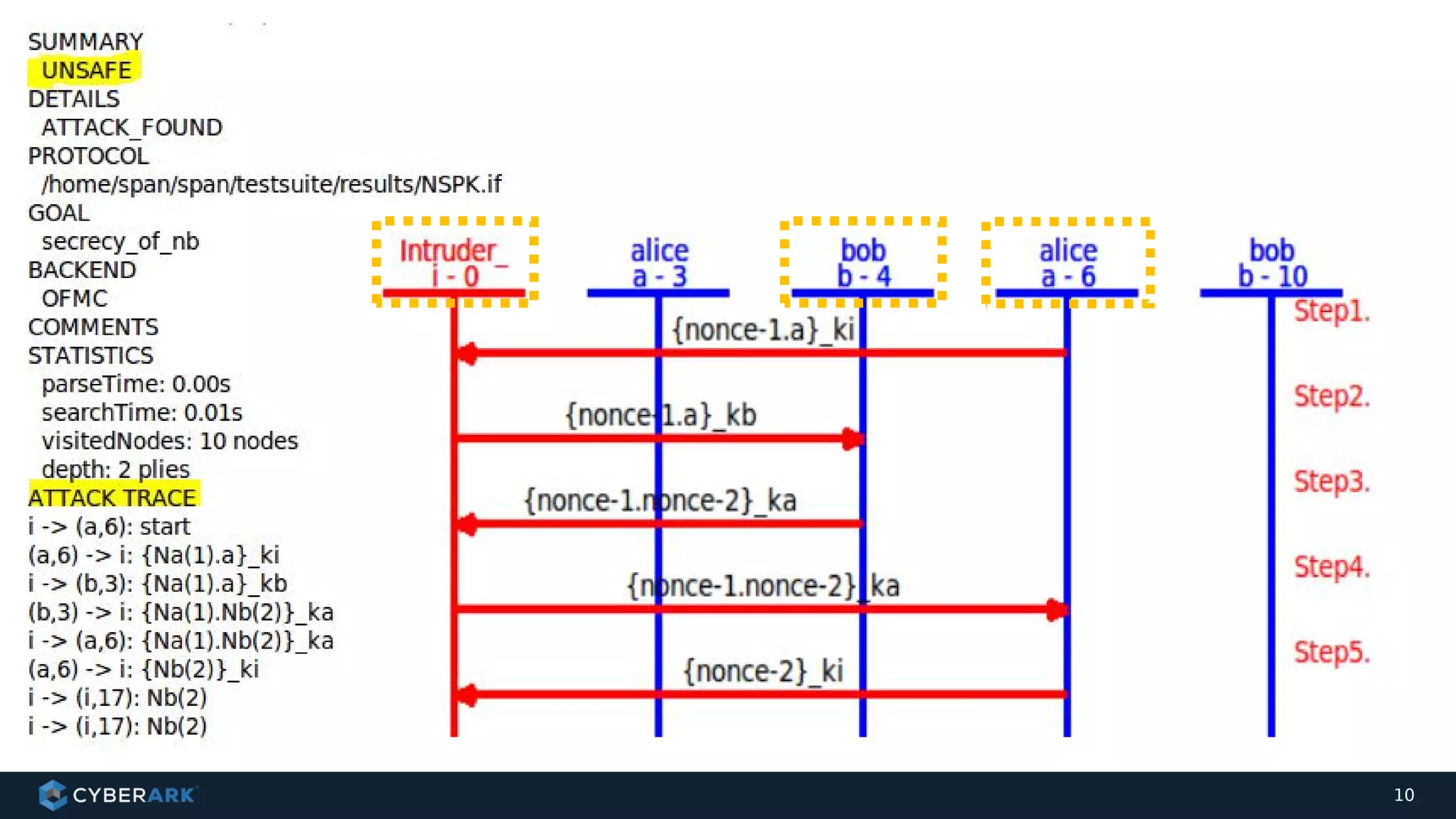
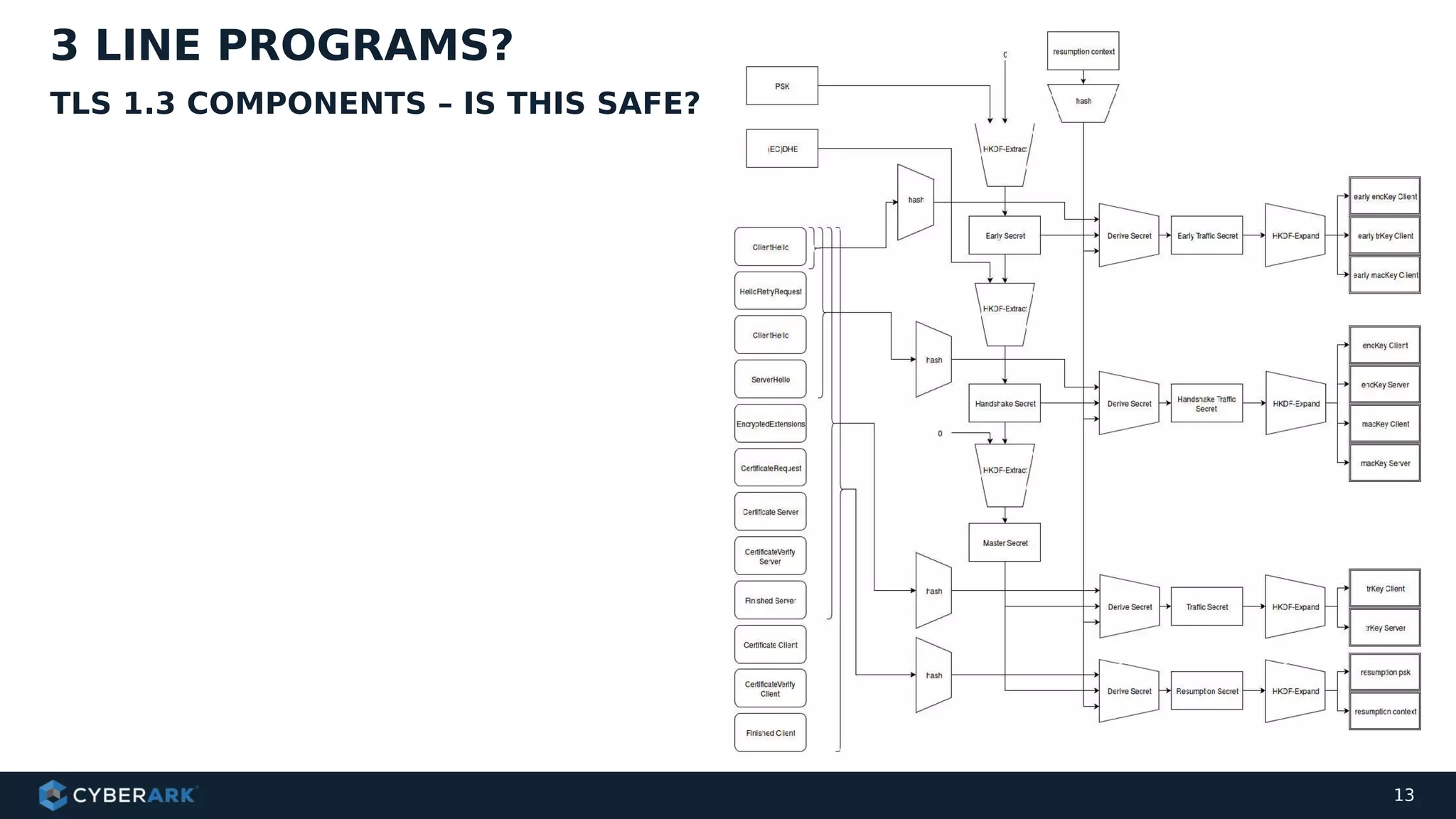
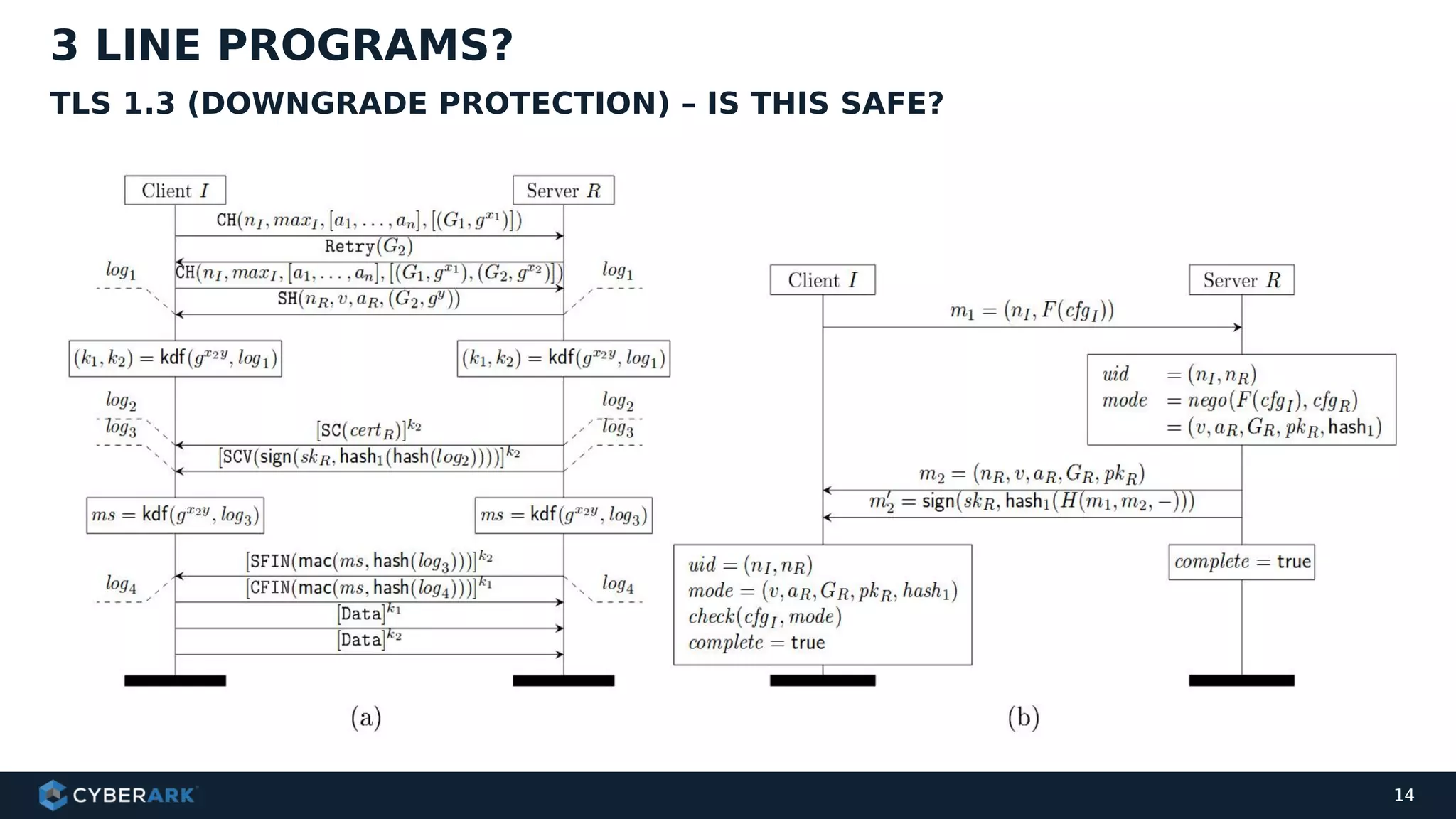
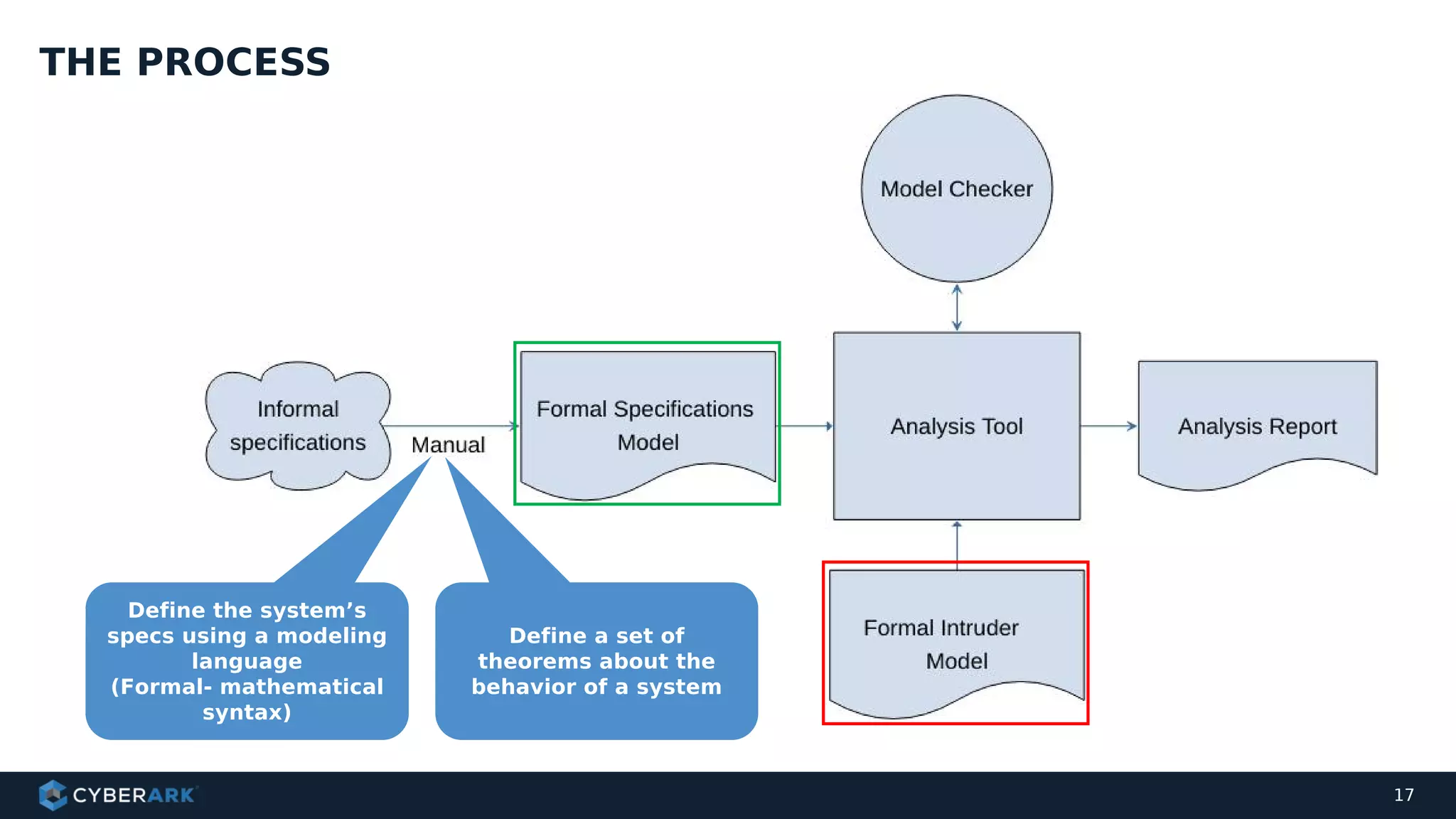
