This document discusses the LDAP Synchronization Connector (LSC), an open-source tool for synchronizing data between different data sources like LDAP directories, SQL databases, and files. It provides an overview of LSC's features like connectors for various data sources, synchronization rules, logging capabilities, and support for Active Directory. The document also describes how to configure LSC to synchronize between an OpenLDAP directory and Active Directory, including handling passwords and attribute mapping between the different schemas.

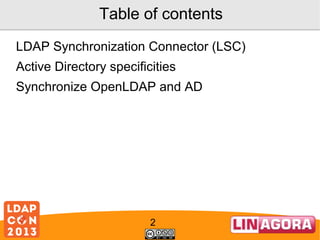





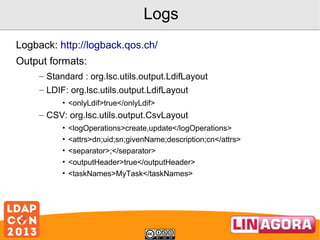
![Examples
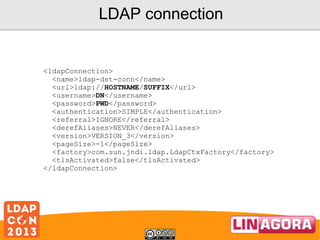
<dataset>
<name>objectClass</name>
<policy>KEEP</policy>
<forceValues>
<string>"top"</string>
<string>"person"</string>
<string>"organizationalPerson"</string>
<string>"inetOrgPerson"</string>
</forceValues>
</dataset>
<dataset>
<name>cn</name>
<policy>FORCE</policy>
<forceValues>
<string><[CDATA[
srcBean.getDatasetFirstValueById("FIRSTNAME") +
srcBean.getDatasetFirstValueById("NAME");
]]></string>
</forceValues>
</dataset>](https://image.slidesharecdn.com/ldapcon2013coudotlscadopenldap-131120051145-phpapp02/85/Synchronize-AD-and-OpenLDAP-with-LSC-16-320.jpg)
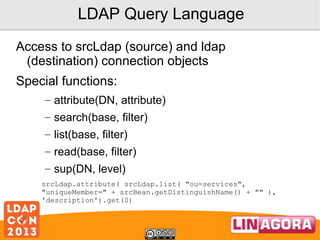

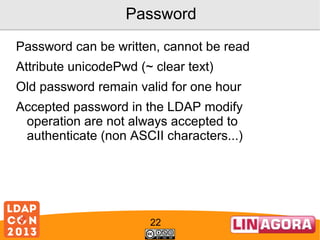
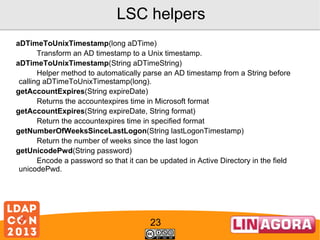
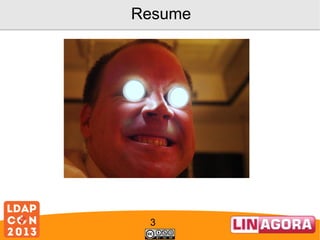
![LSC helpers
unixTimestampToADTime(int unixTimestamp)
Transform a Unix timestamp to an AD timestamp.
unixTimestampToADTime(String unixTimestampString)
Helper method to automatically parse a Unix timestamp from a
String before calling unixTimestampToADTime(int).
userAccountControlCheck(int value, String constToCheck)
Check if a bit is set in UserAccountControl
userAccountControlSet(int origValue, String[] constToApply)
Set or unset some bits to a UserAccountControl attribute of an
AD
userAccountControlToggle(int value, String constToApply)
Toggle a bit in UserAccountControl
24](https://image.slidesharecdn.com/ldapcon2013coudotlscadopenldap-131120051145-phpapp02/85/Synchronize-AD-and-OpenLDAP-with-LSC-24-320.jpg)