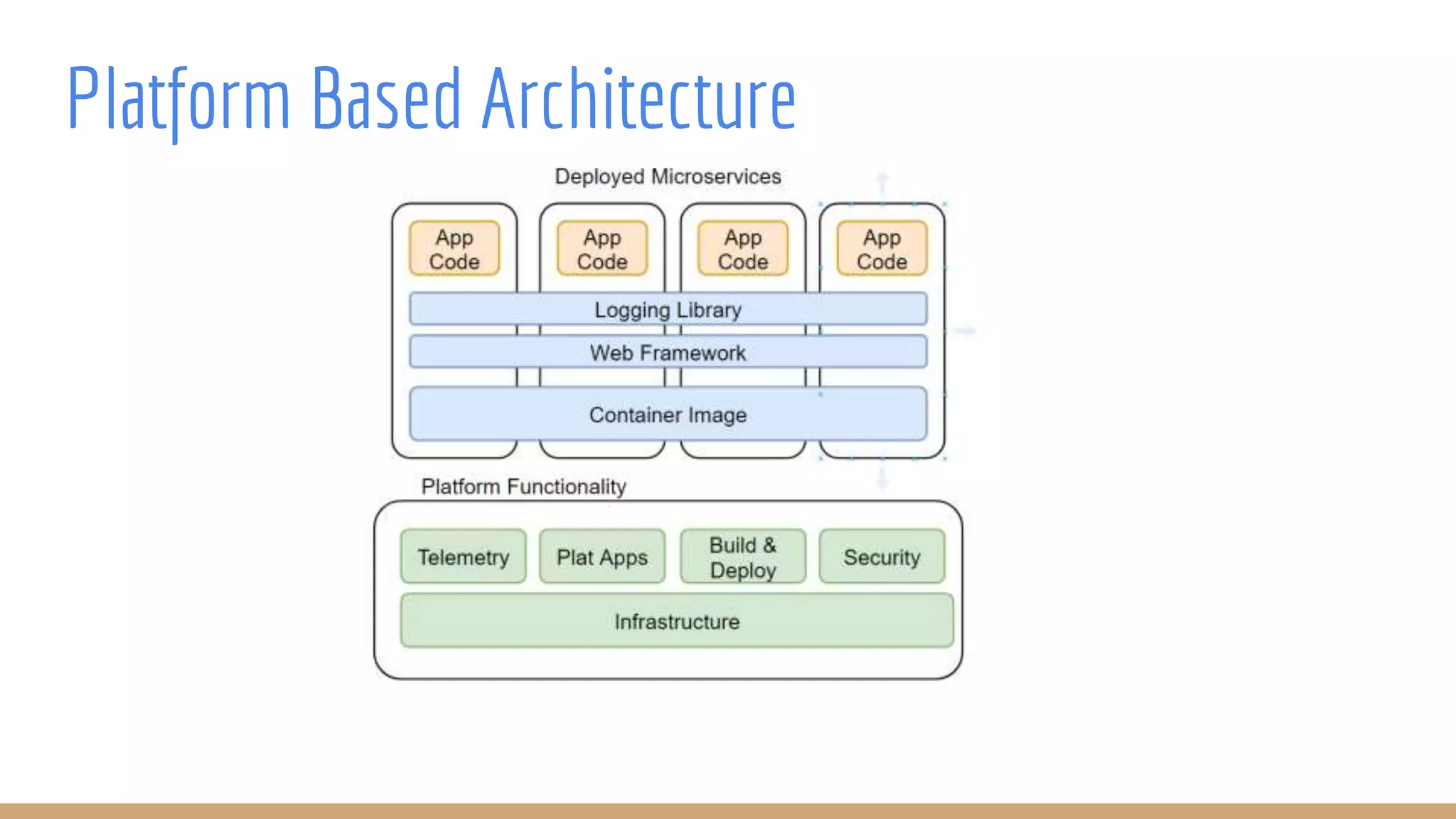
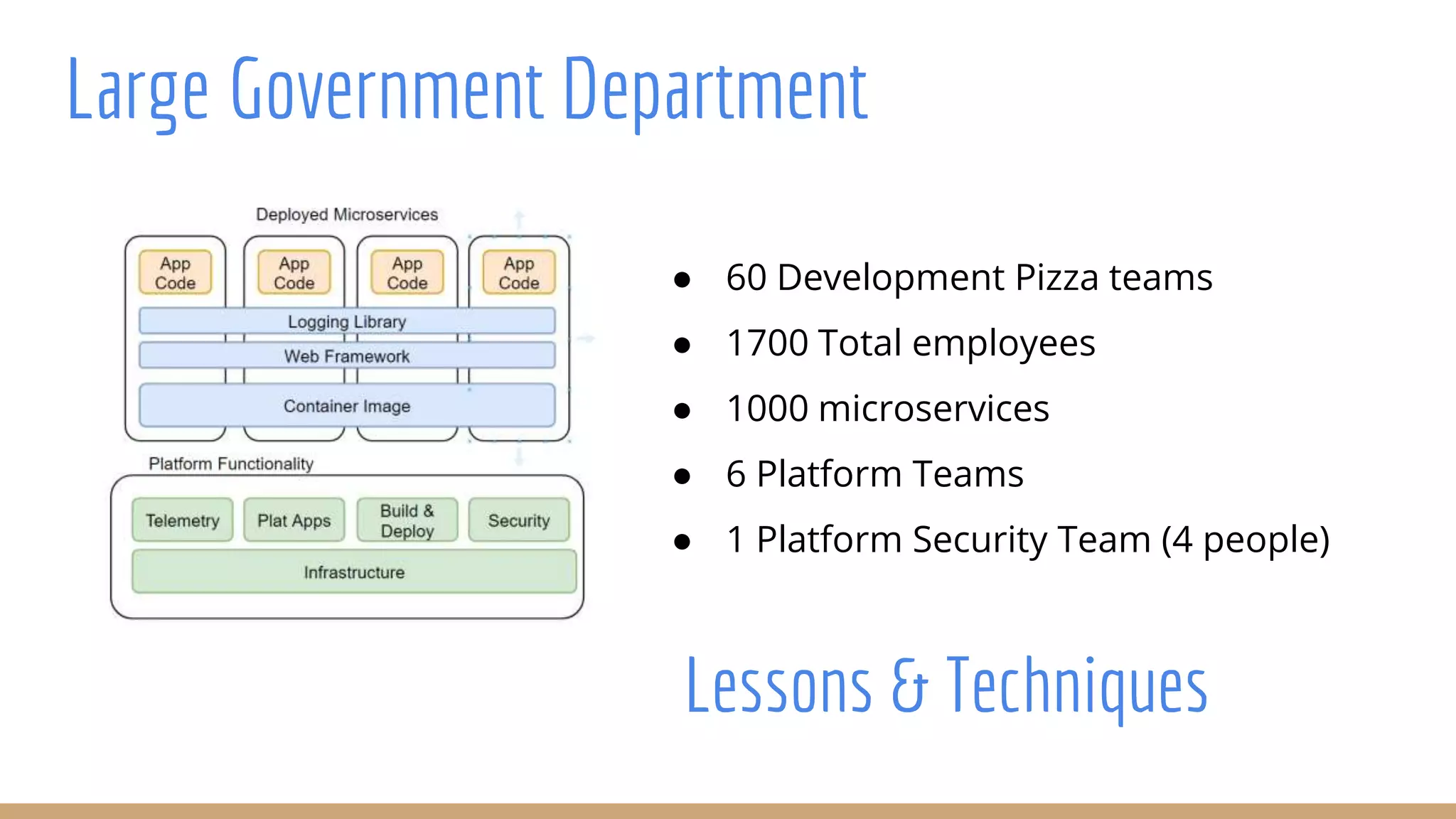
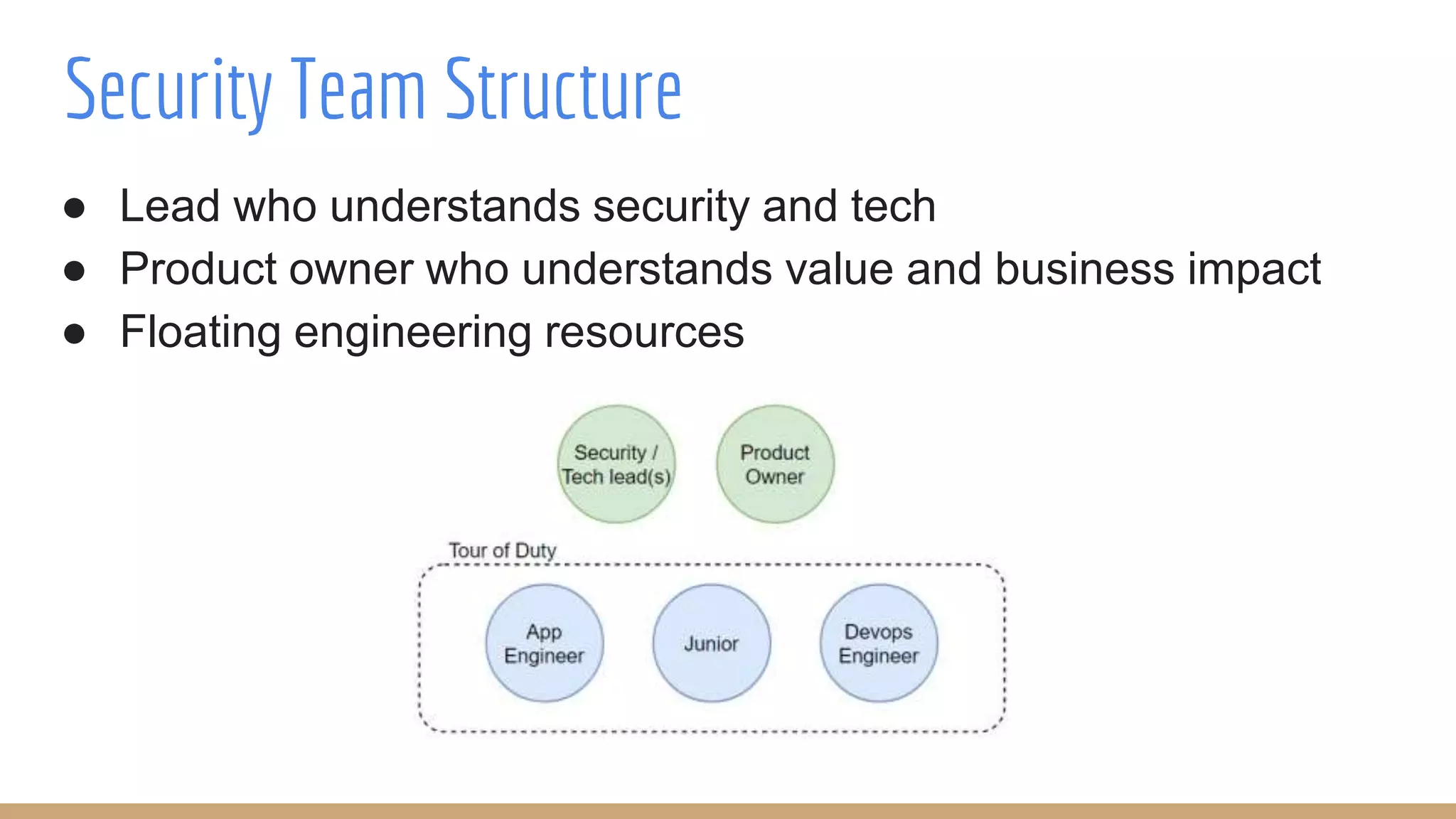
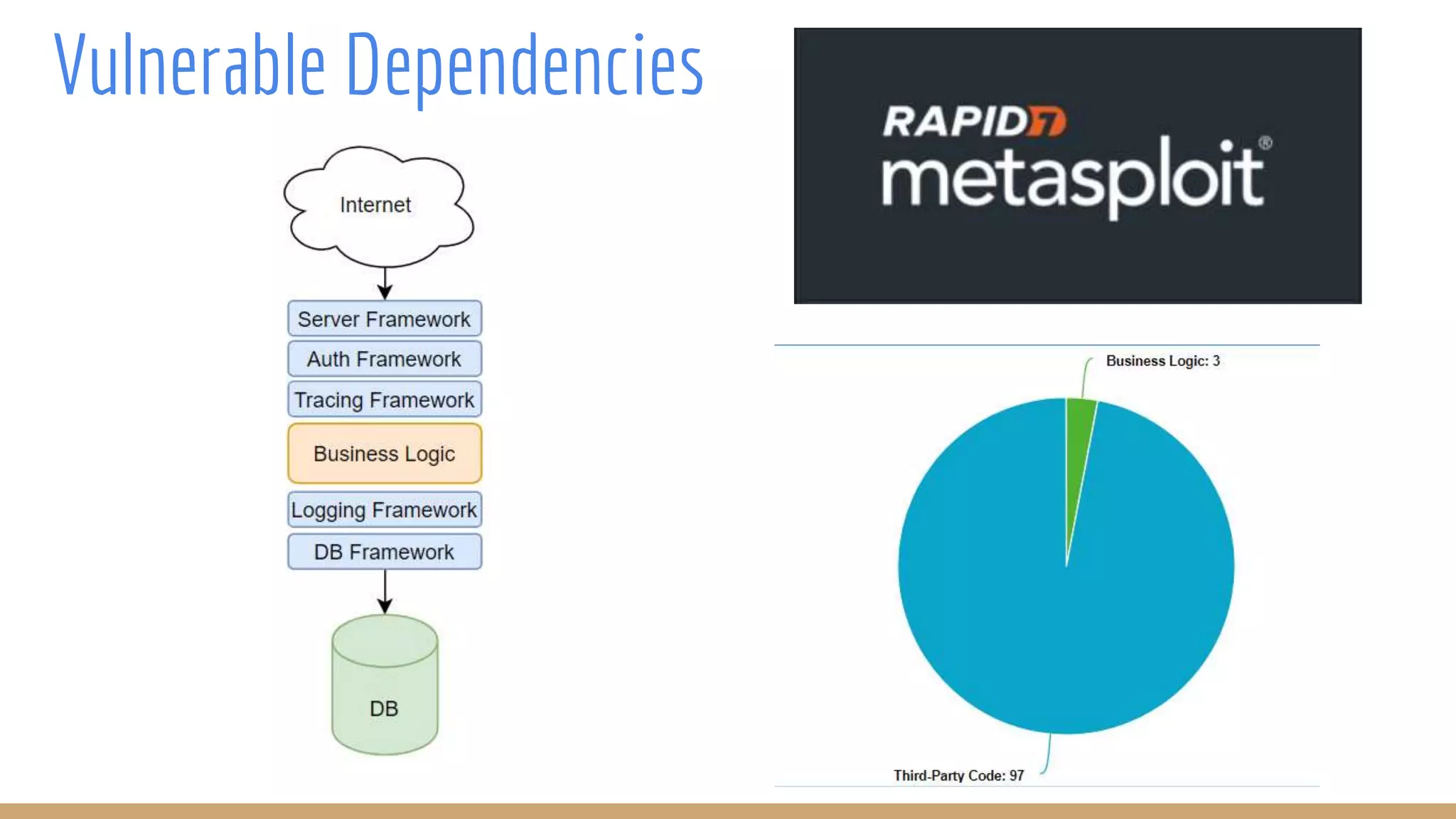
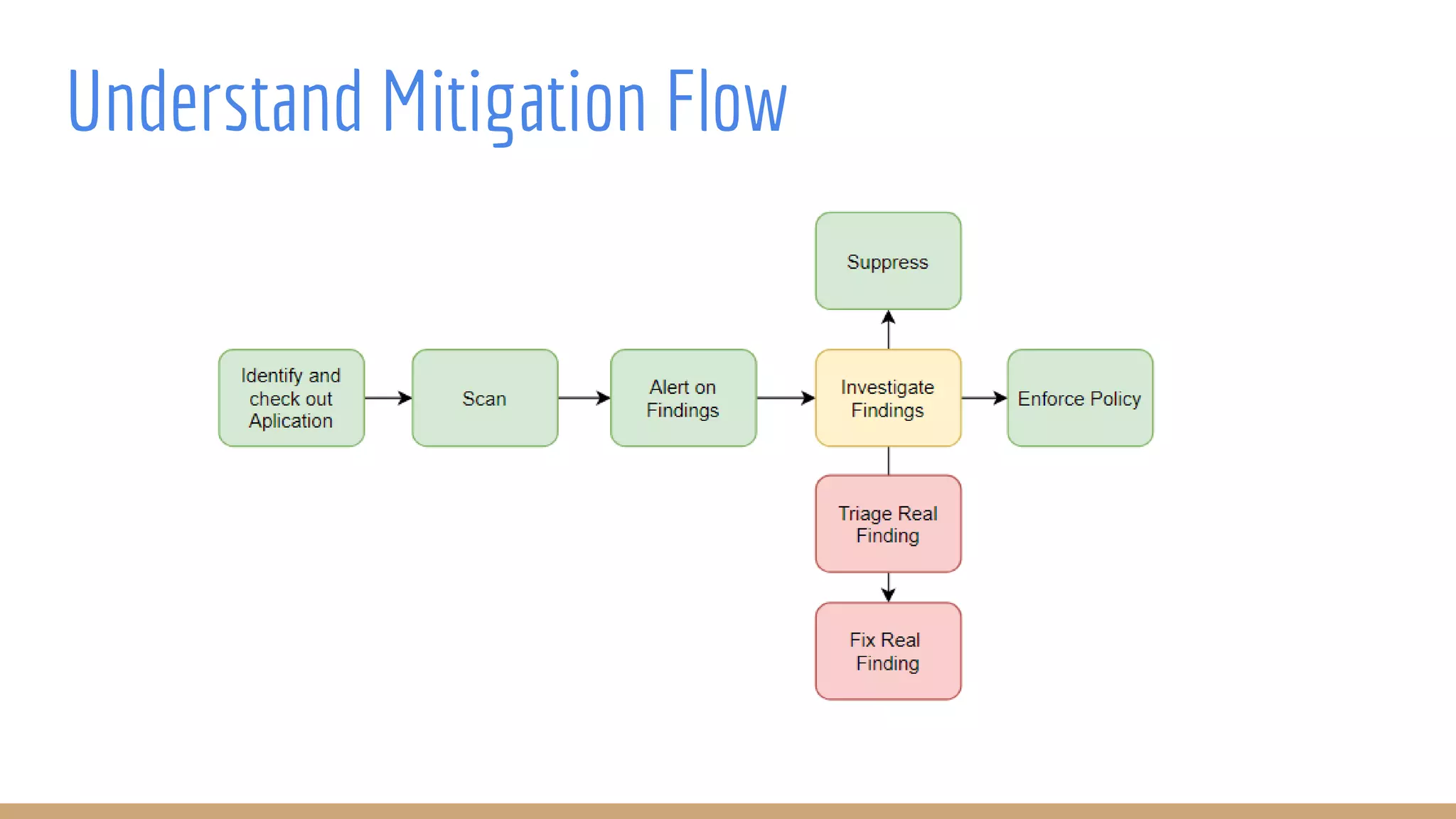