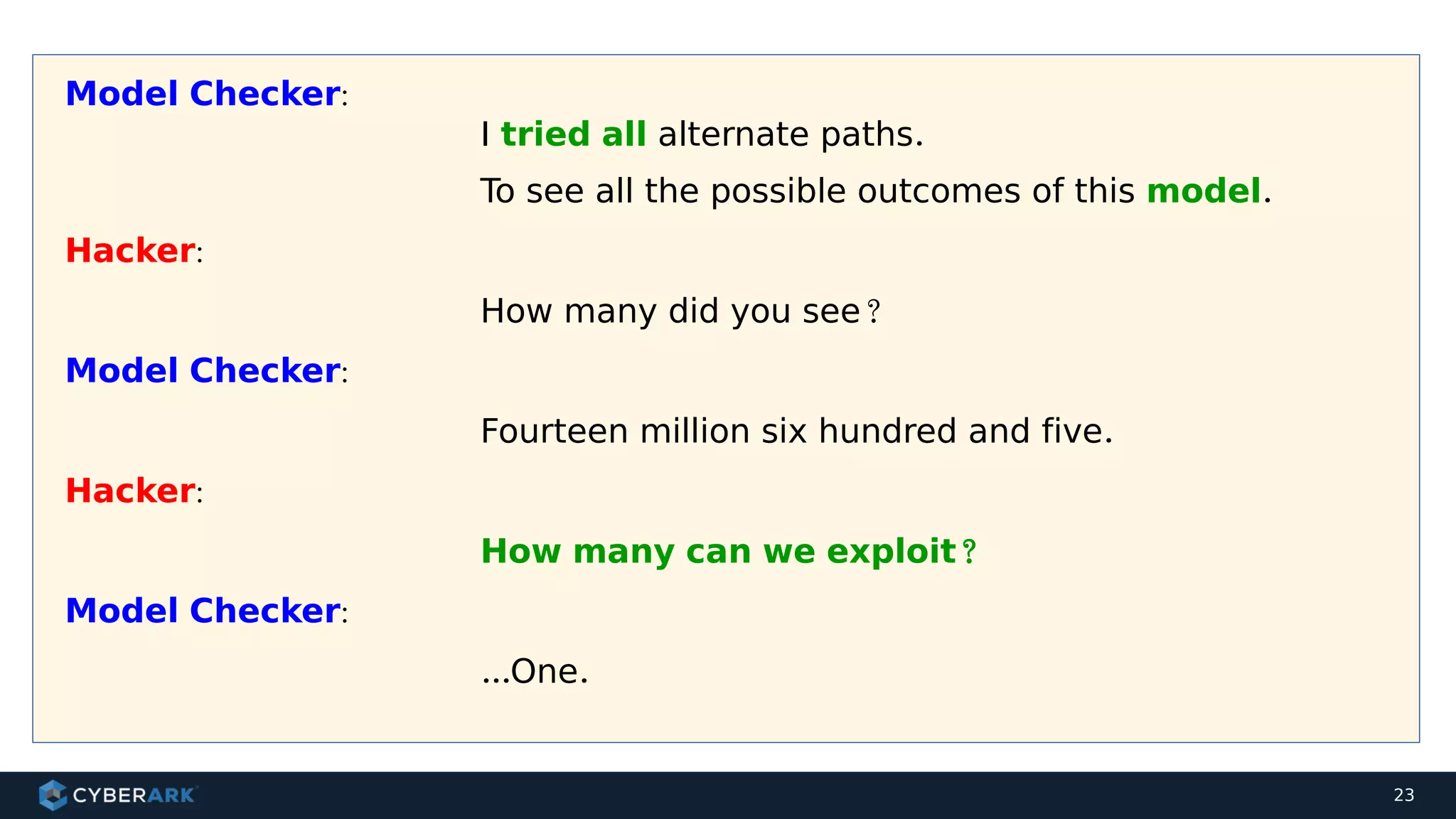
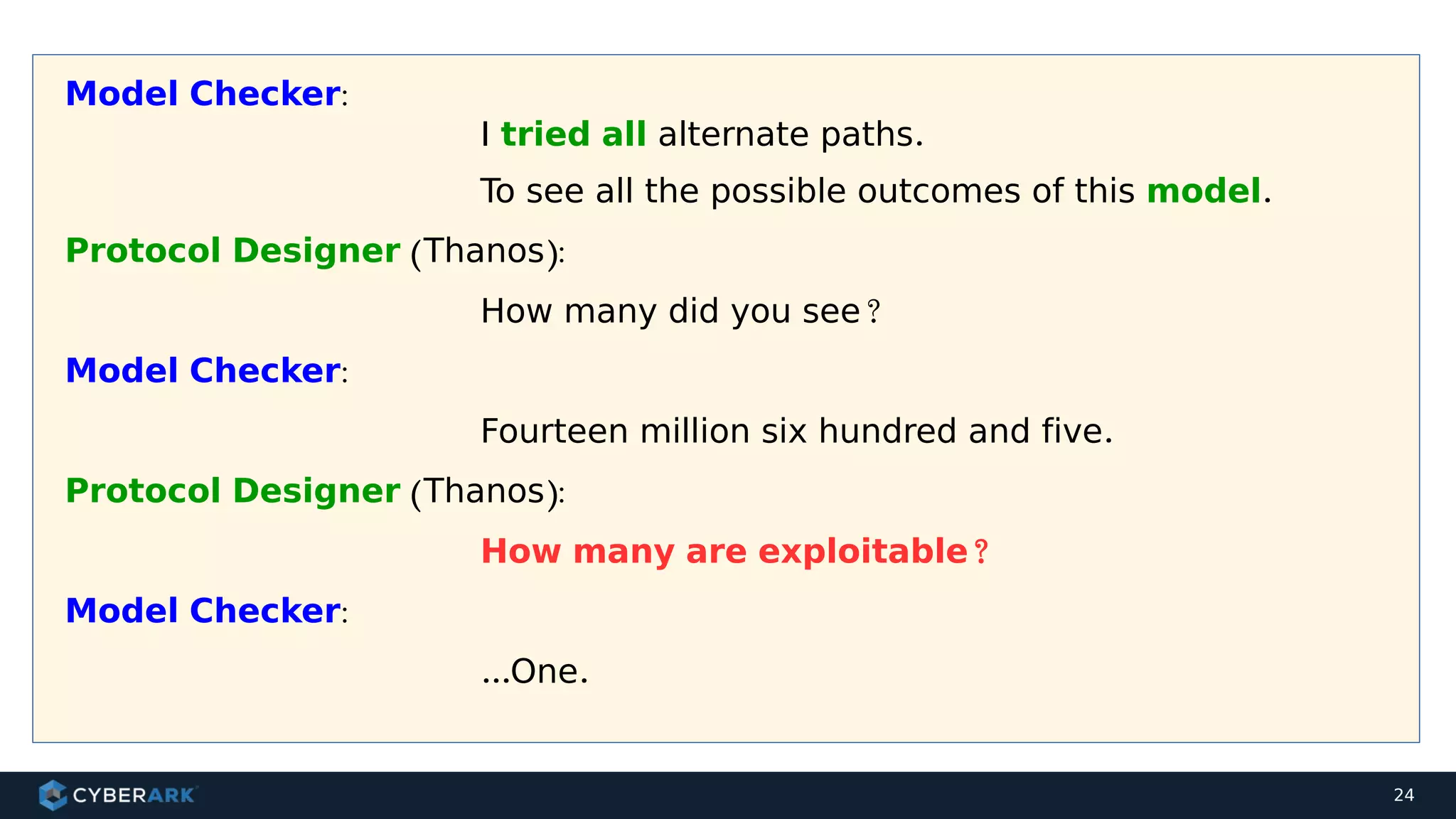
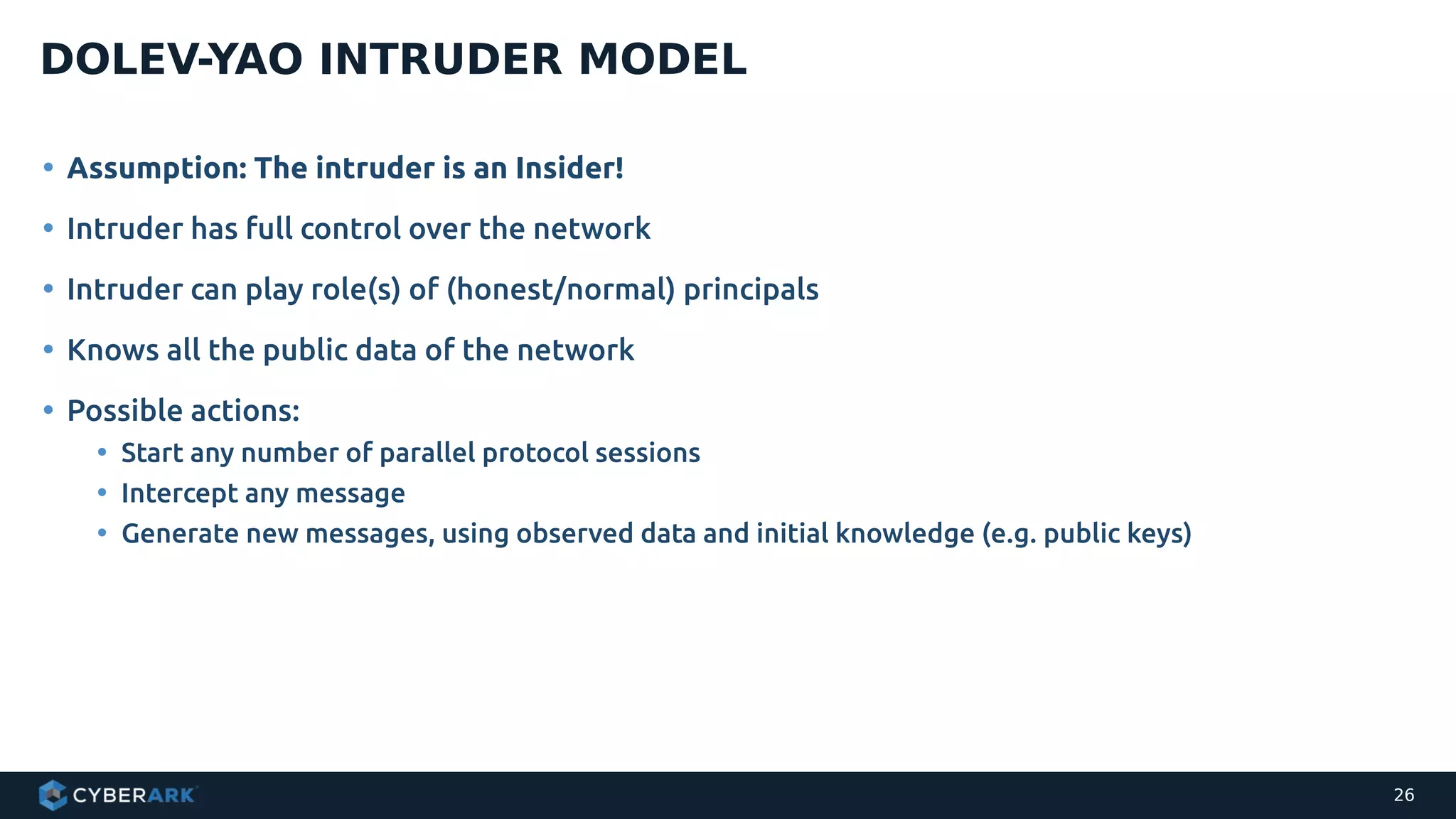
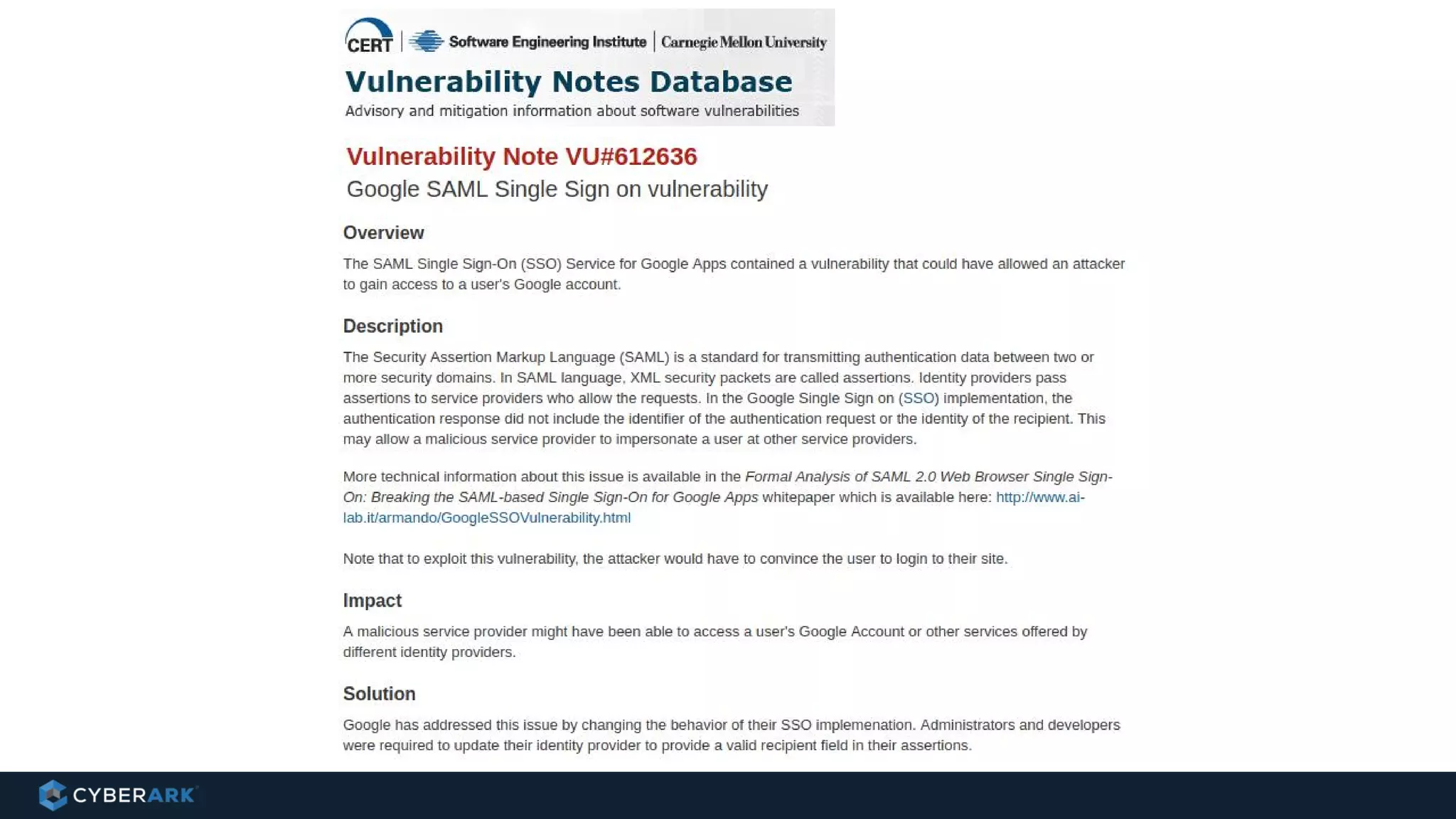
