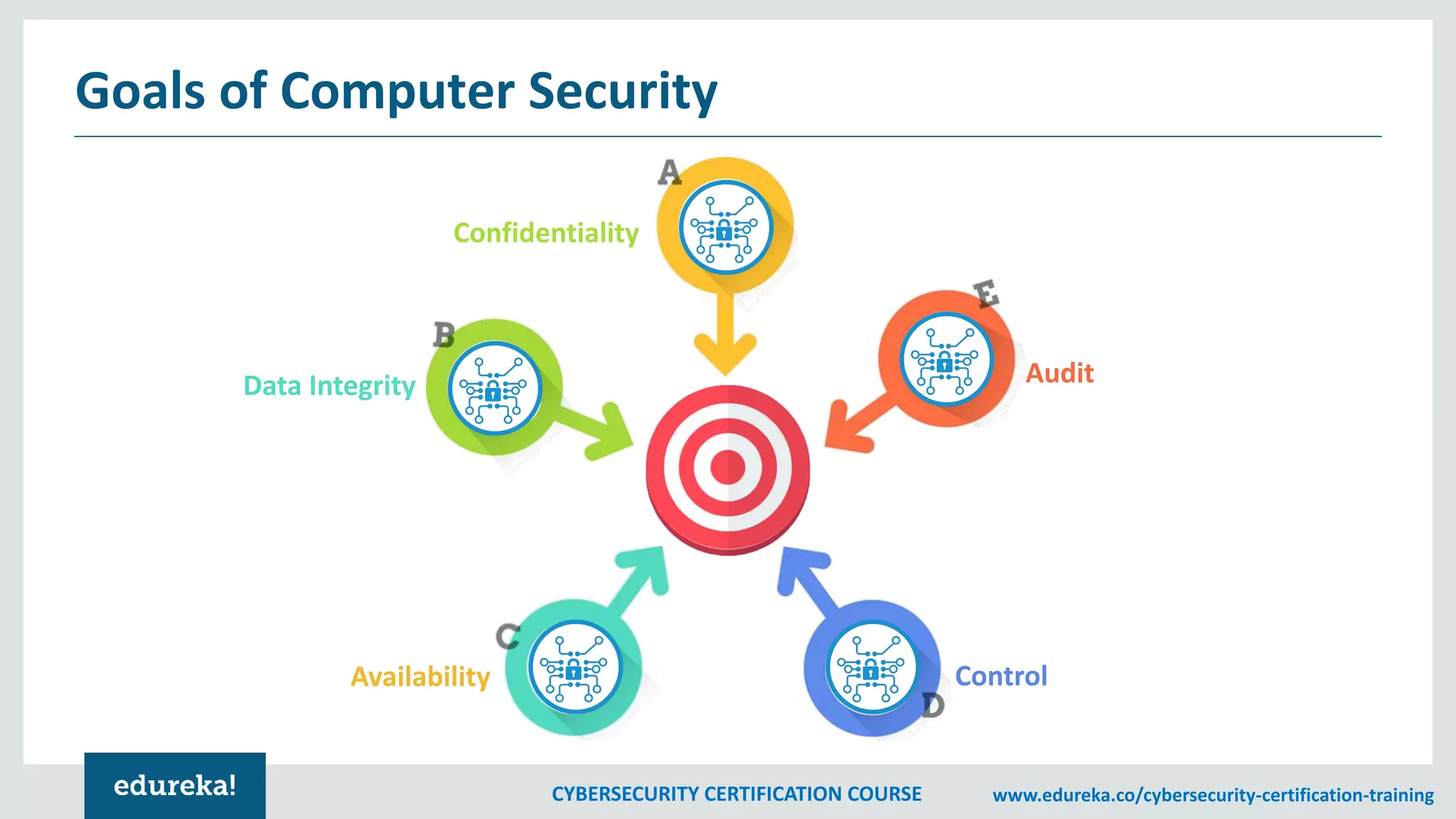
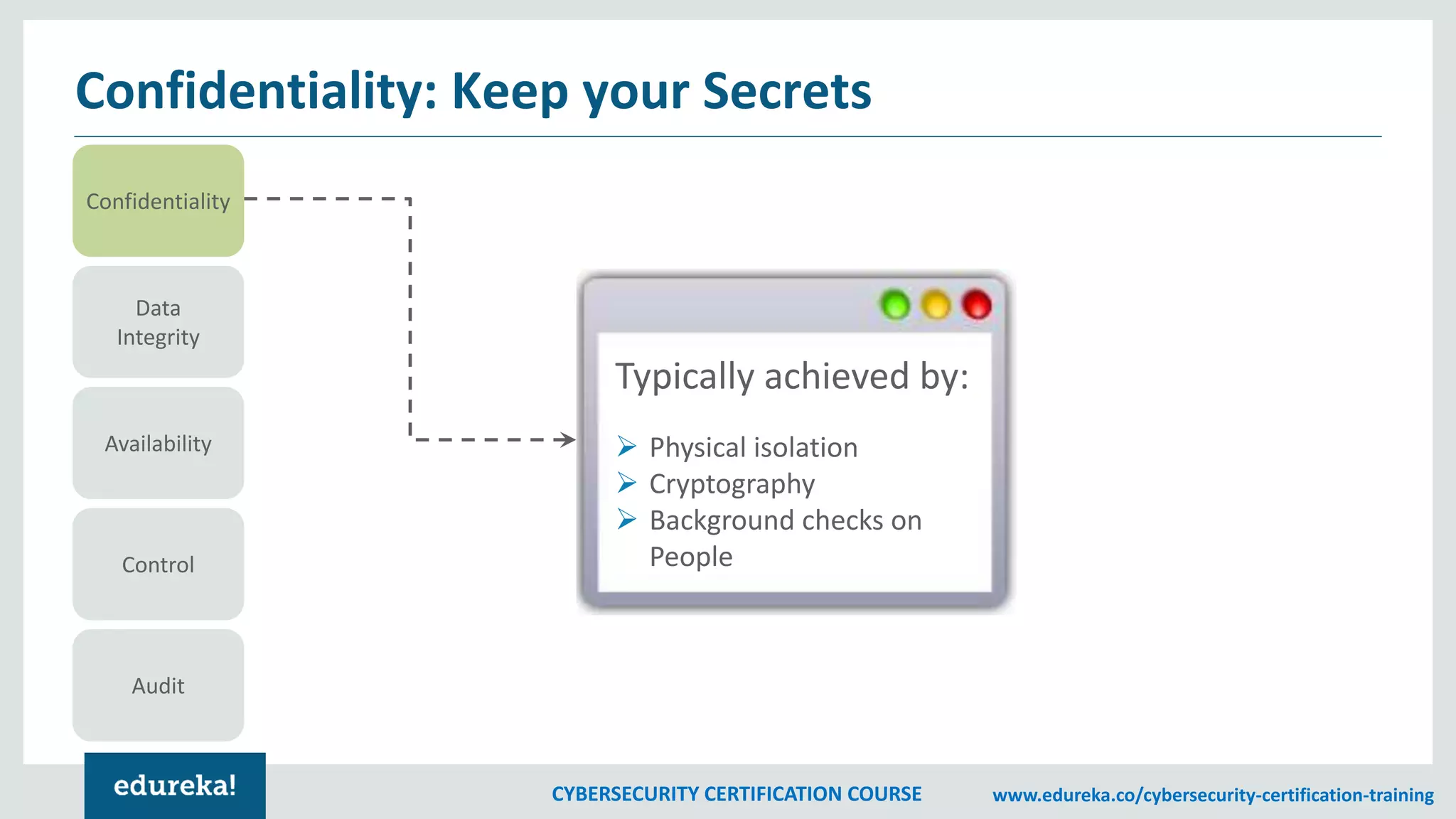