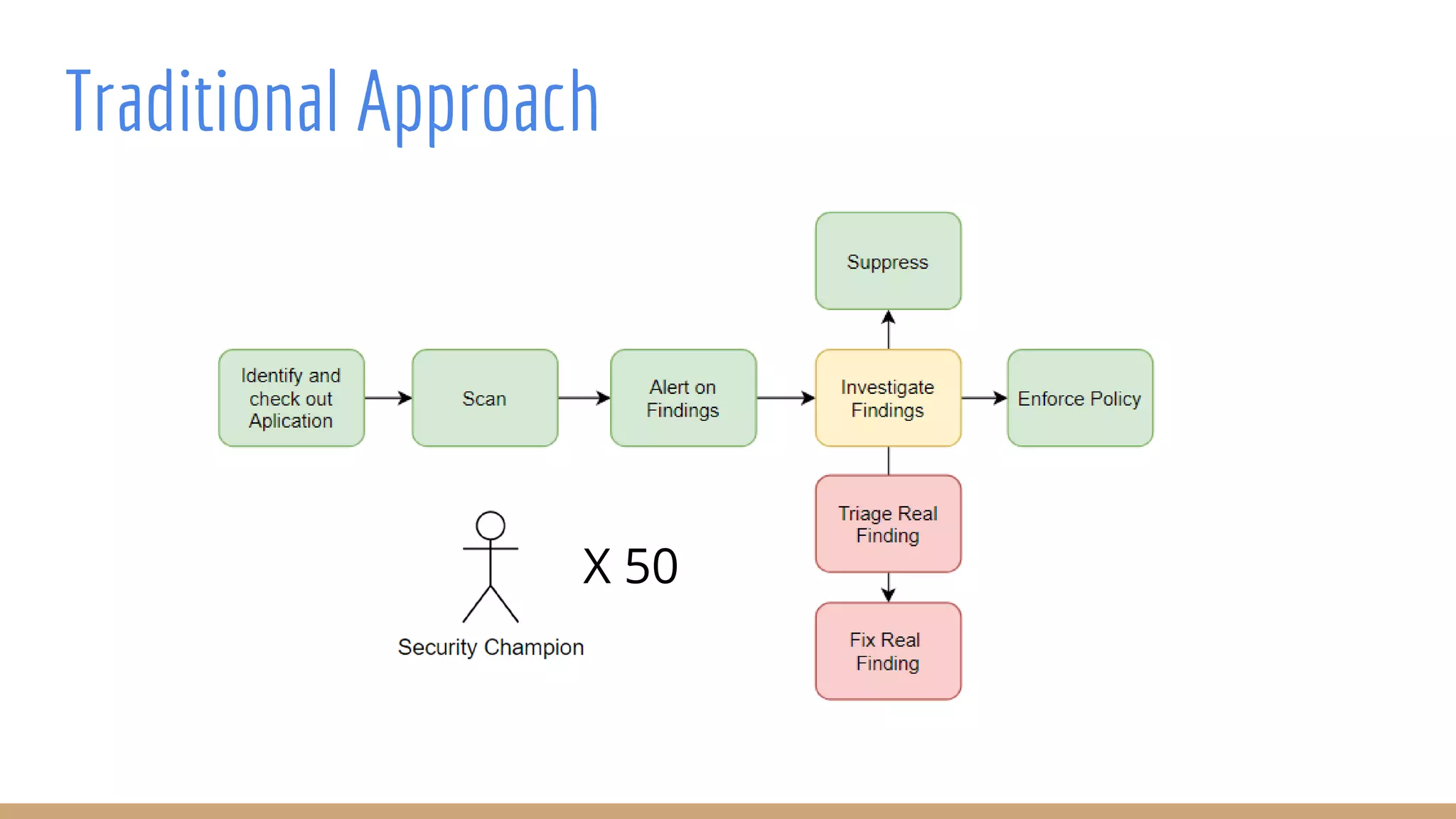
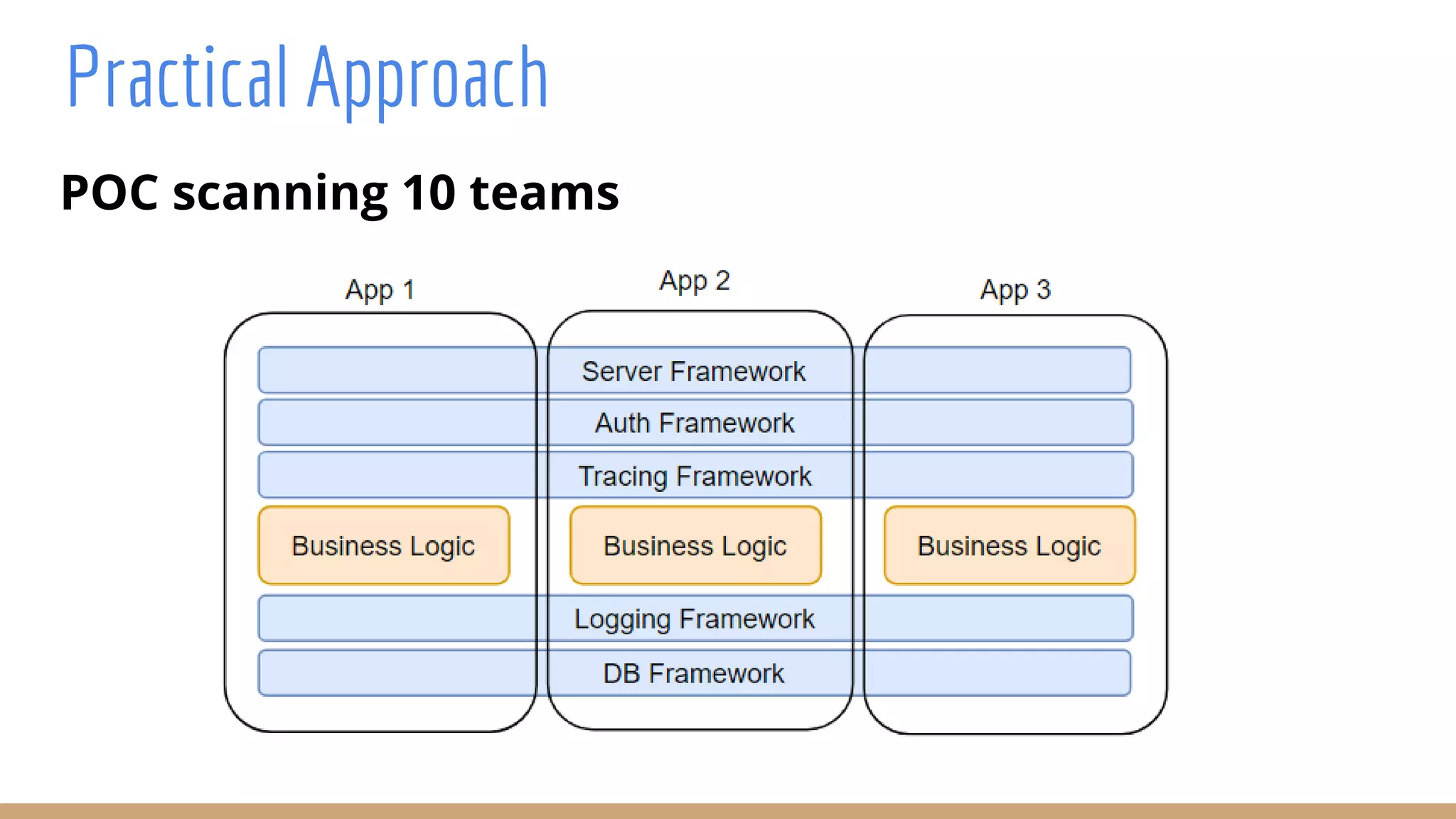
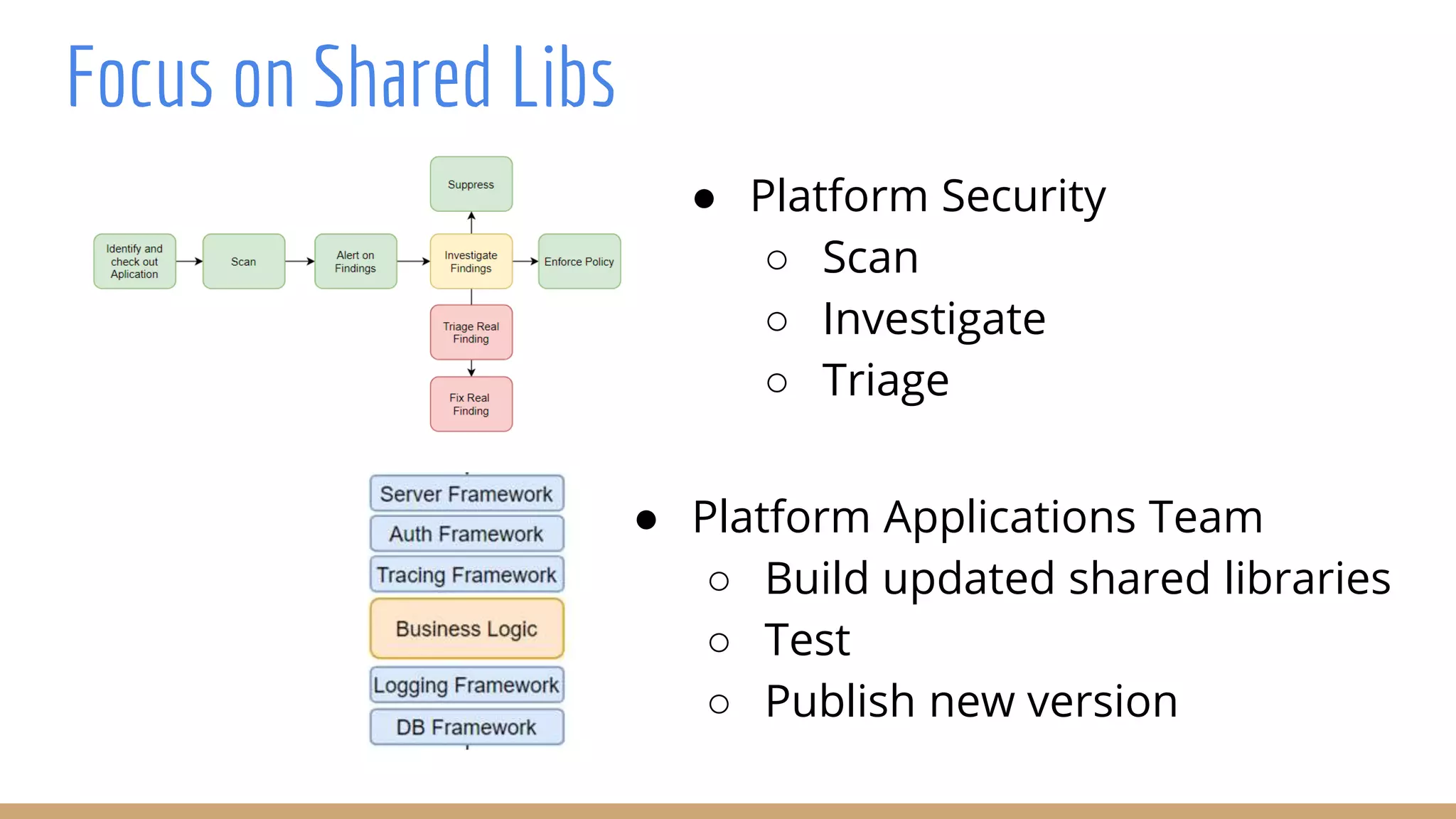
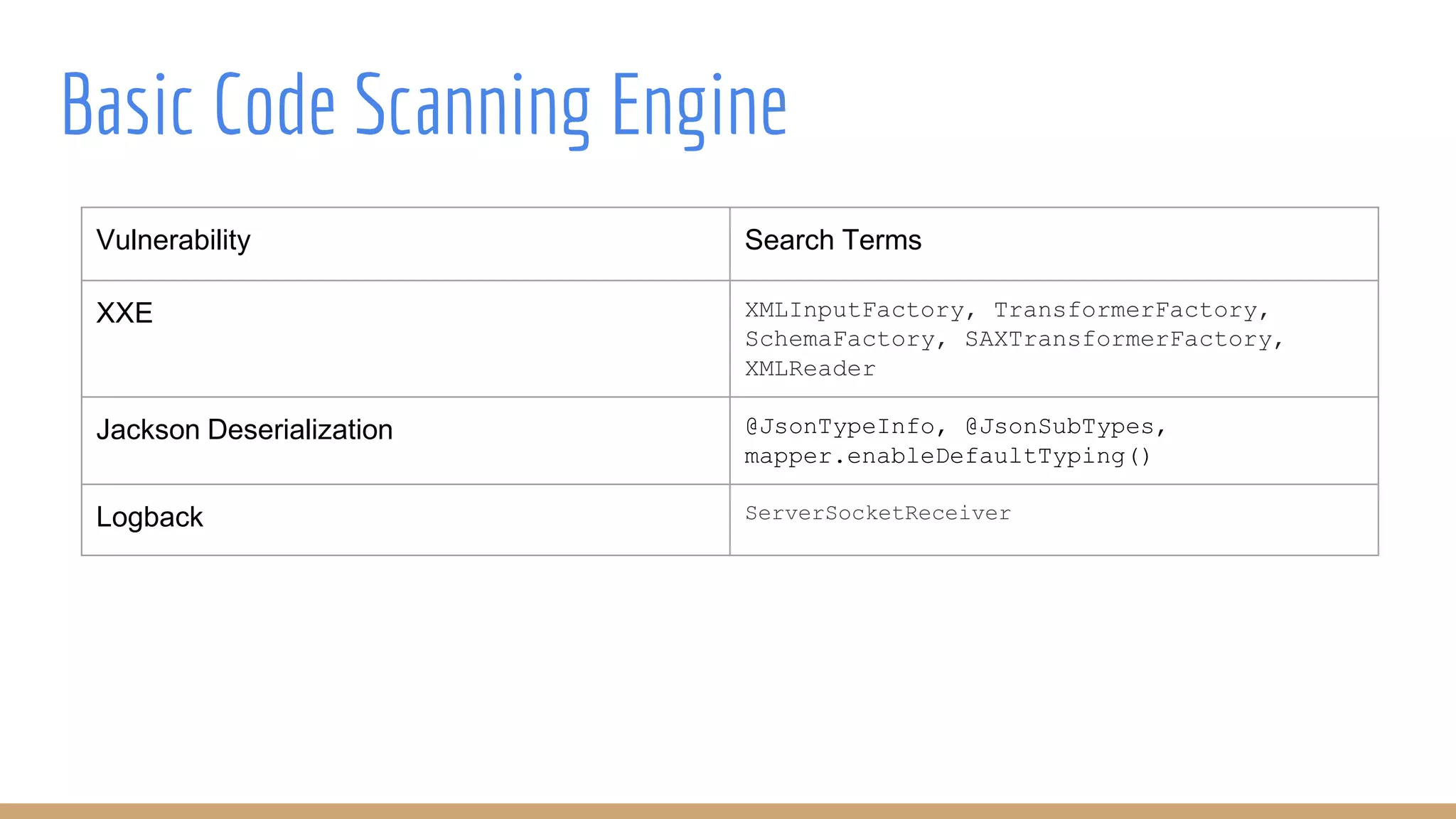
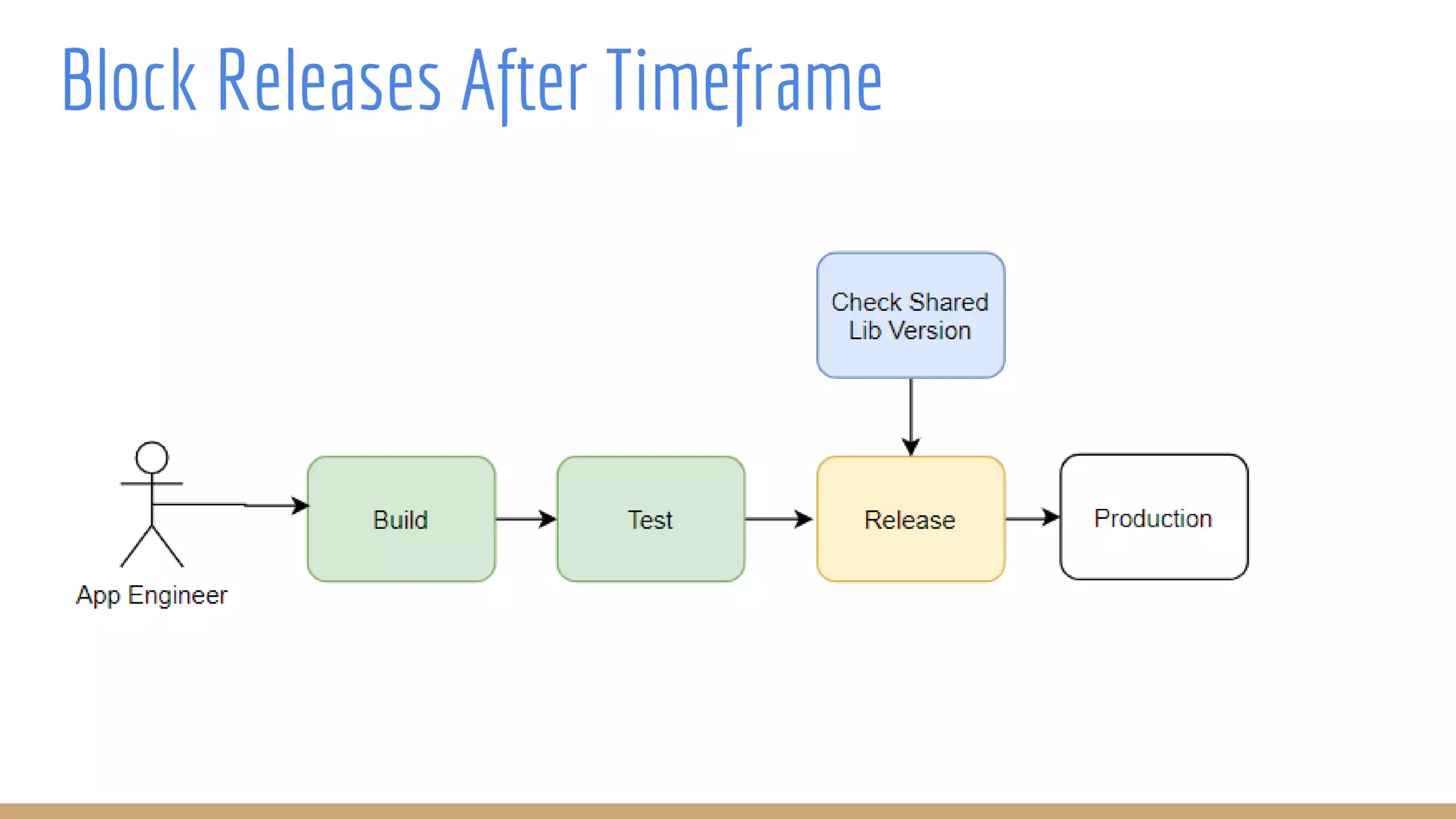