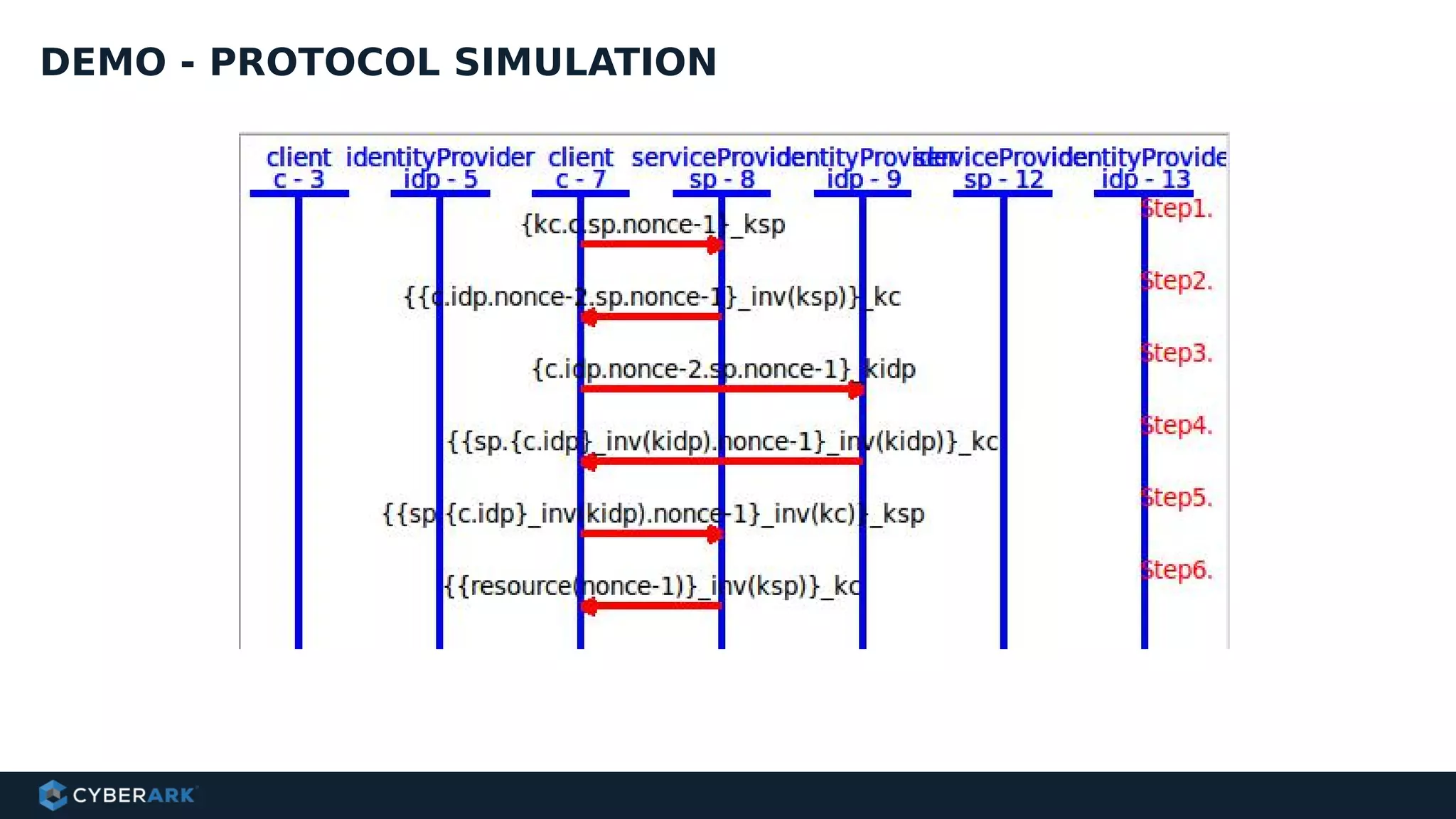
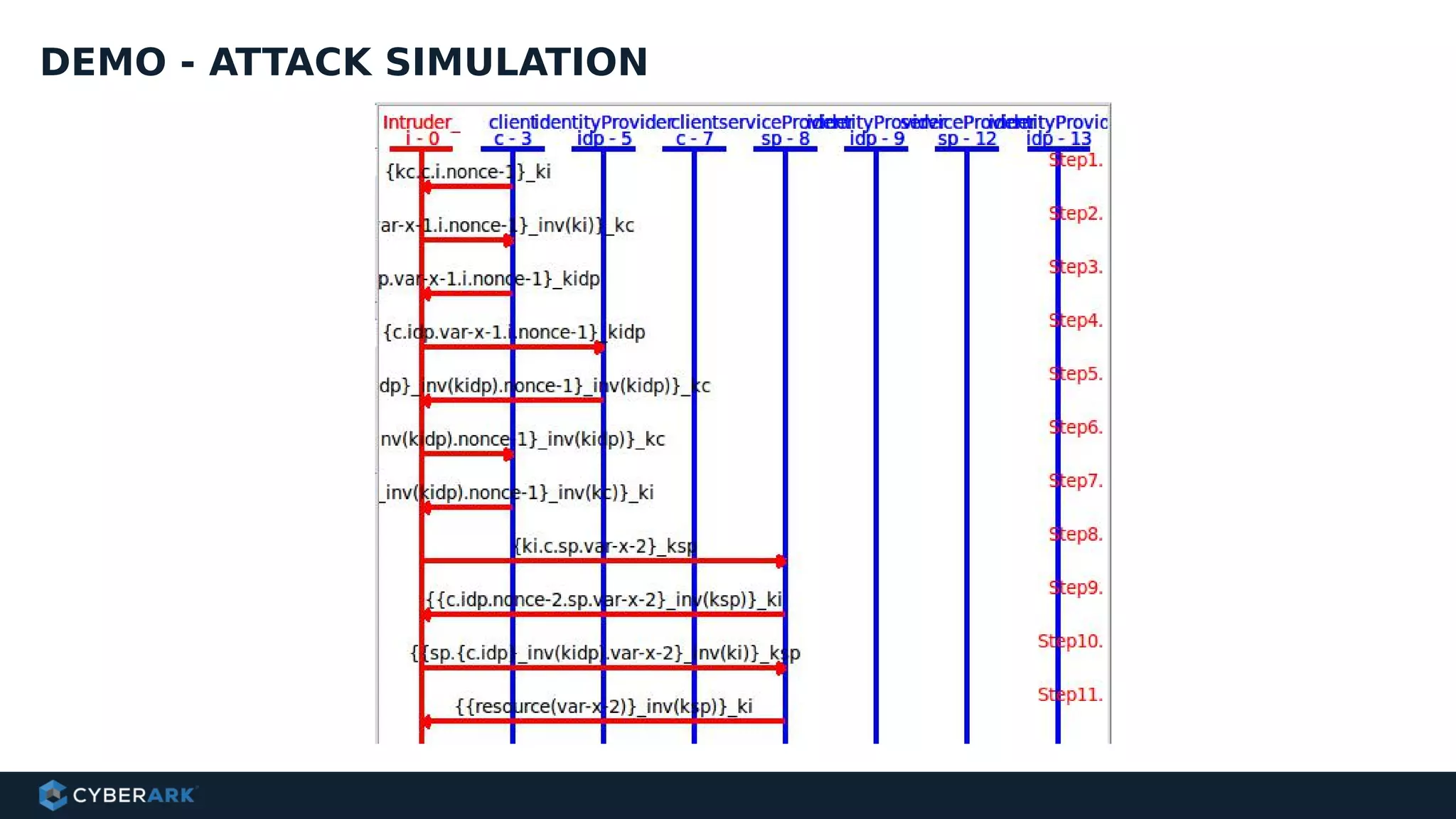
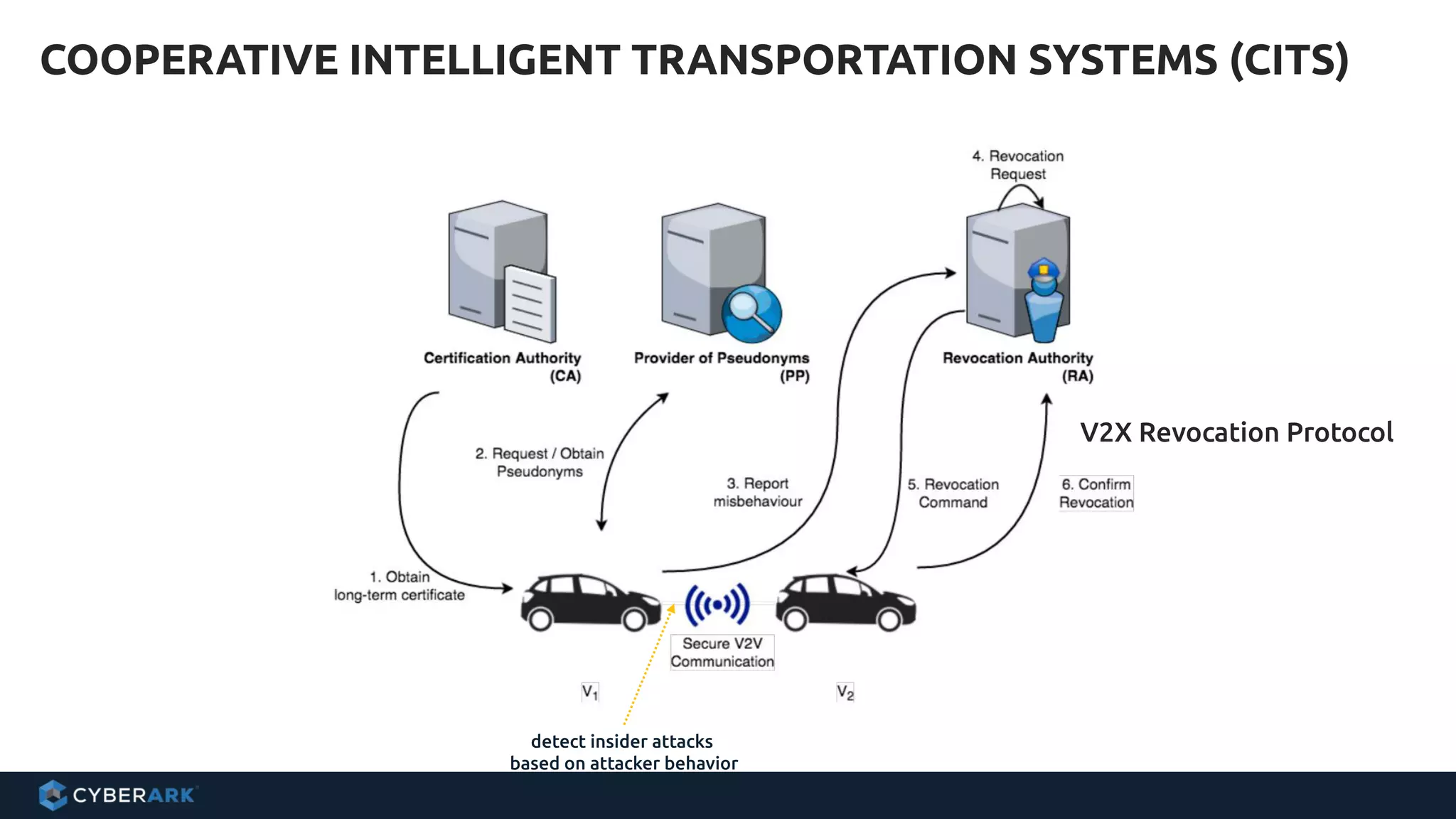
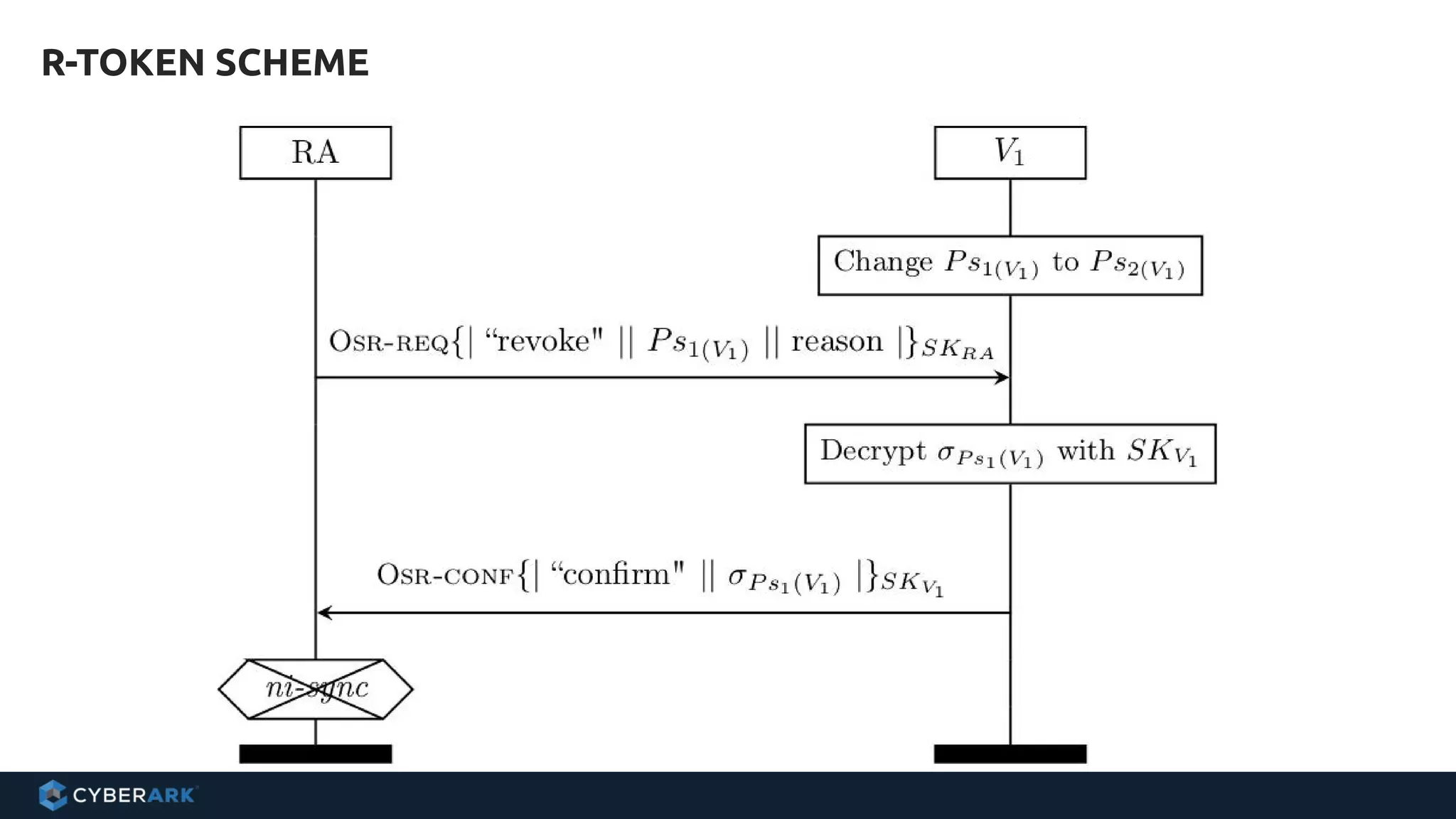
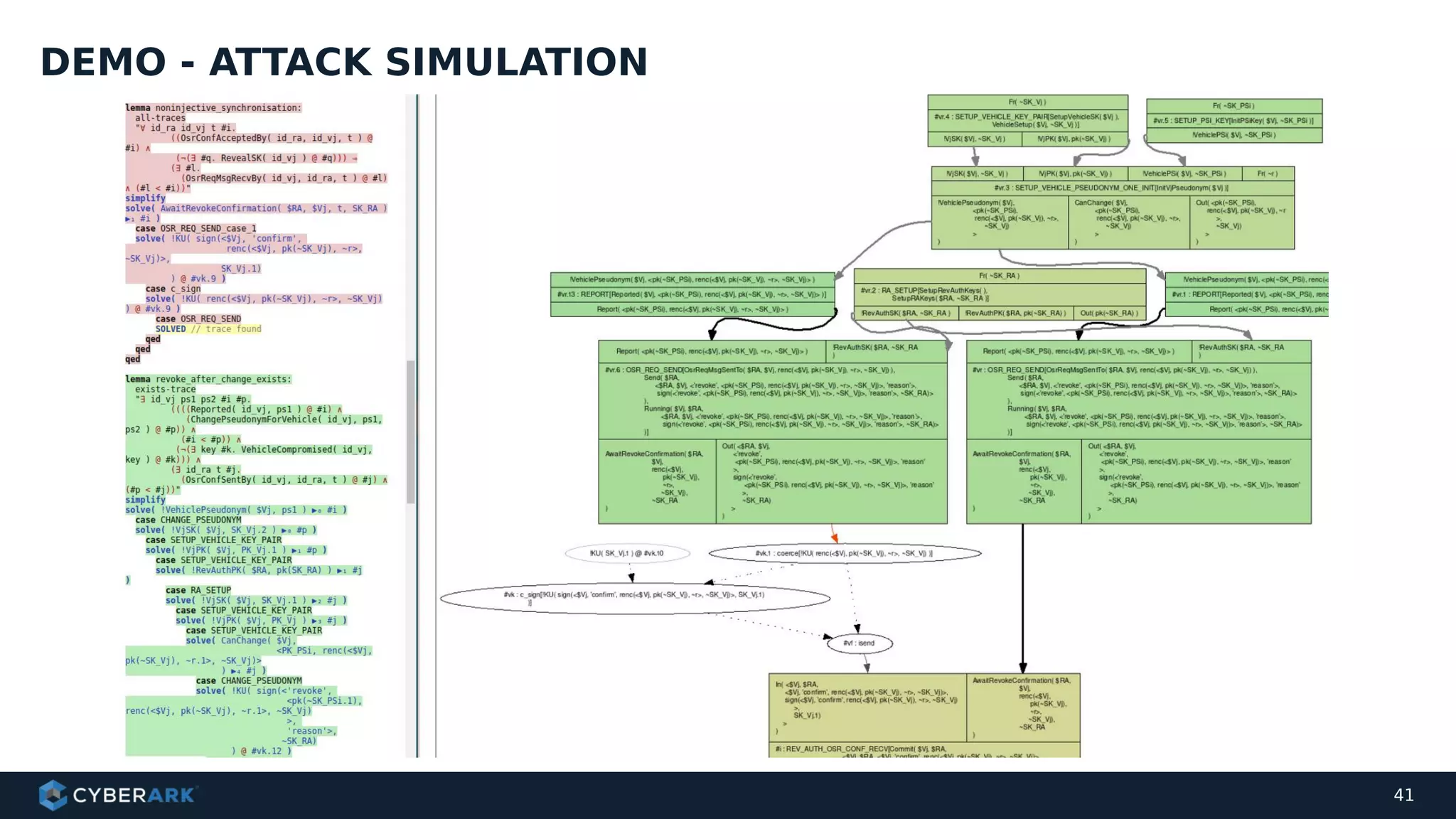
