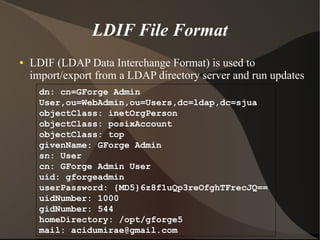
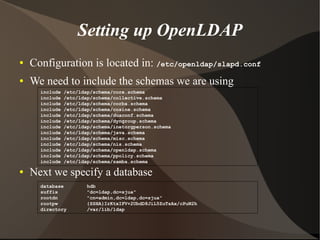
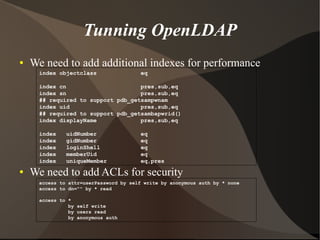
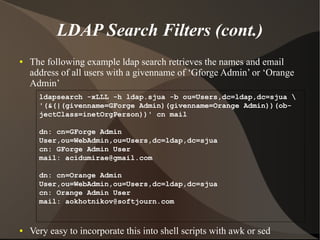
This document provides an overview of LDAP (Lightweight Directory Access Protocol). It discusses directory services and the need for LDAP, provides an introduction to LDAP including its benefits and basics, and covers setting up and tuning OpenLDAP as well as other LDAP tools and applications.