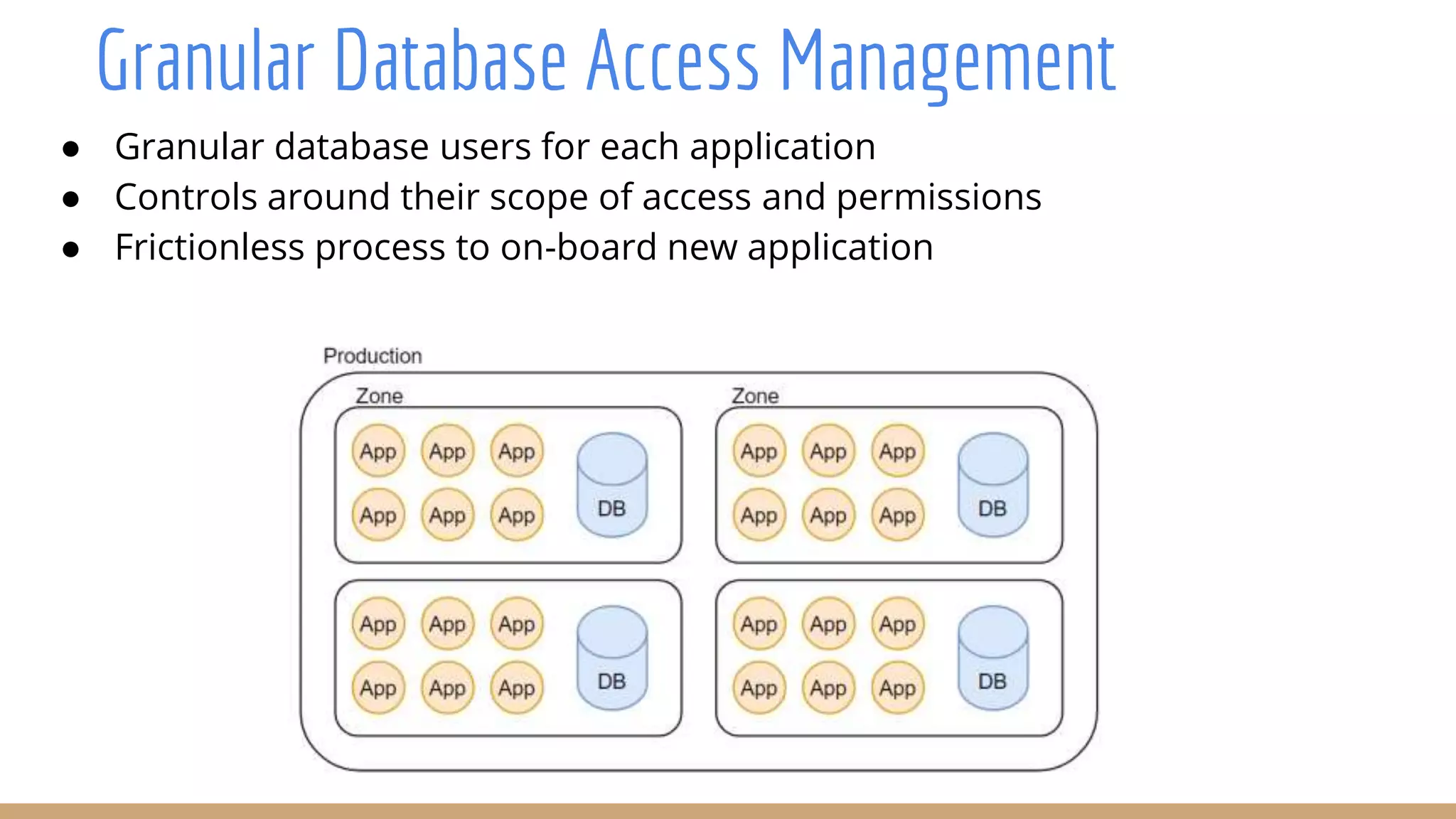
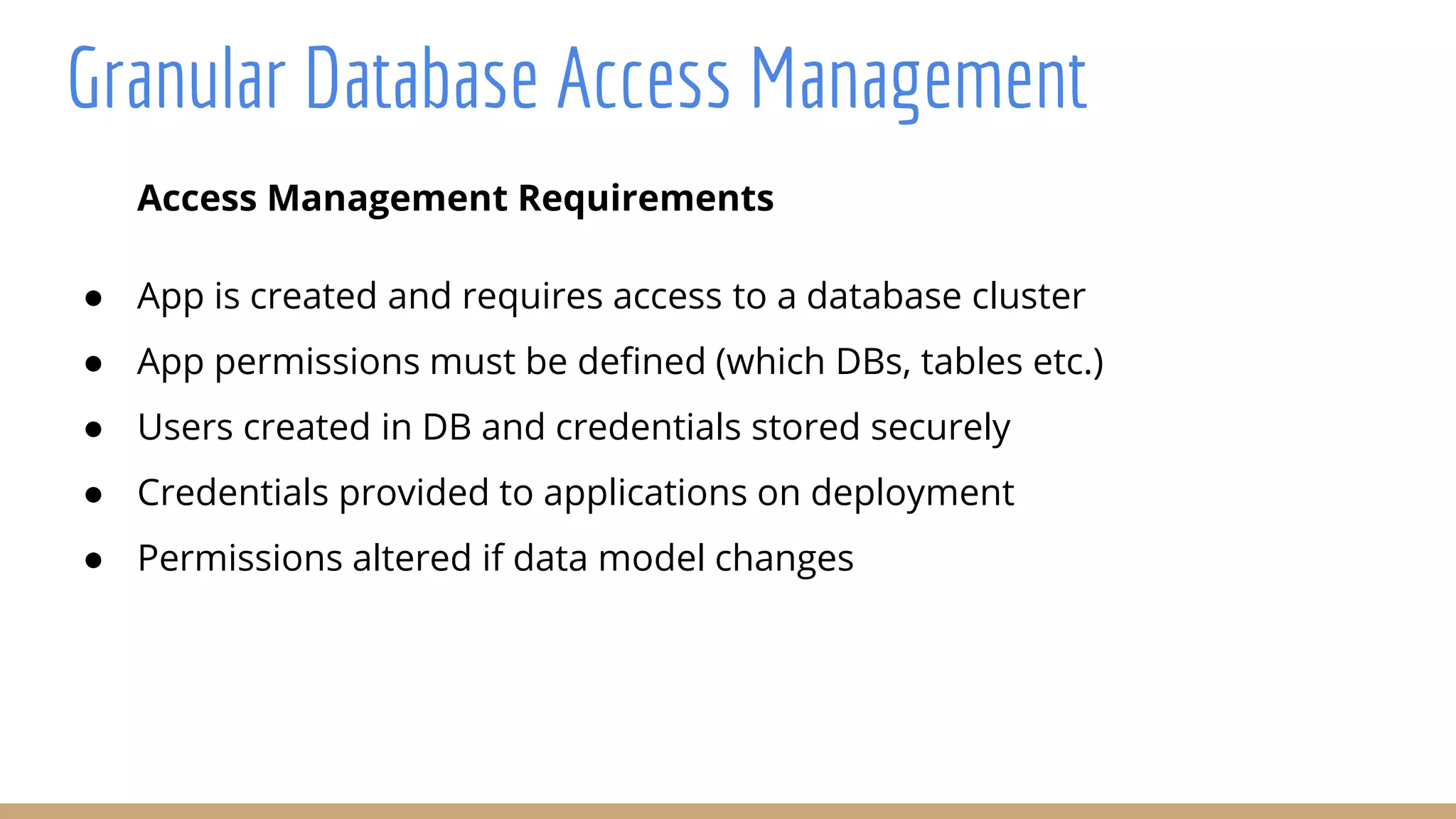
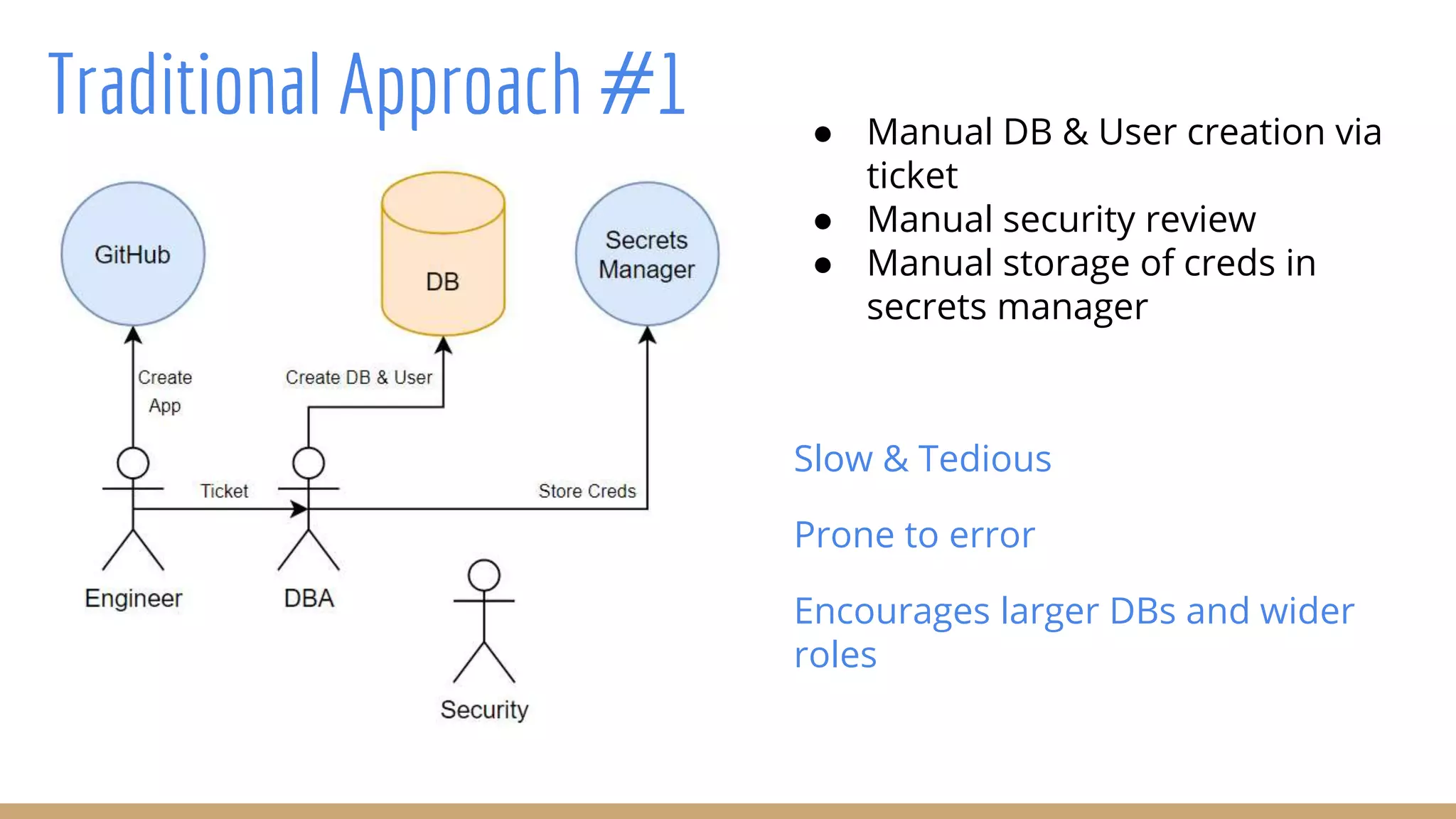
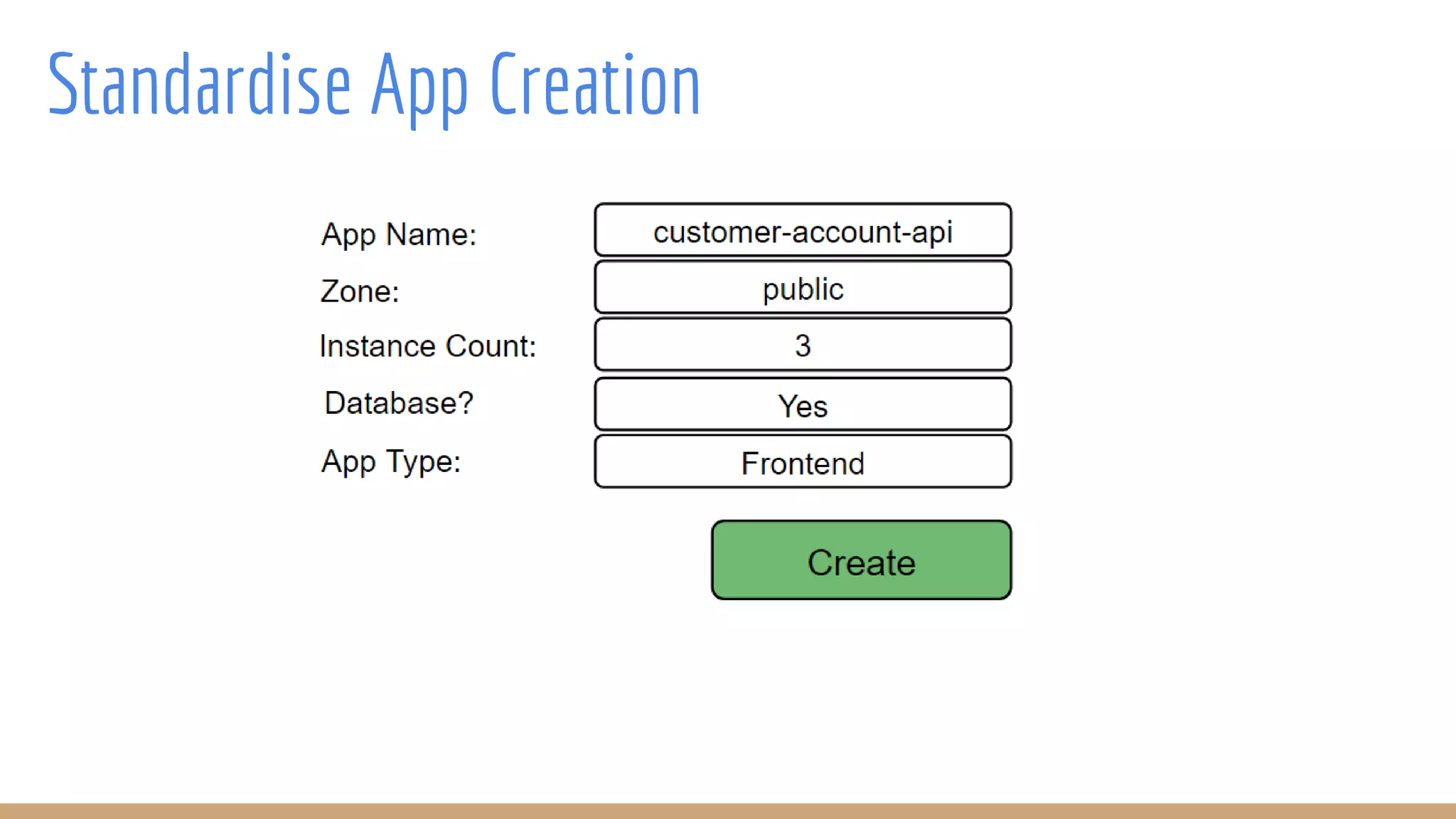