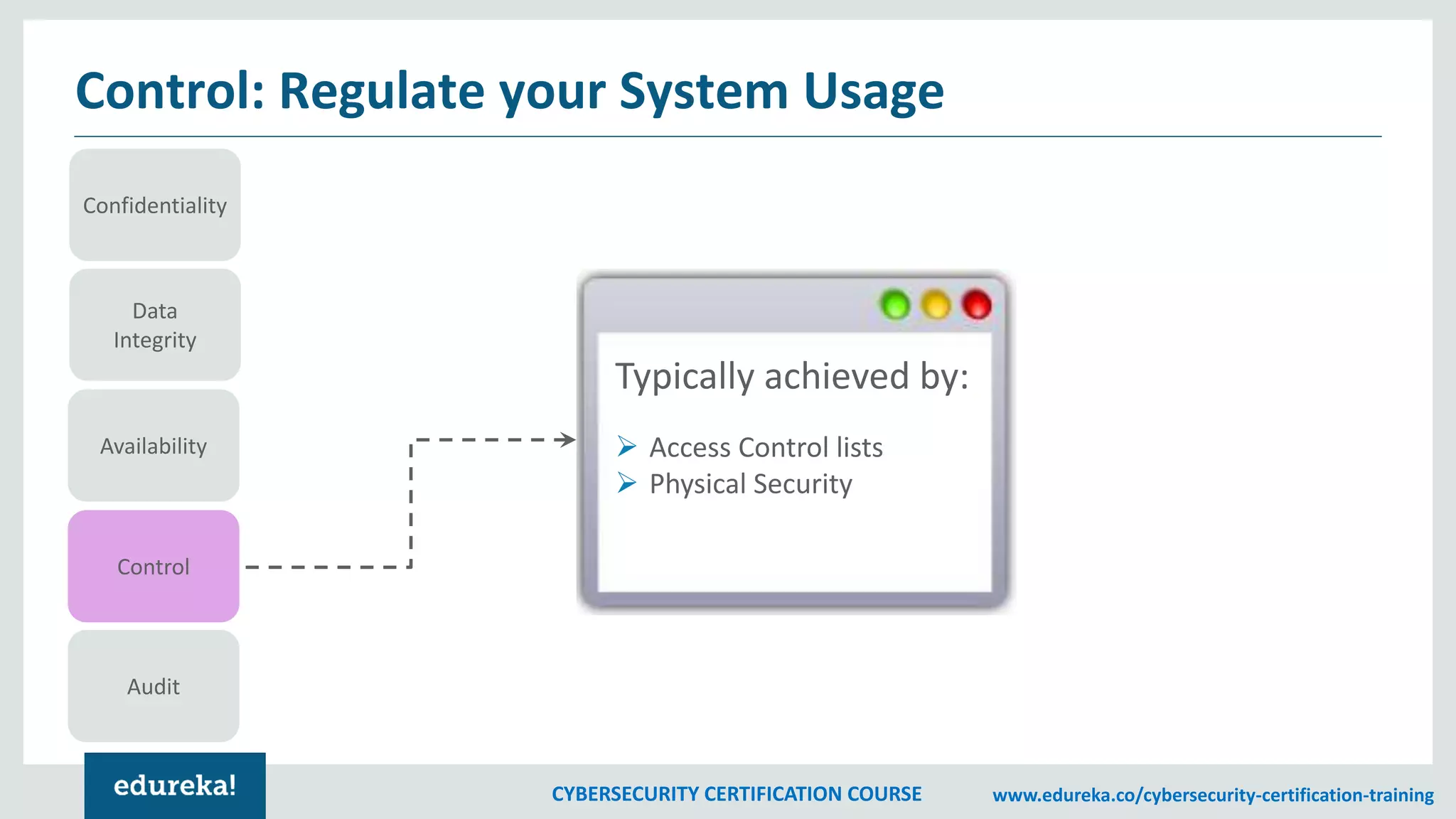
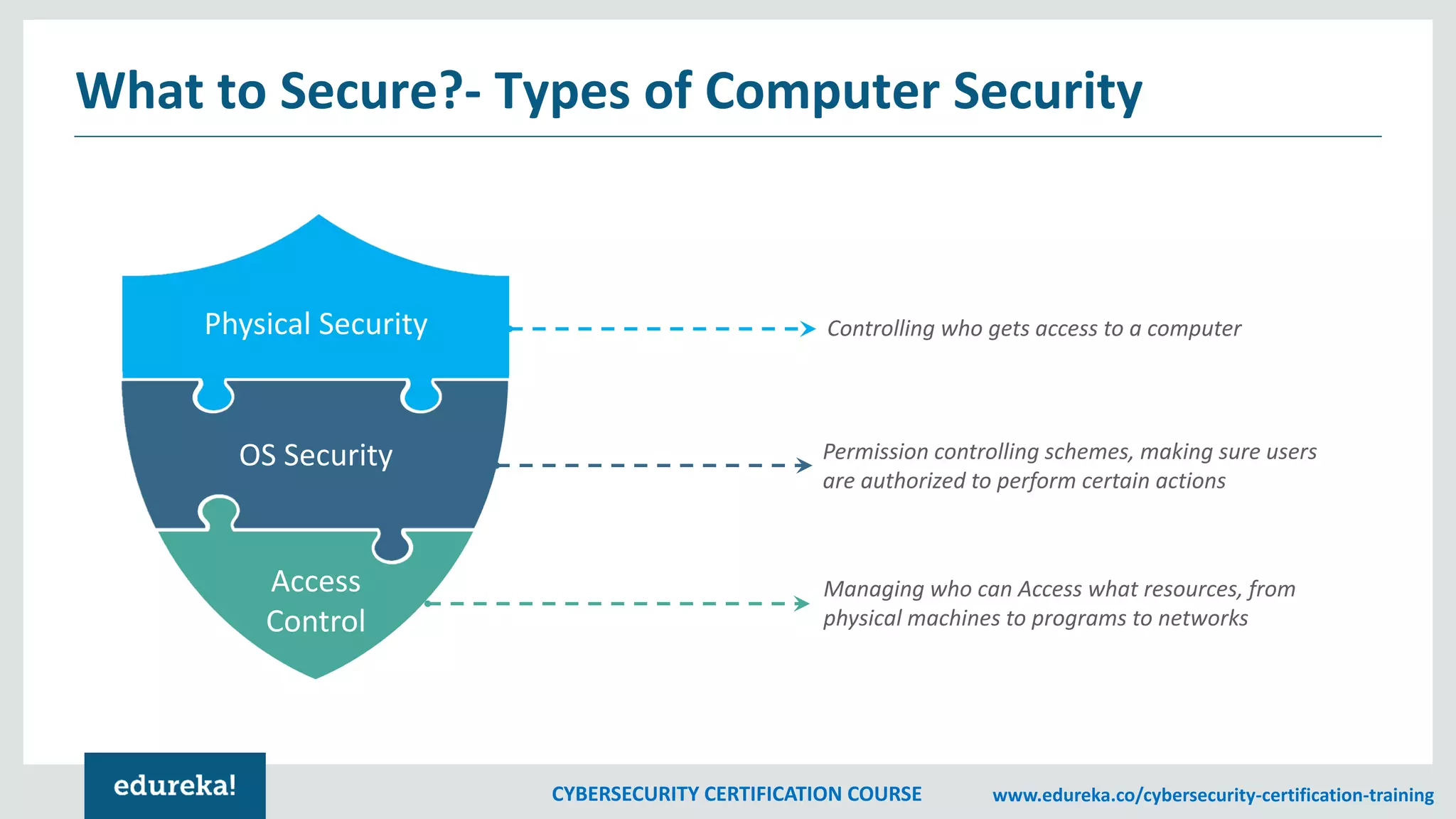
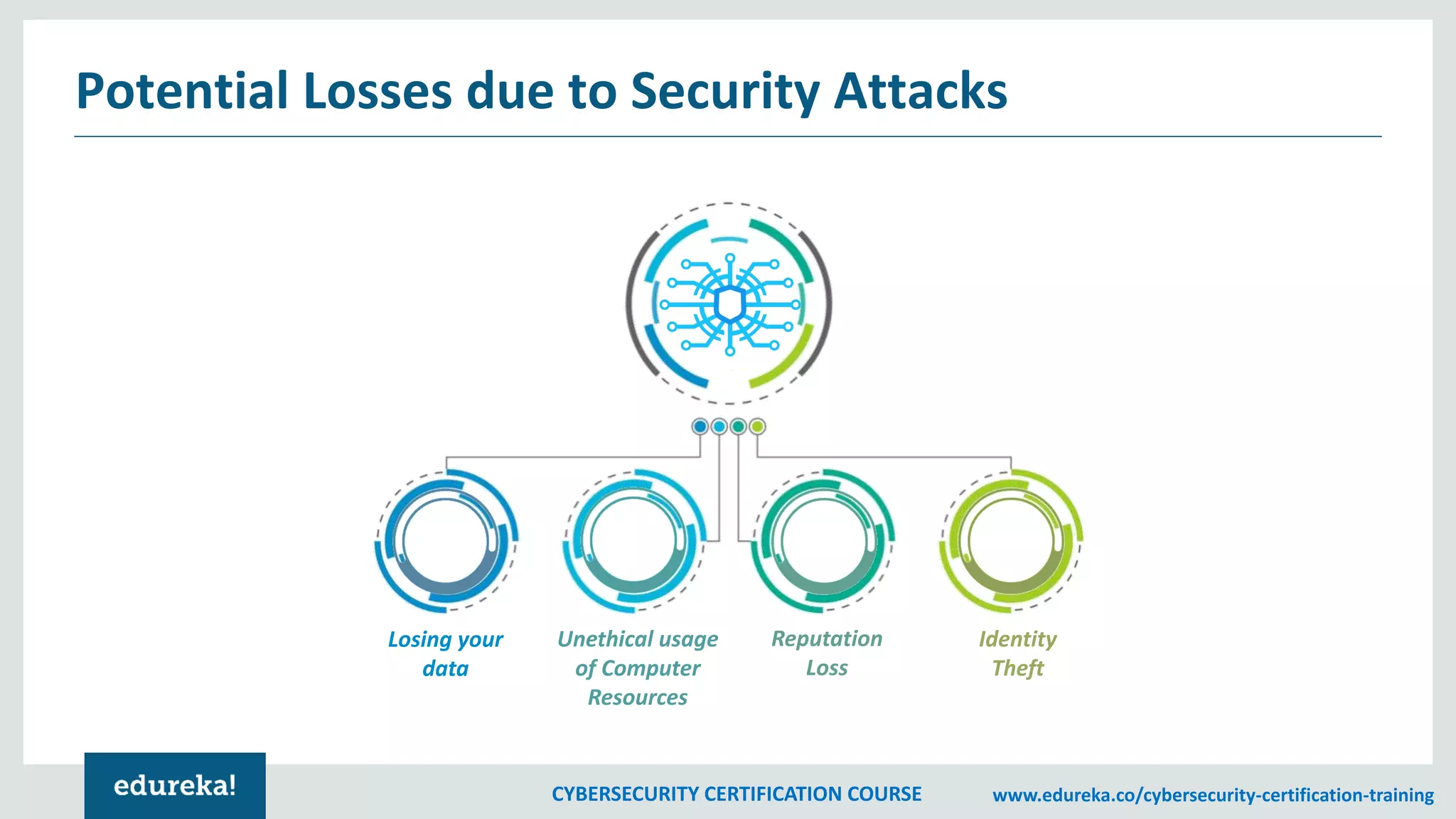