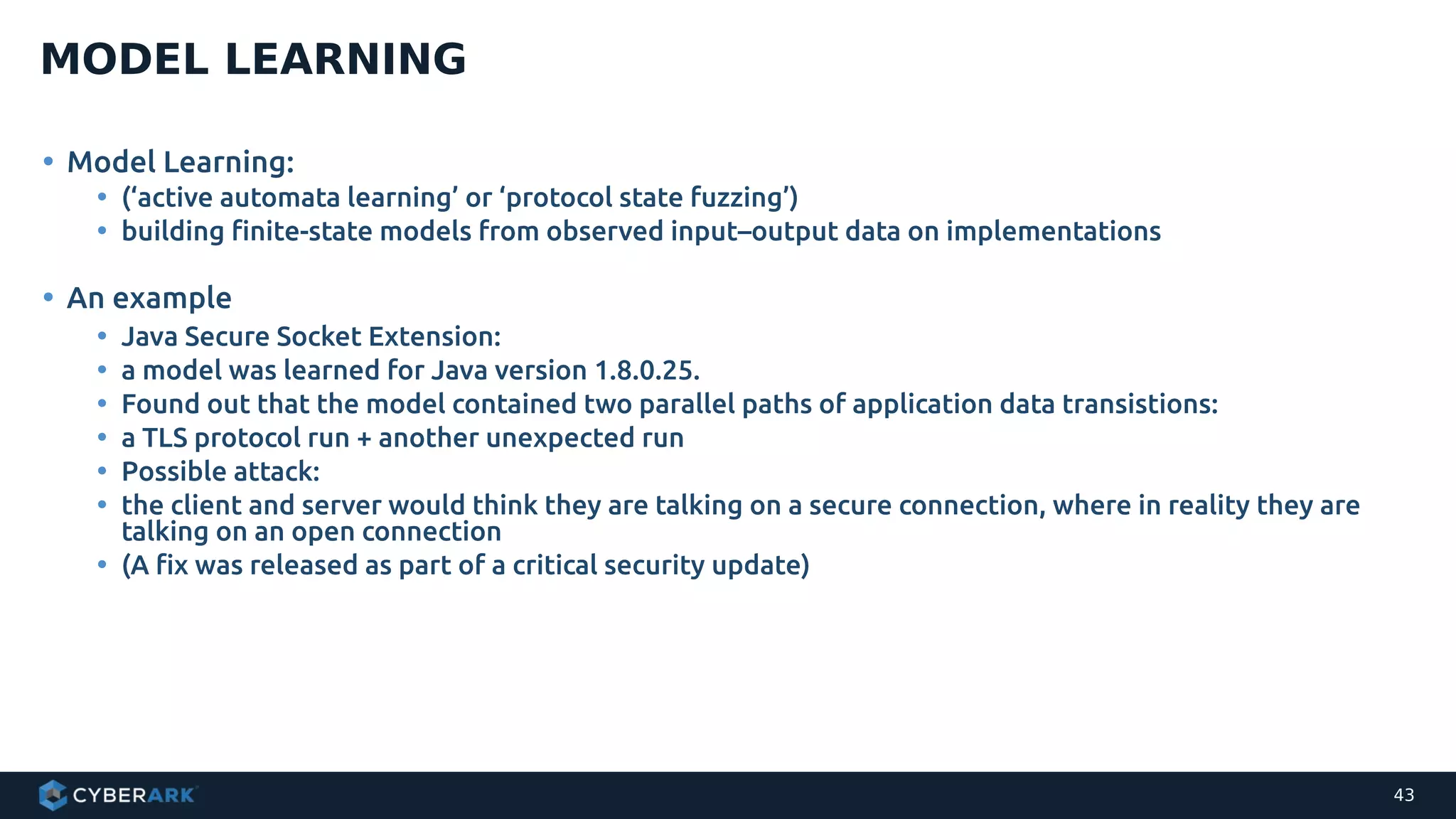
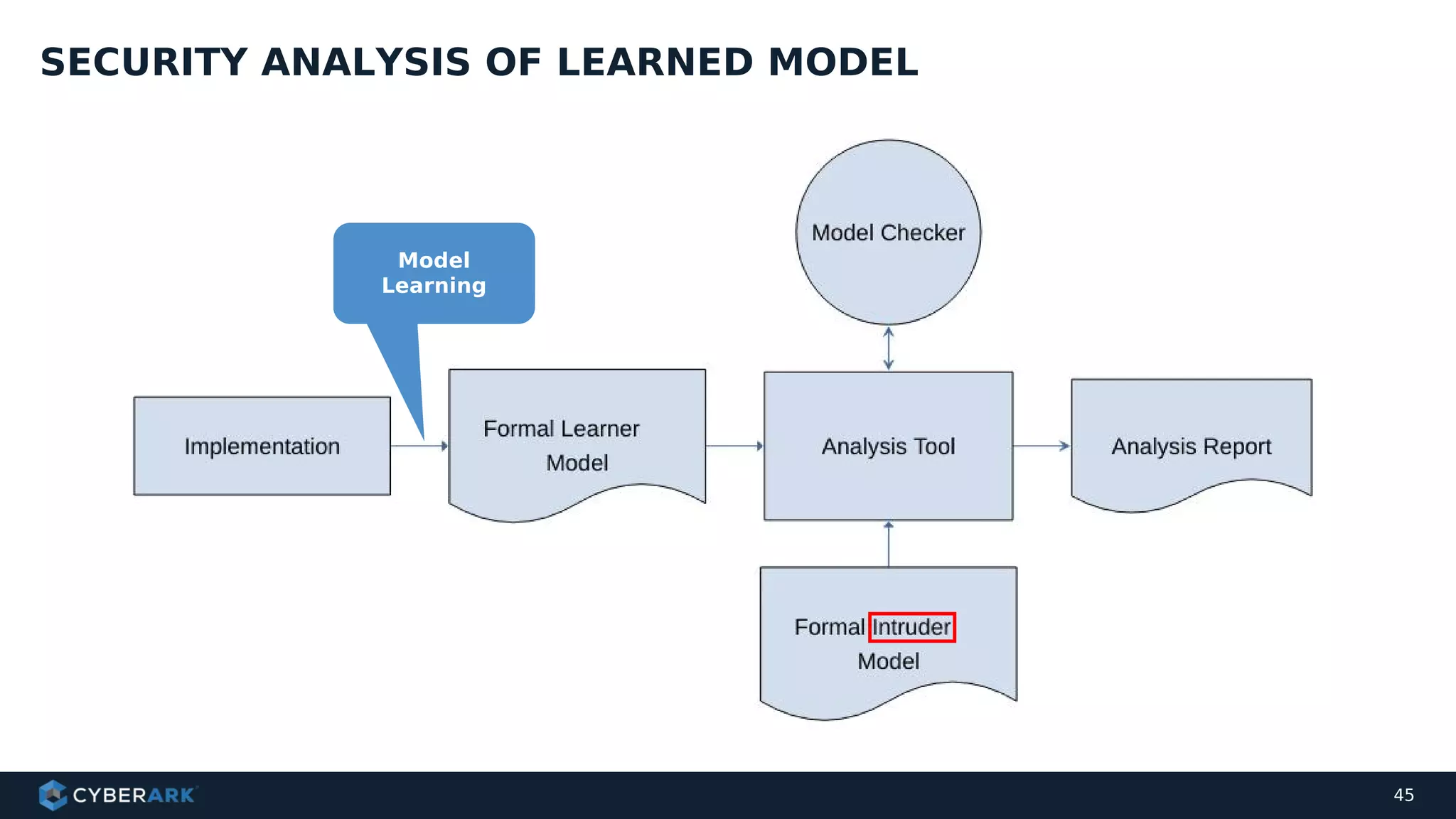
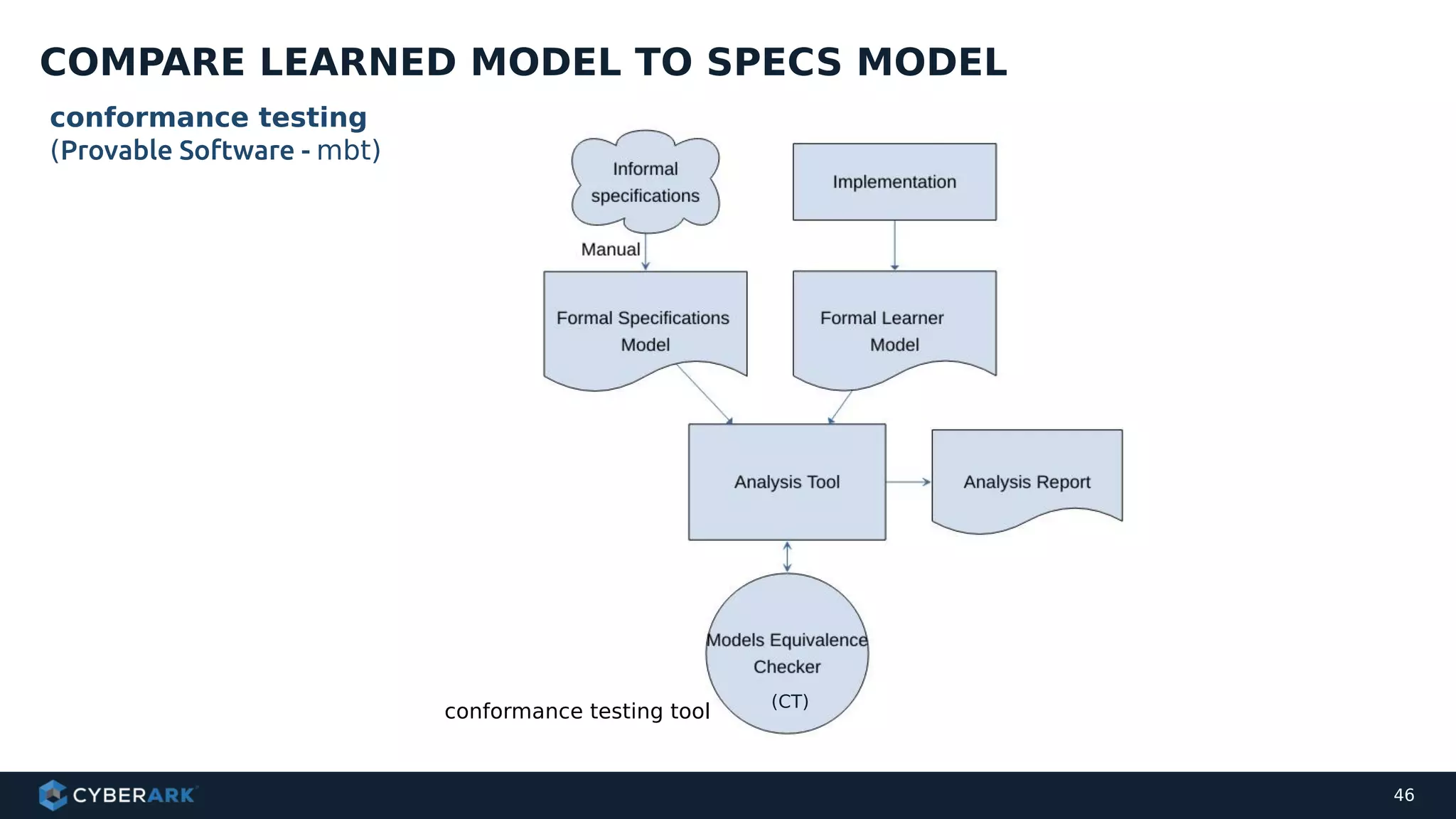
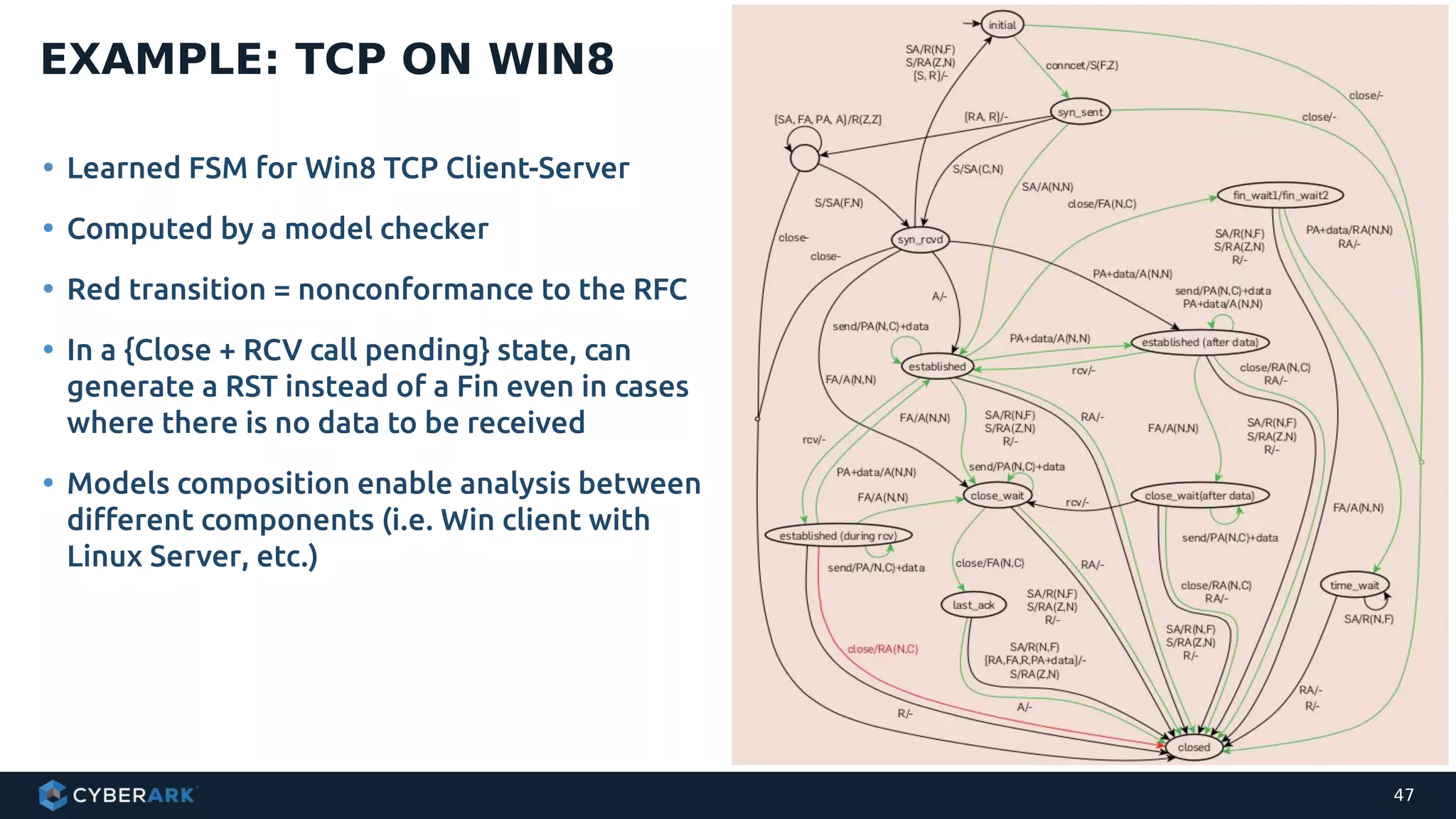
