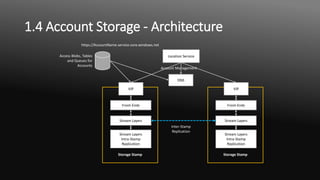
The document outlines seven key cyberattack methods targeting Microsoft Azure, highlighting the importance of understanding these threats for decision makers and IT professionals. It details various attack strategies such as privilege escalation, ransomware, and phishing, along with their countermeasures. The author emphasizes the necessity of strong security practices, including the use of Azure policies and a zero trust approach to mitigate risks in cloud environments.