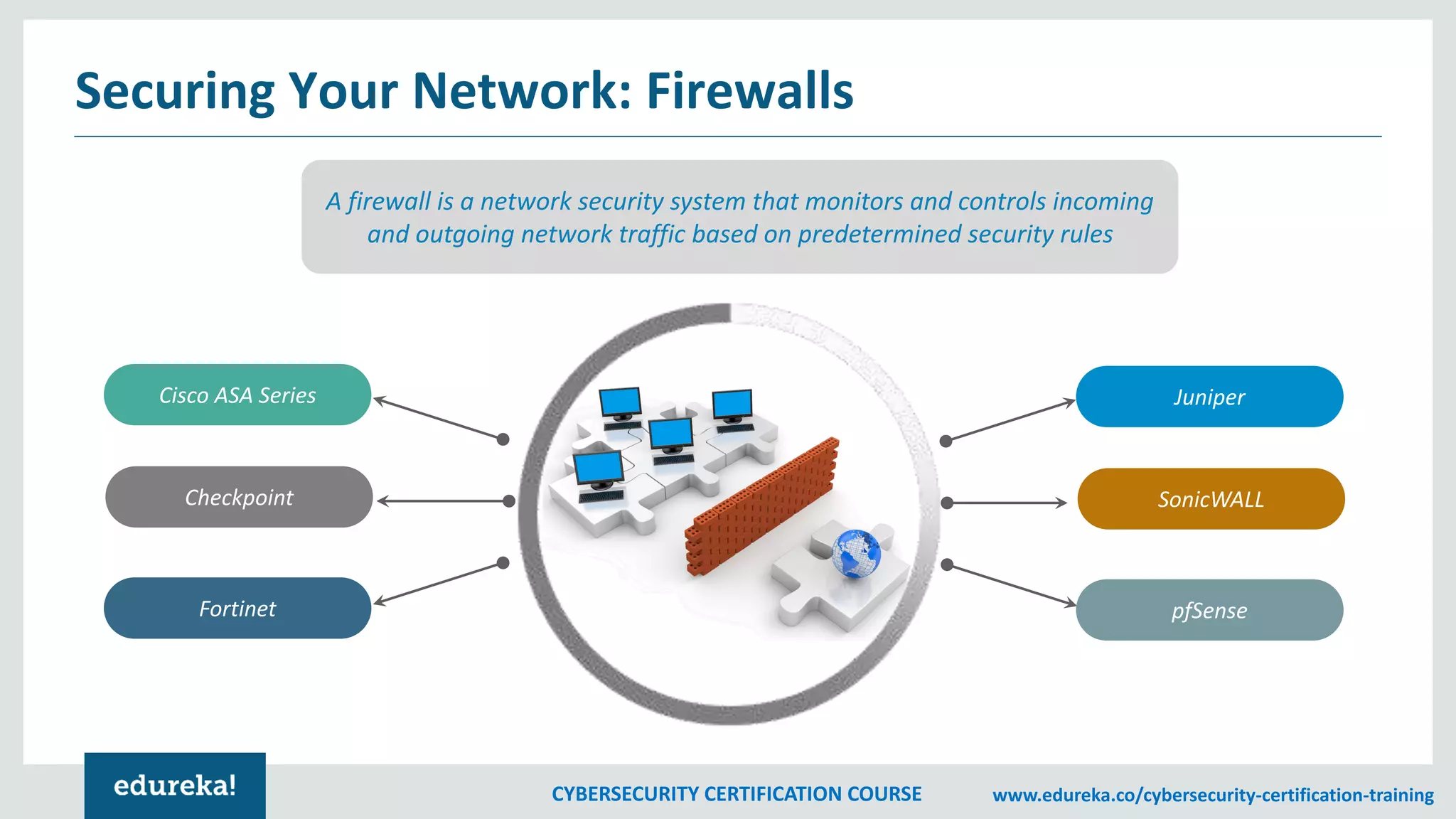
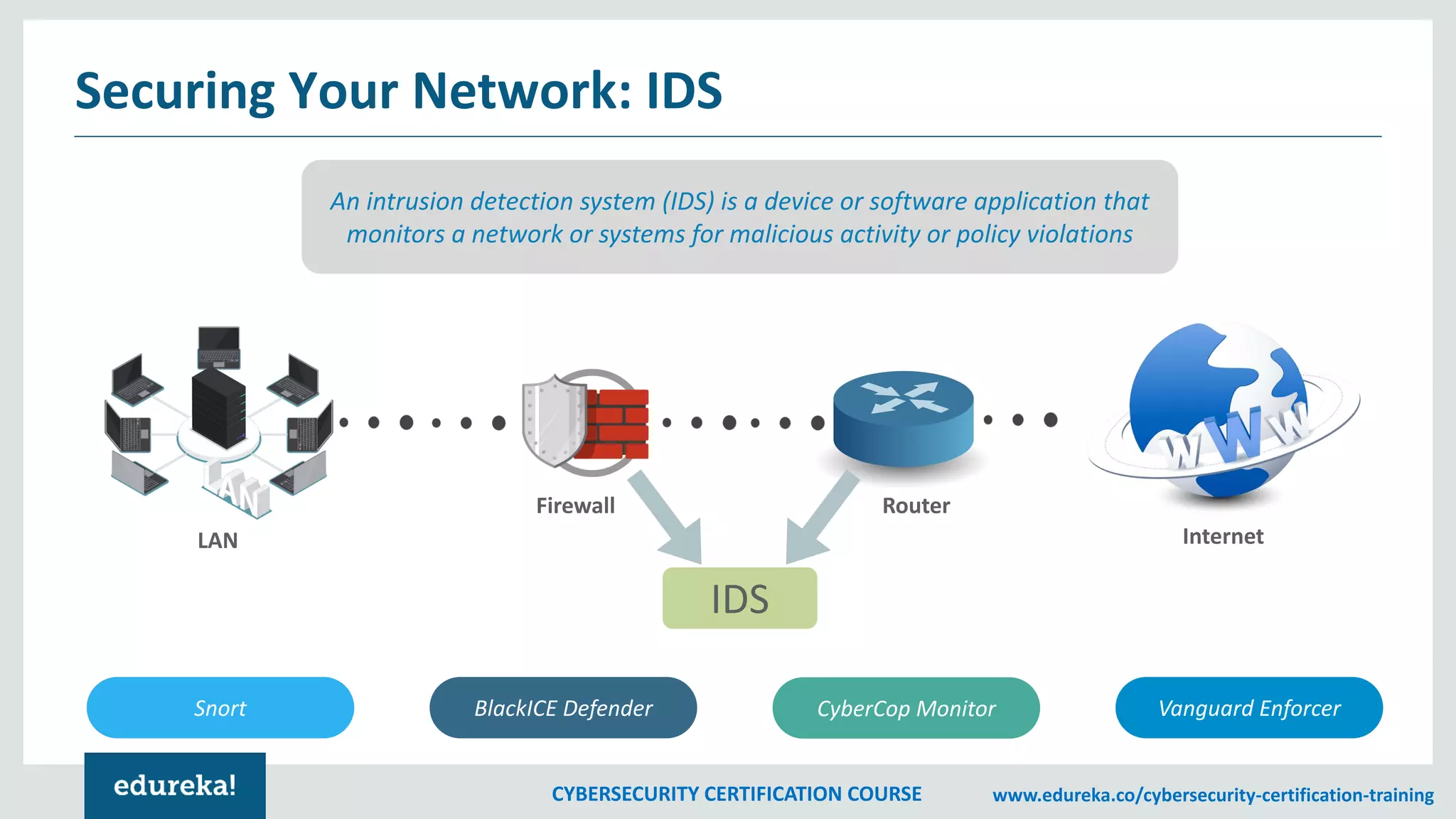