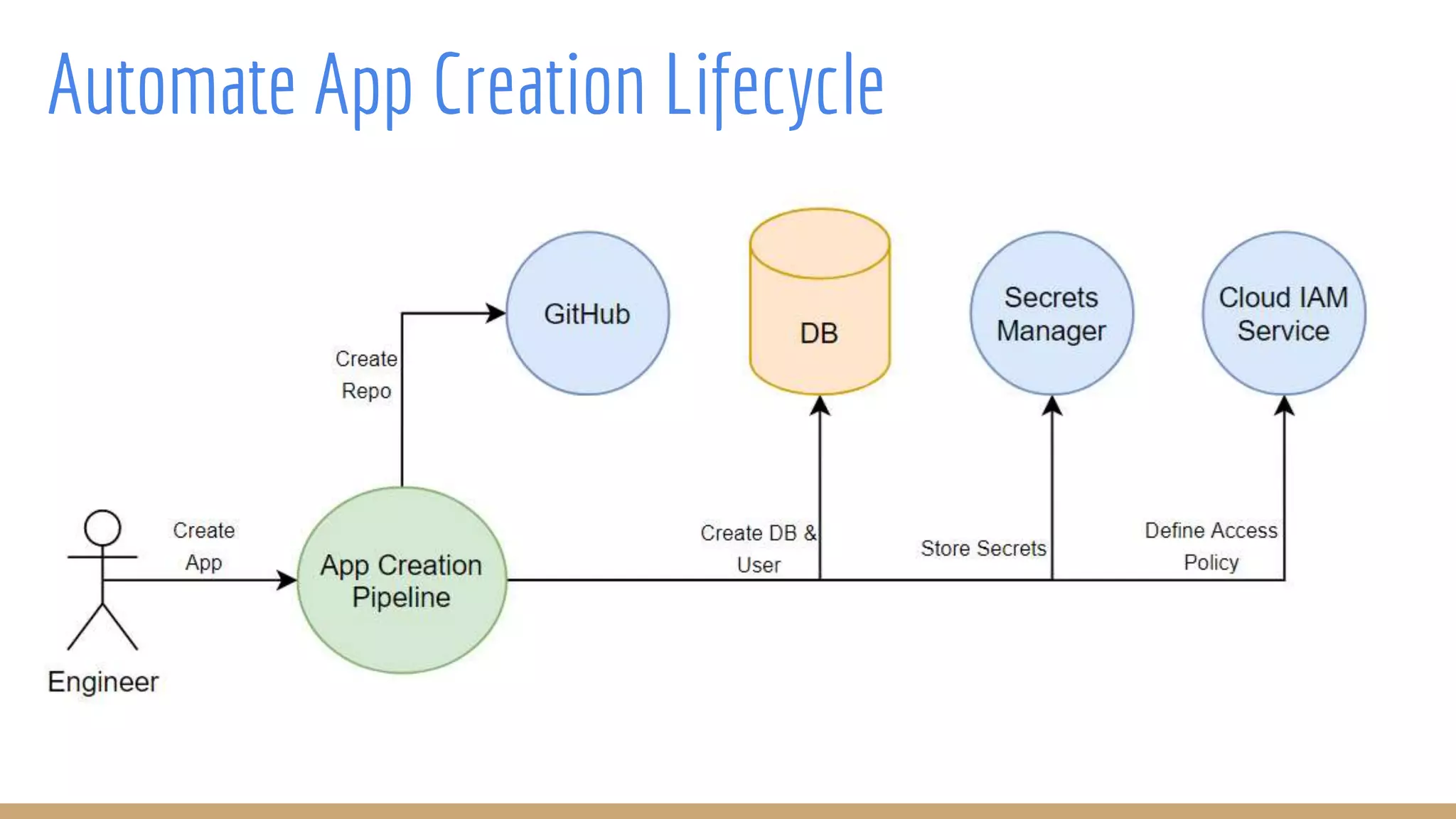
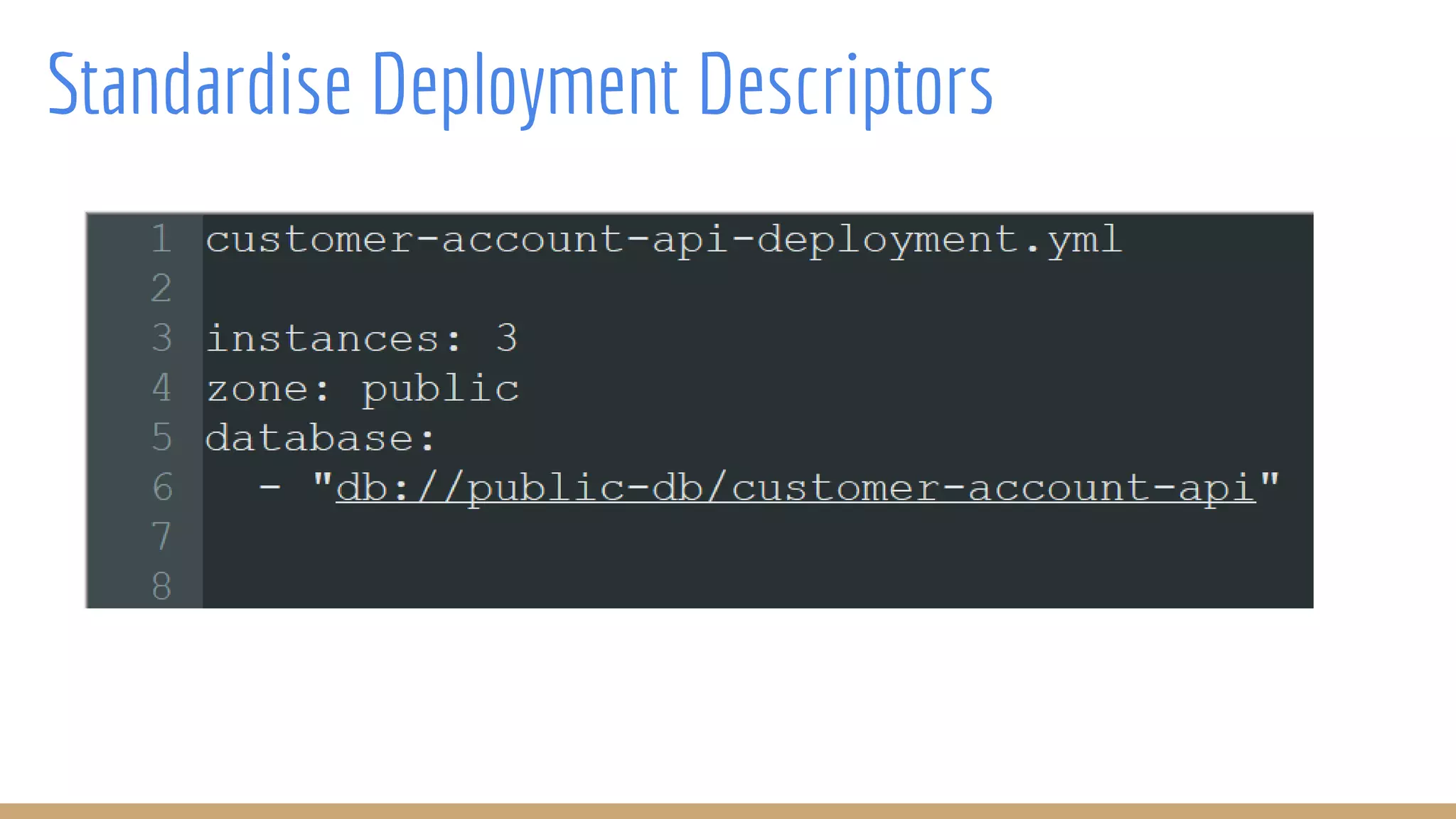
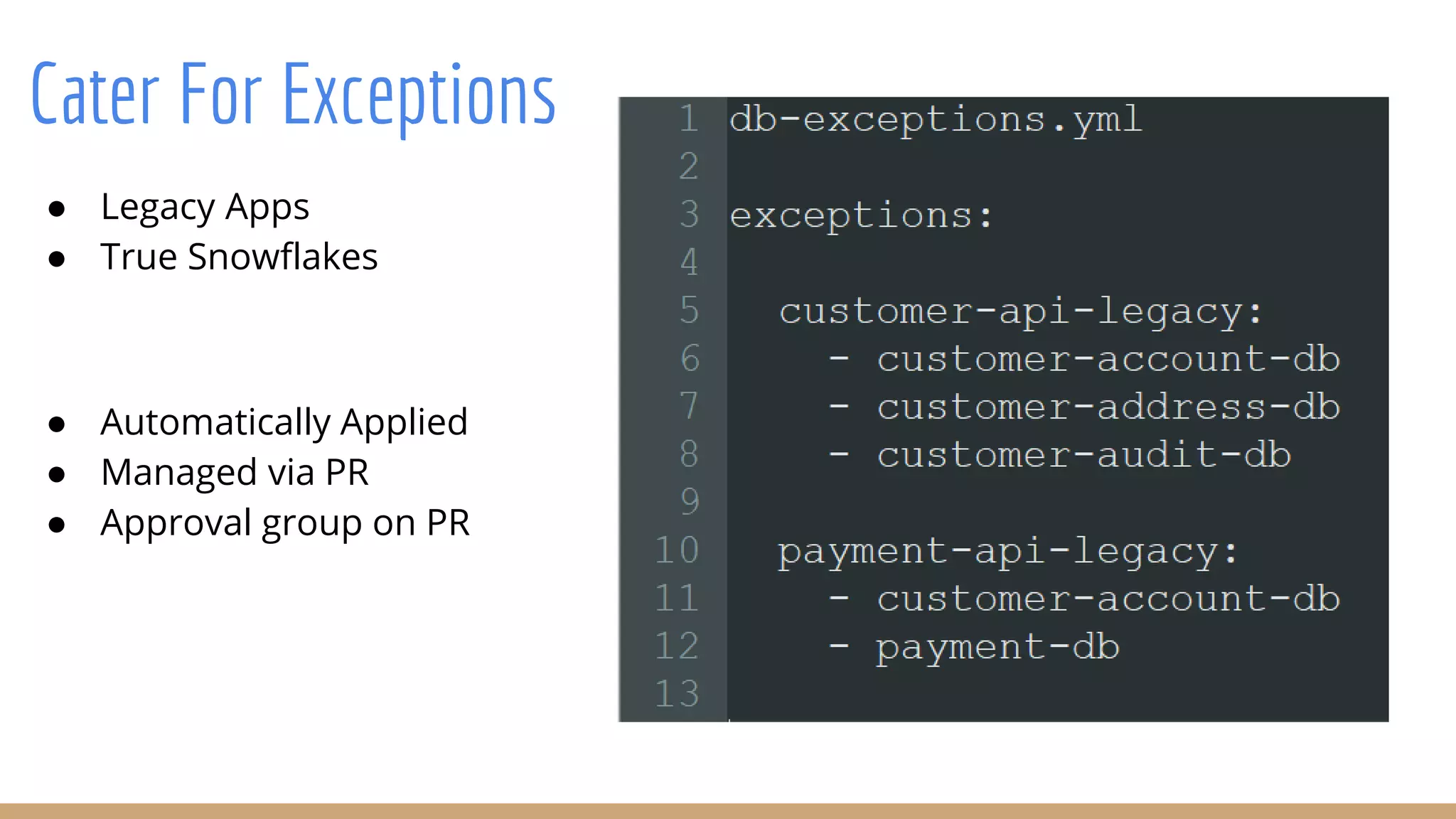
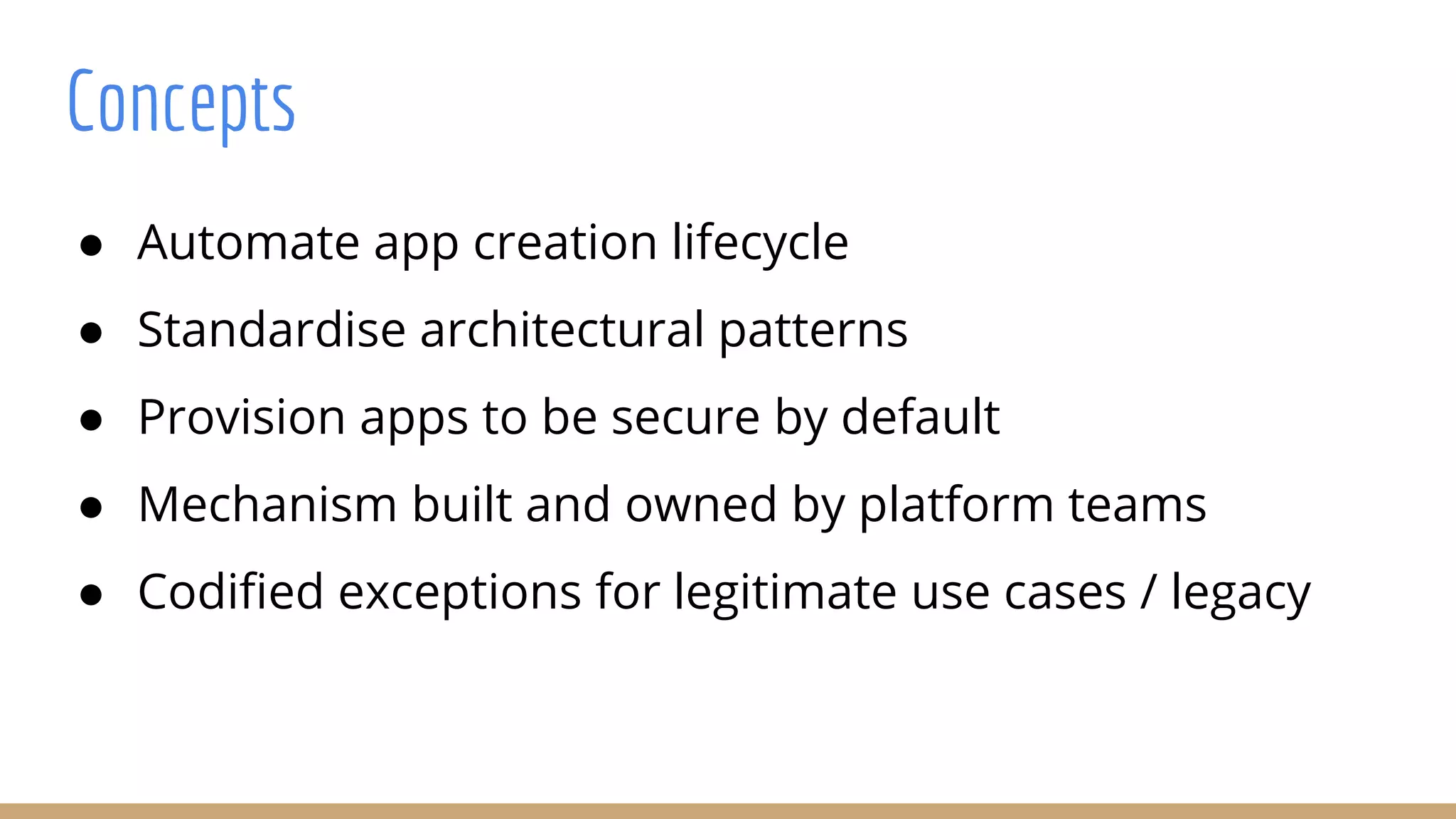
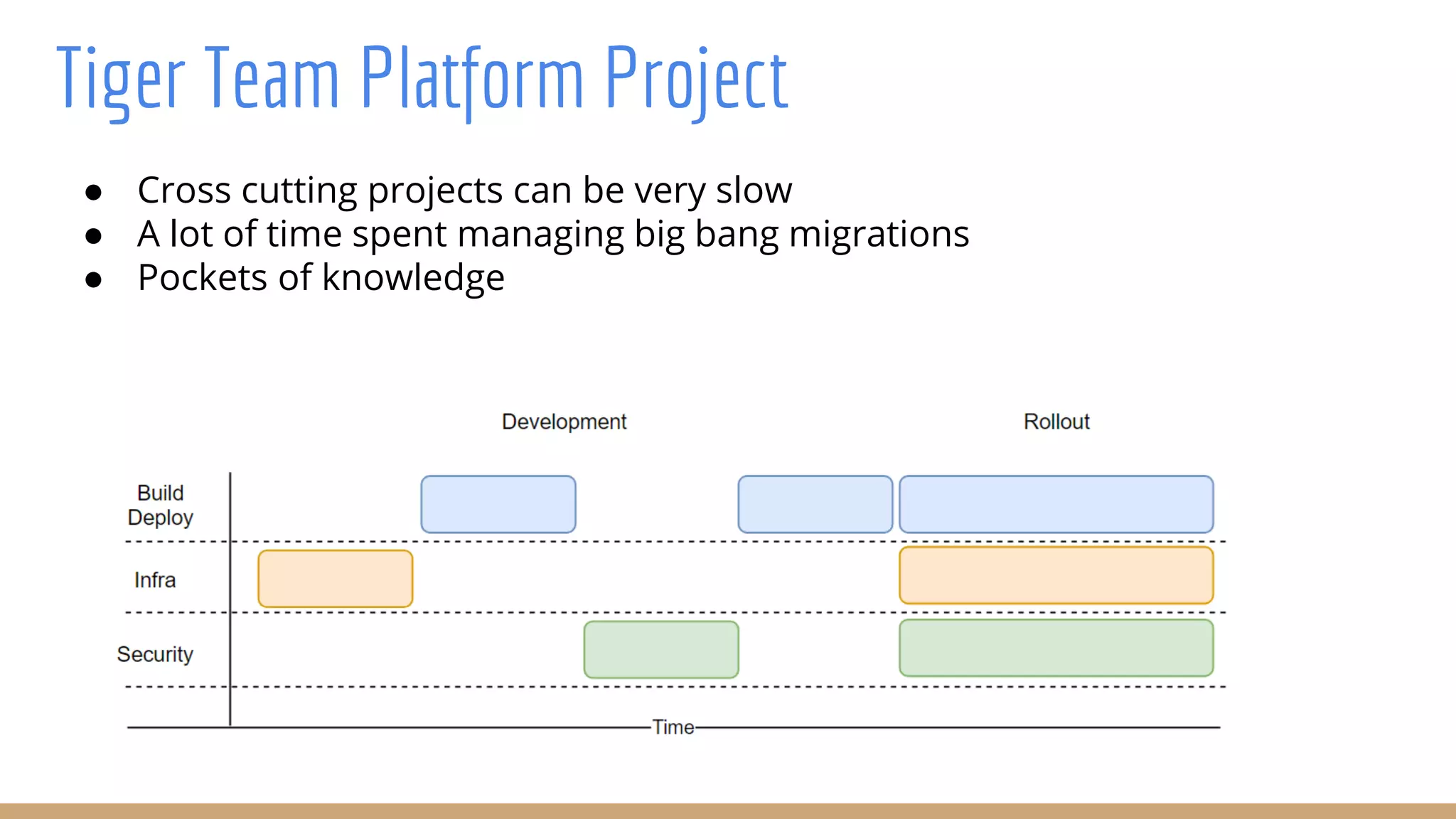
