The document contains questions about network access control lists (ACLs). Some key points:
- ACLs can be used to filter traffic by source/destination IP addresses, protocols, ports and more. Standard ACLs filter based on source IP, extended ACLs add destination IP and other criteria.
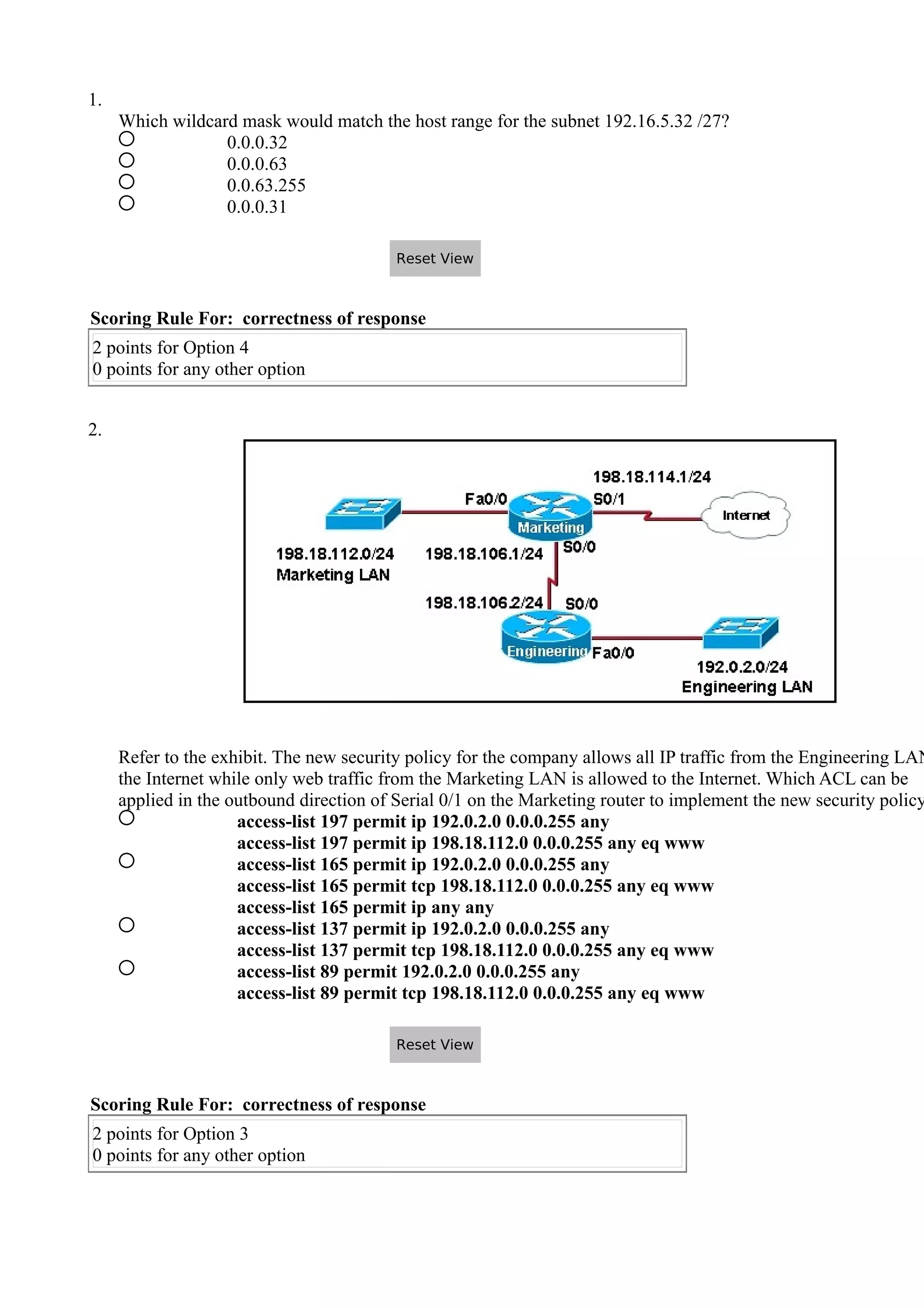
- The position and direction an ACL is applied impacts what traffic it filters. Inbound ACLs filter traffic as it enters an interface while outbound ACLs filter traffic exiting an interface.
