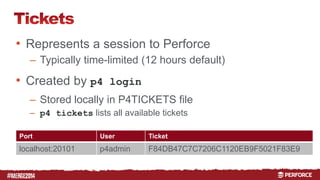
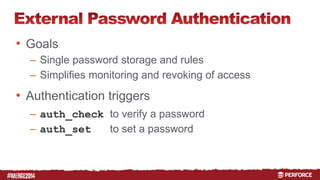
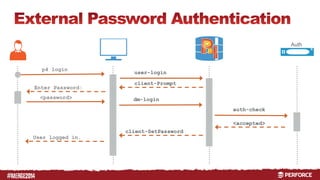
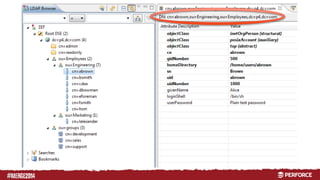
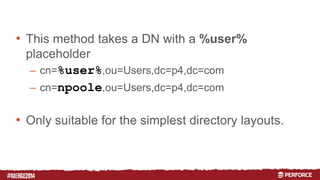
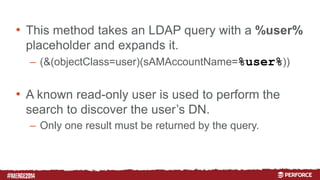
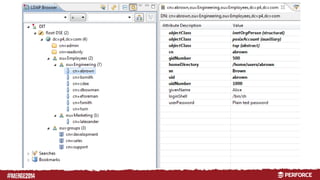
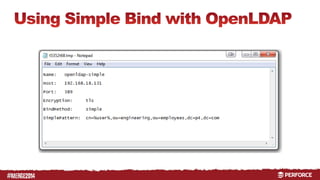
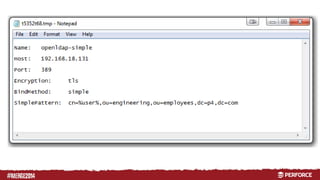
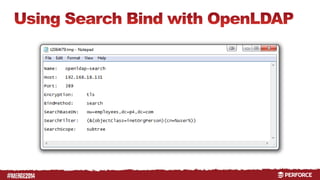
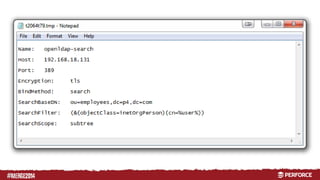
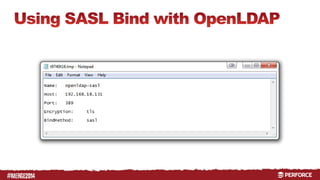
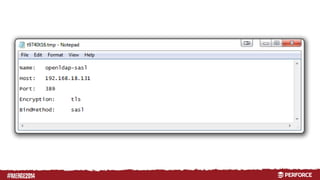
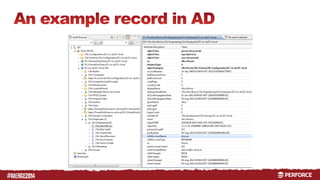
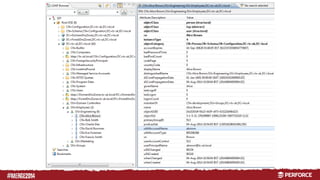
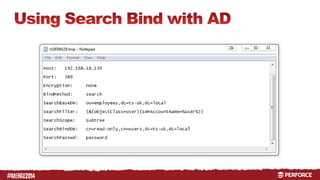
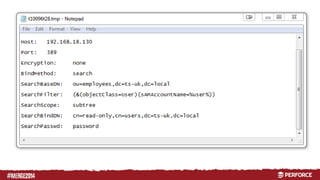
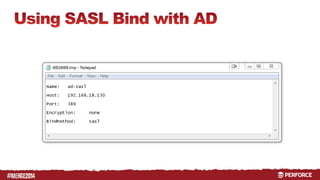
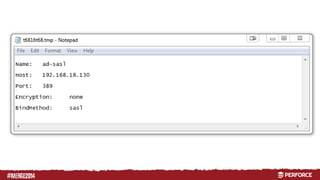
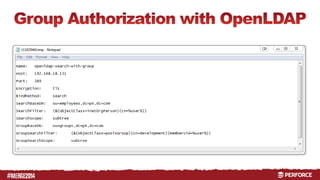
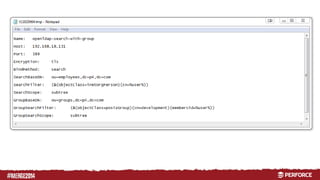
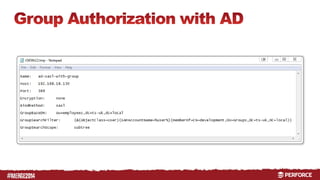
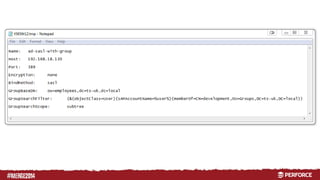
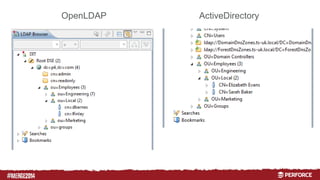
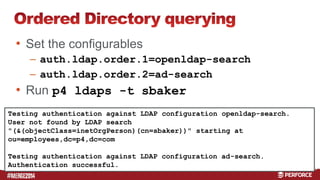
The document provides an overview of user authentication in Perforce, focusing on integrating LDAP for enhanced security and user management. It discusses the configuration of LDAP settings, the creation of protection tables, and various bind methods for user identification. The new LDAP integration simplifies authentication processes and allows for monitoring and revocation of access.