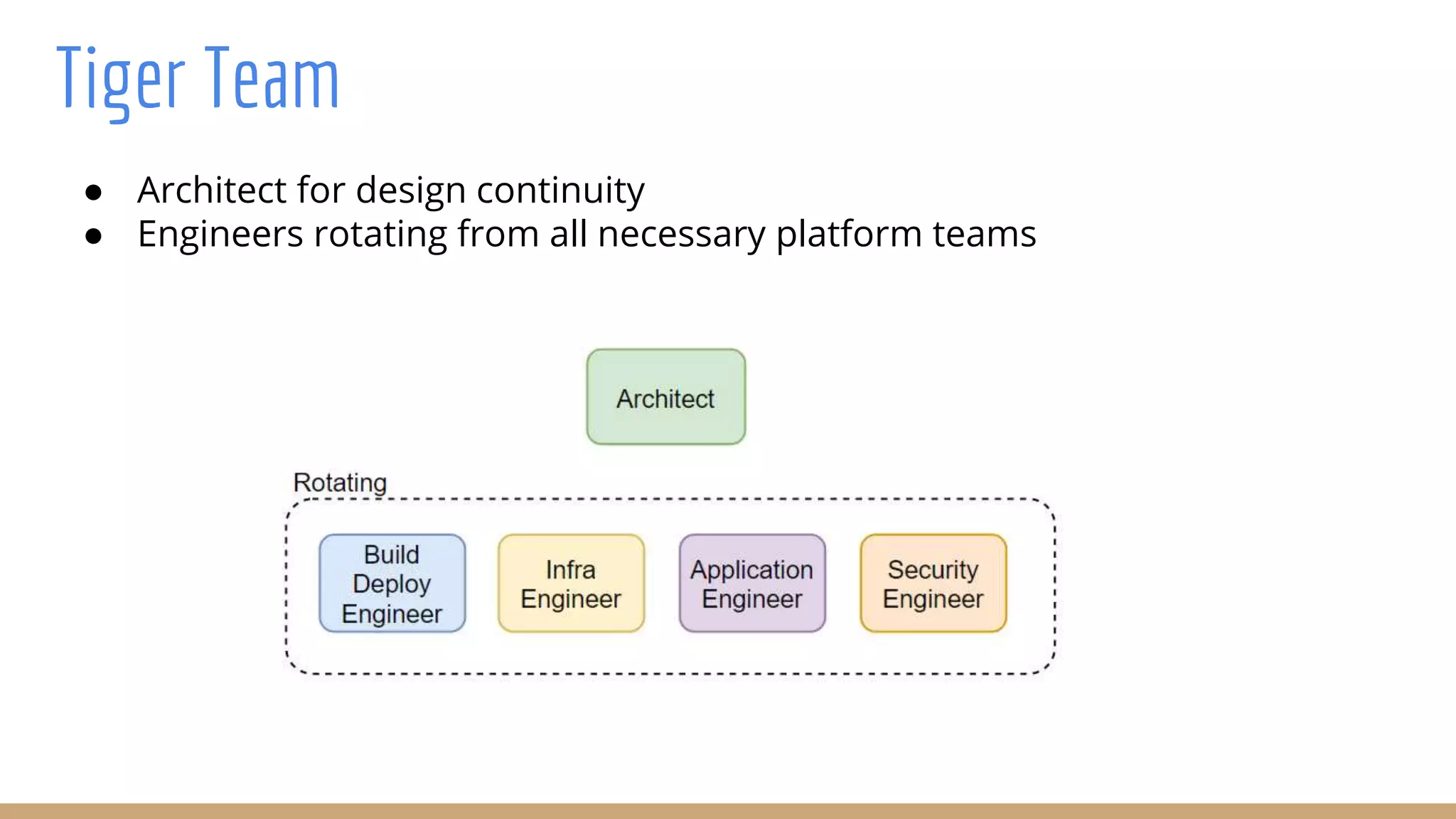
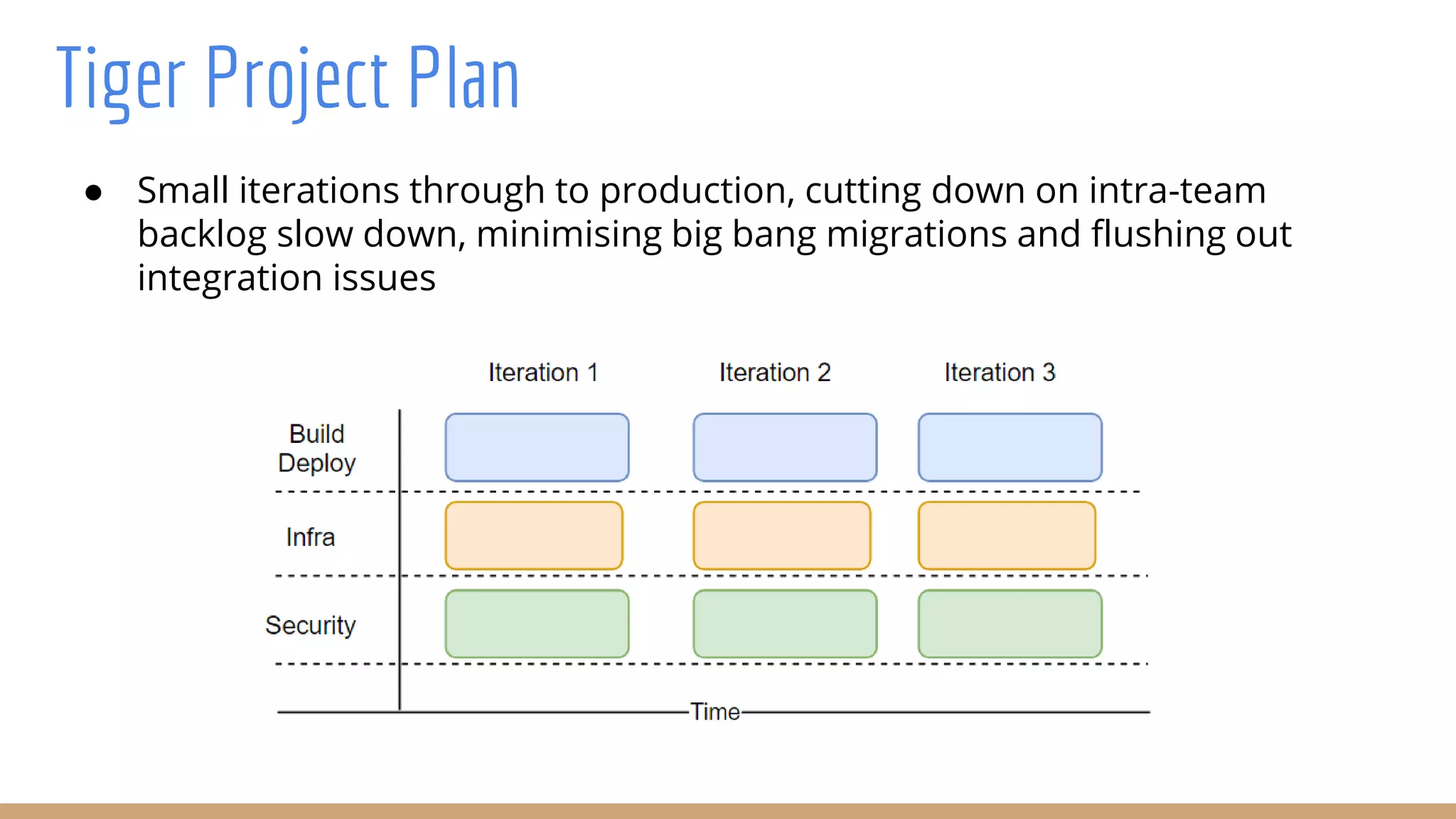
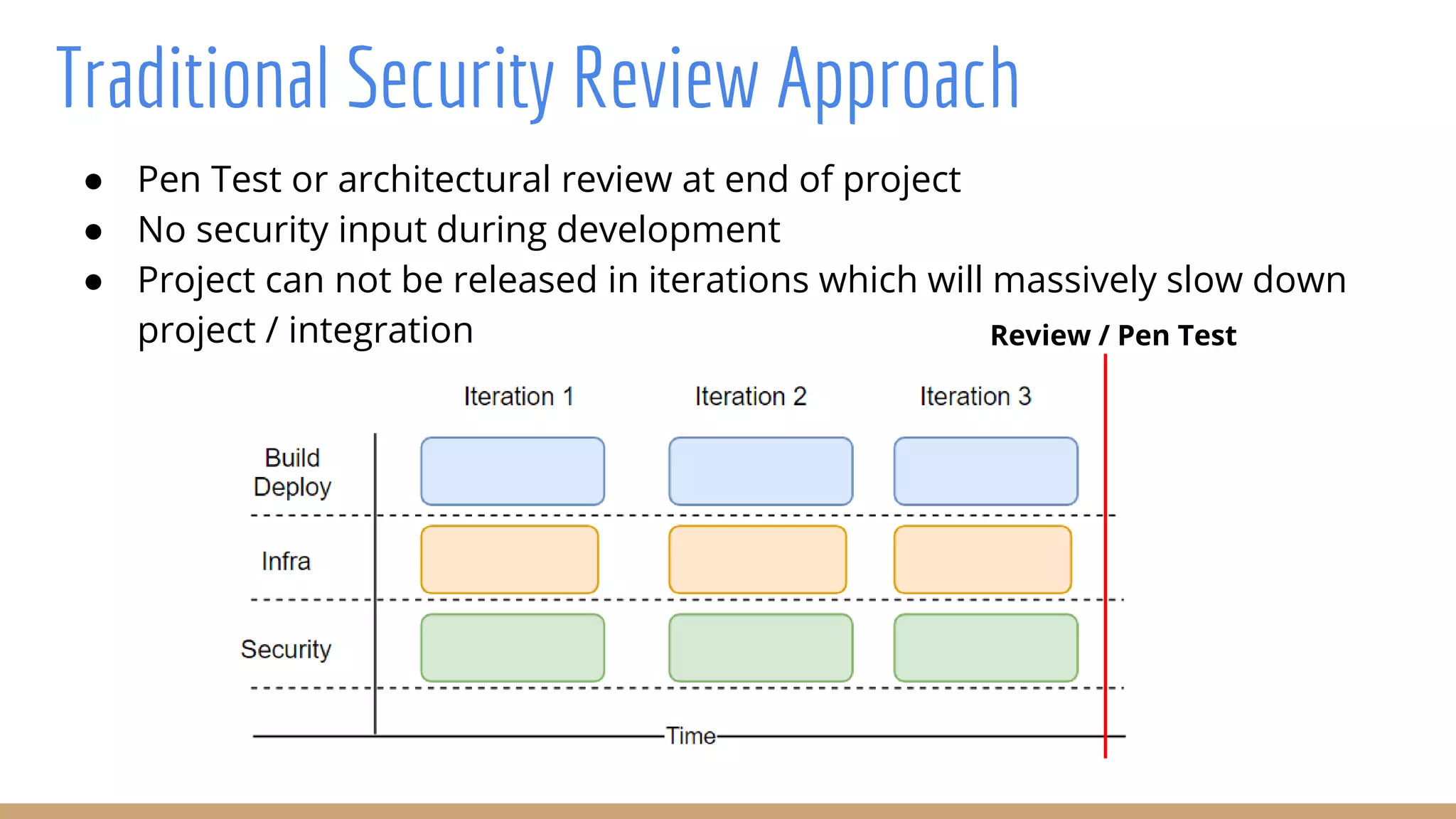
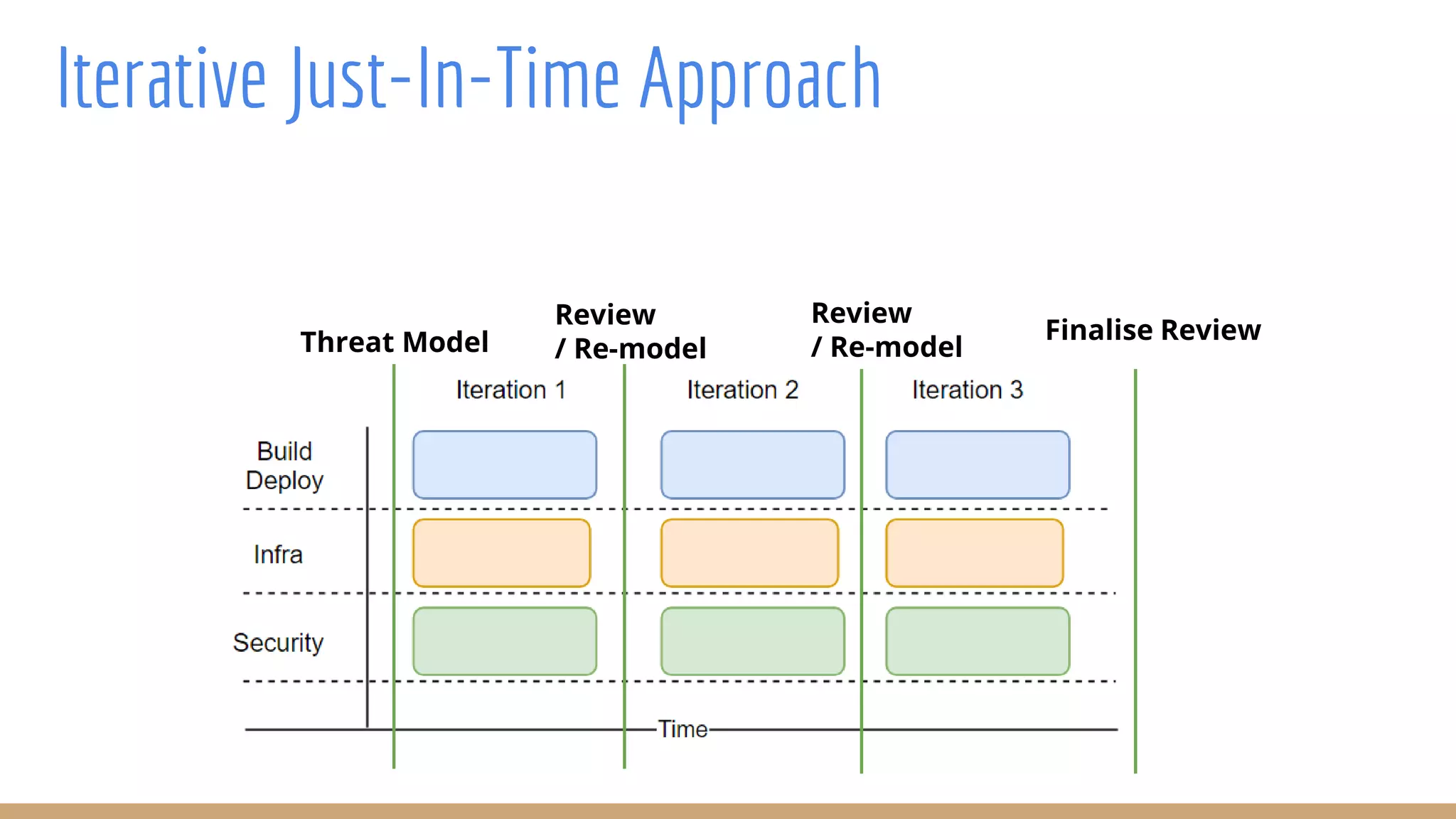
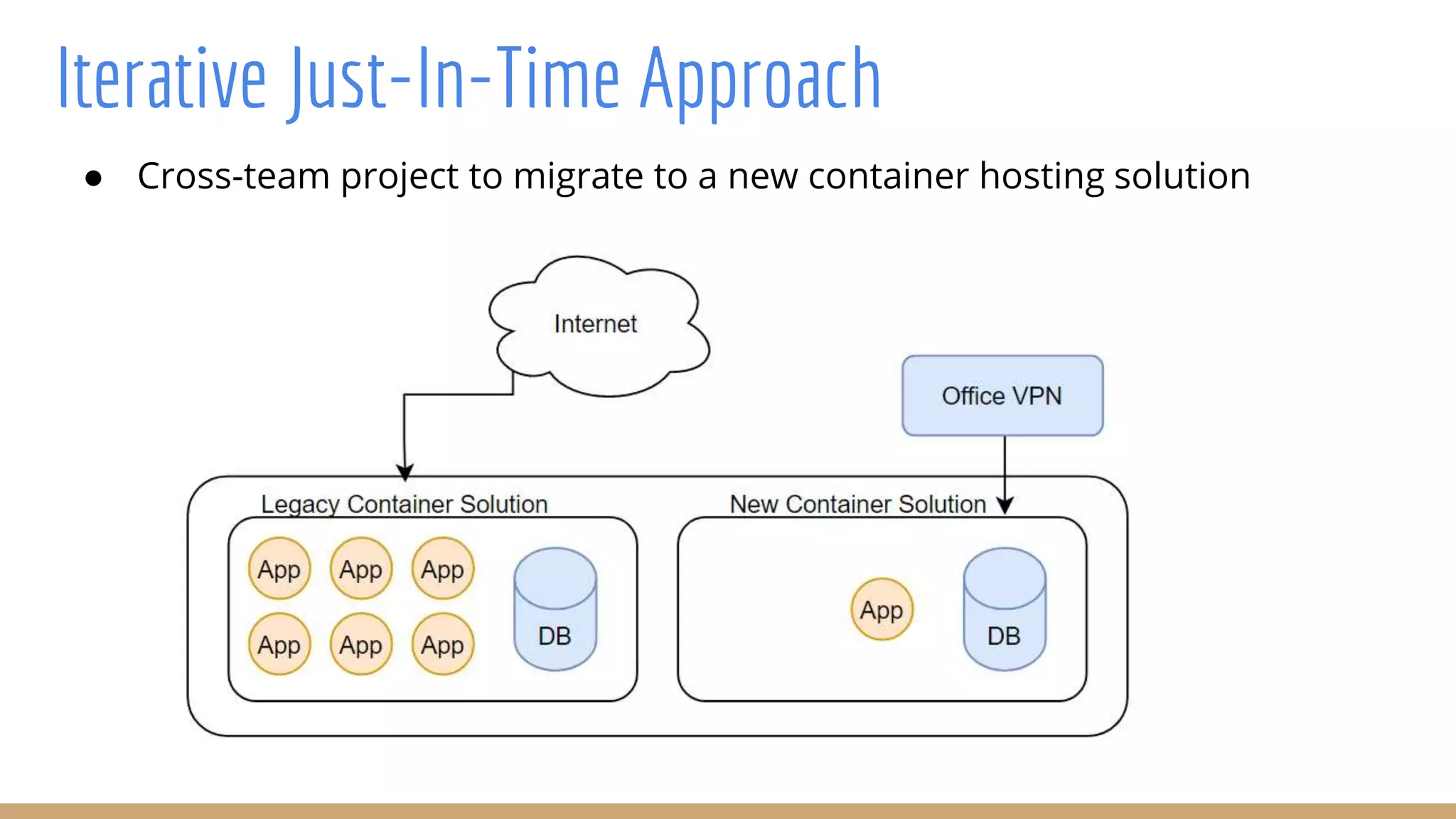
