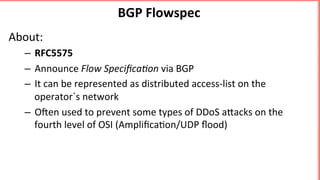
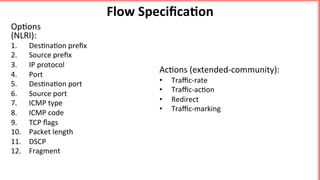
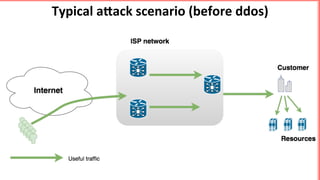
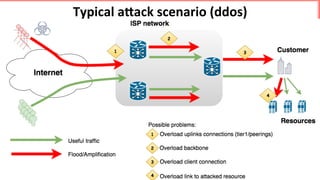
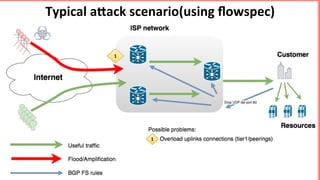
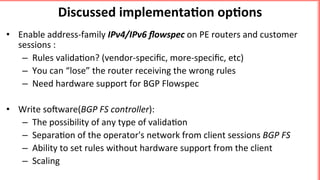
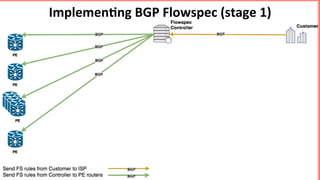
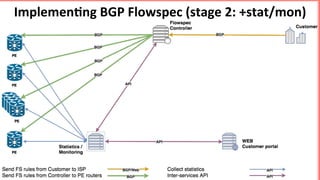
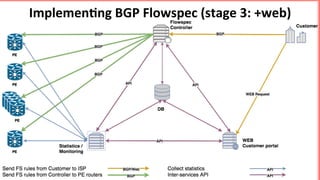
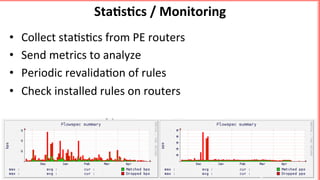
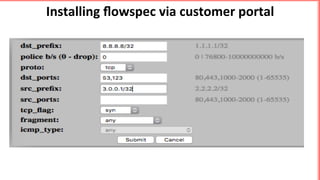
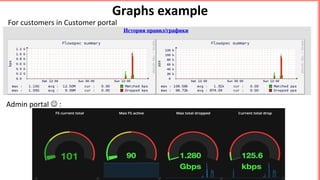
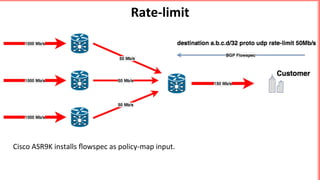
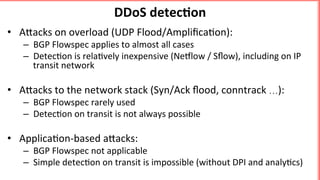
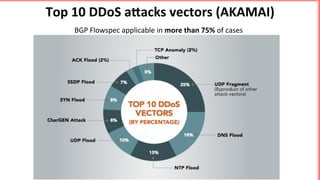
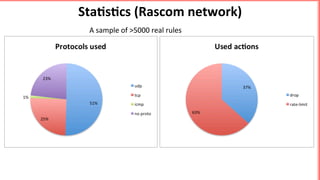
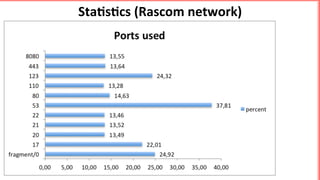
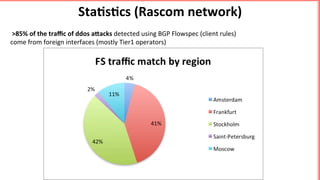
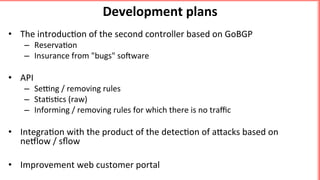
This document discusses implementing BGP Flowspec at an IP transit network to help mitigate distributed denial of service (DDoS) attacks. BGP Flowspec allows network operators to announce flow specifications via BGP to define distributed access lists across their network. The document outlines BGP Flowspec options, typical attack scenarios with and without its use, implementation considerations, validation of rules, statistics collection, and plans for a web portal and integration with attack detection systems. Over 85% of detected DDoS traffic was found to originate from foreign interfaces, showing BGP Flowspec's effectiveness against such attacks.