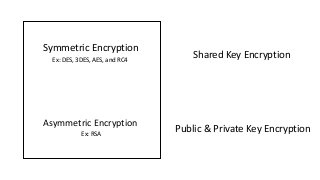
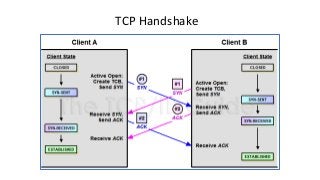
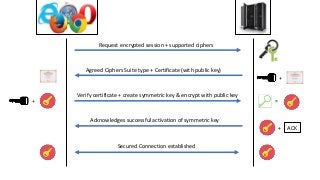
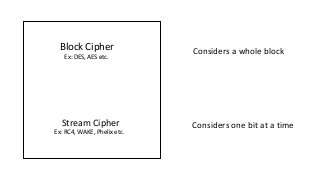
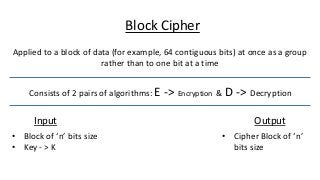
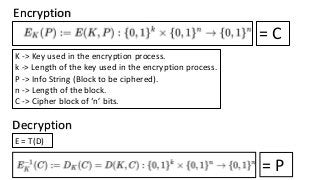
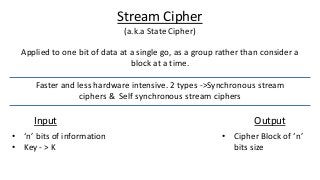
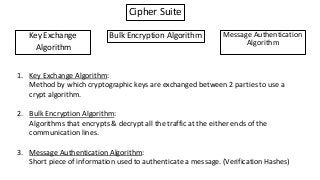
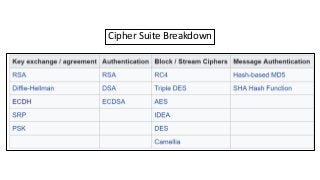
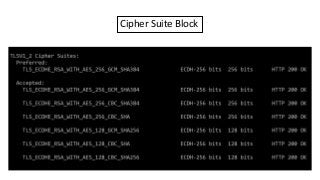
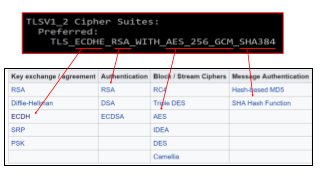
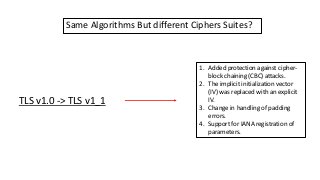
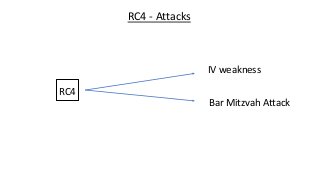
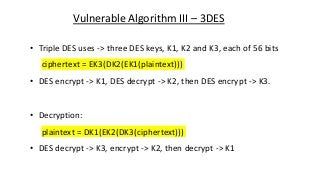
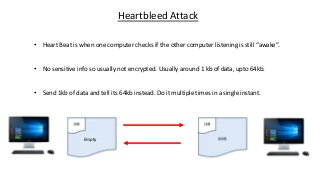
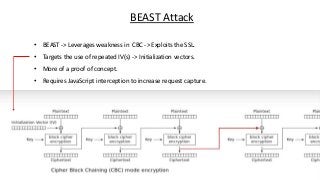
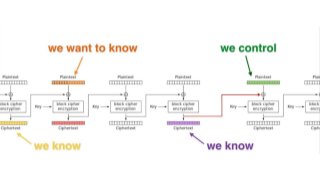
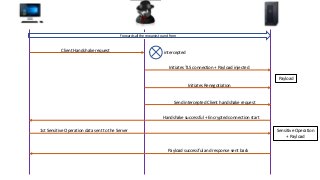
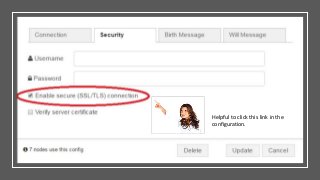
The document provides an in-depth overview of encryption, its various types, and associated protocols such as SSL/TLS. It details the workings of ciphers, cipher suites, and vulnerabilities related to different encryption algorithms and attacks. Additionally, it discusses certificate validation procedures and common vulnerabilities while emphasizing the importance of secure encryption practices.