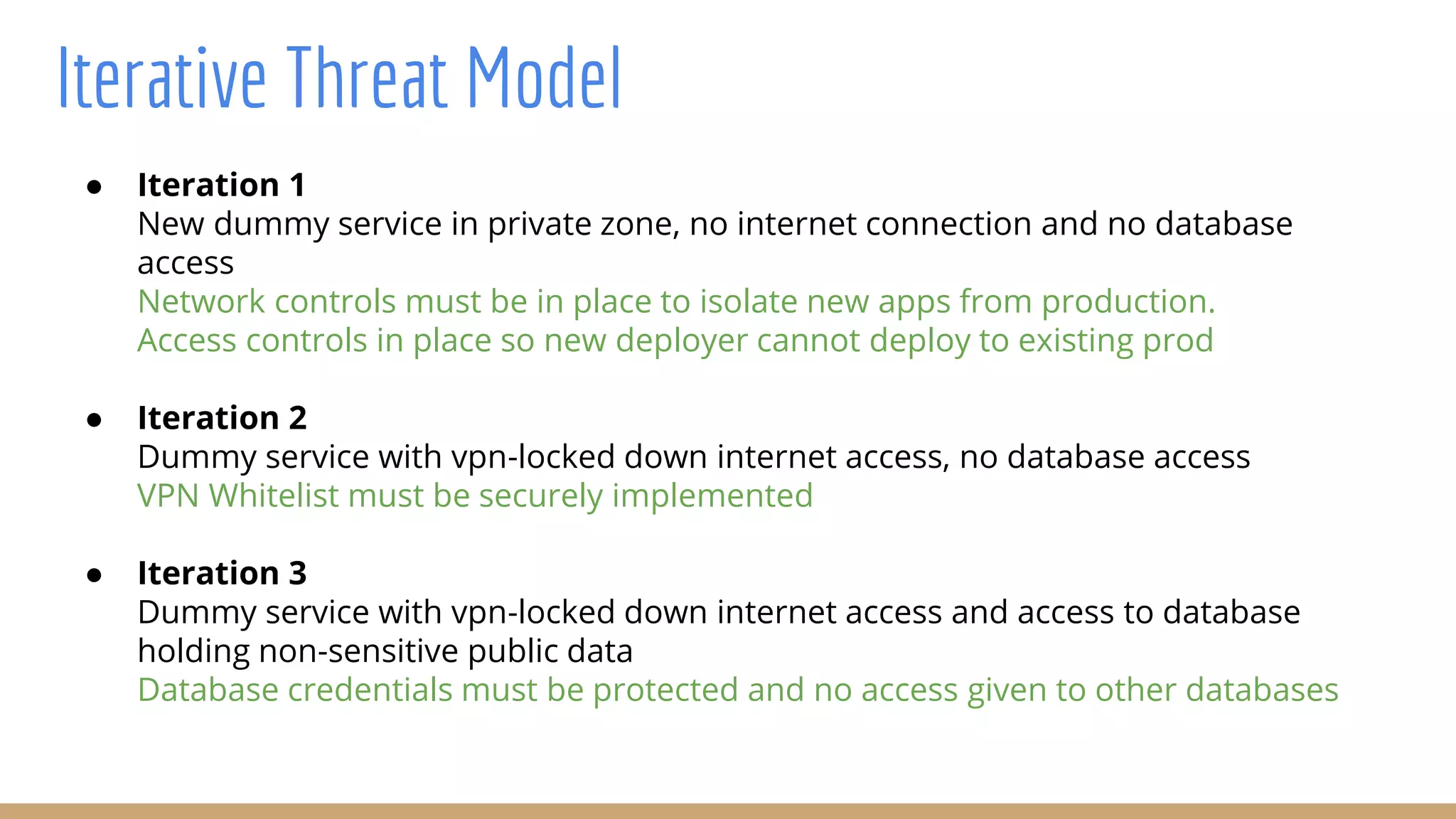
The document outlines best practices for integrating security into platform development workflows, emphasizing a shift-left approach and the importance of ownership by engineers. It discusses the structure and mandate of a platform security team, the challenges of managing security within microservices, and specific vulnerabilities, such as Jackson deserialization. Additionally, it advocates for automation and standardization in access management and database user creation to enhance security while reducing development time and risk.