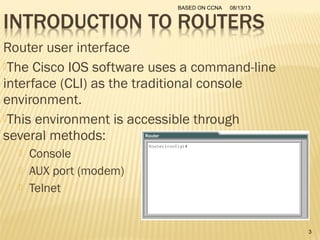
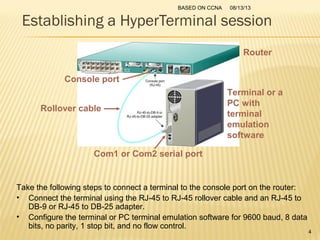
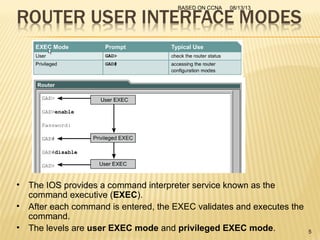
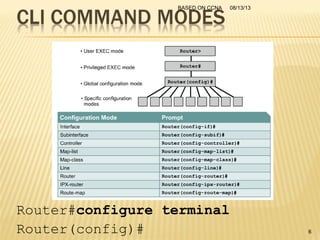
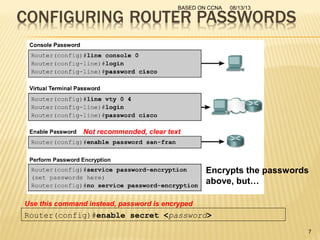
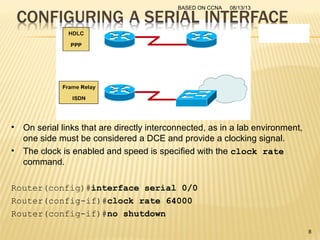
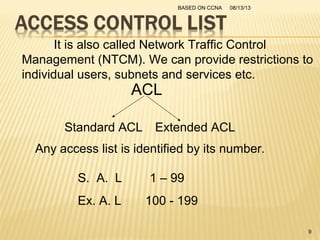
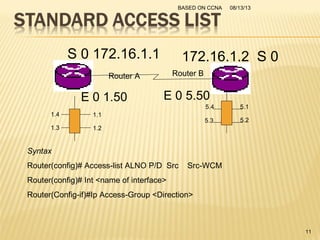
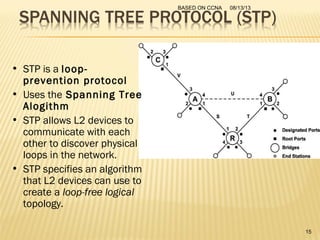
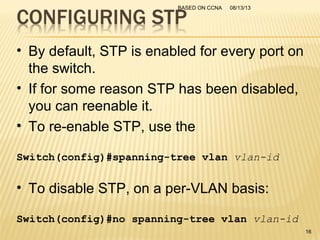
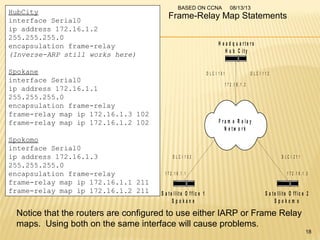
This presentation provides an overview of the Cisco Certified Network Associate (CCNA) certification and covers networking topics required for the CCNA, including router interfaces, access control lists, VLANs, spanning tree protocol, and Frame Relay. It discusses establishing connections to router consoles, router configuration modes, and concepts such as routing protocols, network addressing, and inter-VLAN routing. Examples of configuration commands are provided for tasks like interface configuration, VLAN creation, and Frame Relay mapping.