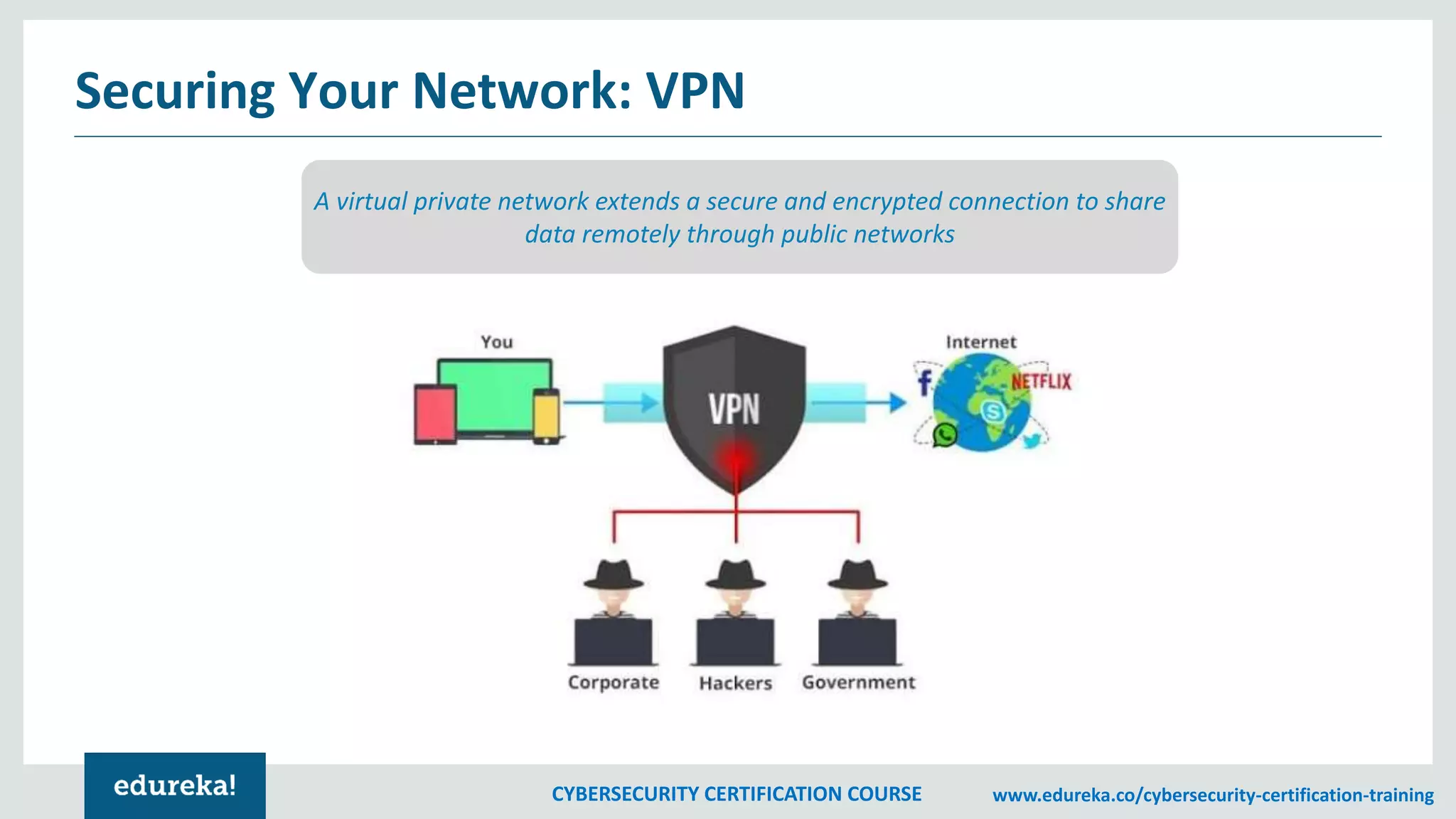
The document outlines a cybersecurity certification course, detailing various aspects of computer security including confidentiality, data integrity, and availability. It emphasizes the importance of securing systems and networks through methods such as antivirus software, firewalls, and physical security measures. Potential losses from security attacks and best practices for maintaining security, such as keeping software updated and regular backups, are also discussed.