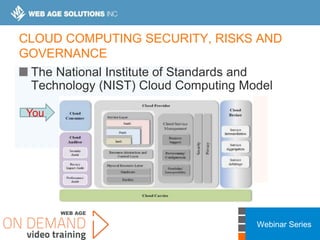
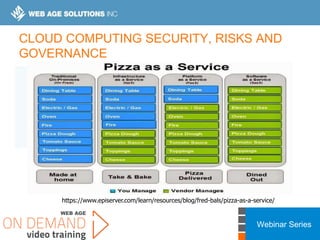
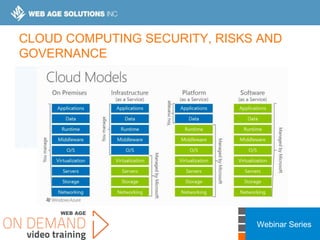
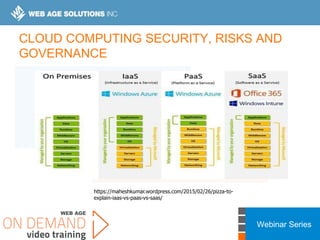
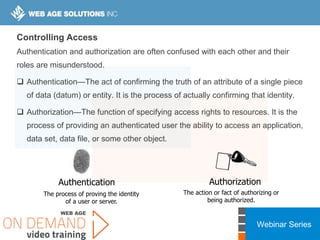
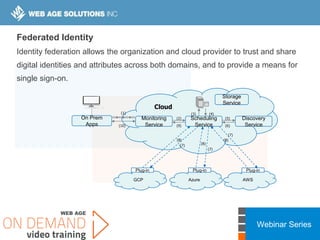
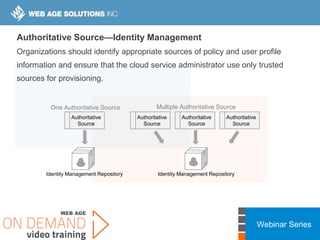
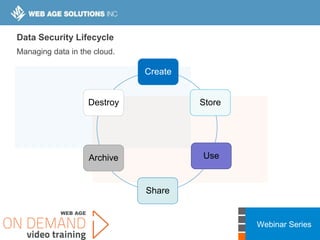
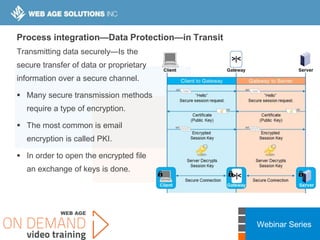
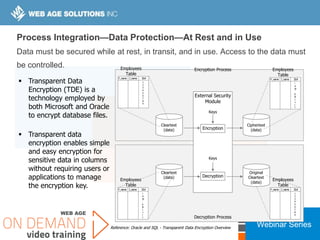
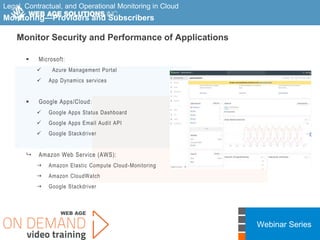
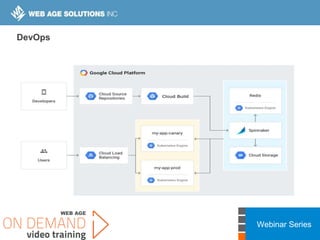
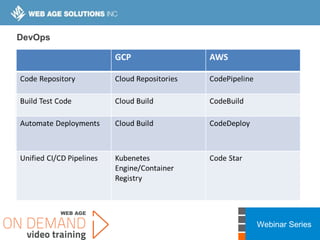
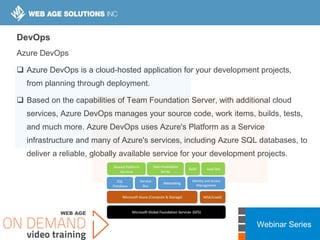
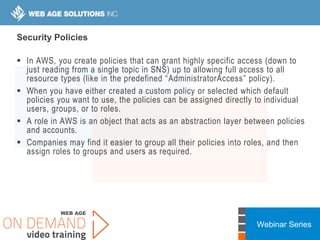
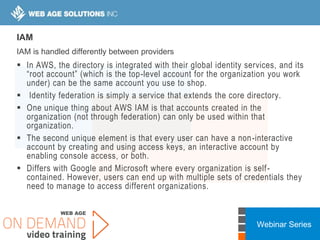
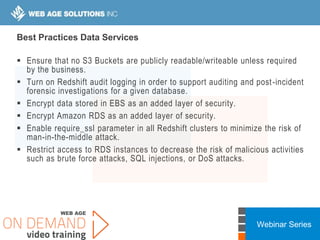
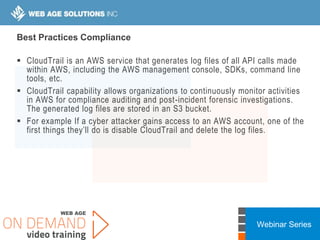
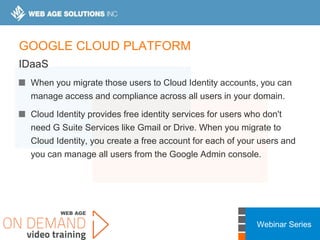
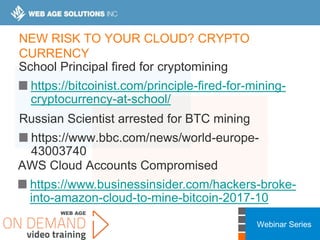
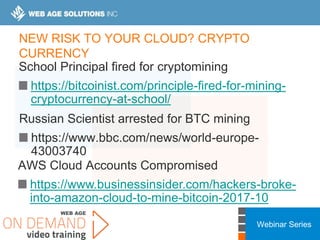
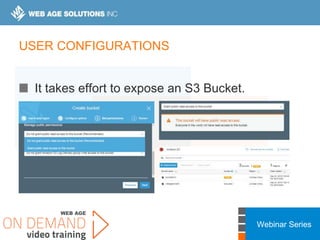
This webinar covers cloud security fundamentals across AWS, Azure, and GCP. It begins with introductions and an overview of the course, which includes cloud security 101, best practices for each cloud provider, and a discussion of current threats. The presentation covers topics such as the shared responsibility model, cloud security risks and governance models, identity and access management, data security, and techniques for mitigating risks in the cloud. It emphasizes the importance of a data-centric approach to security and controlling access according to the principles of least privilege and separation of duties.