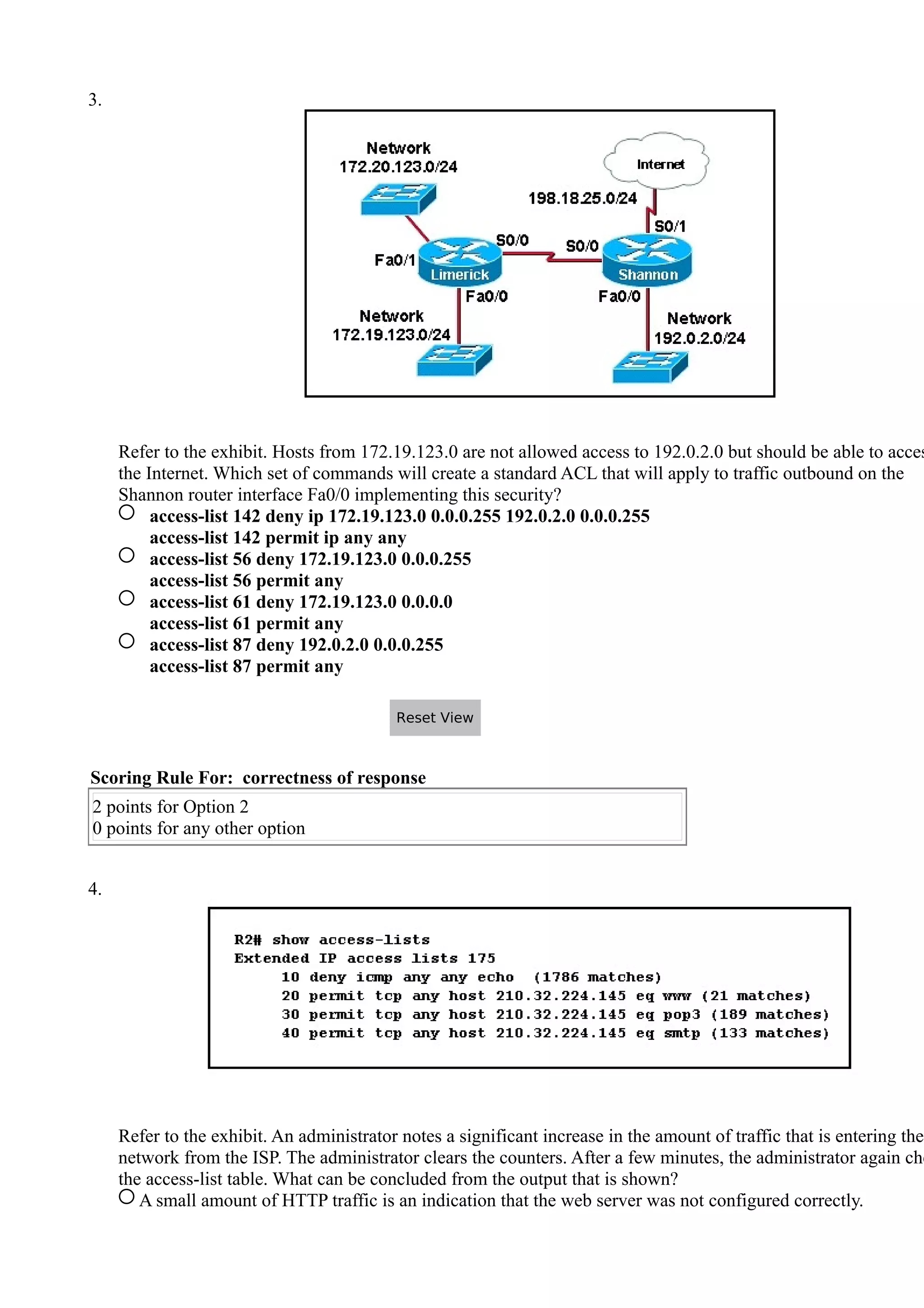
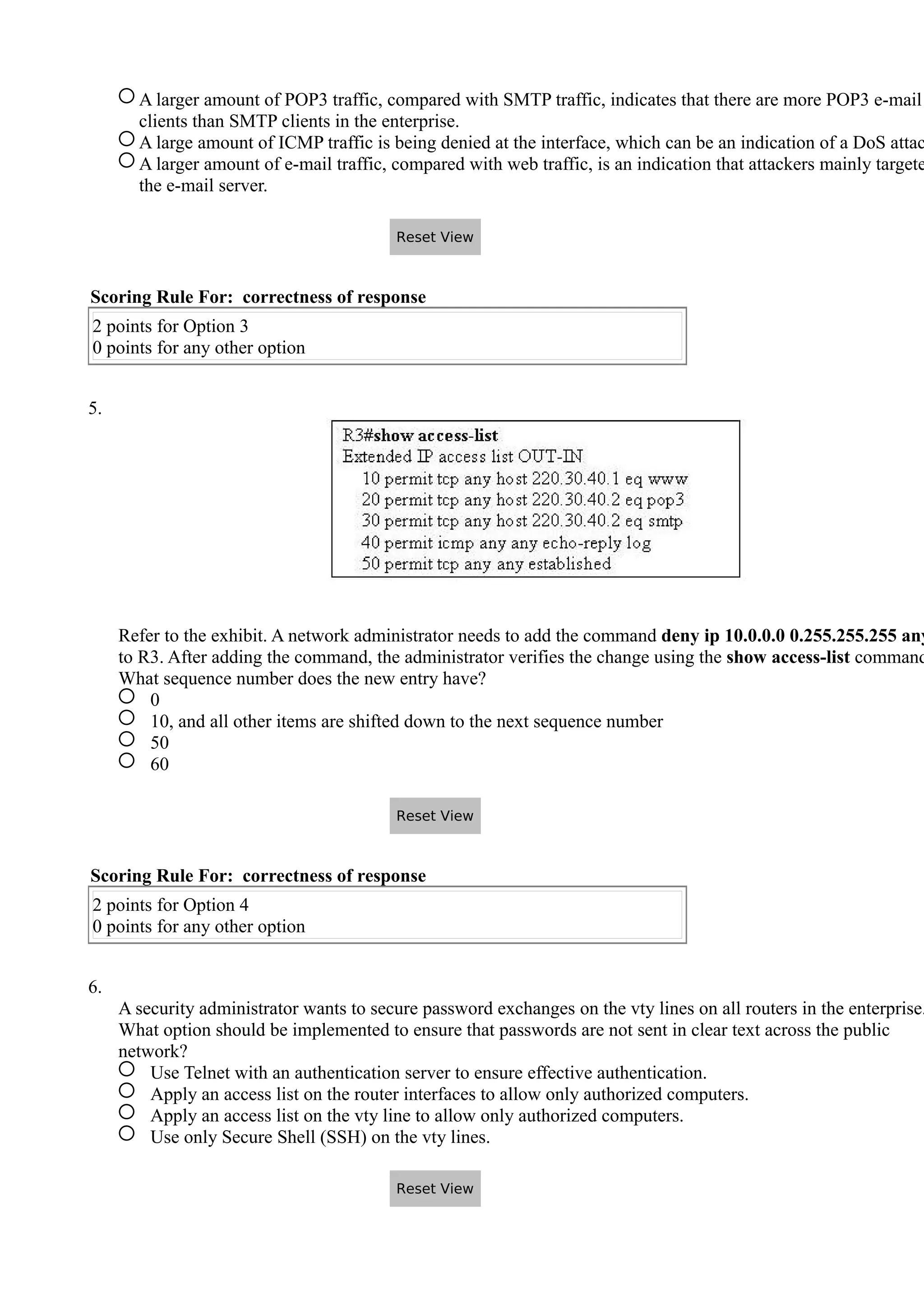
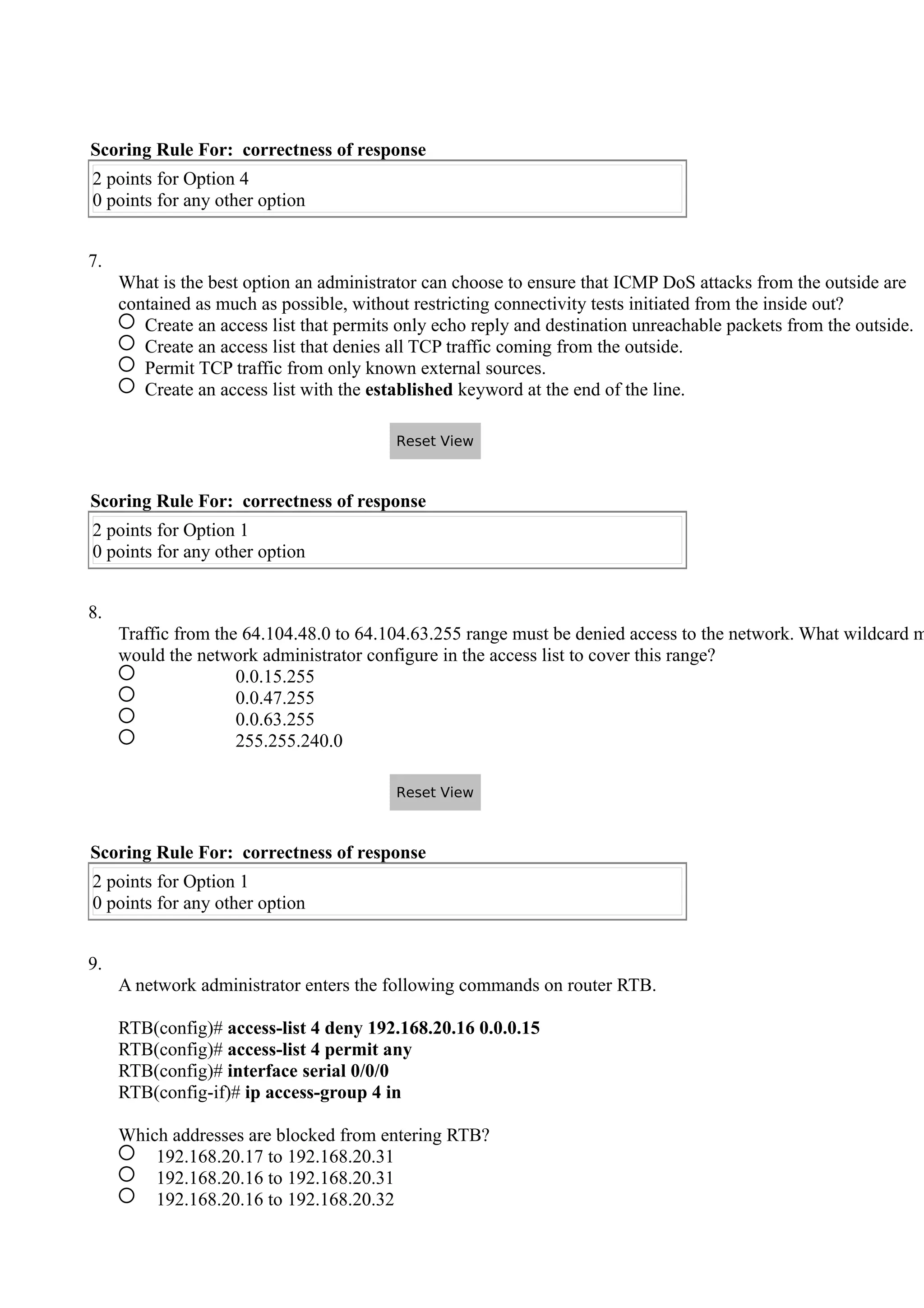
- ACL rules are processed sequentially, with the first match determining if a packet is permitted or denied. Administrators must carefully craft rule orders and contents to implement desired security policies.