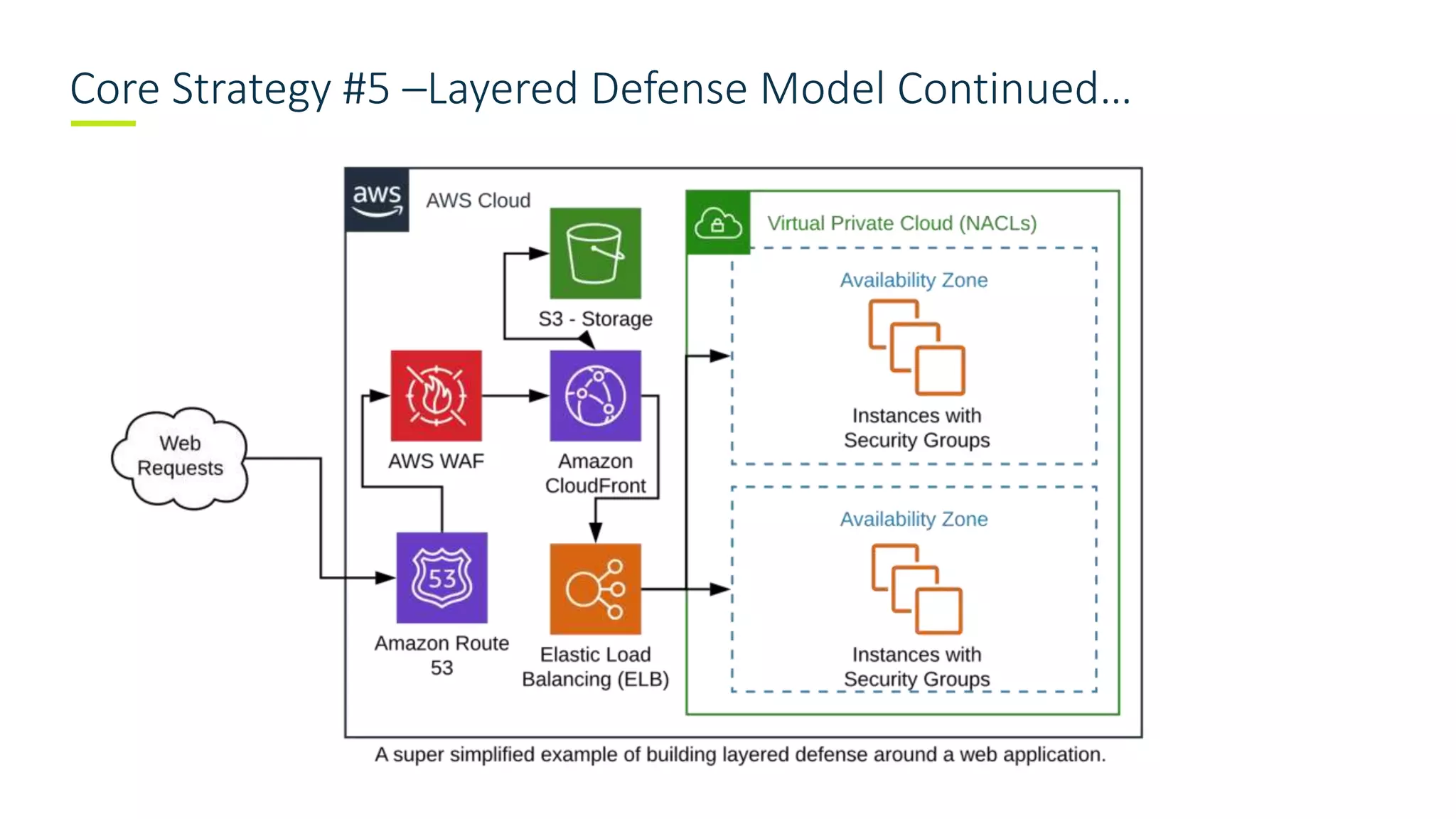
The document outlines core strategies for establishing robust security measures in AWS cloud environments, emphasizing the importance of logging, access management, and layered defenses. Key strategies include enabling cloud-centric logging, restricting root access, developing IAM management strategies, rotating access keys, and ensuring S3 data security. The document highlights that while security tools are valuable, foundational security practices should remain a priority.