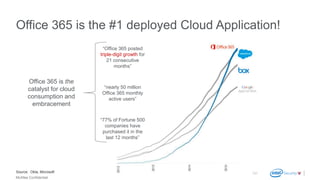
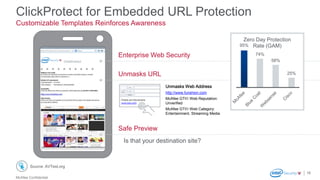
The document discusses McAfee Email Protection for Microsoft Office 365. It highlights that Office 365 adoption is growing rapidly, but email threats still exist in the cloud. McAfee's solution layers additional security on top of Office 365 to protect against phishing and malware. Key features include targeted attack protection, faster protection through McAfee's threat intelligence, and email continuity to ensure uptime. The document also addresses common customer objections and provides resources for sales enablement.