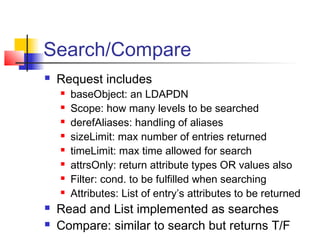
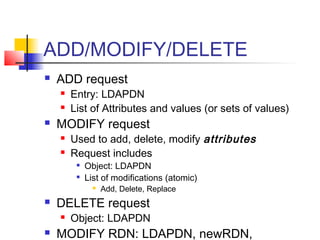
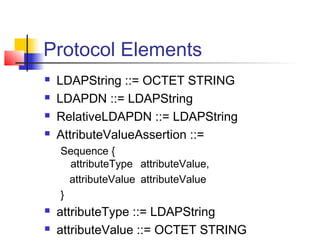
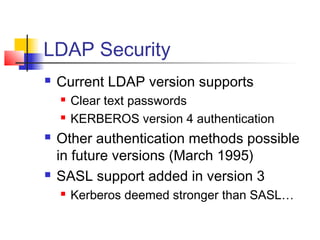
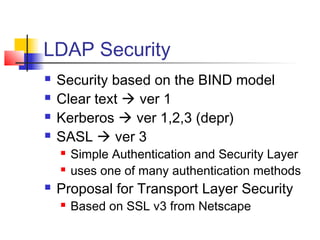
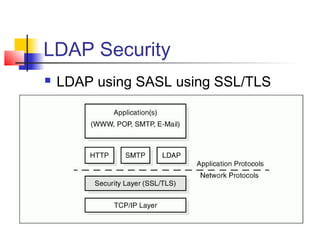
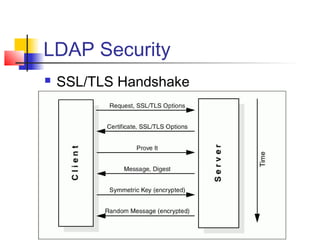
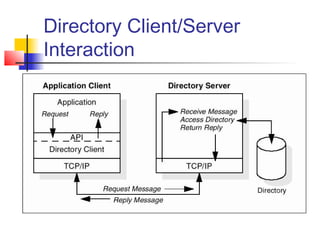
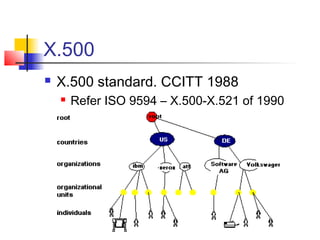
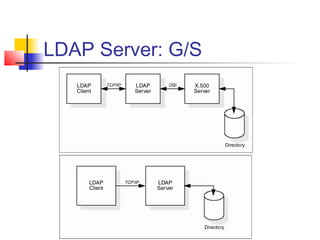
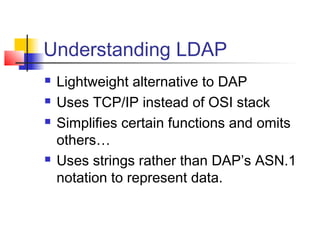
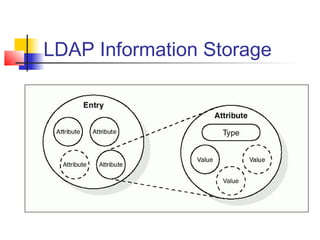
The document discusses the Lightweight Directory Access Protocol (LDAP) which provides a method for accessing and updating directory services based on the X.500 model. It describes LDAP's lightweight alternative approach compared to X.500, how information is structured and named in an LDAP directory, the functional operations that can be performed, security considerations, and how the protocol is encoded for transmission.











![BIND/UNBIND/ABANDON
Request includes LDAP version, the name
the client wants to bind as, authentication
type
Simple (clear text passwords, anonymous)
Kerberos v4 to the LDAP server (krbv42LDAP)
Kerberos v4 to the DSA server (krbv42DSA)
Server responds with a status indication
UNBIND: Terminates a protocol session
UnbindRequest ::= [APPLICATION 2] NULL
ABANDON:](https://image.slidesharecdn.com/khem-130524101900-phpapp01/85/LDAP-19-320.jpg)