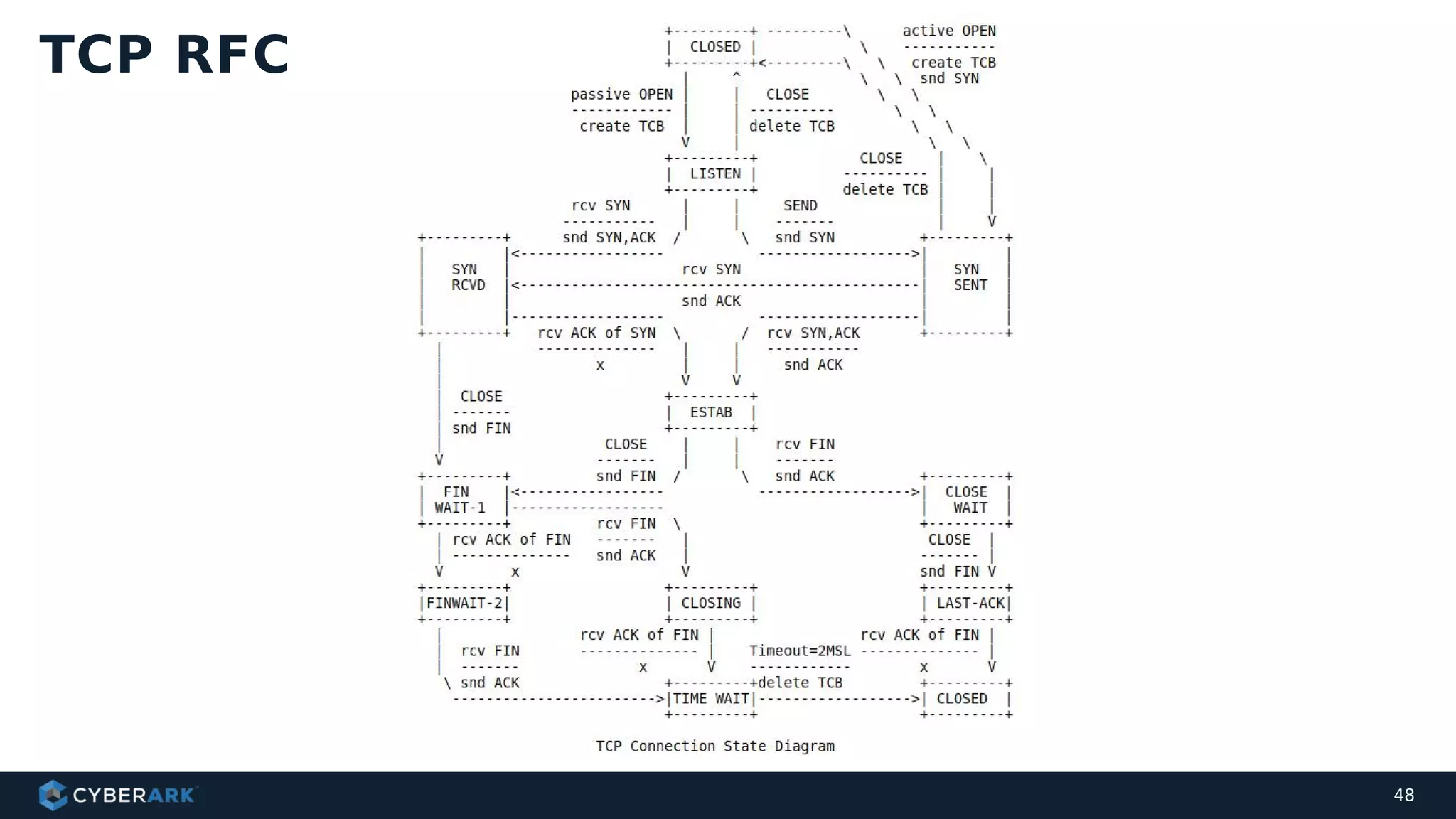
The document discusses using formal methods and model checking to analyze the security of cryptographic protocols. It presents a mutual authentication protocol as an example. Model checking involves defining a system as a finite-state machine model and then exhaustively checking all possible behaviors against security properties to identify vulnerabilities. The document demonstrates analyzing the example protocol using the AVISPA and Tamarin Prover tools, finding an attack on the original protocol but not on an updated version. It also discusses more advanced techniques like model learning and comparing learned models to specifications.