trusted images, including the implementation of Docker Content Trust. Additionally, it covers the necessity of using tools like vulnerability scanners to ensure application security.







![© 2018 Adobe Systems Incorporated. All Rights Reserved. Adobe Confidential.
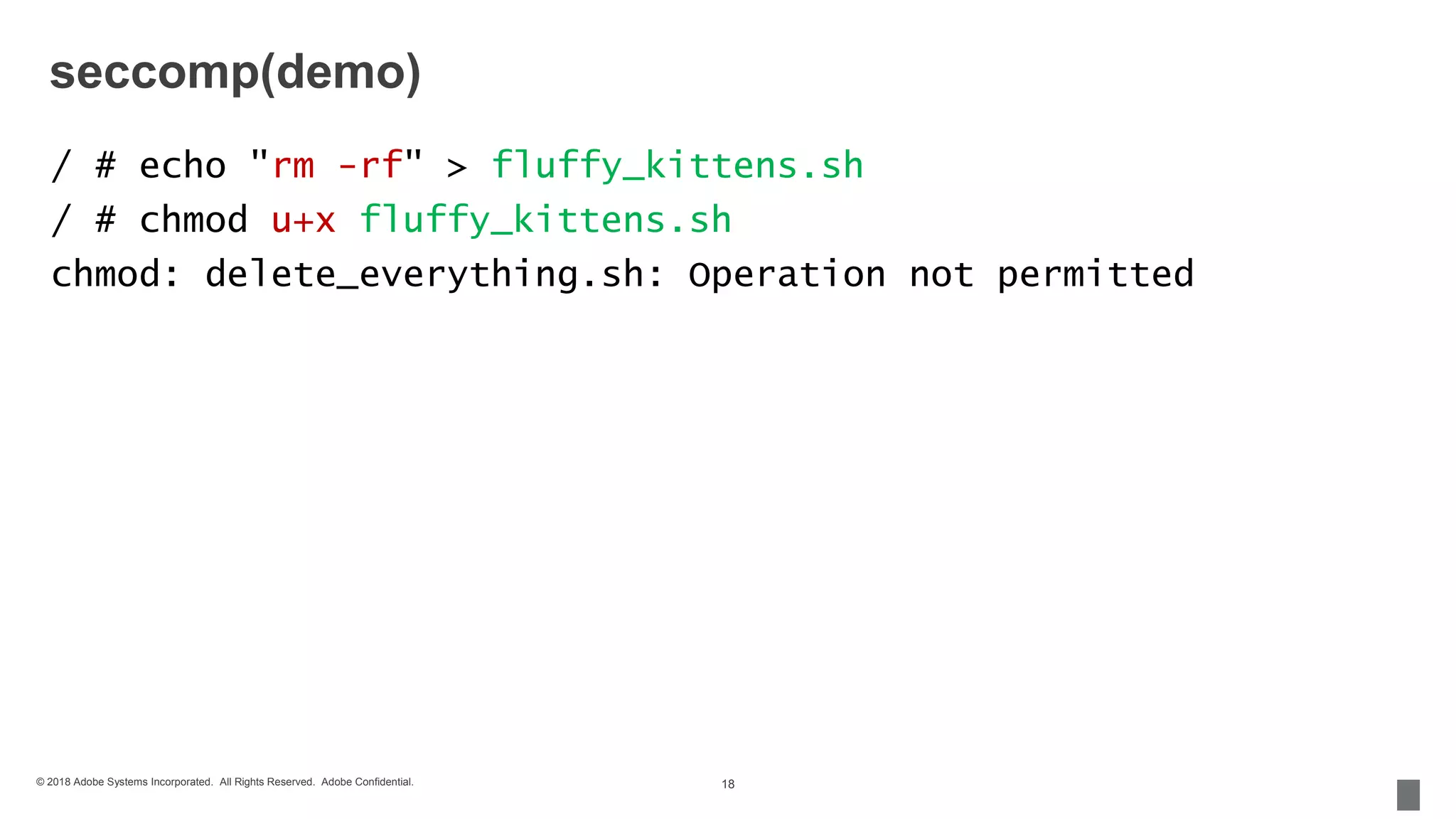
seccomp(demo)
cat seccomp-profile.json
{
"defaultAction": "SCMP_ACT_ALLOW",
"syscalls": [
{
"name": "chown",
"action": "SCMP_ACT_ERRNO"
},
{
"name": "chmod",
"action": "SCMP_ACT_ERRNO"
}
]
}
17](https://image.slidesharecdn.com/securingcontainers-sathya-adobe-180611050600/75/Securing-Containers-Sathyajit-Bhat-Adobe-17-2048.jpg)